I’ve spent 2 solid hours doing bug bounty and I still haven’t made $200k.
Can someone tell me what I’m doing wrong?
#bugbountytips
20.04.2025 23:09 — 👍 4 🔁 0 💬 1 📌 0

I Don’t Want My Devs to Become Hackers! - PentesterLab's Blog
Discover why encouraging developers to learn ethical hacking boosts security, reduces bugs, and fosters a proactive security culture in your organization.
Think teaching devs to hack is risky?
In reality, a bit of hacking knowledge helps them spot vulnerabilities early and build stronger apps.
Discover why having devs with a 'hacker mindset' is a win for security:
pentesterlab.com/blog/why-dev...
13.02.2025 18:21 — 👍 2 🔁 1 💬 0 📌 0
From now on, I'll call any snippet of vulnerable code shared on Social Media as
"Security Code Review Porn"
It gives the wrong expectations about what real code review actually involves.
07.02.2025 02:44 — 👍 4 🔁 0 💬 0 📌 0
Common OAuth Vulnerabilities · Doyensec's Blog
Common OAuth Vulnerabilities
Articles worth reading discovered last week:
🤝 blog.doyensec.com/2025/01/30/o...
☠️ www.feistyduck.com/newsletter/i...
📚 pathonproject.com/zb/?871f0933...
And as always, it’s in our blog: pentesterlab.com/blog/researc...
#PentesterLabWeekly
02.02.2025 21:50 — 👍 6 🔁 3 💬 0 📌 0
If you’re in the area, here’s my schedule:
* OWASP Bay Area (Feb 11)
* CactusCon in Mesa/Phoenix (Feb 14 & 15)
* OWASP Los Angeles (Feb 18)
* OWASP Orange County (Feb 20)
I’d love to connect—if you’re nearby, please stop by and say hello (and maybe grab some swag)!
29.01.2025 23:33 — 👍 0 🔁 0 💬 0 📌 0
I’m excited to share that in a few weeks I’ll be heading to the US for a series of talks and workshops focused on security code review and JWT—and I’ll be bringing some
@pentesterlab.com swag along too!
29.01.2025 23:33 — 👍 5 🔁 2 💬 1 📌 0
 28.01.2025 03:12 — 👍 9 🔁 1 💬 0 📌 0
28.01.2025 03:12 — 👍 9 🔁 1 💬 0 📌 0

...
22.01.2025 09:35 — 👍 2 🔁 0 💬 1 📌 0
YouTube video by Tiny Club Berlin
joernchen - Friday 13th @ 1°C
Have a great weekend and enjoy some tunes:
youtu.be/j_Md8_7mhOU
04.01.2025 13:46 — 👍 6 🔁 3 💬 1 📌 0
Golang: because hackers haven’t given up on SQL injection in 2024...
30.12.2024 00:48 — 👍 11 🔁 1 💬 1 📌 0
Thank you! ☺️☺️☺️
23.12.2024 06:09 — 👍 1 🔁 0 💬 0 📌 0
Someone replied that I had the wrong handle for James, I fixed it but I cannot find the original message.
Thanks to whoever raised it.
18.12.2024 21:56 — 👍 1 🔁 0 💬 1 📌 0
I put together a VERY limited (for now) list of web hackers in a Starter pack:
go.bsky.app/9uay4Ad
A lot of people are missing (I will try to add more as I find them) but make sure you follow people already in the list!
18.12.2024 00:54 — 👍 31 🔁 14 💬 3 📌 0
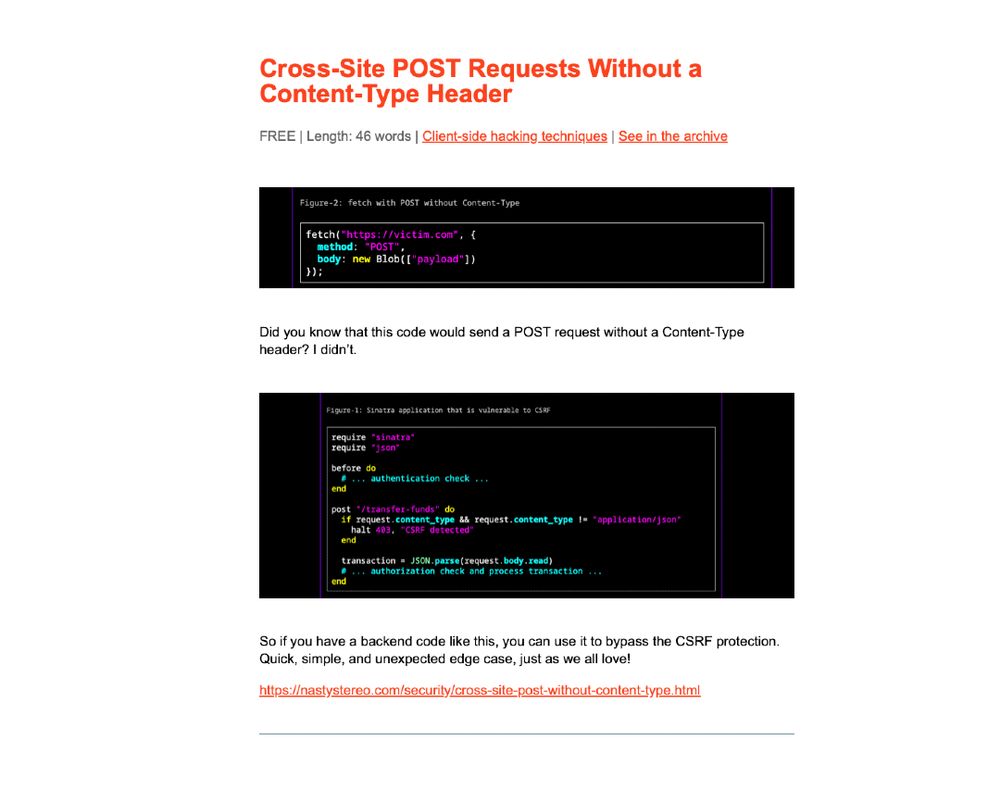
Cross-Site POST Requests Without a Content-Type Header by @lukejahnke
https://nastystereo.com/security/cross-site-post-without-content-type.html
#BBRENewsletter85
16.12.2024 15:05 — 👍 2 🔁 1 💬 0 📌 0
❤It is why I am a huge fan and student of @pentesterlab.com and @snyff.pentesterlab.com
😱This lab show me that I was wrong, since several years, recommending to dev teams using a hash of the token as identifier in a revocation list.
🥰Now, I know the correct recommendation to provide.
#appsec #jwt
14.12.2024 16:31 — 👍 7 🔁 2 💬 0 📌 0

PentesterLab Blog: Reading Between the Lines: A Guide to Thoughtful Learning in Security
Discover how to extract deeper insights from security content by going beyond surface-level understanding. This post explores a reflective approach to learning, helping you uncover patterns, improve y...
Want to level up your learning in security? 🚀 Stop scrolling and start reflecting.
'Reading Between the Lines' challenges you to dig deeper:
1️⃣ What can I learn from this?
2️⃣ What patterns apply elsewhere?
3️⃣ Why didn’t I spot this?
The real breakthroughs come when you ask the right questions. 💡
👇
12.12.2024 03:16 — 👍 5 🔁 4 💬 1 📌 0
 08.12.2024 21:28 — 👍 18 🔁 6 💬 2 📌 1
08.12.2024 21:28 — 👍 18 🔁 6 💬 2 📌 1
Yes, just a one off :/
07.12.2024 08:20 — 👍 1 🔁 0 💬 1 📌 0
I didn't want to spoil the solution
05.12.2024 22:21 — 👍 0 🔁 0 💬 0 📌 0
The real question now is what kind of automation do you have in place to discover this code change/commit 😉
05.12.2024 21:59 — 👍 0 🔁 0 💬 0 📌 0
These are simple issues, but they illustrate how, by thinking of vulnerabilities as patterns rather than code, you can move from one language to another.
05.12.2024 21:57 — 👍 4 🔁 1 💬 1 📌 0
printf 'first**|uname' | ruby hack.rb
05.12.2024 21:53 — 👍 0 🔁 0 💬 2 📌 0
knuck if you buck
https://n0.lol
Security Geek. We build Thinkst Canary - https://canary.tools
hacker, poster, weird machine mechanic
https://chompie.rip
I teach cryptography at Johns Hopkins. https://blog.cryptographyengineering.com
Full of passionate intensity.
Director of Research at @portswigger.net
Also known as albinowax
Portfolio: https://jameskettle.com/
Co-founder, security researcher. Building an attack surface management platform, @assetnote.io
Co-Founder @shielder.com
CTF Player jbz.team
Cliff Jumping Lover (23mt max so far)
🇨🇦 Pen tester, ethical Hacking, always learning and always hacking.. posts are my own.
Fullstack dev & Hacker, training ethical hackers how to hack & web devs to secure their apps! CTO at https://hackinghub.io and Director at https://bsidesexeter.co.uk
Friendly neighborhood cybersecurity guy | expect infosec news, appsec, cloud, dfir. | Long Island elder emo in ATX.
vulnu.com <- sign up for my weekly cybersecurity newsletter
Web App (mostly) Hacker @NetSPI | Cybersecurity Educator | Content Creator | Ex-Brit | Links: http://linktr.ee/tib3rius (he/him) 🇺🇸 A mostly unserious person.
Still your mom’s favorite hacker!
Security Researcher and Software Engineer at GitHub Security Lab
Security Engineer at Zellic, a.k.a vakzz when doing bug bounties and CTFs with Perfect Blue - https://devcraft.io


 28.01.2025 03:12 — 👍 9 🔁 1 💬 0 📌 0
28.01.2025 03:12 — 👍 9 🔁 1 💬 0 📌 0









 08.12.2024 21:28 — 👍 18 🔁 6 💬 2 📌 1
08.12.2024 21:28 — 👍 18 🔁 6 💬 2 📌 1