Different prints!
29.11.2025 12:56 — 👍 1 🔁 0 💬 0 📌 0Ange
@angealbertini.bsky.social
Reverse engineer, file formats expert. Corkami, CPS2Shock, PoC||GTFO, Sha1tered, Magika... Security engineer @ Google. He/him.
@angealbertini.bsky.social
Reverse engineer, file formats expert. Corkami, CPS2Shock, PoC||GTFO, Sha1tered, Magika... Security engineer @ Google. He/him.
Different prints!
29.11.2025 12:56 — 👍 1 🔁 0 💬 0 📌 0I'm looking for a 39C3 ticket for a relative.
No scammer please ;)
To check if a file starts with MZ or GIF, just use file/libmagic.
You don't need AI or Magika for that.
TrID has a lot of heuristics, but a lot of false positives.
Magika is useful in different ways, across binary and source types, and is quite fast. But not fit for weird files.
Magika is a fast file type identifier that covers many file types, binary formats or source texts.
It's not made to detect adversarial attacks.
It's useful for different things that classic binary scanning can't do at this speed.
Magika was trained on all file types with enough available samples.

Weird files are out of scope of Magika. It just wasn't trained on them.
It's trivial to inject some data in a file and keep it functional (w/ my tool Mitra, for example).
So take a JPG, inject a lot of JavaScript data, and ...guess what ?
Check it out: github.com/corkami/mitra

Of course, it's possible to create weird files that will fool Magika and other tools.
Polymocks, polyglots...
I made quite a few - check my CCC talk last year:
speakerdeck.com/ange/fearsom...
Magika uses the first and last kilobytes of the files.
That way, if the file is slightly corrupted, the filetype might still be properly identified.
Magika returns several file types if needed.
It's one of its advantages, but a double-edged sword.
So file contents are used to determine the file type.
To check if the file starts with '\x7FELF', 'MZ' or 'GIF', you don't need IA.
But some file formats don't start with a clear 'magic' signature at offset zero.
And what if you also want to tell apart C++, RUST and HTML ?
No magic for source files
To identify file types, the worst way are file extensions:
the extension is stored in the filesystem entry, not in the file content.
It can be lost, modified, variable...
Almost all file formats are known under several file extensions:
.JPG/.JPEG, .ZIP/.APK/.DOCX, .EXE/.DLL, .ELF/.SO ...

In the process, I also studied in depth other file type identifiers, and I've been contributing to most of them before, including LibMagic, TrID...
Check my talk: speakerdeck.com/ange/overvie...
Hi newcomers: I've been contributing to Magika since 2023 (it became public in 2024).
Some clarifications regarding the recent Magika release...
Magika is useful in its own way, and used in production.
The recent Rust release doesn't change how Magika is fundamentally working.
Is there nowadays a better content extractor from PDF than the classic ‘pdftotext’ ?
Something (maybe ML-driven) that would handle tables, rows of text and formulas ?
I love the little details:
Drop and run, piezo sound…

Public blog post:
opensource.googleblog.com/2025/11/anno...
Source: github.com/google/magika

Magika 1.0 is released, available in Rust, TypeScript and Python, and supporting more than 200 file types.
07.11.2025 09:57 — 👍 5 🔁 1 💬 1 📌 0If you’re into malware analysis, you should really give Malcat a try.
A great all-in-one tool with hex and structure views, disasm and decomp, integrated Yara, python scripting, similarities scanning...
Definitely worth trying!
Is there a good source for non-malicious executables? categorized and with some variety, across platforms, languages...?
08.10.2025 15:28 — 👍 3 🔁 0 💬 2 📌 0
Brand new paper with Roxane Cohen, Robin David (both from @quarkslab.bsky.social ) and Florian Yger on obfuscation detection in binary code doi.org/10.1007/s411... We show that carefully selected features can be leveraged by graph neural networks to outperform classical solutions.
30.09.2025 17:03 — 👍 12 🔁 7 💬 1 📌 1Apple Preview 11.0 (macOS 15.5) does crash while opening gist.github.com/nst/373748f2... as x.pdf (malformed ICC profile).
[com.apple.Preview] CoreGraphics assert(cs != NULL) failed in img_pixels_for_destination: colorspace missing
CoreGraphics/Images/CGSImage.c:4029: failed assertion `cs != NULL'

Color coded display of a zlib compressed version of this post's text, rendered by the flateview demo
lynn.github.io/flateview/
Impressive. Visualizer of zlib (gzip) - paste in a paragraph or two of text.
Reminds me of @angealbertini.bsky.social's binary file-format illustrations (google 'corkami').
I have been learning more about PDFs than I really wanted to for maybe the absolutely most funny reason possible - letting agency forgery: mjg59.dreamwidth.org/73317.html
24.09.2025 22:25 — 👍 128 🔁 33 💬 6 📌 2Enter Sandbox 30: Static Analysis gone wrong
www.hexacorn.com/blog/2025/09...

Grab your @phrack copy (beautiful 150 page color print) at @nullcon’s registration booth!
05.09.2025 06:54 — 👍 3 🔁 0 💬 0 📌 0
You can do that with my Mitra tool with the `--force` parameter (for arbitrary content injection) on ~40 standard formats (which covers many more subformats).
github.com/corkami/mitra

Bash script injection in a JPEG file:
hackers-arise.com/the-one-man-...
Today I have a more serious topic than usual, please consider reposting for reach:
My wife and I are urgently looking for a specialist in neuropediatrics or a similar field for our autistic child with a diagnosed, but not further specified, movement disorder [1/4]
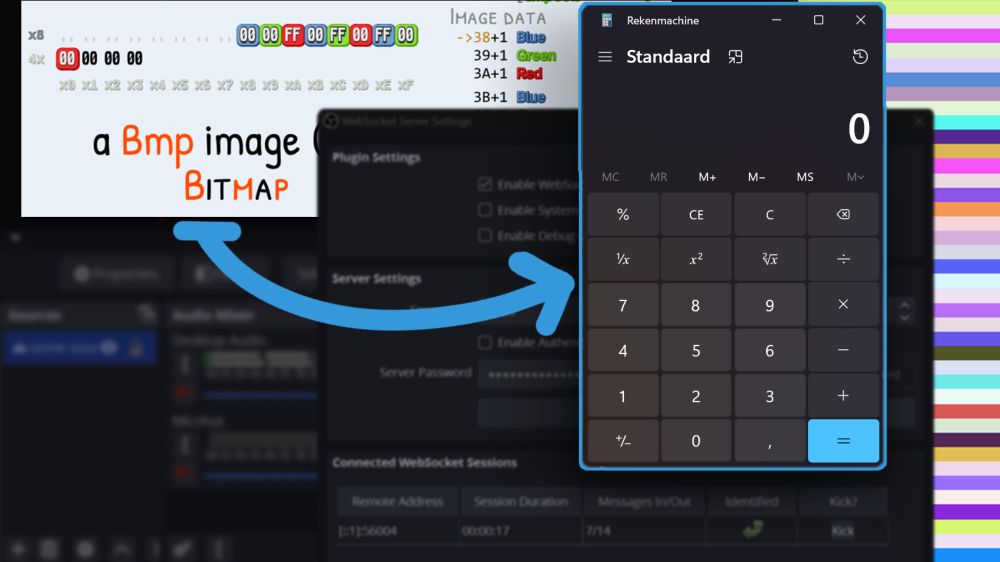
Just pushed a new frontend for my site, and a new post!
This one's about an tricky file write vulnerability on Windows in OBS. By crafting an image with very specific pixels, we can plant a backdoor on your PC all from an attacker's site by misconfiguring:
jorianwoltjer.com/blog/p/resea...
C'est surprenant effectivement, mais peut-être le PDF 1.7 contient de nombreuses informations supplémentaires (accessibilité, XML...) plus récentes.
02.06.2025 17:18 — 👍 2 🔁 0 💬 0 📌 0I had a minor printing problem with an article where the last few letters of the longest lines of text were missing.
It was a small mental puzzle every 5-10 lines to guess the missing letters.
An interesting exercise to stay focused throughout the article.
Fun and informative, as always, thank you!
25.04.2025 06:28 — 👍 1 🔁 1 💬 0 📌 0