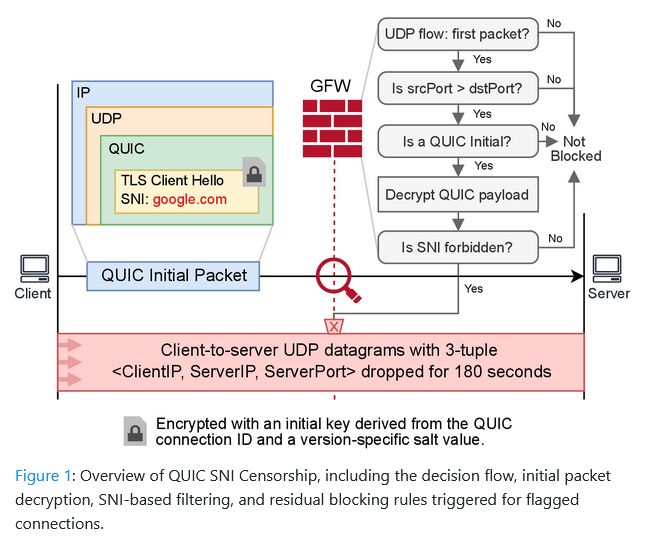
China has started filtering and censoring internet traffic taking place over the QUIC protocol.
The filtering started in April last year.
The Great Firewall now decrypts QUIC packets at scale and uses a separate blocklist for QUIC traffic, separate from its main filters
gfw.report/publications...
02.08.2025 22:31 — 👍 32 🔁 18 💬 0 📌 0
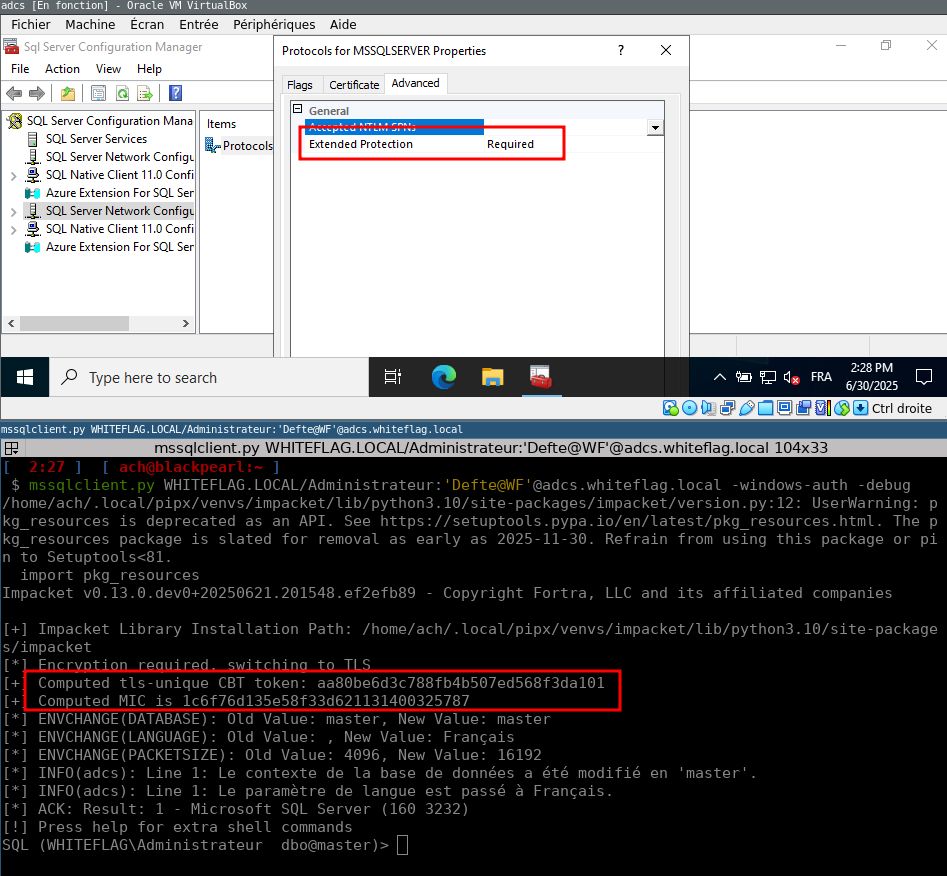
A screenshot of two windows. The top is a view of the Microsoft SQL management GUI showing that “Extended Protection” is enabled for NTLM authentication. The bottom is a terminal showing an invocation of Impacket’s mssqlclient.py successfully connecting using channel binding.
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (@Defte_ on the bird site), including instructions for reproducing the test environment yourself.
sensepost.com/blog/2025/a-...
31.07.2025 16:19 — 👍 9 🔁 6 💬 0 📌 1
BloodHound v8.0 is here! 🎉
This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID.
Read more from Justin Kohler: ghst.ly/bloodhoundv8
🧵: 1/7
29.07.2025 13:13 — 👍 13 🔁 10 💬 1 📌 1

Upcoming Conference Talks - PortSwigger Research
Find details of upcoming talks from the PortSwigger Research team. We also have research papers and recordings available from previous conferences and events.
Not at Black Hat / DEF CON? You can still join the mission to kill HTTP/1.1:
- Watch the livestream from #DEFCON at 16:30 PT on the 8th
- Read the whitepaper on our website
- Grab the HTTP Request Smuggler update & WebSecAcademy lab
Follow for updates & links. It's nearly time!
30.07.2025 14:50 — 👍 12 🔁 2 💬 0 📌 0

Entra Connect Attacker Tradecraft: Part 3 - SpecterOps
How Entra Connect and Intune can be abused via userCertificate hijacking to bypass conditional access and compromise hybrid domains
Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and conditional access bypass.
@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9
30.07.2025 17:01 — 👍 9 🔁 6 💬 1 📌 0
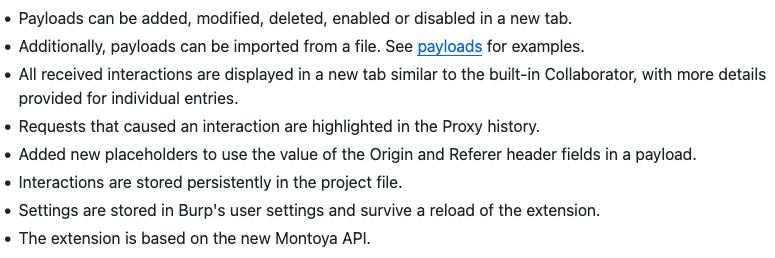
We've just released a massive update to Collaborator Everywhere! This is a complete rewrite by @compass-security.com which adds loads of features including in-tool payload customization. Massive thanks to Compass for this epic project takeover. Check out the new features:
14.07.2025 14:51 — 👍 19 🔁 7 💬 1 📌 1
When Backups Open Backdoors: Accessing Sensitive Cloud Data via
Teammate Leonid discovered a leaked credential that allowed anyone unauthorized access to all Microsoft tenants of orgs that use Synology's "Active Backup for Microsoft 365" (ABM), including sensitive data like Teams channel messages. 🤓
#synology #disclosure #modzero
modzero.com/en/blog/when...
29.06.2025 08:01 — 👍 22 🔁 14 💬 1 📌 1

Introducing the BloodHound Query Library - SpecterOps
The BloodHound Query Library is a community-driven collection of BloodHound Cypher available at https://queries.specterops.io
Introducing the BloodHound Query Library! 📚
@martinsohn.dk & @joeydreijer.bsky.social explore the new collection of Cypher queries designed to help BloodHound users to unlock the full potential of the BloodHound platform by creating an open query ecosystem. ghst.ly/4jTgRQQ
17.06.2025 19:14 — 👍 14 🔁 10 💬 0 📌 1
👀 We have also released a paper which really goes into the nitty-gritty for those who are interested 🕵️♀️:
www.redteam-pentesting.de/publications...
For those that only need a short overview, here's our advisory 🚨:
www.redteam-pentesting.de/advisories/r...
11.06.2025 08:04 — 👍 1 🔁 1 💬 0 📌 0

NTLM reflection is dead, long live NTLM reflection! – An in-depth analysis of CVE-2025-33073
Microsoft just released the patch for #CVE-2025-33073, a critical vulnerability allowing a standard user to remotely compromise any machine with SMB signing not enforced! Checkout the details in the blogpost by @yaumn.bsky.social and @wilfri3d.bsky.social.
www.synacktiv.com/publications...
11.06.2025 10:40 — 👍 7 🔁 5 💬 0 📌 1

Many CI/CD tools promise to keep your dependencies up to date - but if misconfigured, they can expose your organization. From token leaks to MR hijacks, Jan's latest blog post shows how bad configuration can turn a security tool into an attack vector. 🛠️💣
blog.compass-security.com/2025/05/reno...
27.05.2025 07:24 — 👍 6 🔁 3 💬 0 📌 0
MATCH p = (d:Computer)<-[:WriteDacl|Owns|GenericAll|GenericWrite|WriteOwner]-(n:Base)
WHERE d.`msds-delegatedmsastate` IS NOT NULL
AND (NOT "admin_tier_0" IN split(n.system_tags, " ") OR n.system_tags is NULL)
RETURN p
LIMIT 1000
2/2
28.05.2025 12:09 — 👍 0 🔁 0 💬 0 📌 0
You can also use the following BloodHound query to search dMSA accounts which are controllable by non-tier 0 accounts. These could also escalate their privileges. This requires SharpHound's `--collectallproperties`. We added this to our BloodHound query collection: github.com/CompassSecur... 1/2
28.05.2025 12:09 — 👍 0 🔁 0 💬 1 📌 0
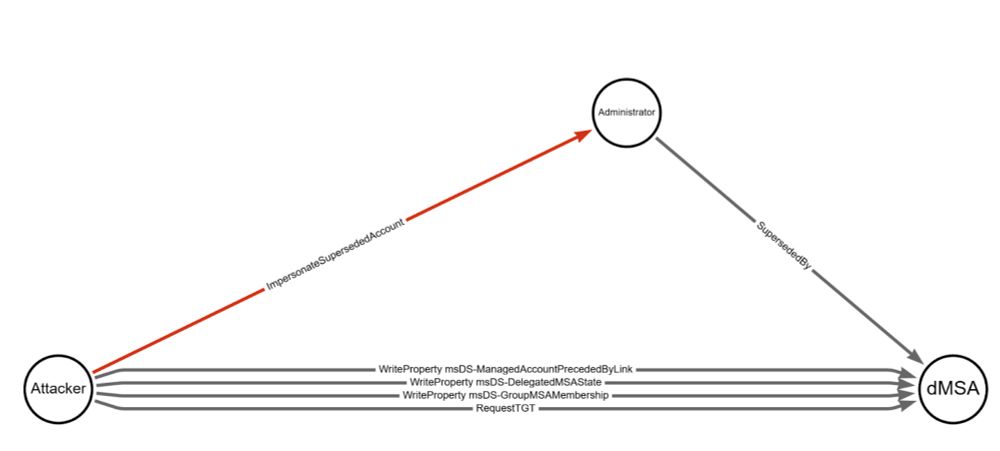
Understanding & Mitigating BadSuccessor - SpecterOps
Understanding the impact of the BadSuccessor AD attack primitive and mitigating the abuse via targeted Deny ACEs on Organizational Units.
BadSuccessor is a new AD attack primitive that abuses dMSAs, allowing an attacker who can modify or create a dMSA to escalate privileges and take over the forest.
Check out @jimsycurity.adminsdholder.com's latest blog post to understand how you can mitigate risk. ghst.ly/4kXTLd9
27.05.2025 21:11 — 👍 16 🔁 9 💬 0 📌 1
⚠️ Note: BloodHound doesn't currently have all elements required for a full BadSuccessor audit, namely 'Create msDS-DelegatedManagedServiceAccount', 'Create all child objects', & dMSA nodes. For that, you should run Get-BadSuccessorOUPermissions.ps1 shared in Yuval's blog.
(8/9)
23.05.2025 18:11 — 👍 2 🔁 1 💬 1 📌 0
BadSuccessor: Abusing dMSA to Escalate Privileges in Active Directory
21.05.2025 16:13 — 👍 1 🔁 1 💬 0 📌 0
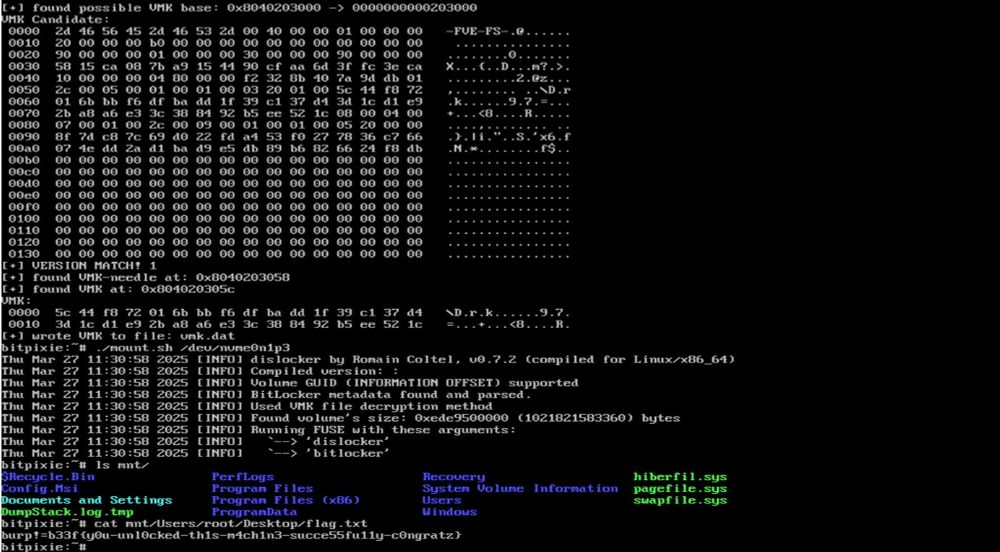
In his latest blog post, Marc Tanner @brain-dump.org shows how to bypass BitLocker using BitPixie (CVE-2023-21563) and signed Microsoft components only. Check out the blog post for a PoC and a demo. #BitLocker #RedTeam
blog.compass-security.com/2025/05/bypa...
13.05.2025 12:38 — 👍 9 🔁 5 💬 0 📌 1

mario meme with our guide on phone searches at the US border
travelling to the US soon?
link: www.wired.com/story/how-to...
09.05.2025 15:41 — 👍 2361 🔁 904 💬 51 📌 34

Tired of sifting through Entra ID manually? EntraFalcon is a PowerShell tool that flags risky objects configs & privileged role assignments with ⚡ Scoring model 📊 HTML reports 🔒 No Graph API consent hassle. Get it now: blog.compass-security.com/2025/04/intr...
#EntraID #IAM
29.04.2025 11:08 — 👍 6 🔁 5 💬 0 📌 0
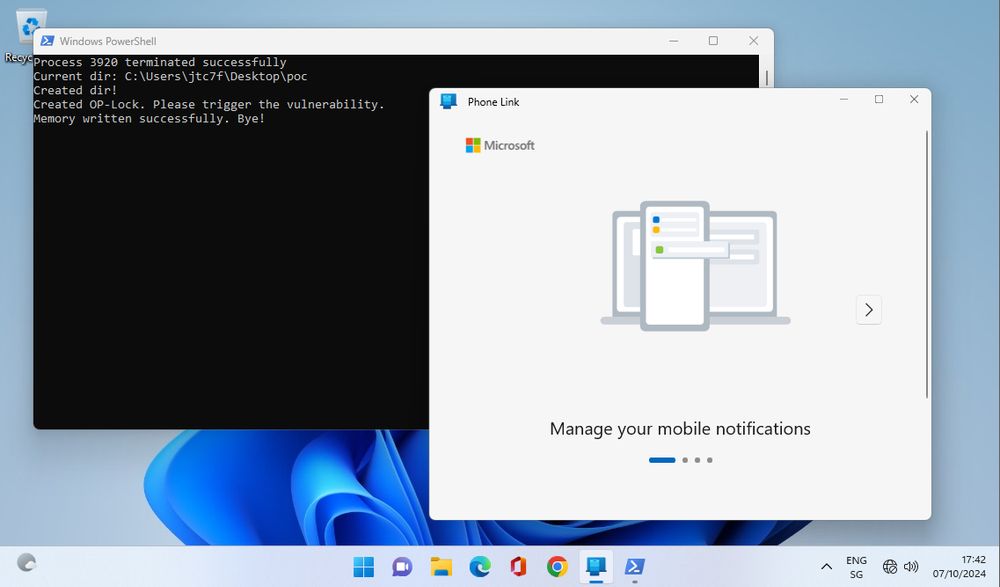
3 milliseconds to admin — Our analyst John Ostrowski turned a DLL hijacking into a reliable local privilege escalation on Windows 11. He chained opportunistic locks, and API hooking to win the race to CVE-2025-24076 & CVE-2025-24994. Read his blog post: blog.compass-security.com/2025/04/3-mi...
15.04.2025 09:00 — 👍 21 🔁 5 💬 0 📌 0
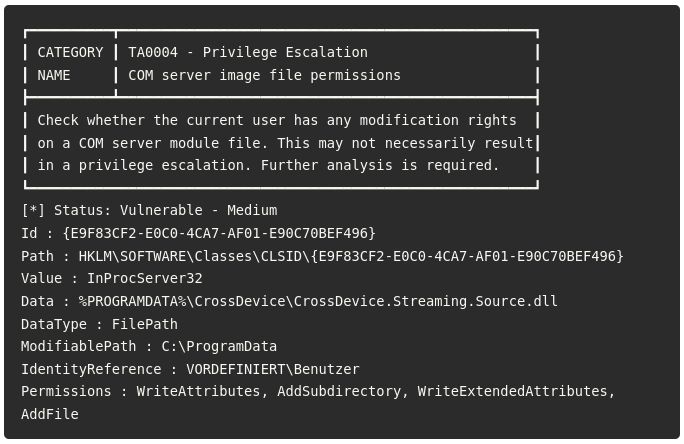
Another example of a Windows 0-day found with PrivescCheck. Congrats to Compass Security for investigating the issue and exploiting it. 👏
blog.compass-security.com/2025/04/3-mi...
15.04.2025 12:41 — 👍 15 🔁 6 💬 1 📌 0
YouTube video by Sense Post
WinRMS Relaying
The S is for Security. How to use WinRMS as a solid NTLM relay target, and why it’s less secure than WinRM over HTTP.
writeup: sensepost.com/blog/2025/is...
PR to impacket:
github.com/fortra/impac...
Demo: youtu.be/3mG2Ouu3Umk
14.04.2025 16:40 — 👍 11 🔁 10 💬 1 📌 0

Think NTLM relay is a solved problem? Think again.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
08.04.2025 23:00 — 👍 27 🔁 20 💬 1 📌 2
YouTube video by Hack In The Box Security Conference
#HITB2024BKK #COMMSEC D1: My First and Last Shellcode Loader
My First and Last Shellcode Loader by Dobin Rutishauser
Talk: www.youtube.com/watch?v=SYM4...
Slides: conference.hitb.org/hitbsecconf2...
Code: github.com/dobin/SuperM...
01.04.2025 17:48 — 👍 1 🔁 1 💬 1 📌 0

Europa muss raus aus den amerikanischen #Clouds. Dieses Interview mit @berthubert.bsky.social soll aufrütteln. Elon & die US-Regierung möchten alle Daten für ihre #KI-Modelle und die Politiker- Emails aus Europa auf Microsofts Servern wären der logische nächste Schritt...
republik.ch/2025/03/31/d...
31.03.2025 06:47 — 👍 141 🔁 61 💬 6 📌 7
since 1985
https://phrack.org
Research and development at the intersection of cyberspace, global security, and human rights. Based at Munk School of Global Affairs & Public Policy, University of Toronto.
👨🏫 Software Engineering Prof. https://ost.ch/i
📙 Author of Patterns for API Design https://api-patterns.org/
✍🏻 Growing Green Software Blog https://medium.com/growing-green-software
senior researcher at @citizenlab.ca
security & software engineering · operating systems & kernel engineering · cyber defense · civil society
https://infosec.exchange/@droe
Manager, Research @ SpecterOps
https://github.com/JonasBK/JonasBK/blob/main/README.md
Mastodon felmoltor@defcon.social. Now with more #OSCP than the previous version. Working @SensePost.com - Orange Cyberdefense
https://blog.felipemolina.com/
Account for RedTeam Pentesting GmbH
Imprint: https://redteam-pentesting.de/imprint/
CTF player with The Flat Network Society - bug bounty & web security research
Pentagrid performs technically solid IT security assessments.
Website: https://www.pentagrid.ch/
Mastodon: https://infosec.exchange/@pentagrid
Imprint: https://www.pentagrid.ch/en/pages/imprint-and-contact/
Know. When it matters.
https://canary.tools
Principal Identity Security Researcher @Microsoft. Ex-Secureworks (PhD, MSc, MEng, CITP, CCSK).
And yes, opinions are my own ;)
red & purple team operations,*nix plumber,bass,org-(mode/roam),🇨🇭🇿🇦,🌶 & 🎶 addict. SMI²LE. Herbivore.
Opinions my own, not that of my employer
Hacker at Orange Cyberdefense's SensePost Team
https://hello.singe.za.net/
WHY2025 is an international non-profit outdoor hacker camp/conference taking place in The Netherlands in the summer of 2025.
WHY2025.org
I like making computers misbehave. Does stuff at http://specterops.io.
Github: https://github.com/leechristensen
Mastodon: @tifkin_@infosec.exchange
Former Pentester
Engineer at SpecterOps
Author of BloodHound