A nice workaround against my YARA rule.
kuwaitist.github.io/posts/Patchi...
ocdsec
@ocdsec.bsky.social
🏴☠️ 💚 🇺🇦 computer tester | 603,628 km²
@ocdsec.bsky.social
🏴☠️ 💚 🇺🇦 computer tester | 603,628 km²
A nice workaround against my YARA rule.
kuwaitist.github.io/posts/Patchi...
A Chinese think tank has published a hit piece on seven cybersecurity and policy experts specializing in Chinese cyber operations
www.guancha.cn/xinzhiguanch...

Ukraine Hackers Attacking Russian Aerospace Companies and Other Defence-Related Sectors
02.12.2025 20:24 — 👍 4 🔁 1 💬 0 📌 0
LibIPC is a simple Crystal Palace shared library for inter-process communication, based on Named Pipes.
github.com/pard0p/LibIPC
Slides from Alexander Bluhm (bluhm@)'s talk "Update on #OpenBSD Networking Performance Improvements" today at #EuroBSDcon 2025.
www.openbsd.org/papers/eurob...
Netscaler vulnerability was exploited as zero-day for nearly two months (CVE-2025-6543)
12.08.2025 16:10 — 👍 1 🔁 1 💬 0 📌 1
Hundreds of GitHub Malware Repos Targeting Novice Cybercriminals Linked to Single User
06.06.2025 23:44 — 👍 3 🔁 2 💬 0 📌 0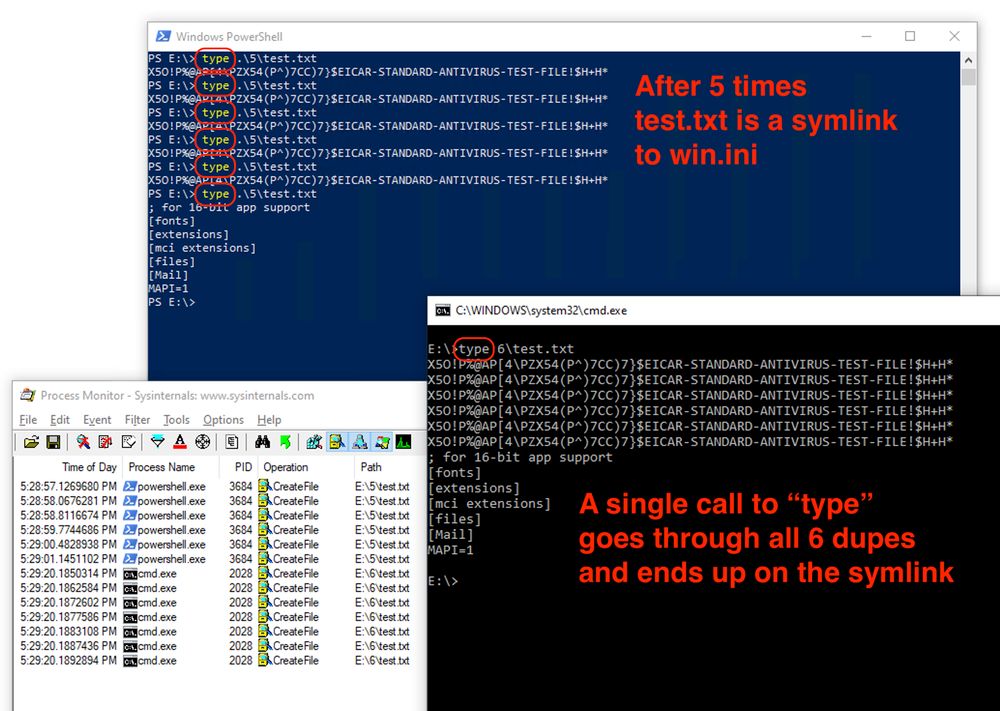
Powershell: after 5 "type .\5\test.txt" calls, the test.txt file is a symlink to win.ini CMD: A single "type .\6\test.txt" call results in every single file being printed, including the final win.ini symlink
From over at the Bad Place:
There's an interesting NTFS symlink attack outlined here:
https://dfir.ru/2025/02/23/symlink-attacks-without-code-execution/
Basically, if an NTFS filesystem is corrupted in a way to provide duplicate file names, Windows will […]
[Original post on infosec.exchange]

cybercrime zeroday faded tee
cybercrime
but its bigger
and on both sides.
Well there are lots of people who have been treating Google and many others like that for ages, and this is why the solutions are already out.
You lose convenience the deeper you go, but the solutions are there.
well they exist ^^
01.03.2025 21:51 — 👍 0 🔁 0 💬 1 📌 0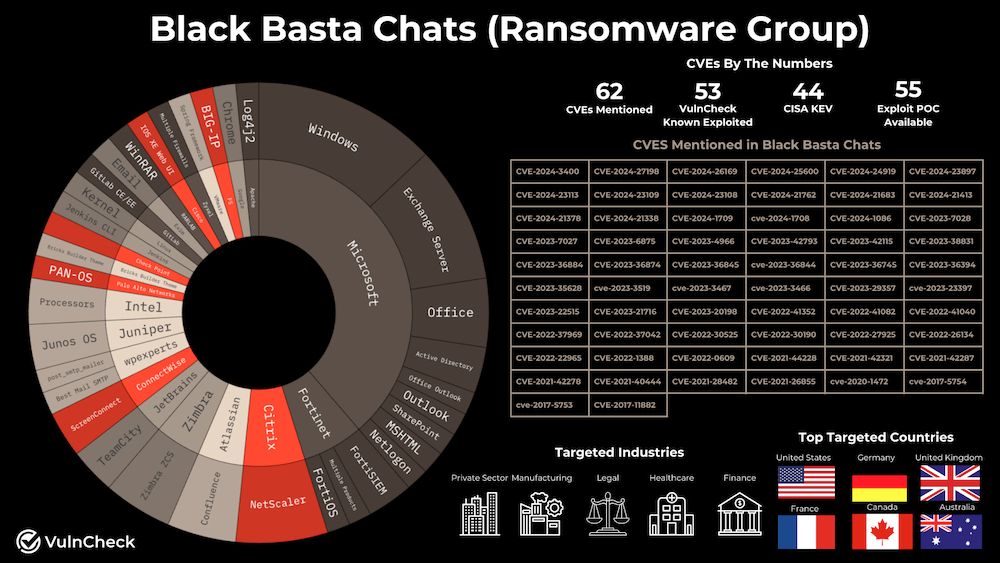
VulnCheck has extracted and made a list of all the CVEs mentioned in a recent leak from the internal Matrix chat server of the BlackBasta ransomware group.
The list includes 62 vulnerabilities.
VulnCheck says the group focuses on CVEs with already public exploits
vulncheck.com/blog/black-b...
I cannot overstate the value of being in community with other activists right now. It is what gives me the strength to get up in the morning and fight fascism.
24.02.2025 20:53 — 👍 1830 🔁 204 💬 63 📌 20
"Over the course of the GitVenom campaign, the threat actors behind it have created hundreds of repositories on GitHub that contain fake projects with malicious code"
Campaign delivers an infostealer, obviously. The threat-du-jour these days
securelist.com/gitvenom-cam...
I just finished our #shmoocon talk on container security. Here's my seccomp bpf disassembler and diffing tool.
github.com/antitree/sec...
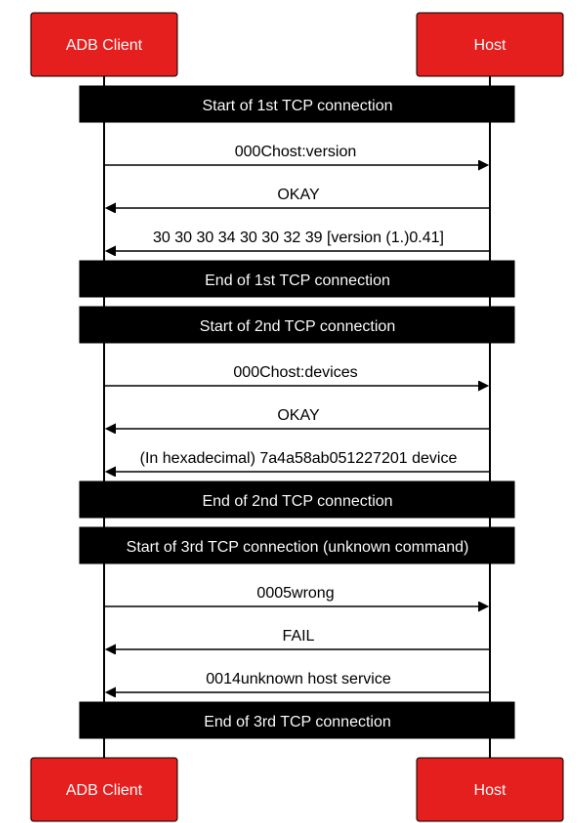
Diving into ADB protocol internals:
part 01: www.synacktiv.com/publications...
part 02: www.synacktiv.com/en/publicati...
#adb #mobile #protocol #informationsecurity #cybersecurity #reverseengineering

These are some really nice blog posts regarding algo confusion bugs in JWT by @pentesterlab.com pentesterlab.com/blog/jwt-alg... & pentesterlab.com/blog/another... nice one @snyff.pentesterlab.com!
22.12.2024 19:06 — 👍 20 🔁 5 💬 1 📌 0
Ruble to fall to 200 per dollar: Russian economist warns of approaching catastrophe – media
читайте подробнее на сайте "Диалог.UA": www.dialog.ua/business/306...

Wow, a fairly serious auth bypass in Next.js, a super popular frontend framework:
"If a Next.js application is performing authorization in middleware based on pathname, it was possible for this authorization to be bypassed."
securityonline.info/...
The #OpenBSD Foundation is currently at ~$230,280 (65%) raised of the $350,000 goal for their 2024 Fundraising Campaign, and it's nearly the end of December. 🐡
www.openbsdfoundation.org/campaign2024...
www.openbsdfoundation.org/donations.html
Donations fund events for developers, infra. costs.
I did a blog instead of working on my projects again. This time a maldev blog talkin' about PE runtime decryption and other ways to be an asshole to the analyst. amethyst.systems/blog/posts/v... #infosec #malware
07.12.2024 20:18 — 👍 27 🔁 10 💬 0 📌 0
The #OBTS day 2 livestream is on!
www.youtube.com/watch?v=Nm0z...