
E voi, che cane avete? (continua⬇️ )
#canotipi #cani #cane #cana
@cdzeno.bsky.social
Security Researcher @nozominetworks




E voi, che cane avete? (continua⬇️ )
#canotipi #cani #cane #cana
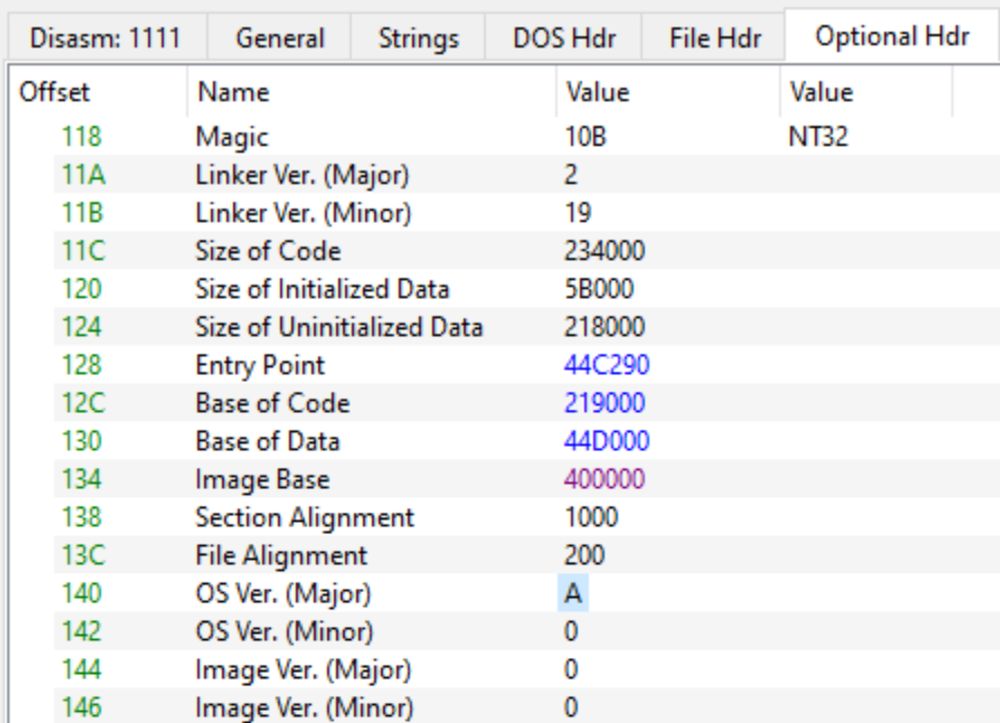
A small demo/tutorial on unpacking executables with #PEsieve and #TinyTracer: hshrzd.wordpress.com/2025/03/22/u...
- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims

I’ve posted a detailed explanation of why the claimed ESP32 Bluetooth chip “backdoor” is not a backdoor. It’s just a poor security practice, which is found in other Bluetooth chips by vendors like Broadcom, Cypress, and Texas Instruments too. https://darkmentor.com/blog/esp32_non-backdoor/
09.03.2025 12:49 — 👍 57 🔁 34 💬 7 📌 3
Great article about Apple's 🍎 Exclaves & Conclaves that provides a high-level overview and then dives into technical details implemented in XNU 👀
randomaugustine.medium.com/on-apple-exc...
THIS IS HUGE! Researchers at Stanford University have developed a dual-antibody treatment that remains effective against ALL SARS-CoV-2 variants by targeting a less-mutable part of the virus. This breakthrough could lead to longer-lasting therapies that OUTPACE viral evolution. 🧪🧵⬇️
09.03.2025 16:00 — 👍 29957 🔁 7882 💬 587 📌 723
Tarlogic found a "backdoor" im the ESP32 chips:
bleepingcomputer.com/news/security/undocumented-commands-found-in-bluetooth-chip-used-by-a-billion-devices
Broadcom & Cypress chips have the same HCI "backdoor" allowing to write to the Bluetooth chip's RAM. This feature is used for firmware patches.
The 3rd episode of our #OffensiveRust series, "Streamlining vulnerability research with #IDAPro and #Rust", is here! @raptor introduces new tools to assist with reverse engineering and vulnerability research, based on @HexRaysSA IDA and @binarly_io idalib […]
25.02.2025 06:40 — 👍 2 🔁 3 💬 0 📌 0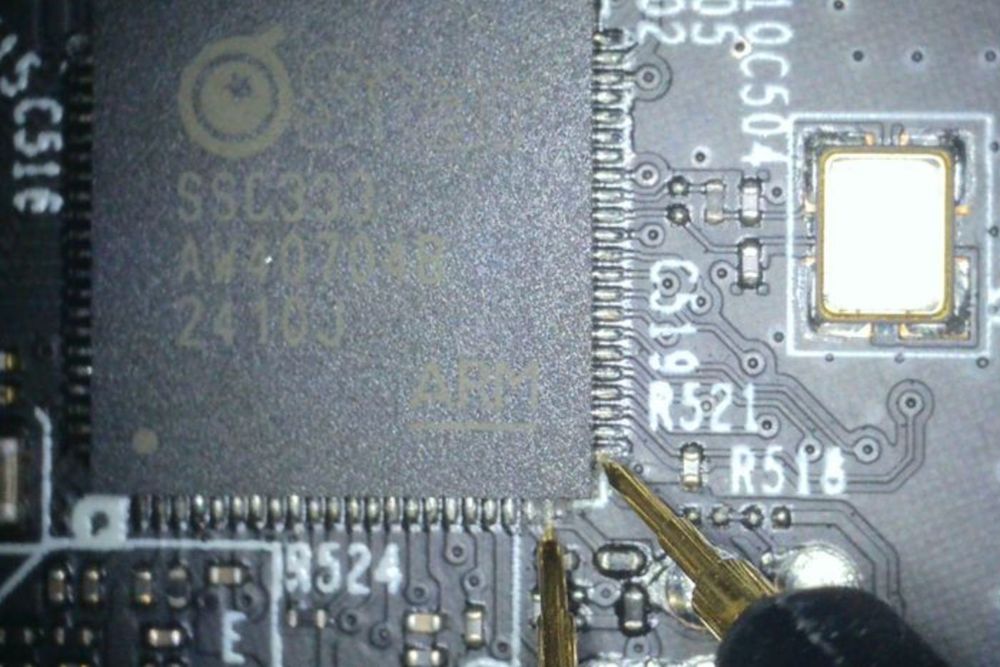
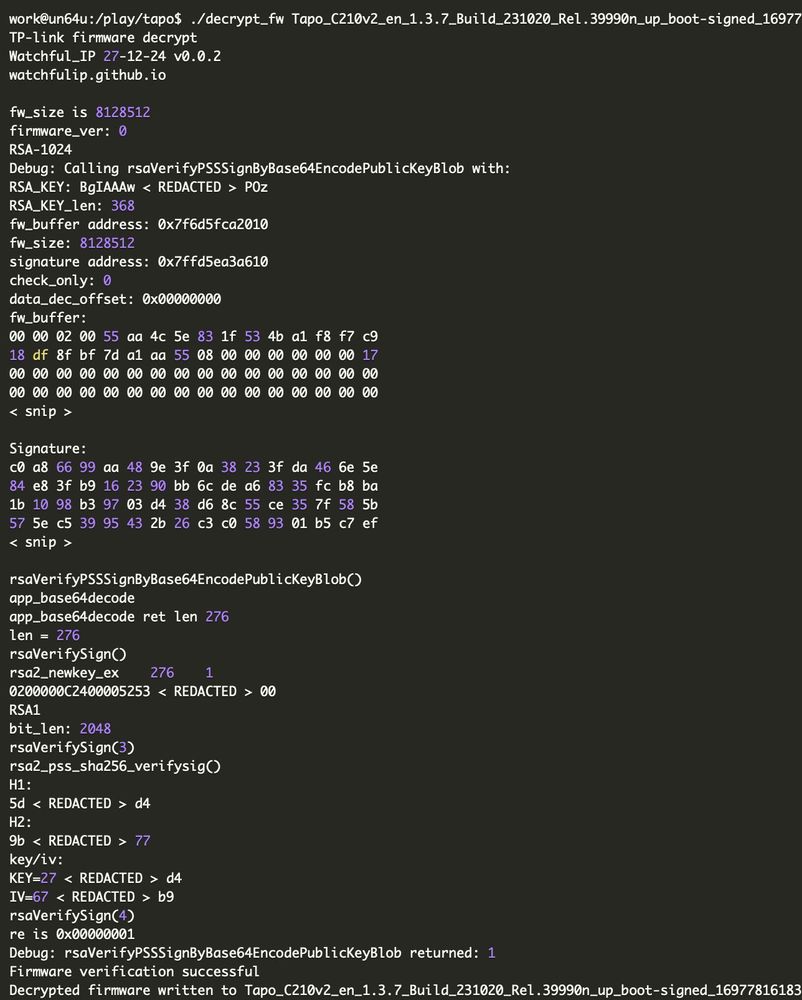
TP-Link (Tapo) C210 V2 cloud camera: bootloader vulnerability and firmware decryption
watchfulip.github.io/28-12-24/tp-...
#embedded #infosec

“Decompiling Mobile Apps With AI Language Models” by @trufae.bsky.social at @nowsecure.bsky.social www.nowsecure.com/blog/2025/01...
29.01.2025 17:54 — 👍 12 🔁 6 💬 1 📌 0[RSS] Linux Kernel TLS Part 1
u1f383.github.io ->
Original->
All videos from The 38th Chaos Communication Congress (38C3) 2024:
media.ccc.de/b/congress/2...
#cybersecurity #informationsecurity #hacking #exploitation #iOS #android #apple #exploitation #reverseengineering #vulnerability

Example LLM prompt from “From One Thousand Pages of Specification to Unveiling Hidden Bugs: Large Language Model Assisted Fuzzing of Matter IoT Devices”
“From One Thousand Pages of Specification to Unveiling Hidden Bugs: Large Language Model Assisted Fuzzing of Matter IoT Devices”
With a focus on the Matter network protocol, walks through the process of using an LLM to transform a human-readable spec into something a fuzzer can leverage.
Hello new (fuzzing) followers! I haven’t done much fuzzing recently unfortunately but here’s an example of past work I’m happy to talk about: mhlakhani.com/static/pdf/F...
Still hope to get back to it one day. But for now I’m still in the security / systems space (and dabbling in AI)
Microsoft just released a tool that lets you convert Office files to Markdown. Never thought I'd see the day.
Google also added Markdown export to Google Docs a few months ago.
github.com/microsoft/markitdown
 30.11.2024 15:06 — 👍 37 🔁 12 💬 2 📌 0
30.11.2024 15:06 — 👍 37 🔁 12 💬 2 📌 0

I'm launching a new website: sdk.blue - a list of all libraries/SDKs for building things on #ATProto, grouped by language 🙂
If I forgot anything important, or you have an ATProto/Bluesky library that you think would be a good fit there (or if I should remove anything), please send me a PR :) #atdev
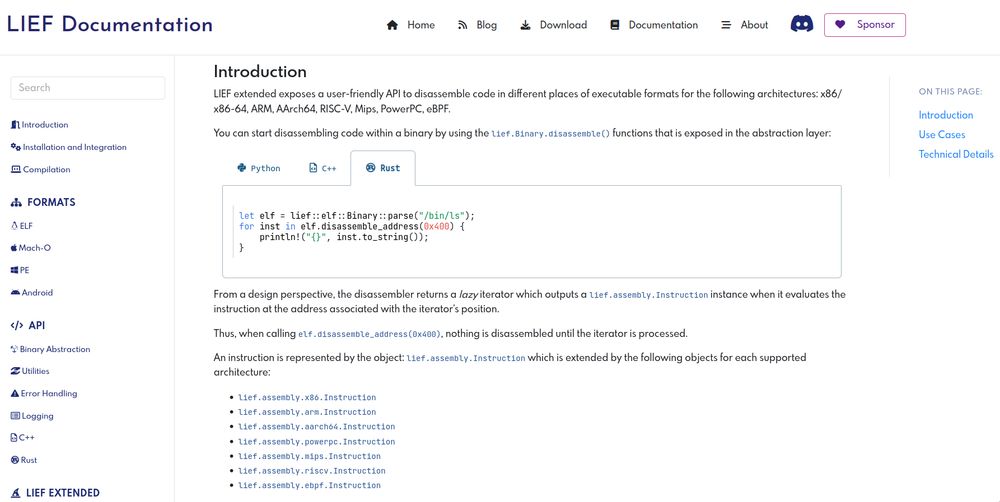
LIEF Disassembler API based on LLVM MC
So for my first post on Bluesky, I'm happy to share that LIEF (extended) is now providing an API to disassemble code (backed by the LLVM MC layer).
This disassembler is integrated with other functionalities
like dyldsc or DWARF info.
You can checkout lief.re/doc/latest/e... for the details.
Slides for my @ekoparty talk "Advanced Fuzzing
With LibAFL"
- >
docs.google.com/presentation...
C Harness to #LibAFL
https://github.com/v-p-b/libfuzzer_kfx/blob/main/C2LIBAFL.md
I nice part of making an archive of my Twitter posts is that I realize I wrote stuff like this o.O #fuzzing
Original->
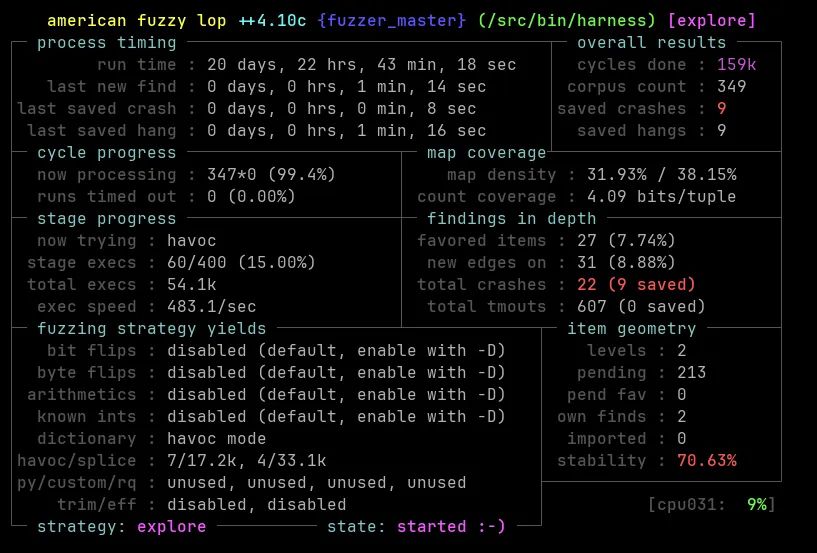
Just discovered 10 memory corruption vulnerabilities in the popular Mongoose Web Server (11k stars on GitHub) by fuzzing its embedded TLS stack protocol with @aflplusplus.bsky.social. More technical details here: www.nozominetworks.com/blog/hunting...
#fuzzing #afl #vulnerability #tls
My DM is open if you’re interested in more technical details about the research :)
19.11.2024 18:45 — 👍 0 🔁 0 💬 0 📌 0
Just discovered 10 memory corruption vulnerabilities in the popular Mongoose Web Server (11k stars on GitHub) by fuzzing its embedded TLS stack protocol with @aflplusplus.bsky.social. More technical details here: www.nozominetworks.com/blog/hunting...
#fuzzing #afl #vulnerability #tls

Physics vs. Magic xkcd.com/2904
08.03.2024 22:09 — 👍 2422 🔁 514 💬 27 📌 33