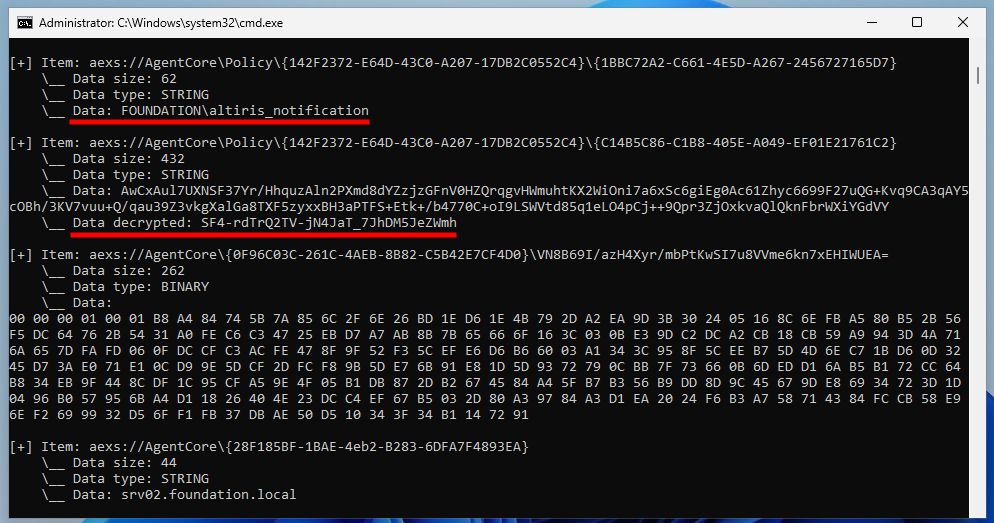
Screenshot showing the output of the proof-of-concept tool "SMAStorageDump", where ACCs are dully decrypted.
🆕 New blog post!
"Offline Extraction of Symantec Account Connectivity Credentials (ACCs)"
Following my previous post on the subject, here is how to extract ACCs purely offline.
👉 itm4n.github.io/offline-extr...
#redteam #pentesting
15.06.2025 16:33 — 👍 11 🔁 4 💬 3 📌 0
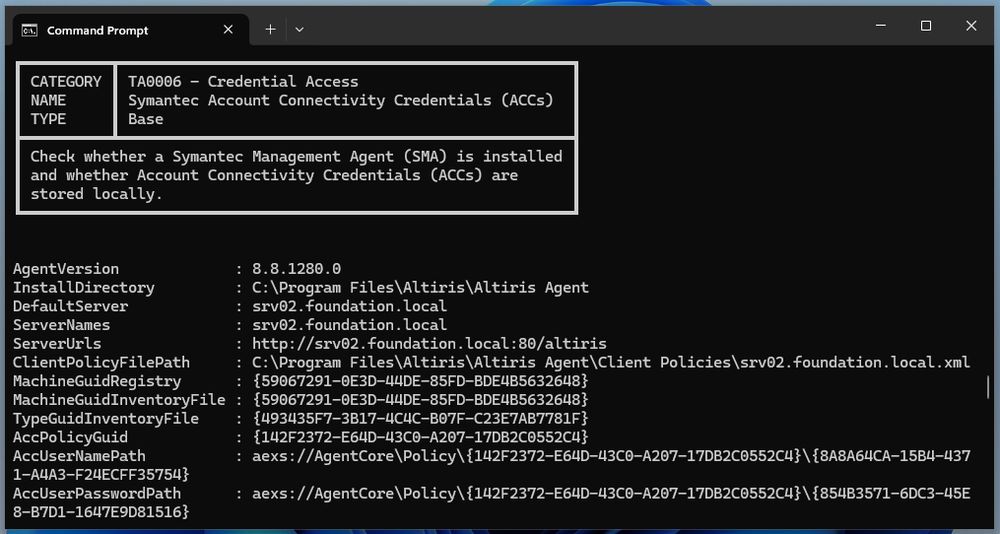
Sample output of PrivescCheck showing the information collected about the Symantec Management Agent (SMA).
🆕 New blog post!
"Checking for Symantec Account Connectivity Credentials (ACCs) with PrivescCheck"
This blog post is not so much about PrivescCheck, but rather brings additional insight to the original article published by MDSec on the subject.
👉 itm4n.github.io/checking-sym...
#redteam
11.06.2025 15:46 — 👍 8 🔁 4 💬 0 📌 0
Hijacking the Windows “MareBackup” Scheduled Task for Privilege Escalation – SCRT Team Blog
🆕 New blog post! It's a rather short one, nothing crazy. Just wanted to share a random finding I made recently. 🤷♂️
'Hijacking the Windows "MareBackup" Scheduled Task for Privilege Escalation'
👉 blog.scrt.ch/2025/05/20/h...
#pentest #pentesting #redteam #windows #privilegeescalation
28.05.2025 07:08 — 👍 8 🔁 5 💬 0 📌 0
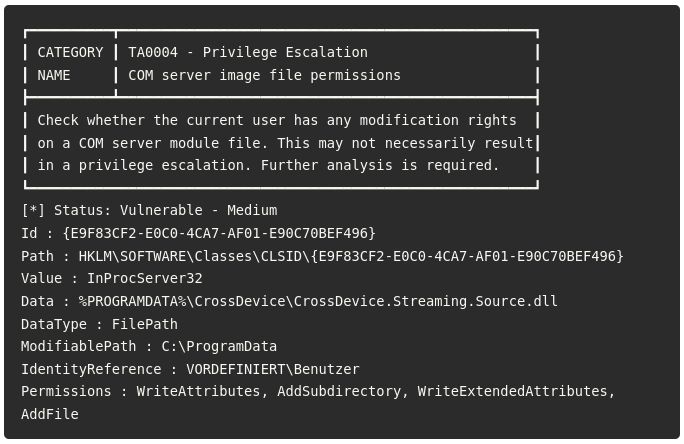
Another example of a Windows 0-day found with PrivescCheck. Congrats to Compass Security for investigating the issue and exploiting it. 👏
blog.compass-security.com/2025/04/3-mi...
15.04.2025 12:41 — 👍 14 🔁 6 💬 1 📌 0
You're absolutely right! 😬
Thanks for your message. I'll do that. 🙂
This whole DLL thing is essentially a dirty hack anyway.
20.02.2025 08:56 — 👍 1 🔁 0 💬 0 📌 0
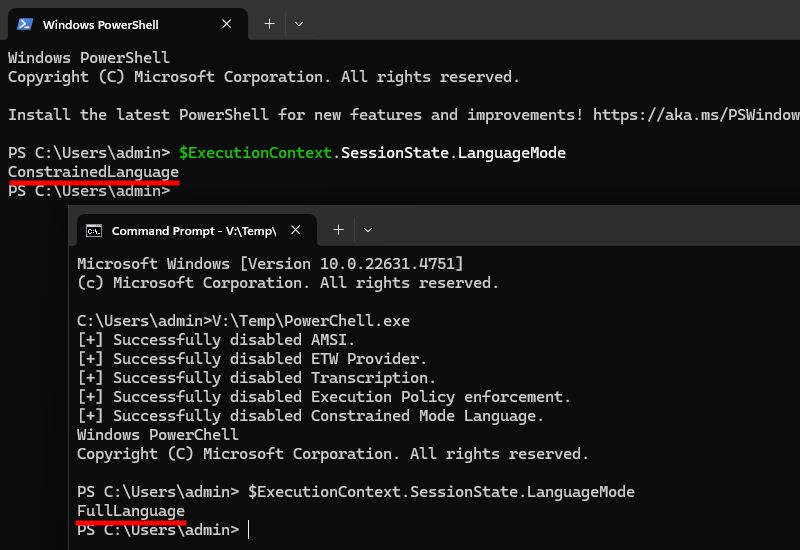
Screenshot showing the execution of the proof-of-concept named PowerChell in comparison to a typical PowerShell prompt. In particular, it shows that PowerChell is able to bypass the Constrained Language Mode (CLM).
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
19.02.2025 09:13 — 👍 43 🔁 19 💬 2 📌 2

Windows BitLocker -- Screwed without a Screwdriver
Breaking up-to-date Windows 11 BitLocker encryption -- on-device but software-only
Really great blog post about bypassing BitLocker using "PXE soft reboot" (even if PXE boot is disabled in the BIOS).
"Windows BitLocker -- Screwed without a Screwdriver"
👉 neodyme.io/en/blog/bitl...
👉 media.ccc.de/v/38c3-windo...
20.01.2025 10:03 — 👍 15 🔁 7 💬 1 📌 0
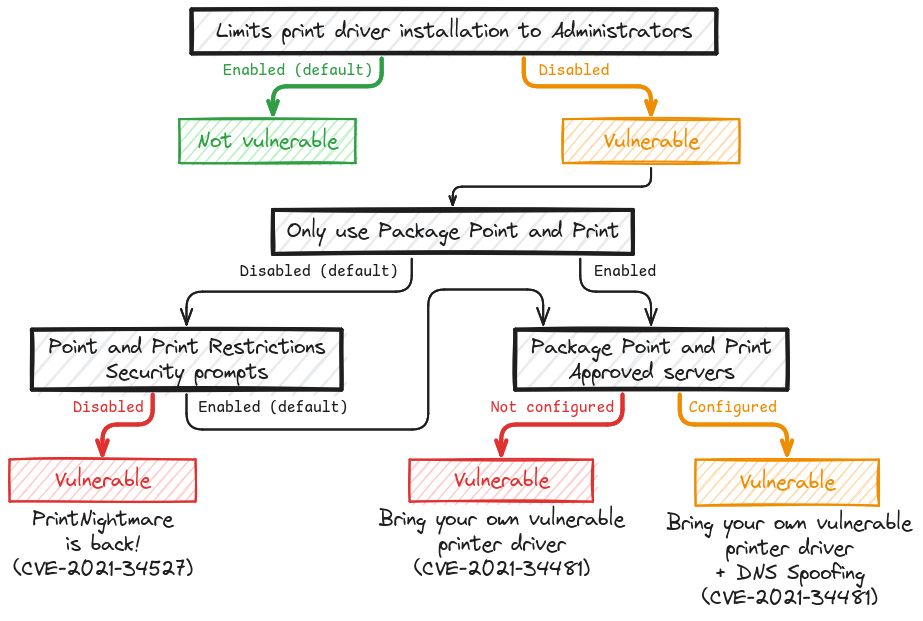
Diagram representing the various Windows Point and Print configurations that reintroduce the PrintNightmare exploit variants.
I updated the diagram representing the different Point and Print configurations and their exploitation on my blog.
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞
04.12.2024 17:42 — 👍 18 🔁 8 💬 0 📌 0
August 13, 2024—KB5041585 (OS Builds 22621.4037 and 22631.4037) - Microsoft SupportYour Privacy Choices Opt-Out Icon
Interestingly enough, MS disabled the "Use my Windows user account" checkbox when connecting to Wi-Fi on the lock screen to address CVE-2024-38143 in the August Patch Tuesday.
This change completely remediates the "Airstrike" attack as well. 🤯
support.microsoft.com/en-us/topic/...
03.12.2024 20:45 — 👍 1 🔁 2 💬 0 📌 0

I'm glad to release the tool I have been working hard on the last month: #KrbRelayEx
A Kerberos relay & forwarder for MiTM attacks!
>Relays Kerberos AP-REQ tickets
>Manages multiple SMB consoles
>Works on Win& Linux with .NET 8.0
>...
GitHub: github.com/decoder-it/K...
25.11.2024 17:31 — 👍 63 🔁 43 💬 3 📌 0
Thanks!
Yes, I already thought about doing something like this, and I already took a look at cross-references to find the offset of the object. I didn't take the time to check older versions though, there might be some diffs to take into consideration. There is clearly more to work on. :)
13.11.2024 08:22 — 👍 1 🔁 0 💬 0 📌 0
Exploiting KsecDD through Server Silos – SCRT Team Blog
🆕 New blog post! "Exploiting KsecDD through Server Silos"
In my latest mini research project, I've been working with my teammate @PMa1n (X) on extending the work of @floesen_ (X) on the KsecDD driver. I'm thrilled to finally share the results.
👉 blog.scrt.ch/2024/11/11/e...
11.11.2024 13:40 — 👍 12 🔁 7 💬 1 📌 0
A trick, the story of CVE-2024-26230
"A Trick, The Story of CVE-2024-26230" by k0shl
Write-up about the discovery and exploitation of a UAF vulnerability in the Windows Telephony service + CFG bypass leading to local privilege escalation. 🔥🔥🔥
whereisk0shl.top/post/a-trick...
10.04.2024 18:57 — 👍 3 🔁 0 💬 0 📌 0
GitHub - itm4n/PrivescCheck: Privilege Escalation Enumeration Script for Windows
Privilege Escalation Enumeration Script for Windows - itm4n/PrivescCheck
🆕 New PrivescCheck extended check!
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
11.03.2024 20:29 — 👍 4 🔁 2 💬 0 📌 0
Work like hell,
Share all you know,
Abide by your handshake,
Have fun. - Dan Geer
Pwn2Own 20{22,23,24,24.5}, i look for 0-Days but i find N-Days & i chase oranges 🍊
https://summoning.team/
Just a biologist that loves to break cyber-stuff. Adepts of 0xCC founder.
Hacker at outsidersecurity.nl. Researches Entra ID, AD and occasionally Windows security. I write open source security tools and do blogs/talks to educate others on these topics. Blog: dirkjanm.io
Creators of BloodHound | Experts in Adversary Tradecraft | Leaders in Identity Attack Path Management
Team Lead Kovert AS, previously Red Team TrustedSec, terrible creator of InfoSec content 📹Opinions are my own and not the views of my employer.
Security enthusiast, likes Windows internals, AD & Azure.
Blogging at: https://csandker.io
Red Brain, Blue Fingers
Malware Analysis, Reverse Engineering, Threat Hunting, Detection Engineering, DFIR, Security Research, Programming, Curiosities, Software Archaeology, Puzzles, Bad dad jokes
https://www.hexacorn.com/blog/
hexacorn@infosec.exchange
"I'm interested in all kinds of astronomy."
https://scrapco.de
Mostly cross-posting from Fediverse: @buherator@infosec.place
I like making computers misbehave. Does stuff at http://specterops.io.
Github: https://github.com/leechristensen
Mastodon: @tifkin_@infosec.exchange
Offsec stuff @Caisse Nationale de l'Assurance Maladie || Interested in Malware 🤓 || Nerd stuff here https://alice.climent-pommeret.red/