
New @economist.com article cites @interseclab.bsky.social 's @opentechfund.bsky.social-supported research into how Chinese firm Geedge Networks exports internet-control technology.
www.economist.com/internationa...
@interseclab.bsky.social
InterSecLab is a specialized digital security laboratory with advanced capabilities in digital forensics, research and threat intelligence.

New @economist.com article cites @interseclab.bsky.social 's @opentechfund.bsky.social-supported research into how Chinese firm Geedge Networks exports internet-control technology.
www.economist.com/internationa...

The translation, other #GreatFirewallExport reports, interviews, and other updates are available on interseclab.org/research/the...
30.10.2025 15:15 — 👍 1 🔁 0 💬 0 📌 0
Anonymity Networks Community is a group, based in Taiwan, focused on "Anonymous Networks" and "Internet Freedom", aiming to raise public awareness about the importance of internet freedom through tools like Tor, Tails, and OONI.
Learn more: anoni.net/docs/en/about/
We would like to express our sincere gratitude to the Anonymity Networks Community @anoni.net for their support to spreading our report further and help communities to understand the implications of these findings.
30.10.2025 15:15 — 👍 0 🔁 0 💬 1 📌 0Their goal with this translation is to ensure this critical information is widely understood and discussed across diverse cultural and linguistic contexts, fostering greater dialogue and collaboration in collectively addressing the challenges of the digital age.
30.10.2025 15:15 — 👍 0 🔁 0 💬 1 📌 0
Readers in Chinese-speaking regions can now gain deeper insights into our findings on Geedge's suite!
Our report “The Internet Coup” is now available in Traditional Chinese (using Taiwanese terminology), thanks to the translation by @anoni.net. #GreatFirewallExport
anoni.net/docs/report/...

PBS did a great section on the Great Firewall Export, that we published together with @papertrailmedia.de @interseclab.bsky.social @justiceformyanmar.org @theglobeandmail.com @torproject.bsky.social and us @amnesty.org. www.pbs.org/newshour/sho...
23.10.2025 19:39 — 👍 27 🔁 14 💬 0 📌 1
Our post reveals what this shift means: when repression becomes a service that can be bought, civil liberties now depend on what states can afford to purchase.
Read more: interseclab.org/can-mass-sur... #GreatFirewallExport
What makes this leak significant is the technical detail showing how these systems track users across platforms, adapt to defeat Tor, and enable retroactive identification of activities that were legal at the time.
16.10.2025 15:07 — 👍 0 🔁 0 💬 1 📌 0This connects to stories many outlets have covered: Myanmar's post-coup crackdown, new laws criminalizing VPNs, and the global surveillance market that emerged as Western export restrictions tightened.
16.10.2025 15:07 — 👍 0 🔁 0 💬 1 📌 0Geedge Networks, founded by the architect of China's censorship system, is commercializing surveillance as a managed service — complete with maintenance, upgrades, and custom blocking rules.
16.10.2025 15:07 — 👍 0 🔁 0 💬 1 📌 0
Mass surveillance has become a consumer product. Our new blog post explores what 100,000+ leaked documents reveal about a new frontier in state control — and what it means for protecting privacy and digital security.
Read more: interseclab.org/can-mass-sur... #GreatFirewallExport
This connects to stories many outlets have covered: Myanmar's post-coup crackdown, new laws criminalizing VPNs, and the global surveillance market that emerged as Western export restrictions tightened.
16.10.2025 14:56 — 👍 0 🔁 0 💬 0 📌 0Geedge Networks, founded by the architect of China's censorship system, is commercializing surveillance as a managed service — complete with maintenance, upgrades, and custom blocking rules.
16.10.2025 14:56 — 👍 0 🔁 0 💬 1 📌 0
Interestingly, Geedge is developing the rules of censorship for and with the client governments. A list found inside the leak contains 281 applications to be blocked. Among them are VPNs, Tor/Orbot, the tool Psiphon, and – depending on the country – also messengers like Signal and Whatsapp.
29.09.2025 10:41 — 👍 2 🔁 0 💬 0 📌 0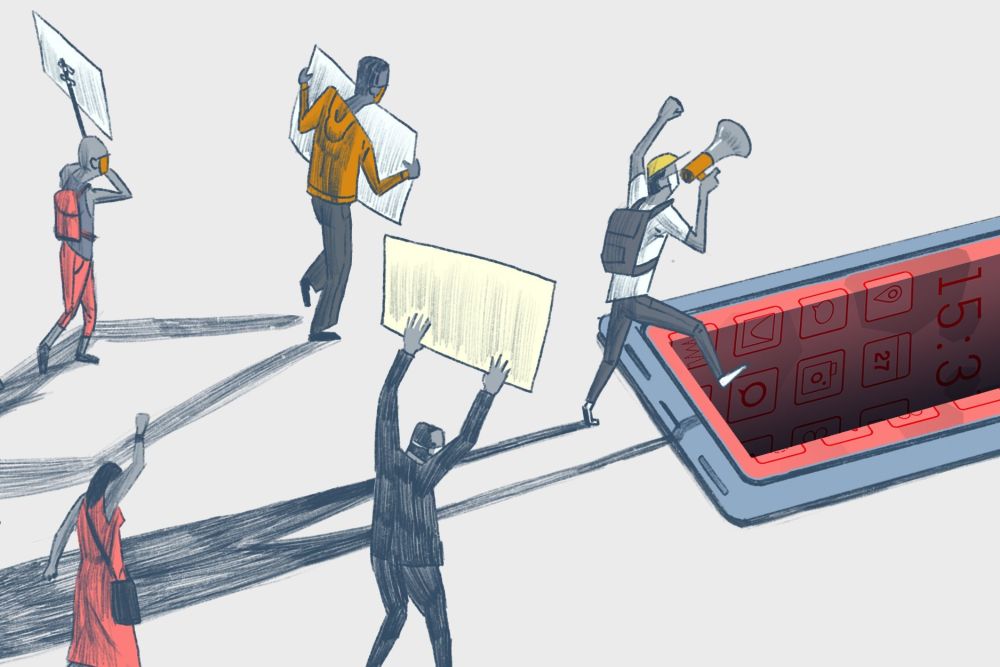
Am Dienstag, dem 30. September, laden @amnesty.de und @hauberlin.bsky.social zum Event „Digital Surveillance: How States Are Spying on the Resistance“. Mehr Infos und Tickets zur Paneldiskussion: www.hebbel-am-ufer.de/programm/pde...
26.09.2025 14:30 — 👍 11 🔁 6 💬 1 📌 0
Registration:
www.hebbel-am-ufer.de/en/programme...
Workshops and Digital Security Clinic for Civil Society (drop in) are free!
If you cannot afford the evening panel ticket (8 Euro) but would like to join, reach out to me or @chorlitz.bsky.social.

Weißer Text auf schwarzem Grund: Digital Surveillance: How States are Spying on the Resistance, mit Logos von HAU und Amnesty International
Join us?
💥Workshops w/ @papertrailmedia.de @amnesty.de @interseclab.bsky.social
💥Dig. Security Clinic w/ @accessnow.org, @pressefreiheit.bsky.social&Tact. Tech
💥Panel w/ @donncha.is @sophieintveld.bsky.social @davidyambio.bsky.social @anjaosterhaus.bsky.social
&Art by @forensicarchi.bsky.social
Other provinces affected are Fujian and Jiangsu. The Geedge activity inside China shows high levels of trust that the company enjoyed by the Chinese government. The leak also indicates a close relation between Geedge and Mesalab, an academic research laboratory at the Chinese Academy of Sciences.
25.09.2025 23:43 — 👍 0 🔁 1 💬 0 📌 0Previous research by the GFW Report already indicated the existence of provincial firewalls across China with different levels of surveillance and censorship. The Geedge leak confirms that. Xinjiang, the home of 11 million Uyghurs, seems to serve as a testing ground for Geedge's new features.
25.09.2025 23:43 — 👍 0 🔁 1 💬 1 📌 0The unknown client: A24 is the codename for a client country we were not able to identify. Geedge’s naming convention suggests that the country starts with A and collaboration started in 2024. The implementation of Geedge tools at A24 has been in its early stages when the documents were leaked.
23.09.2025 13:29 — 👍 3 🔁 1 💬 0 📌 0Some ISPs that collaborated with Geedge have received investment from Western institutions. Frontiir (Myanmar) has been supported by the governments of Denmark, Norway and the UK. Safaricom (Ethiopia) received investment from the World Bank Group and British International Investment, among others.
23.09.2025 13:29 — 👍 2 🔁 1 💬 1 📌 0Complicity of Western companies: The Geedge suite relies on the DRM software “Sentinel HASP” to manage its subscriptions. This product is owned by the French aerospace and defense giant Thales Group. Thales confirmed the cooperation, but stated that Geedge does not rely on Sentinel to function.
23.09.2025 13:29 — 👍 2 🔁 1 💬 1 📌 0The Tigray internet shutdown lasted 2 years and was one of the longest in history. It presumably enabled and concealed serious war crimes by hindering people to publish news on social media.
23.09.2025 13:29 — 👍 2 🔁 1 💬 1 📌 0
#TheInternetCoup: In Ethiopia, the Geedge suite have been in use in the same time period as the Tigray civil war took place. Geedge began operating in Ethiopia in 2021, one year before the Tigray ceasefire in 2022.
23.09.2025 13:29 — 👍 3 🔁 3 💬 1 📌 0We proudly want to present you our analysis of the stalkerware Celular007 that has been covered today by the Brazilian magazine Piauí.
18.09.2025 18:15 — 👍 2 🔁 4 💬 0 📌 0
We advise you not to share the password for your phone and computer with anybody. This should be more normalized as a healthy practice among couples. If you feel you may be affected by stalking, we recommend you the following guide: interseclab.org/interseclab-...
18.09.2025 17:32 — 👍 0 🔁 0 💬 0 📌 0
InterSecLab has conducted an in-depth analysis of the stalkerware: interseclab.org/research/unv...
Based on our research, we demand the authorities to effectively ban Celular007 and similar apps, to protect the privacy of all individuals.
Celular007 can listen to calls, determine the location, read notifications and messages, access apps such as Whatsapp, Facebook or Instagram, and use the camera remotely. With these permissions, it turns the victim’s phone into an omni-present spy that accesses even the most intimate parts of life.
18.09.2025 17:32 — 👍 1 🔁 1 💬 1 📌 0Its 2-day trial period only requires an email address, and the website offers detailed instructions for non-technical users. Installation requires physical access to the victim’s device, though. Once installed, the app remains invisible and gains almost full control of the victim’s phone.
18.09.2025 17:32 — 👍 1 🔁 1 💬 1 📌 0