vx-underground Black Mass Volume III zine print edition, cover

Article “EFI Byte Code Virtual Machine, A Monster Emerges” in vx-underground Black Mass Volume III zine print edition
seeing my @vxundergroundre.bsky.social Black Mass article “EFI Byte Code Virtual Machine - A Monster Emerges” in the print copy of vol III at long last has me verklempt.
All the blood,sweat+tears that I poured into writing the first UEFI EBC virus were v worth it. 🖤
26.07.2025 21:03 — 👍 7 🔁 2 💬 1 📌 0
My GitHub contribution graph for the past year
Today I’m celebrating one year of #Rust! 🦀
I started learning it last summer, and since then, I’ve pretty much stopped programming in any other language. Over the past year, I’ve gone from playing with the basics to building some (hopefully 😜) useful […]
[Original post on infosec.exchange]
15.07.2025 20:47 — 👍 3 🔁 4 💬 0 📌 0
idalib documentation
I'm pleased to announce a new version of the Rust bindings for IDA Pro! With:
- Improved strings, metadata, and core APIs.
- Support for the names API.
Thank you to @raptor.infosec.exchange.ap.brid.gy & Willi Ballenthin for contributing!
Docs: idalib.rs
Code: git.idalib.rs
15.07.2025 01:12 — 👍 10 🔁 7 💬 0 📌 0
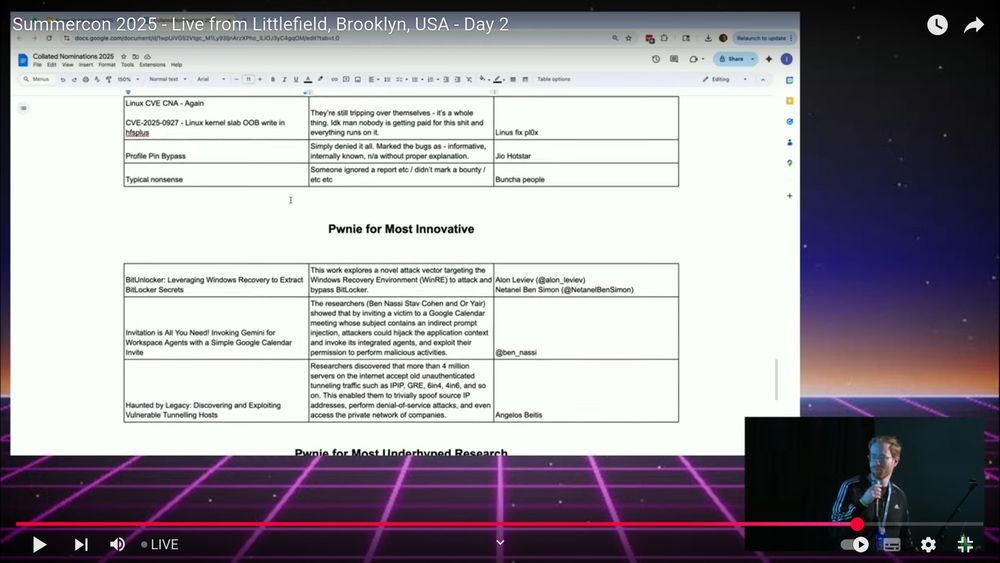
Our research on open tunneling servers got nominated for the Most Innovative Research award :)
The work will be presented by Angelos Beitis at Black Hat and also at USENIX Security
Brief summary and code: github.com/vanhoefm/tun...
Paper: papers.mathyvanhoef.com/usenix2025-t...
12.07.2025 20:17 — 👍 7 🔁 6 💬 0 📌 0
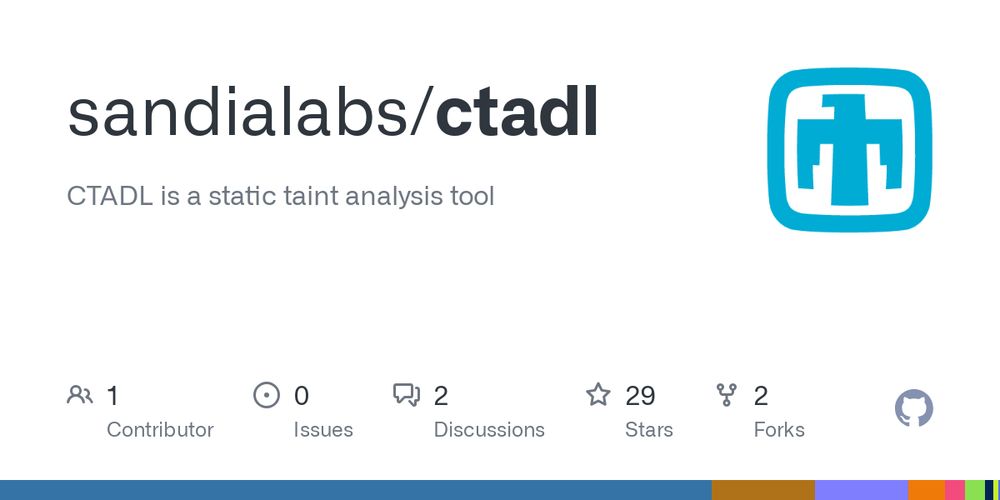
GitHub - sandialabs/ctadl: CTADL is a static taint analysis tool
CTADL is a static taint analysis tool. Contribute to sandialabs/ctadl development by creating an account on GitHub.
CTADL - a Datalog-based interprocedural static taint analysis engine for Java/Android bytecode (via JADX) and Pcode (via Ghidra)
Code: github.com/sandialabs/c...
Talk (via @krismicinski.bsky.social): youtu.be/3ec9VfMUVa8?...
09.07.2025 10:10 — 👍 9 🔁 2 💬 1 📌 0
YouTube video by Kristopher Micinski
Minnowbrook Logic Programming Seminar (Supercut w/ Extras)
May 25-27, 2025, I hosted an event, the "Minnowbrook Logic Programming Seminar," in Blue Mountain Lake, NY. I recorded 11 talks on Datalog-related interests, totaling over 9+ hours of video, which I have just now published on YouTube youtu.be/3ec9VfMUVa8
07.07.2025 18:50 — 👍 19 🔁 6 💬 2 📌 1
Original post on infosec.exchange
Exploring fault injection on ESP32 V3!
Inspired by Delvaux work, we tested voltage #glitching as an attack vector. With advanced triggers & GDB, we achieved a ~1.5% success rate. #Hardware #FaultInjection is becoming more practical! […]
18.06.2025 08:23 — 👍 1 🔁 3 💬 0 📌 0
🚨 Blog Post: ""A Human Study of Automatically Generated Decompiler Annotations" Published at DSN 2025" https://edmcman.github.io/blog/2025-06-16--a-human-study-of-automatically-generated-decompiler-annotations-published-at-dsn-2025/
16.06.2025 16:46 — 👍 3 🔁 1 💬 0 📌 0

placard saying protesting is our human right, with split image showing Westminister in the background
ONLY 5 DAYS LEFT
🚨 The Crime and Policing Bill is in the House of Commons on Tuesday 17.06.
We have 5 days left to email MPs to act.
MPs right now have the power to protect our protest rights.
We can’t let them ignore us.
📝 Take action: www.amnesty.org.uk/actions/emai...
12.06.2025 14:09 — 👍 25 🔁 20 💬 0 📌 0
Hydroph0bia (CVE-2025-4275) - a trivial SecureBoot bypass for UEFI-compatible firmware based on Insyde H2O, part 1
#Hydroph0bia (CVE-2025-4275) - a trivial #SecureBoot bypass for UEFI-compatible firmware based on Insyde #H2O, part 1
https://coderush.me/hydroph0bia-part1/
11.06.2025 05:53 — 👍 1 🔁 5 💬 0 📌 0
My greatest achievement so far in the #rust ecosystem: the “security” category in crates.io is gaining traction 😉
https://crates.io/search?q=category%3Asecurity&sort=downloads
05.06.2025 19:46 — 👍 2 🔁 2 💬 0 📌 0

DWARF as a Shared Reverse Engineering Format
This blog post introduces a new API in LIEF to create DWARF files
[Blog Post] New high-level API in LIEF that allows the
creation of DWARF files. Additionally, I present two plugins designed to export
program information from Ghidra and BinaryNinja into a DWARF file.
lief.re/blog/2025-05...
(Bonus: DWARF file detailing my reverse engineering work on DroidGuard)
27.05.2025 13:50 — 👍 21 🔁 15 💬 1 📌 0
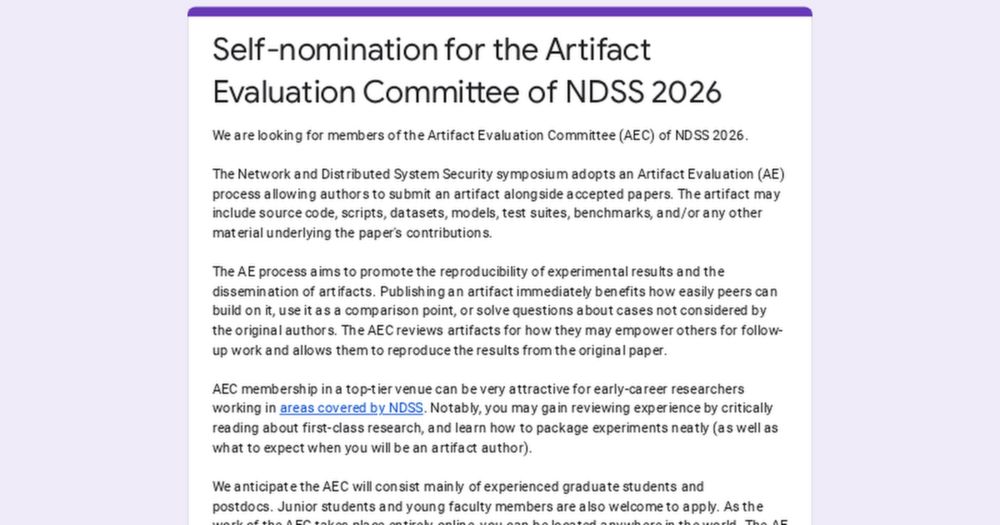
Self-nomination for the Artifact Evaluation Committee of NDSS 2026
We are looking for members of the Artifact Evaluation Committee (AEC) of NDSS 2026.
The Network and Distributed System Security symposium adopts an Artifact Evaluation (AE) process allowing authors t...
All papers should publish their code. Help realize this by becoming an artifact reviewer at NDSS'26, apply here: docs.google.com/forms/d/e/1F...
You'll review artifacts of accepted papers. We especially encourage junior/senior PhD students & PostDocs to help. Distinguished reviews will get awards!
25.05.2025 13:25 — 👍 12 🔁 10 💬 0 📌 1
🚨 Blog Post: "Re-compiling Decompiler Output" https://edmcman.github.io/blog/2025-05-02--re-compiling-ghidra-decompiler-output/
03.05.2025 14:54 — 👍 1 🔁 2 💬 0 📌 0
Original post on infosec.exchange
My first official rust-lang contribution 😜
https://github.com/rust-lang/crates.io/pull/10905
On crates.io, you can now categorize your crate under “security” (“Crates related to cybersecurity, penetration testing, code review, vulnerability research, and reverse engineering.”) […]
28.03.2025 20:57 — 👍 4 🔁 1 💬 0 📌 0

Hex-Rays - Plugins & Apps
Your description here
My idalib-based "vulnerability divination" tool suite is finally available in the official Hex-Rays Plugins & Apps repository! 🦀
https://plugins.hex-rays.com/search-results?search_term=0xdea
#idapro #idalib #vulnerabilityresearch
#reverseengineering
27.03.2025 09:00 — 👍 1 🔁 1 💬 0 📌 0

The difference between the paper and reality.
21.03.2025 15:43 — 👍 3 🔁 1 💬 1 📌 0
Original post on infosec.exchange
I've just pushed to crates.io updated releases of my #VulnerabilityResearch tools written in #Rust, compatible with Hex-Rays IDA Pro 9.1 and upgraded to the Rust 2024 Edition.
Thanks to @xorpse and Yegor Vasilenko at @binarly_io for the immediate update of their idalib Rust bindings!
For more […]
03.03.2025 09:17 — 👍 3 🔁 4 💬 0 📌 0

crates.io: Rust Package Registry
We @binarly.bsky.social are pleased to announce a new release of our Rust bindings for Hex-Rays IDA Pro (crates.io/crates/idalib) with support for the latest v9.1 release! Special thanks to @yeggor.bsky.social for taking care of the changes needed to make everything compatible with this release!
28.02.2025 20:56 — 👍 7 🔁 2 💬 0 📌 0
We’re Hiring – Tenured Faculty Positions in Cybersecurity!
CentraleSupélec is recruiting 2 tenured Ass. Prof. / Prof. in Cybersecurity at IRISA (UMR CNRS 6074), Rennes, France.
Application deadline: April 14, 2025
Full job details: team.inria.fr/sushi/files/...
Contact us before applying!
05.02.2025 21:07 — 👍 0 🔁 2 💬 0 📌 0

Under the cloak of UEFI Secure Boot: Introducing CVE-2024-7344
ESET researchers have discovered a vulnerability that affects the majority of UEFI-based systems and allows bypassing UEFI Secure Boot.
#ESETresearch discovered and reported to #certcc a vulnerability that allows bypassing UEFI Secure Boot on most UEFI-based systems. This vulnerability, #CVE-2024-7344, was found by x.com/smolar_m in a UEFI app signed by Microsoft’s 3rd-party UEFI certificate. welivesecurity.com/en/eset-rese... 🧵1/4
16.01.2025 10:46 — 👍 13 🔁 10 💬 1 📌 0
Original post on infosec.exchange
In this new @hnsec blog post, @MrAle_98@twitter.com demonstrates how to leverage the I/O Ring technique to bypass the latest #exploit mitigations, such as hypervisor-protected code integrity (#HVCI), and achieve local privilege elevation on a recent #Windows 11 […]
15.01.2025 09:01 — 👍 1 🔁 2 💬 0 📌 0
After an embargo of 8 months, we are glad to finally share our USENIX Security '25 paper! We found more than 4 MILLION vulnerable tunneling servers by scanning the Internet.
These vulnerable servers can be abused as proxies to launch DDoS attacks and possibly to access internal networks.
14.01.2025 14:12 — 👍 59 🔁 26 💬 2 📌 0
Original post on infosec.exchange
2025 is just around the corner. If #LearningRust is among your New Year’s resolutions, I’ve got you.
Following my ongoing #Rust series on the @hnsec blog (https://security.humanativaspa.it/tag/rust/) and adding something along the way, in the next days I’ll recommend the learning resources […]
26.12.2024 06:54 — 👍 2 🔁 5 💬 0 📌 0
I talk about functional programming and compilers. Building a high performance Datalog called “eclair” with Haskell and LLVM.
Reverse Engineering | Network | Dev | Hacking
https://www.linkedin.com/in/fabdotnet
https://hackerone.com/fabdotnet
https://twitter.com/FabDotNET
Malware analyst and reverse engineer, author of the Binary Analysis Course. DMs are always open. Opinions are my own and not the views of my employer.
http://github.com/frankmcsherry/blog
i sometimes do things with rust and sometimes also do other things and sometimes i don't do anything at all
find me as Noratrieb everywhere I am
The Next 700 Programmers.
Reverse Engineer – Passion for decompiler, disassembler, and anything that breaks software
Blog: https://nicolo.dev
Binary Security Researcher, Chief Scientist at http://emproof.com and Trainer.
Website: https://synthesis.to
kmicinski.com
Interested in automated reasoning, static analysis, and logic programming and literally nothing else.
We secure software with deep-dive audits, cutting-edge research, and in-depth trainings.
CS professor at UT Austin, does research in programming languages & formal methods.
galois.com
For nearly 25 years, Galois has combined mathematical rigor with curious creativity to cut through complexity and guarantee trustworthiness in the world’s most critical systems.
Principal Security Architect at Microsoft. Formerly at Google and Amazon.
Assistant Professor @ Eurecom. I'm interested in formal methods for low-level security. https://leslyann-daniel.fr
swedish cat computer math person
He/They • 🏳️🌈🏳️⚧️ pan
🐸 and 🐢 appreciator & 🍄 enthusiast
🧑💻 SRE/Security Engineering
👾 REing dead games
✊ anti-capitalist & anti-imperialist • pro-unionization
Black Lives Matter, Trans Rights are Human Rights, I stand for a free Palestine 🇵🇸
Security Researcher and InfoSec PhD-er