KQL Cafe - April 2025, Tue, Apr 29, 2025, 6:00 PM | Meetup
Hi Kusto Fans,
Another month another [KQL Cafe](https://kqlcafe.com/#upcoming-shows) session.
As usual we cover what is new in KQL and what we did with KQL in the last mont
Are you joining The KQL Cafe (@kqlcafe.bsky.social) next week? I will be talking about #KQL, Logic Apps, APIs and a combination of the three during the session.
Interested? Register here: www.meetup.com/kql-cafe/eve...
📅 When: April 29 18:00 - 19:30 (CET)
🖥️ Where: Online
💰 Cost: Free of charge
22.04.2025 16:09 — 👍 1 🔁 0 💬 0 📌 0
https://github.com/SecurityAura/DE-TH-Aura/blob/main/100DaysOfKQL/Day%20100%20-%20CScript.exe%2C%20WScript.exe%20or%20MSHTA.exe%20Executed%20from%20Web%20Browser%20Process.md
#100DaysOfKQL
Day 100 - CScript.exe, WScript.exe or MSHTA.exe Executed from Web Browser Process
IT'S FINALLY OVER! I had another query in store for today, but I feel like this challenge wouldn't be complete without that one.
(cont)
t.co/lwO1hmrqUk
13.04.2025 02:46 — 👍 5 🔁 1 💬 2 📌 0
Pushed a #KQL that returns the top 10 SecurityEvents with the largest ingestion size. This can help determine which events you may want to aggregate or filter, depending on your detection/forensic needs.
github.com/Bert-JanP/Hu...
12.04.2025 07:58 — 👍 3 🔁 0 💬 0 📌 0
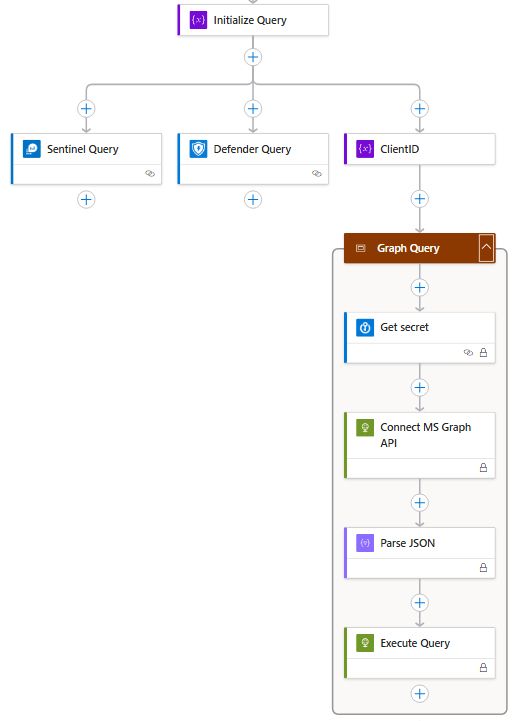
It's time to prepare some content for the next
@kqlcafe.bsky.social . I will discuss #KQL, Logic Apps and hunting through the available APIs.
The session is on April 29th and is completely free to attend online.
🗓️Event registration & details: www.meetup.com/kql-cafe/
31.03.2025 18:06 — 👍 5 🔁 2 💬 0 📌 0

On my way to #ELDK2025 🇩🇰
First stop Hamburg! 🇩🇪
03.03.2025 14:21 — 👍 1 🔁 0 💬 0 📌 0
GitHub - Bert-JanP/Incident-Response-Powershell: PowerShell Digital Forensics & Incident Response Scripts.
PowerShell Digital Forensics & Incident Response Scripts. - Bert-JanP/Incident-Response-Powershell
🛡️Released DFIR PowerShell V3!
New features include:
- Granular response capabilities for Acquisition, Analysis, and Containment
- Expanded support beyond Windows, enabling Cloud response activities via Graph API
github.com/Bert-JanP/In...
27.02.2025 19:39 — 👍 4 🔁 0 💬 0 📌 0
What EndpointCall do you use for these detections? Or do you only rely on SignInLogs for device code auth?
18.02.2025 16:52 — 👍 0 🔁 0 💬 1 📌 0
I am aware, that is most often the case for the phishing flow. But this scenario focusses more on the flow of accessing management apis from unmanaged devices using device code auth.
18.02.2025 16:50 — 👍 1 🔁 0 💬 0 📌 0
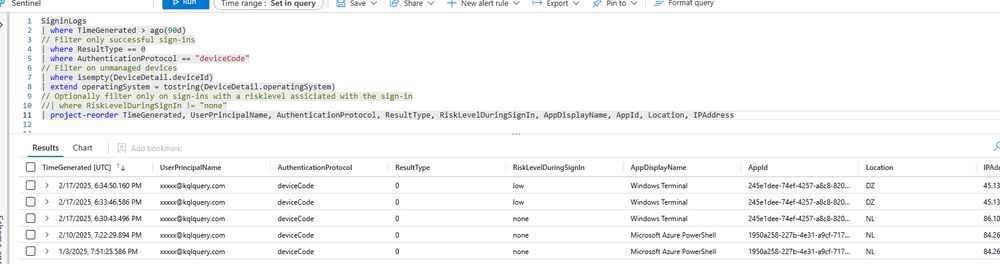
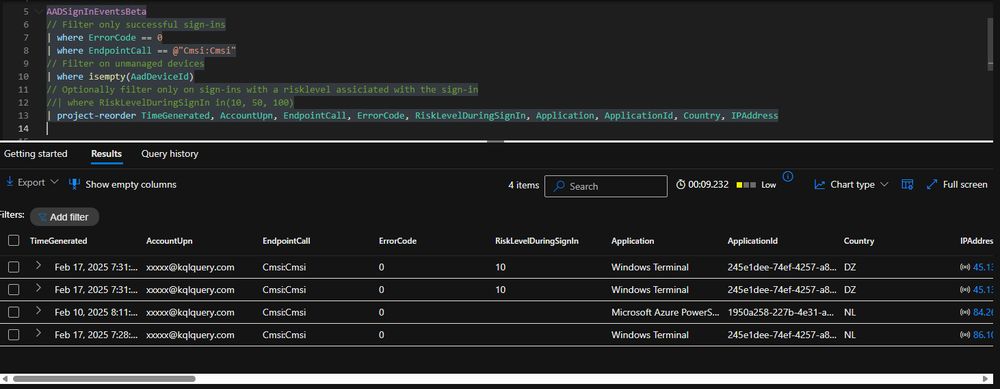
Pushed a #KQL for: Successful device code sign-in from an unmanaged device.
Query is available for AADSignInEventsBeta and SigninLogs. Less known is the AADSignInEventsBeta filter for device code:
| where EndpointCall == "Cmsi:Cmsi"
🏹Query: github.com/Bert-JanP/Hu...
17.02.2025 18:53 — 👍 5 🔁 3 💬 2 📌 0
Microsoft Expanded Cloud Logs Implementation Playbook | CISA
If your company runs Exchange Online and/or Microsoft 365 have a look at CISA's latest publication: Microsoft Expanded Cloud Logs Implementation Playbook.
The report includes KQL, SPL and Powershell code to perform incident response.
www.cisa.gov/resources-to...
20.01.2025 19:08 — 👍 4 🔁 1 💬 0 📌 0
📬 Have you checked latest Kusto Insights by @ugurkoc.de & @bertjancyber.bsky.social
🗓 December update is available now kustoinsights.substack.com/p/kusto-insi...
#KustoInsights #KustoQuery #KustoQueryLanguage #KQL #MicrosoftSecurity
12.01.2025 15:18 — 👍 2 🔁 1 💬 0 📌 0
Created a #KQL hunting query to list the initial LDAPNightmare exploit (CVE-2024-49113) connection. With this, you can hunt for both successful and failed exploitation attempts 🏹
github.com/Bert-JanP/Hu...
06.01.2025 20:44 — 👍 1 🔁 0 💬 0 📌 0
That deployment pipeline is not finished yet :D
23.12.2024 20:55 — 👍 1 🔁 0 💬 0 📌 0
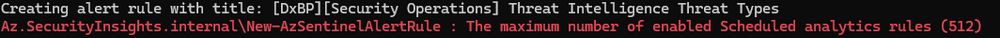
It has been a good day. 😅
Az.SecurityInsights.internal\New-AzSentinelAlertRule : The maximum number of enabled Scheduled analytics rules (512)
learn.microsoft.com/en-us/azure/...
23.12.2024 18:38 — 👍 2 🔁 0 💬 1 📌 0
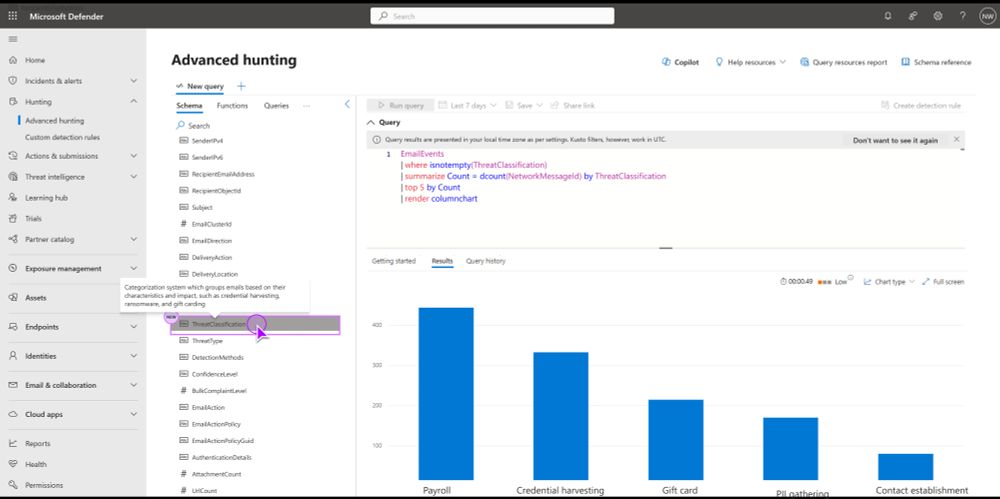
Anyone already seen the column ThreatClassification land in their tenant? The column will be added to the EmailEvents table.
Source: techcommunity.microsoft.com/blog/microso...
06.12.2024 17:42 — 👍 3 🔁 0 💬 1 📌 0
Time to get a #KQL query from the shelve: Potential Adversary in the middle Phishing
If you have High-Risk users and axios useragents in the results please revoke some sessions.
🏹 github.com/Bert-JanP/Hu...
Query is available for both SigninLogs and AADSignInEventsBeta.
02.12.2024 17:37 — 👍 6 🔁 2 💬 0 📌 0
🔓 Microsoft MVP Security
👷♂️ Security Architect/Engineer
writer of mediocre code 💻
blog: https://infernux.no
github: https://github.com/lnfernux
practical hacking: https://infernux.no/practical-hacking/
#Microsoft #Security #MVP #CTF
GCIH, GCFE | DFIR, Threat Hunting, Detection Engineering | @CuratedIntel DFIR Member
SecurityAura.com
http://infosec.exchange/@SecurityAura
Chaotic good security analyst | CTI & OSINT | Wanna be threat hunter | They/them
Tech, organizer, founder of Experts Live Denmark
Cyber Defence Specialist
mbsecure.nl/about/
Senior Security Researcher (DART) at Microsoft. Opinions are my own. #MSIncidentResponse #DART #Microsoft365 #EntraID #DefenderXDR #Sentinel
Sr. Director of SOC at Huntress. Ex-Mandiant/FireEye. Bringing security to the Fortune 5,000,000.
💜-Team Hacker
my spirit animal is a trojan horse 🐎😈
Training the next generation of purple team hackers
(he/him)
https://maikroservice.com/email
Threat Hunting - DFIR - Detection Engineering
🐙 https://github.com/mthcht
🐦 https://x.com/mthcht
📰 https://mthcht.medium.com
Love Microsoft Security, love to ride his Canyon roadbike, happy dad.
📂 GitHub: https://github.com/awt-tom
💼 LinkedIn: https://linkedin.com/in/tomrolvers
✍️ Blog: https://AzurewithTom.com
Working @ https://yellowarrow.nl
Things I say on Twitter are personal opinions and views.
Team Blue | DFIR | Bug bounties
Full time Blood Glucose manager (T1D)
https://blog.wesselhissink.nl
Co-leader OWASP Cornucopia. If you like what we do for open source, visit our code repository https://github.com/OWASP/cornucopia and give us a star ⭐
🌈 «Difference is of the essence of humanity» 🦄 – John Hume
#appsec #owasp #cornucopia #threatmodeling
Regional Threat Protection Tech Lead @ Microsoft | Former Microsoft MVP | Father 👭/Hasbund 👫/🍷&⌚️ enthousiast/Explorer ✈️ | Views my own | blog michalos.net
Dad ⚭ Husband
𒉭 Azure Security | IAM | DE&TH
https://attackthesoc.com/
🤬🧊
What stands in the way, becomes the way
PowerShell.org: Empowering the PowerShell and DevOps community with resources, events, and insights. Join us for scripts, tools, and collaboration! #PowerShell #DevOps
CTO Principal Cyber Security Consultant at @BaseVISION | building cyber defenses to protect the enterprise | Microsoft security MVP | Host of http://KQLCafe.com
@chvancooten on the bird app 🐦
---
Benevolently malicious offensive security enthusiast || OffSec Developer & Malware Linguist || NimPlant & NimPackt author || @ABNAMRO Red Team
Hacker at outsidersecurity.nl. Researches Entra ID, AD and occasionally Windows security. I write open source security tools and do blogs/talks to educate others on these topics. Blog: dirkjanm.io