
PIC Development Crash Course
Some helpful content for writing position independent code.
Position Independent Code (PIC) Development Crash Course.
My July 2025 overview of PIC writing fundamentals.
Don't know why jump tables are bad? Got a __chkstk relocation error? Watch this video.
#GoodLuckAndHappyHacking
vimeo.com/1100089433/d...
16.07.2025 15:40 — 👍 9 🔁 4 💬 0 📌 1
ي
10.07.2025 13:59 — 👍 0 🔁 0 💬 0 📌 0

Potato exploits have been a cornerstone of local priv esc on Windows for years, but how & why do the inner starchy workings of the potatoes function?
Join @atomicchonk.bsky.social next week to understand Windows access tokens & their use in the Windows environment. ghst.ly/june-web-bsky
20.06.2025 16:55 — 👍 4 🔁 2 💬 0 📌 0
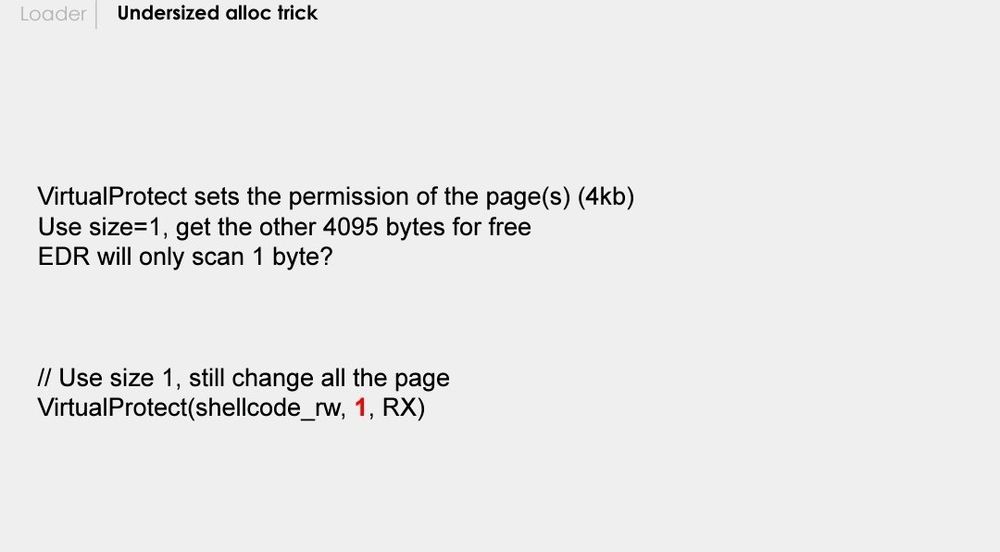
This is getting some attention today. Cool shellcode trick from:
My First and Last Shellcode Loader by @dobinrutis.bsky.social at HITB 2024.
H/T x.com/Jean_Maes_19...
01.04.2025 17:48 — 👍 2 🔁 2 💬 1 📌 0
Yo this is supercool
07.06.2025 15:08 — 👍 0 🔁 0 💬 0 📌 0
When James Forshaw post, you read 🫡
13.12.2024 11:47 — 👍 0 🔁 0 💬 0 📌 0

Snowblind: The Invisible Hand of Secret Blizzard
Hack the other group’s c2 infra to use for your own campaign 👌. Interesting
blog.lumen.com/snowblind-th...
05.12.2024 01:14 — 👍 0 🔁 0 💬 0 📌 0

EDR Silencers and Beyond: Exploring Methods to Block EDR Communication - Part 1
For red teams and adversary alike it’s important to stay hidden. As many companies nowadays have EDR agents deployed those agents are always in focus and tools like EDRSilencer or EDRSandblast use…
🛡️Windows Firewall and WFP are only two ways to silence an #EDR agent.
📢In my latest blog post I discuss another network based technique to prevent data ingest and ways to detect it.
And if you want even more, checkout part 2 released by @Cyb3rMonk Link in the post
01.12.2024 15:04 — 👍 21 🔁 10 💬 0 📌 0
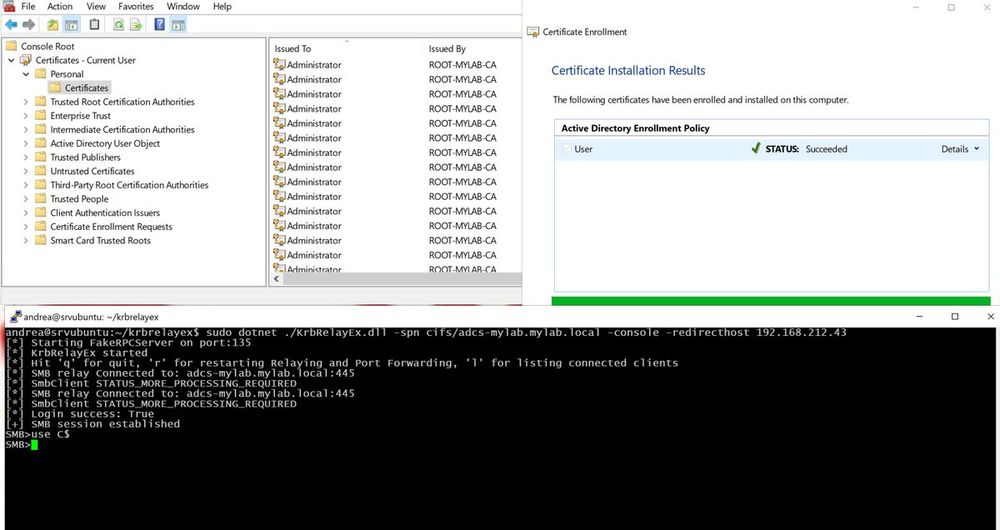
Relaying DCOM has always intrigued me, so I decided to dive in. Started with a MiTM attack using a fake DNS entry, targeting certificate requests to an ADCS server and relaying to SMB.
29.11.2024 21:42 — 👍 9 🔁 4 💬 1 📌 0
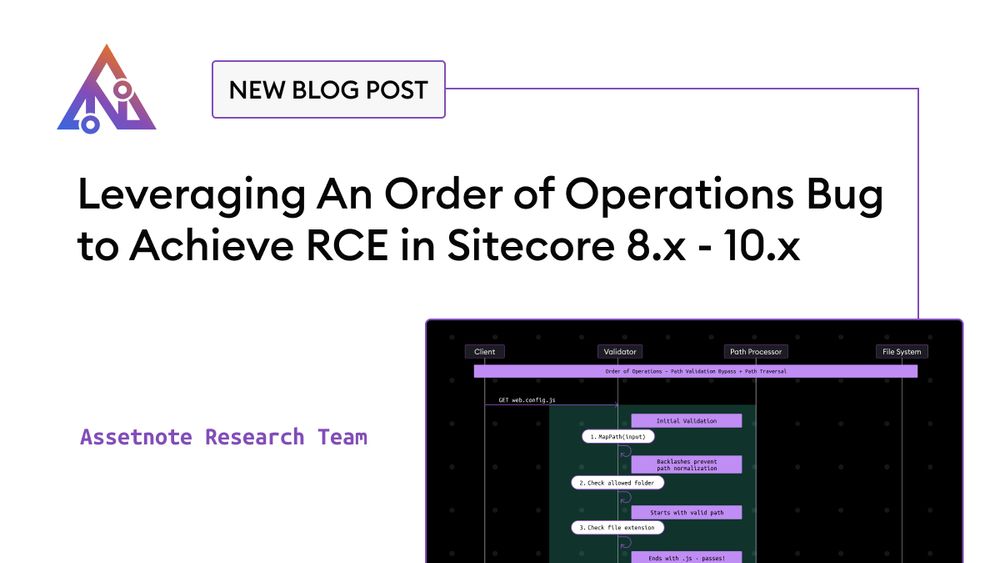
Earlier this year, Assetnote's Security Research team discovered a vulnerability in Sitecore XP (CVE-2024-46938) that can lead to pre-authentication RCE.
Order of operations bugs are one of my favorite types of bugs :) Write up and exploit script here: assetnote.io/resources/re...
22.11.2024 05:50 — 👍 51 🔁 25 💬 1 📌 0
Dipping sweet potatoes into hummus is kinda goated tbh
14.11.2024 00:53 — 👍 0 🔁 0 💬 0 📌 0
GitHub - itm4n/PrivescCheck: Privilege Escalation Enumeration Script for Windows
Privilege Escalation Enumeration Script for Windows - itm4n/PrivescCheck
🆕 New PrivescCheck extended check!
ℹ️ The script can now enumerate dangerous default file extension associations, such as '.bat' or '.wsh'.
⚠️ A manual review of the result is always recommended, but for the most part, it should be fine.
github.com/itm4n/Prives...
11.03.2024 20:29 — 👍 4 🔁 2 💬 0 📌 0
Principal Security Researcher and Pâtissier at @codewhitesec.bsky.social
Riding around in the breeze. Security Thinker. Hacker. USAF Veteran. https://aff-wg.org
Security research and breaking news straight from ESET Research Labs.
welivesecurity.com/research/
Defcon goon, Adversarial Architect. Photography, Driving, Blog and general purveyor of chaos. Metal/DnB Fan
Waitress turned Congresswoman for the Bronx and Queens. Grassroots elected, small-dollar supported. A better world is possible.
ocasiocortez.com
Detect, Defend, Defeat – Building robust #CyberResilience for organizations through advanced, future-proof #CyberSecurity solutions.
Lemmy: https://lemmy.ml/c/rocketmeup
Matrix: https://matrix.to/#/#rocketmeup:matrix.org
Telegram: https://t.me/rocketmeup
Security researcher, pentester
Maintainer of NetExec, DonPAPI, dploot, certsync, and all the stuff on https://github.com/zblurx
We are the Threat Intelligence and Malware Analysis team of
@SentinelOne
https://sentinellabs.com
https://labscon.io
The world’s most advanced, autonomous AI-powered cybersecurity platform. We empower the world to run securely, with leading organizations trusting us to Secure Tomorrow™. Secure your enterprise: http://sentinelone.com/request-demo/
Red Teamer @BHinfoSecurity. Implant Dev is my passion.
https://strikeready.com/blog.html
Download live malware samples mentioned here: https://github.com/StrikeReady-Inc/samples
If you prefer marketing (our product is great!) subscribe to our main page @strikeready.com
Wannabe security guy. Director @ Zero-Point Security.
Infosec professional, beverage snob, and fantasy book consumer. Vice President @ Atredis Partners. Forever terrified of Kithicor.
Co-founder, security researcher. Building an attack surface management platform, @assetnote.io
javascript:/*--></title></style></textarea></script></xmp><svg/onload='-/"/-/onmouseover=1/-/[*/[]/-alert(1)//'>
https://garethheyes.co.uk/#latestBook









