
I wonder if Microsoft secretly wants everyone to switch to Linux. There are certainly fewer reasons to stick to Windows every day: www.theverge.com/news/793579/...
07.10.2025 03:51 — 👍 218 🔁 48 💬 38 📌 7@kxynos.bsky.social
PhD. IT Sec. architect and ISO at an Automotive OEM. Computer Security & Forensics Consultant, ex-Educator & Researcher. S/W and H/W hacking. @kxynos@mastodon.social Twitter:@kxynos https://kosta.xynos.eu

I wonder if Microsoft secretly wants everyone to switch to Linux. There are certainly fewer reasons to stick to Windows every day: www.theverge.com/news/793579/...
07.10.2025 03:51 — 👍 218 🔁 48 💬 38 📌 7
zimperium.com/blog/insecur... - the report
04.10.2025 20:22 — 👍 0 🔁 0 💬 0 📌 0
One day soon at a research lab near Santa Barbara or Seattle or a secret facility in the Chinese mountains, it will begin: the sudden unlocking of the world’s secrets. Your secrets.
Cybersecurity analysts call this Q-Day—the worst holiday maybe ever.
wrd.cm/4iyJdjP

Apple fixes critical font processing bug. Update now!
www.malwarebytes.com/blog/news/20...

Live streams from the RomHack 2025 security conference are available on YouTube
www.youtube.com/playlist?lis...

Unitree G1 humanoid robots collect and send sensor and telemetry to servers in China every 5 min without the owner's knowledge or consent.
arxiv.org/abs/2509.14139
The G1 also contains BLE vulnerabilities that can be exploited to pivot to a customer's internal network.
github.com/Bin4ry/UniPwn

The #BSidesLDN2025 Call for Volunteers is open!
All BSides events simply cannot run without the help of volunteers, and so, we need your help...
More information and to apply: bit.ly/BSidesLDN202...
#Security #BSides #London #Volunteers

Bcrypt cracking table, updated by SpecOps for modern GPU gear
specopssoft.com/blog/bcrypt-...

the cast of Hackers (1995) posing in a series of adjacent phone booths
Today is the 30th anniversary of Hackers
15.09.2025 23:56 — 👍 3640 🔁 1059 💬 76 📌 330Academics has developed a new side-channel attack that breaks virtualized environments
The VMScape attack works against AMD Zen CPUs and Intel Coffee Lake CPUs
It is a Spectre-like attack that can allow malicious guests in a cloud environment to leak hypervisor data
comsec.ethz.ch/research/mic...

Meet HackRF Pro! HackRF Pro is a Software Defined Radio peripheral capable of transmission or reception of radio signals from 100 kHz to 6 GHz.
You can read more about HackRF Pro and preorder it now from select resellers here: greatscottgadgets.com/hackrf/pro/
We've made substantial progress toward the launch of our newest product, HackRF Pro! We'd like to share an update on the project timeline - you can read it in full here: greatscottgadgets.com/2025/09-05-h...
09.09.2025 15:56 — 👍 2 🔁 2 💬 0 📌 0
Largest NPM supply chain attack in history. Attackers compromised 18 core JavaScript packages with 2+ billion weekly downloads after phishing a maintainer. Malware targets crypto wallets & steals credentials. Millions of developers affected worldwide www.aikido.dev/blog/npm-deb...
08.09.2025 19:23 — 👍 24 🔁 16 💬 2 📌 2
📣"Bluetooth 2222: Bluetooth reconnaissance with Blue2thprinting" is now released!📣
ost2.fyi/BT2222
This class teaches you about the 30+ data types that the Blue2thprinting software can collect for when you're trying to determine what a device is, and whether it has any known vulnerabilities.

Talks from the SteelCon 2025 security conference, which took place in July, are now available on YouTube
www.youtube.com/playlist?lis...

Chess.com has disclosed a data breach after threat actors gained unauthorized access to a third-party file transfer application used by the platform.
04.09.2025 13:52 — 👍 10 🔁 3 💬 0 📌 1
We’re proud to announce that OrangeCon 2025 is SOLD OUT!
A huge thank you to everyone who believes in our mission and to all who helped make this possible (you know who you are). We can’t wait to see you this Friday!
Oh and don’t forget to check the full schedule: orangecon.nl#schedule

"Challenges and Pitfalls while Emulating Six Current Icelandic Household Routers"
Evaluation of different tools for routers firmware emulation
(FACT, QEMU, EMUX, Qiling, Firmadyne, FAT, FirmAE, Pandawan, and EMBA)
skemman.is/bitstream/19...
#cybersecurity #embedded

#ESETResearch has discovered the first known AI-powered ransomware, which we named #PromptLock. The PromptLock malware uses the gpt-oss:20b model from OpenAI locally via the Ollama API to generate malicious Lua scripts on the fly, which it then executes 1/7
26.08.2025 15:37 — 👍 66 🔁 45 💬 2 📌 14
A new tool targets the 5G handshake gap—sniffing traffic and downgrading connections. If you're relying on mobile networks, don’t assume they're secure by default. #5Gsecurity #infosec #mobilethreats www.theregister.com/2025/08/18/s...
20.08.2025 15:04 — 👍 1 🔁 1 💬 0 📌 0
"Graphic with 'Anthropic' logo on left, circuit-like design. Right text reads: 'Authors: You May Be Part of This Class Action Lawsuit. Anthropic AI Lawsuit Explained.' Modern, tech-themed design."
A federal court ruled that ANTHROPIC illegally copied MILLIONS of books to train its AI.
All authors and publishers whose books were downloaded by Anthropic from pirate websites are subject to receiving compensation. This could involve your work.
For more info: authorsguild.org/news/anthrop...

WOOT 2025 schedule, all papers are now online open access:
usenix.org/conference/w...
Talks are recorded, and should be online in a few weeks.

Security researchers found a weakness in OpenAI’s Connectors, which let you hook up ChatGPT to other services, that allowed them to extract data from a Google Drive without any user interaction.
10.08.2025 20:53 — 👍 253 🔁 116 💬 7 📌 4
New WinRAR zero-day: www.win-rar.com/singlenewsvi...
Found by ESET, but BI.ZONE suggests this is the Paper Werewolf APT: bi.zone/news/kibersh...
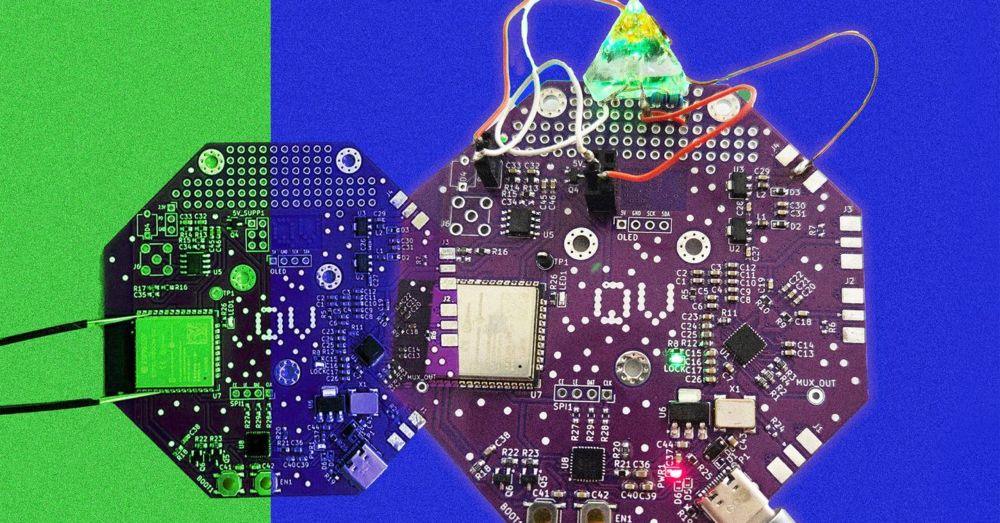
Today @defcon.bsky.social the Quantum Village co-founders will present a fully open source quantum sensor that anyone can build for under $150. And it's all possible because of a Very Specific Diamond 💎💅 www.wired.com/story/fully-...
09.08.2025 18:59 — 👍 49 🔁 18 💬 1 📌 0Here is the emergency directive
07.08.2025 17:45 — 👍 6 🔁 5 💬 1 📌 0
Low Energy to High Energy: Daan Keuper exposes how nearby EV chargers can be hacked over Bluetooth. Important insights into security risks in EV infrastructure. #Cybersecurity #EVCharging #Bluetooth #Infosec
Watch here: youtu.be/KOqfjjzCLQE?...

Mark the date: September 3–4 in Amsterdam. For €1500 + €250 kit you get an intensive 2-day hardware hacking training led by Roman Stuehler. Learn firmware dumping, power glitching, root access. At OrangeCon we bring quality and affordability together.
Register here: orangecon.nl/trainings/ha...

Coming soon: ESP32JTAG - a multifunction, wireless JTAG tool powered by an ESP32 and an FPGA www.crowdsupply.com/ez32/esp32jtag
05.08.2025 18:45 — 👍 3 🔁 1 💬 0 📌 0The "Bluetooth 2222: Bluetooth reconnaissance with Blue2thprinting" beta class was originally slated to start Aug 4th but it opened a little early. However the class registration will close Aug 4th as planned, and the class will run till Sept 1st.
02.08.2025 13:46 — 👍 2 🔁 1 💬 0 📌 0