#BREAKING #ESETresearch identified the wiper #DynoWiper used in an attempted disruptive cyberattack against the Polish energy sector on Dec 29, 2025. At this point, no successful disruption is known, but the malware’s design clearly indicates destructive intent. 1/5
23.01.2026 16:30 — 👍 35 🔁 30 💬 1 📌 5

Trend Micro tracks SHADOW-VOID-042 spear-phishing (Nov 2025) using Trend Micro-themed lures and a decoy site mimicking Trend’s corporate style, targeting defence, energy, chemicals, cybersecurity and ICT sectors. www.trendmicro.com/en_us/resear...
12.12.2025 10:22 — 👍 3 🔁 3 💬 0 📌 0

spear phishing email using Trend Micro updates as a lure

targeted industries

comparison between this intrusion set and Void Rabisu

Website mimicking Trend Micro graphical design
We investigated an #APT with links to Void Rabisu (Romcom) that used Trend Micro updates as a lure in a recent campaign involving vulnerability exploitation. There were at least 4 stages before the final payload, some of them being tailored to the targeted machine www.trendmicro.com/en_us/resear...
11.12.2025 15:03 — 👍 1 🔁 1 💬 0 📌 0

SHADOW-VOID-042 Targets Multiple Industries with Void Rabisu-like Tactics
Recently various industries, including Trend Micro, were targeted by a Trend Micro-themed campaign. Trend Vision One™ stopped it early in the kill chain. The campaign somewhat aligns with Void Rabisu (ROMCOM). For now we track this temporarily under SHADOW-VOID-042 www.trendmicro.com/en_us/resear...
11.12.2025 12:01 — 👍 2 🔁 0 💬 0 📌 0

The Rise of Collaborative Tactics Among China-aligned Cyber Espionage Campaigns
Cyberespionage campaigns are becoming increasingly complex due to the close collaboration between distinct APT groups. Learn how China-aligned Earth Estries provides initial access to compromised assets for Earth Naga (Flax Typhoon) to continue exploitation: www.trendmicro.com/en_us/resear....
22.10.2025 20:34 — 👍 1 🔁 0 💬 0 📌 0
Internet Crime Complaint Center (IC3) | Home Internet Connected Devices Facilitate Criminal Activity
One of the botnets that is using a modular approach that will likely be able to circumvent network-based access controls against residential proxies is known as BadBox 2.0. The FBI issued an advisory yesterday: www.ic3.gov/PSA/2025/PSA...
06.06.2025 11:28 — 👍 0 🔁 0 💬 0 📌 0
This modular model is already employed by residential proxy providers in the Far East who obtain millions of residential proxies by exploiting vulnerabilities in the supply chain of inexpensive IoT devices and by shipping pre-infected Android Open Source Project-supported devices (AOSP).
04.06.2025 08:18 — 👍 2 🔁 0 💬 1 📌 0
We anticipate that residential proxy providers will seek to bypass connection and session-based access controls, by uploading separate software modules to residential endpoints. These modules can independently carry out specific tasks like advertisement fraud without relying on proxied connections.
04.06.2025 08:17 — 👍 3 🔁 0 💬 1 📌 0

The Rise of Residential Proxies as a Cybercrime Enabler
This research discusses how residential proxies help cybercriminals bypass antifraud and IT security systems, and how vulnerabilities in the IoT supply chain are exploited where Android-based devices ...
Residential proxies are a key enabler of cybercrime today. This creates a growing need for connection and session-based access control. We used Ja4T fingerprinting that successfully tagged incoming connections from residential proxies to 1,500 IDS systems. www.trendmicro.com/vinfo/us/sec...
04.06.2025 08:15 — 👍 17 🔁 10 💬 2 📌 0
One of my favorite pieces of evidence we were able to obtain was 7 videos with English text, which painstakingly explain how to set up a Beavertail C&C. The screen recording, lasting more than 1 hour, was created by someone logged in with a BlockNovas account from an IP address probably in Russia.
24.04.2025 08:04 — 👍 2 🔁 0 💬 0 📌 0

Russian Infrastructure Plays Crucial Role in North Korean Cybercrime Operations
DPRK cybercrime uses Russian infrastructure in Khasan and Khabarovsk, masked by VPNs, proxies, and RDPs. One fictitious DPRK company to lure IT professionals with interviews was BlockNovas. FBI seized BlockNovas' site and a related C&C on April 23, 2025. Read more: www.trendmicro.com/en_us/resear...
24.04.2025 07:51 — 👍 5 🔁 1 💬 1 📌 0

Updated Shadowpad Malware Leads to Ransomware Deployment
Updated Shadowpad malware used in recent attacks against the manufacturing industry led to ransomware in some incidents. Research by @thehellu.bsky.social : www.trendmicro.com/en_us/resear...
20.02.2025 08:51 — 👍 0 🔁 0 💬 0 📌 0

Earth Koshchei Coopts Red Team Tools in Complex RDP Attacks
Yet another suspected case of publicly disclosed red team tools being used by an intelligence agency — allegedly the SVR — to conduct a sweeping surveillance operation.
(ht @feikeh.bsky.social)
www.trendmicro.com/en_us/resear...
17.12.2024 14:35 — 👍 8 🔁 6 💬 0 📌 0

Earth Koshchei Coopts Red Team Tools in Complex RDP Attacks
Earth Koshchei (APT29): A cyberespionage group targeting critical sectors with stealthy techniques. Here’s what you need to know: www.trendmicro.com/en_us/resear... #Cybersecurity #ThreatIntel with @feikeh.bsky.social
17.12.2024 12:04 — 👍 4 🔁 3 💬 0 📌 0

Earth Koshchei Coopts Red Team Tools in Complex RDP Attacks
Since Aug 2024 Earth Koshchei (APT29, Midnight Blizzard) used 193 RDP relays and 34 rogue backends against military, MFAs and others. The campaign peak was likely preceded by barely audible campaigns that ended with a bang in Oct 2024. Details and indicators here: www.trendmicro.com/en_us/resear...
17.12.2024 08:33 — 👍 8 🔁 7 💬 0 📌 0
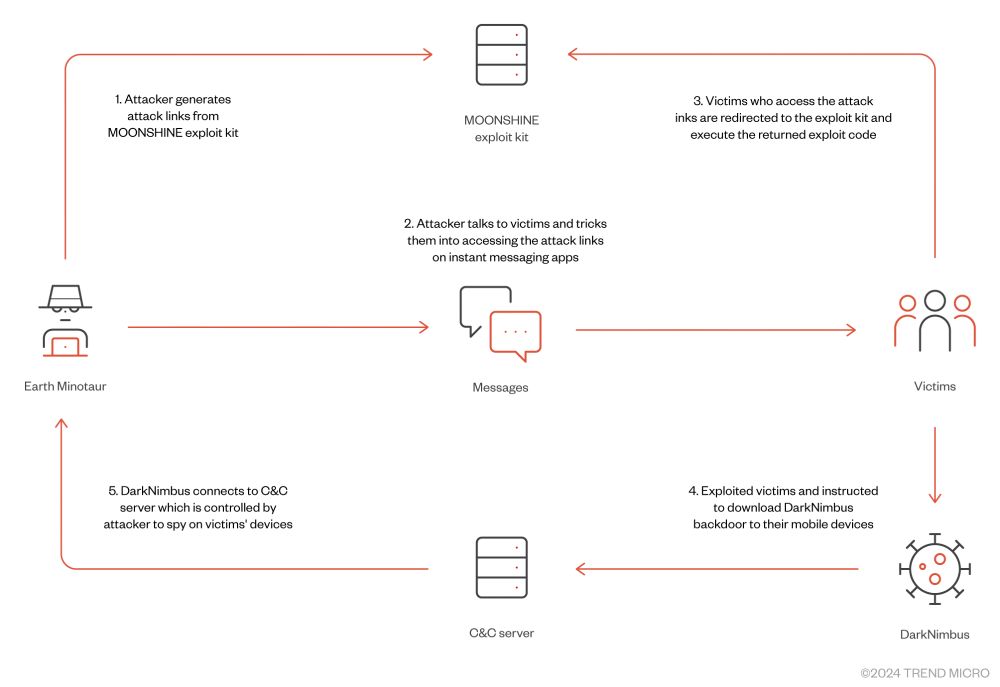
Attack chain showing attacker generating link on Moonshine, then sending it through targeted application to the victim, which after clicking the links gets compromised and delivered the DarkNimbus backdoor
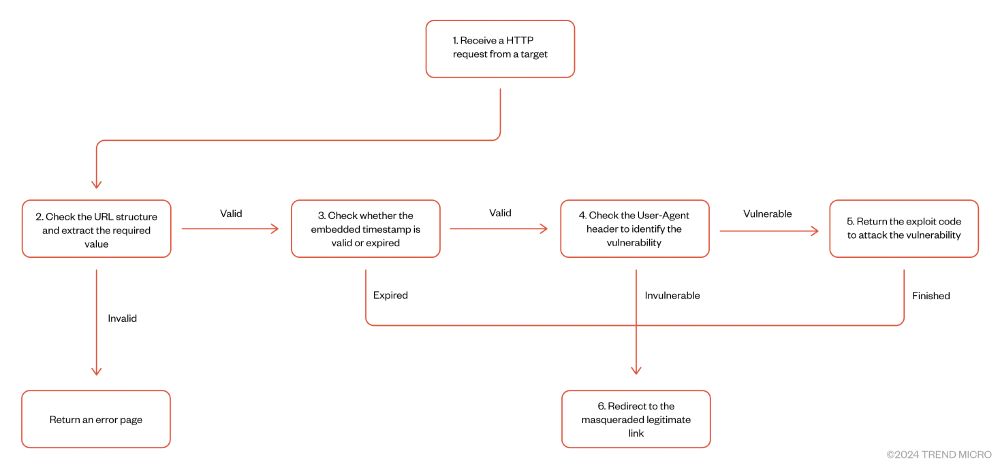
Validation flow that fingerprints the target by looking at user agent and delivering the proper exploit
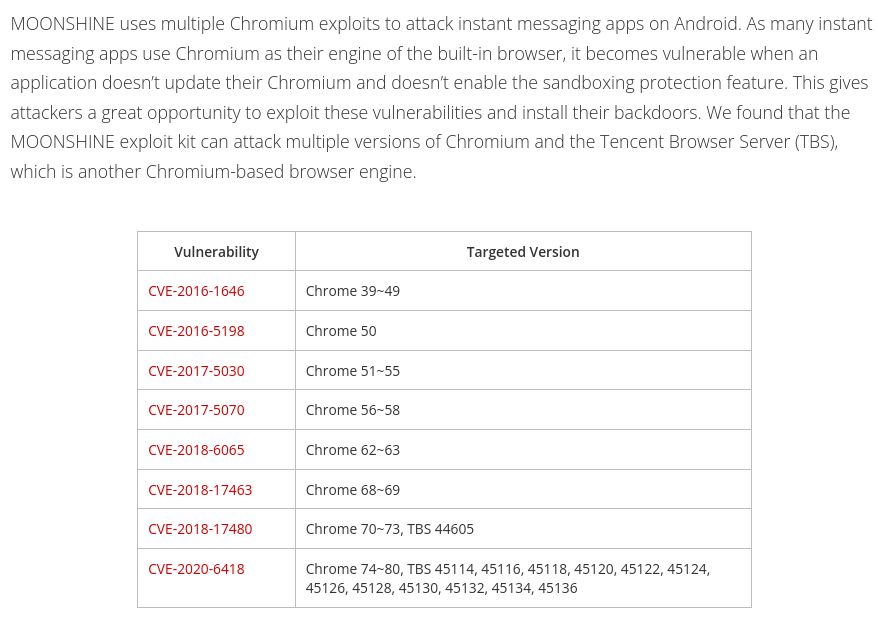
multiple Chrome vulnerabilities exploited in the third-party applications
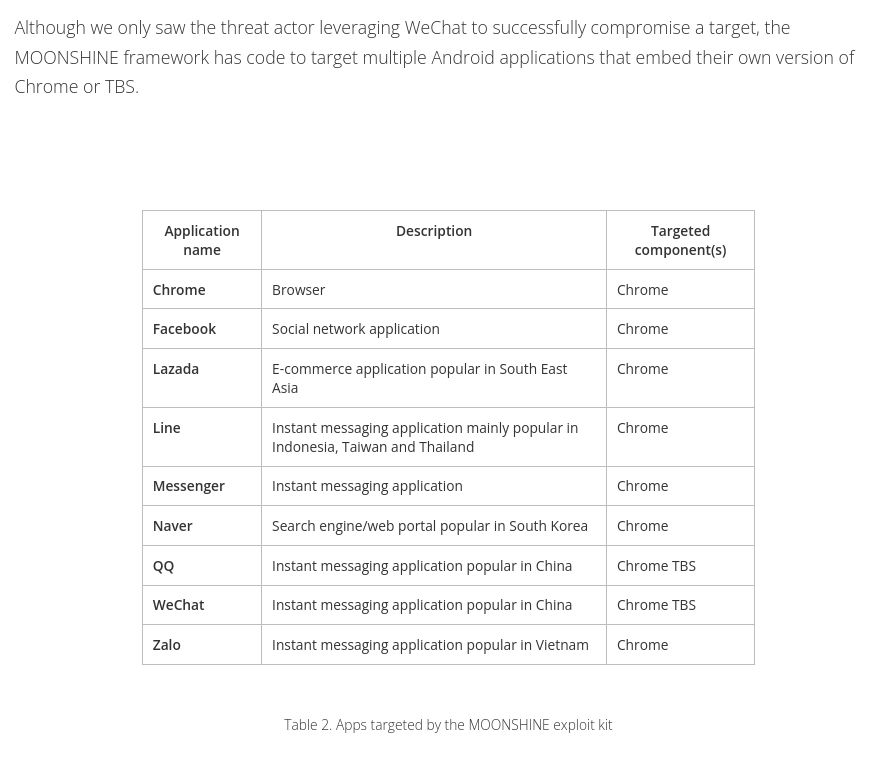
List of Android applications being targeted
Most are very popular in South East Asia
Our latest report presents Earth Minotaur, a threat actor targeting Tibetans and Uyghurs using Moonshine, an exploitation framework for Android apps described in 2019 by
@citizenlab.ca
leveraging vulnerabilities in applications embedding old versions of Chromium trendmicro.com/en_us/resear...
05.12.2024 08:48 — 👍 12 🔁 7 💬 0 📌 2
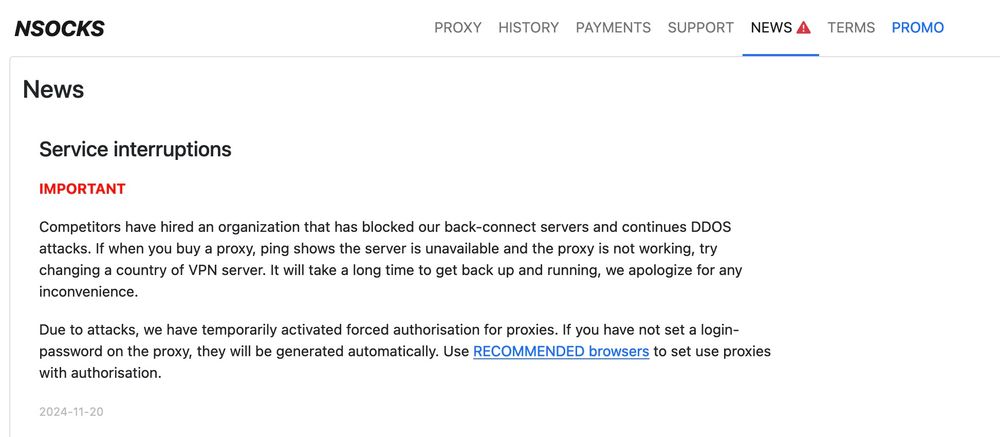
Nsocks provides an alternative explanation: "Competitors have hired an organization that has blocked our back-connect servers and continues DDOS attacks." Nsocks now also mandates authentication for their SOCKS5 entrance nodes (which was not the case previously - security by obscurity)
26.11.2024 13:01 — 👍 0 🔁 0 💬 0 📌 0
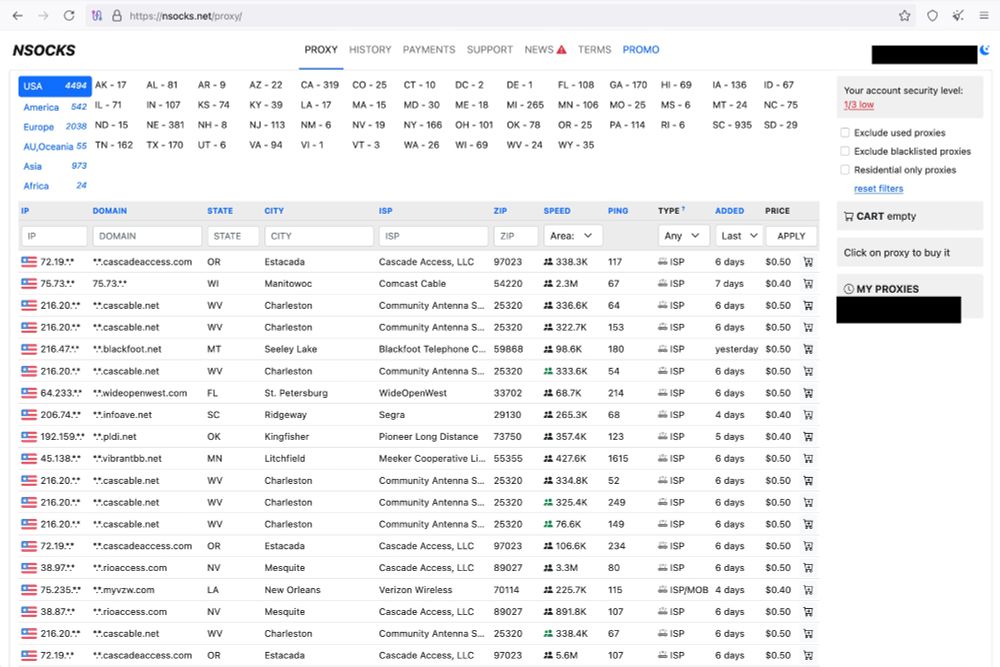
One week ago Lumen/Shadowserver sinkholed Water Barghest C&Cs. Nsocks (alleged seller of Ngioweb bots) apparently suffers from this: US proxies down to 4494 (was 14037), EU proxies down to 2038 (was 9092). I expected a faster recovery. Still expect Water Barghest will make their botnet more robust.
26.11.2024 12:53 — 👍 2 🔁 1 💬 1 📌 0

Inside Water Barghest’s Rapid Exploit-to-Market Strategy for IoT Devices
Water Barghest automated each step between finding vulnerable IoT devices to offering them for rent on a commercial residential proxy provider. Water Barghest's infrastructure was used to exploit Cisco IOS XE devices with a 0-day in October 2023. Read more here: www.trendmicro.com/en_us/resear...
19.11.2024 09:09 — 👍 1 🔁 0 💬 0 📌 0
Security information portal, testing and certification body.
Organisers of the annual Virus Bulletin conference.
Security researcher @ Cisco Talos. / Ex-Google TAG / Black Hat & HITCON review board / Organiser of Rhacklette.
Security & Privacy. Data Protection. Research & Development. Engineering. Analyst. Policy. W3C. Consultant. Author. King’s College London/War Studies. me@lukaszolejnik.com
lukaszolejnik.com/books
blog.lukaszolejnik.com
techletters.substack.com
Fighting Disinformation since 2022.
Soups: https://vatniksoup.com/
Debunk of the Day: https://vatniksoup.com/en/topics/debunk-of-the-day/
Support our work: https://vatniksoup.com/en/support-our-work/
Official Bluesky page of the 780th Military Intelligence Brigade (Cyber). The Army's only offensive cyberspace operations brigade (following, re-posts, and links ≠ endorsement).
Principal Threat Analyst - Google Threat Intelligence Group
Manager at Microsoft Threat Intelligence Center (MSTIC). Adjunct Faculty at Georgetown University. Penn State Alum. Tweets are my own.
Technologist @ Human Rights Watch (previously Amnesty, Citizen Lab)
Malware, Threats, Online Investigations, Disinformation, Human Rights and silly memes.
On Mastodon: tek@todon.eu
Also on https://maynier.eu/
Threat Researcher @TrendMicro,OSINT Researcher
Malware Researcher @ @esetresearch.bsky.social
macOS Threat and Detections Researcher @ Jamf
Verified parody account
Theins.press editor-in-chief
The Insider is a Russia-focused, independent media outlet. We're fully committed to investigative journalism and to debunking fake news.
theins.press/en
Threat researcher at Trend Micro mostly focused on APT
Lawyer working on human rights, technology, spyware, litigation, Russia and Eastern Europe.
Currently Senior Tech-Legal Counsel at Access Now. Formerly OSINT investigator and prosecutor.
oh great, now I’m on bluesky






















