I would put more weight on these internal factors than on influence. Especially in an employer’s hiring market. Though I don’t know the importance of influence for attracting staff+ employees
04.08.2025 10:53 — 👍 0 🔁 0 💬 0 📌 0
The external post can also be useful docs for coworkers and future employees. External posts warrant more time investment to make them good than internal docs do. And it can help change team culture to work more in the open and invite feedback, rather than isolated from other teams / your peers
04.08.2025 10:53 — 👍 0 🔁 0 💬 1 📌 0
From the creator of UML 1.0: “There’s a sweet spot for a tremendous amount of software engineering that does not need the UML”
02.08.2025 17:21 — 👍 0 🔁 0 💬 0 📌 0
41:00 "Bill Gates said 'Grady, I'm stepping down and I'd like you to take the role of Chief Architect'. I did some research, and came back, 'Bill, I'm flattered, but you have a profoundly dysfunctional company, and I'm not the one to fix it."
pca.st/w2a6ta7h?t=41m
02.08.2025 17:08 — 👍 1 🔁 0 💬 1 📌 0
MCP is a headless scripting language (bring your own syntax)
02.08.2025 11:23 — 👍 1 🔁 0 💬 0 📌 0
Not to mean they’re wrong, but I think they misjudged their audience — it was hard for me with 5 years of 🇳🇱 high school chemistry.
02.08.2025 09:51 — 👍 0 🔁 0 💬 0 📌 0
And -OH is what turns alkanes into alcohols. It’s -OOH for carboxylic acids 🤷🏼 I guess one O was in the Ac
02.08.2025 09:50 — 👍 2 🔁 0 💬 1 📌 0
But then Nebula’s payouts can’t add up to much either with 50% of €3 going to creators…
02.08.2025 09:16 — 👍 0 🔁 0 💬 0 📌 0
YouTube Premium makes it a bug-ridden product instead of a super annoying bug-ridden product 🤷🏼
And I have this nagging feeling that creators get very little of my €13/month, instead it goes mostly to music labels (I don’t use it for music). I resent that idea
02.08.2025 09:16 — 👍 1 🔁 0 💬 1 📌 0
Someone should compare the environmental cost of letters to receiving GMail when Gemini is active
01.08.2025 23:19 — 👍 0 🔁 0 💬 0 📌 0
Favorite jj alias: jj swap — swap the last two commits
Define with:
swap = ["rebase", "-r", "@-", "-B", "@--"]
01.08.2025 09:29 — 👍 2 🔁 0 💬 0 📌 0
…and today the blocklist feeds again
I’m sorry you have to go through this 😔
01.08.2025 06:07 — 👍 0 🔁 0 💬 1 📌 0
This is a good talk.
31.07.2025 10:26 — 👍 2 🔁 0 💬 0 📌 0
The politics in question: “people deserve to live and not to starve”
31.07.2025 07:27 — 👍 0 🔁 0 💬 0 📌 0
And interesting thoughts about Google vs Amazon’s DNA in the full episode
30.07.2025 09:51 — 👍 1 🔁 0 💬 0 📌 0
“Just sing out a Te Deum / when you see that ICBM” is one of my favourite rhymes of all time
R.I.P. Tom Lehrer
27.07.2025 20:55 — 👍 55 🔁 3 💬 2 📌 0
I know very little about personal branding but “typically humble, proactive, and helpful, without much concern for personal gain” seems like a personal brand to me, and I’m glad that your org supports that
28.07.2025 22:11 — 👍 2 🔁 0 💬 0 📌 0
Maybe it’s contrasting to hypothetical CISOs who care about ass-covering and ticking boxes at any cost to the org? And who don’t really care about being helpful
(Just speculating, not speaking from any experience)
28.07.2025 22:08 — 👍 3 🔁 0 💬 1 📌 0
On the cultural price of distributed teams
24.07.2025 04:05 — 👍 2 🔁 0 💬 0 📌 0
For sure, moddable keyboard have a tendency to be a time sink.
23.07.2025 03:31 — 👍 1 🔁 0 💬 0 📌 0
I need this on my 60% UHK60, but I also get value out of it. It means you can have a 2-key chord for rarer actions like media control, LockScreen, Suspend, mouse.
22.07.2025 12:21 — 👍 0 🔁 0 💬 0 📌 0
I guess it’s a bit late, but did you consider a layer modifier button to hide rarer keys behind?
22.07.2025 12:21 — 👍 0 🔁 0 💬 2 📌 0
I also see "blocked post". Maybe they set the thread to mutuals only, or so?
20.07.2025 22:39 — 👍 1 🔁 0 💬 0 📌 0
I let a goat from my local zoo run SQL commands against prod without protection and it nuked my data
The comments: have you tried this other much smarter goat
20.07.2025 16:32 — 👍 759 🔁 157 💬 12 📌 5

Screenshot of article text: “Formal verification today is very useful, but for most systems it’s very difficult to write the kinds of complete specifications that verification needs. However, other kinds of specifications are popular: for example, a test case is a kind of limited, partial specification. The key is that a test case is immediately useful, and doesn’t impose undue costs on the development team. We need to find ways to specify systems that have these virtues, and avoid the trap of imposing a complete and coherent view that fundamentally does not exist.”

Screenshot of article text: “ I’ve come to think writing formal specifications is just a very difficult task. It requires a top-down view of the system that designers and engineers typically don’t have or, more importantly, need. In contrast, informal specifications can be ambiguous, partial, flexible. Informal specifications are intended as communication mechanisms between humans, and as a result they can be ‘wrong but useful’, and elide aspects of the system that are not of interest. This is a strength, but it also results in systems that can’t be easily formalized.”

Screenshot of article text: “ I think systems are typically both designed from the top and grown incrementally. Most systems have some degree of top-down structure, but few systems have a mathematically coherent specification that covers every behavior. The effect is that most systems obey some formal specification for some core functionality, but if outside this core, we rapidly enter muddy territory where it is unclear what the system should do, or whether the designer should even care”
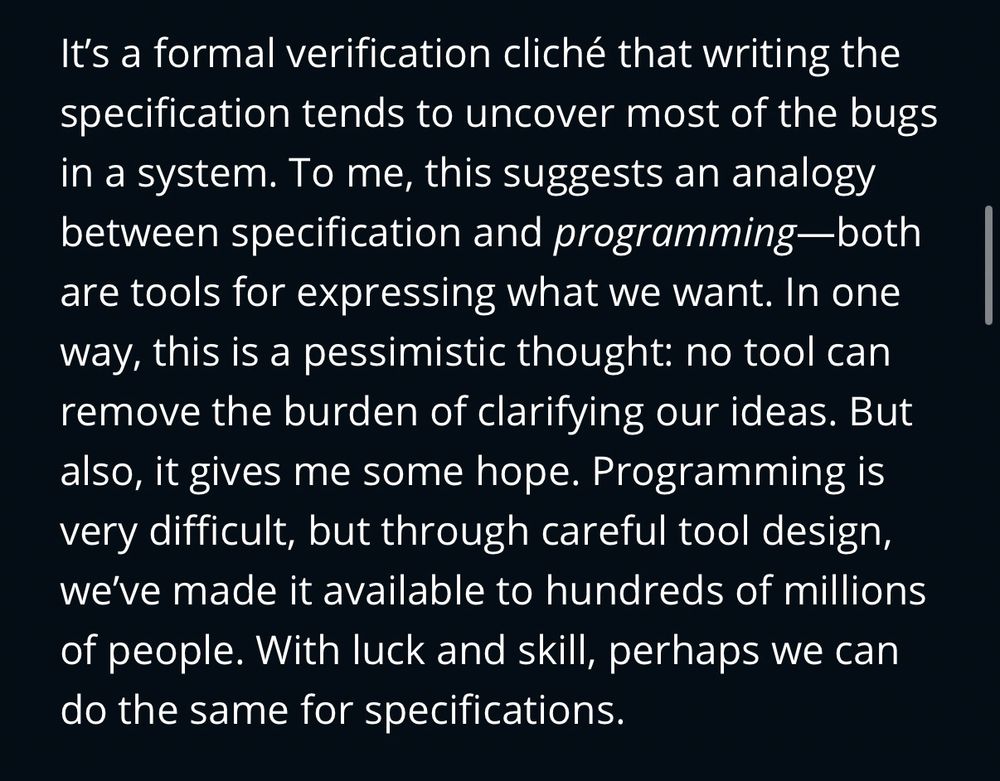
Screenshot of article text: “ It’s a formal verification cliché that writing the specification tends to uncover most of the bugs in a system. To me, this suggests an analogy between specification and programming—both are tools for expressing what we want. In one way, this is a pessimistic thought: no tool can remove the burden of clarifying our ideas. But also, it gives me some hope. Programming is very difficult, but through careful tool design, we’ve made it available to hundreds of millions of people. With luck and skill, perhaps we can do the same for specifications.”
New Galois blog: “Specifications Don’t Exist”. If we want to formally verify more systems, we need formal specifications, but most real systems are hard to specify for very deep reasons www.galois.com/articles/spe...
16.07.2025 00:48 — 👍 6 🔁 1 💬 0 📌 0
AI is now significantly weakening Internet security by burdening maintainers
(It may be helpful in other regards, or harmful in more ways than this)
14.07.2025 11:28 — 👍 2 🔁 0 💬 0 📌 0
Drive(way) is for being stationary, probably your need Google Park(way)
13.07.2025 18:25 — 👍 1 🔁 0 💬 0 📌 0
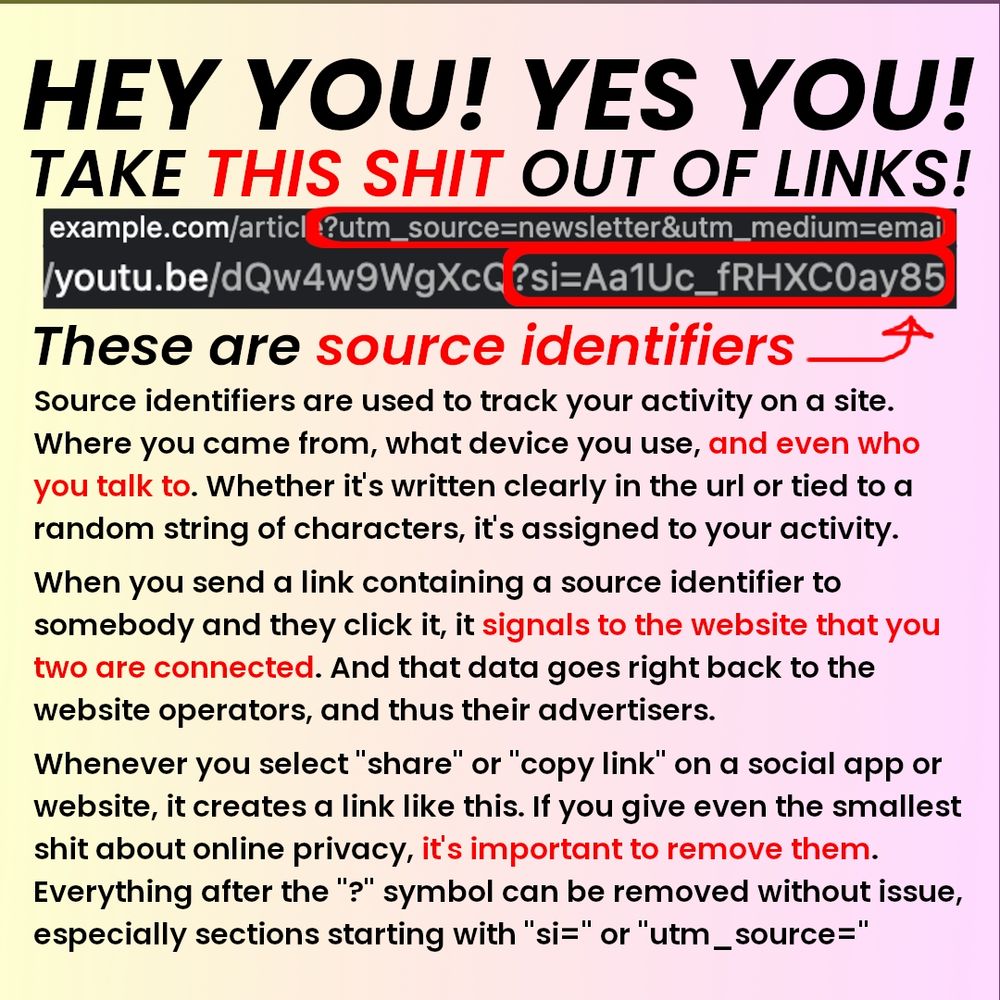
Header text: "HEY YOU! YES YOU! TAKE THIS SHIT OUT OF LINKS!"
This is followed by a couple example urls, with a red square highlighting the sections with source identifiers. The rest of the text is as follows:
Source identifiers are used to track your activity on a site. Where you came from, what device you use, and even who you talk to. Whether it's written clearly in the url or tied to a random string of characters, it's assigned to your activity.
When you send a link containing a source identifier to somebody and they click it, it signals to the website that you two are connected. And that data goes right back to the website operators, and thus their advertisers.
Whenever you select "share" or "copy link" on a social app or website, it creates a link like this. If you give even the smallest shit about online privacy, it's important to remove them. Everything after the "?" symbol can be removed without issue, especially sections starting with "si=" or "utm_source="
I saw an infographic a couple years ago about how to remove source identifiers from links and why it's important, but I can't find it again and too many people I know are sending me links with them so here's an infographic straight from the oven
11.07.2025 22:22 — 👍 12206 🔁 7124 💬 182 📌 295
CTO at Vercel
@cramforce on Twitter
industrialempathy.com
scientist, storyteller, philosopher
computingthehumanexperience.com
trancefem hypnowitch, not a person, never alone
💖 ringsworn moth to @kanba.gay ✨
💜 witch to my familiar @transgender.parts 🌙
it/they by default, she/her for prey, "Miss" for property
🇵🇱 🏳️⚧️ 🎼 💻 lv29 flesh golem
very nsfw account; mdni, you know the drill
Turn your data into a backend, admin panels, or apps with a custom UI, instant APIs, auth & more. Built for devs, used by everyone. ✨
that guy from the internet • waging a victorious 2-front war against cars and xmas • big fan of being a big fan of things • see https://anildash.com
Haskell and type theory enthusiast
they/them
CTO at Multiplayer.app, we help teams go from bug reported to bug fixed fast, with zero guesswork.
Also: 🤖 robot builder 🏃♂️ runner 🎸 guitar player
🚀rockit network engineer
👩🏼💻ethernet fangirl
🛜 weird use cases & silly tech!
💌 tracket@tracketpacer.com
🌎 tracketpacer.com
Minors DNI, please.
I'm 27, polyamorous, I adore public transit and love Lichtenberg. 161✊
Formal methods nitwit. https://mikedodds.github.io
AI / math / formal methods paper feed: @ai-fm-papers.bsky.social
An inside track on how to facilitate domain modeling decisions. Lay out of pragmatic techniques for making collaborative design decisions, ensuring you’re getting a group’s full participation and input to solve real business problems.
Co-author Collaborative Software Design: How to facilitate domain modeling decisions. Independent consultant & trainer specialised in technical leadership, software architecture, and #sociotechnical systems design. #DDD #TeamTopologies #DeepDemocracy
Postdoc at the University of Nottingham working on type theory. PhD from the University of Birmingham. Mathematician, computer scientist and runner.
🌉 bridged from https://mathstodon.xyz/@de_Jong_Tom on the fediverse by https://fed.brid.gy/
A conference for #rustlang developers building networked applications with Tokio. 🦀 Join us April 20–22, 2026, for the inaugural TokioConf — practical knowledge, real-world insights, and more!
I post about databases, web development, software engineering and other nerdy stuff.
Sydney 🇦🇺
Website: https://weiyen.net
i work with computing nonsense
👋 they/he
🔗 https://barretts.club
disco pervert & technology sister.
co-founder @ https://ondora.xyz
blog: https://piss.beauty
code: https://github.com/stella3d
📍= ATX / ✈️