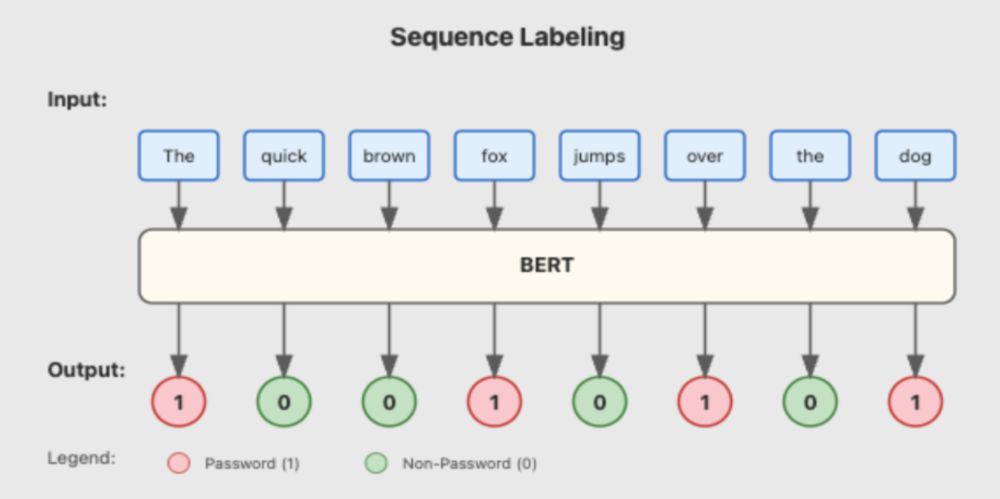
What’s Your Secret?: Secret Scanning by DeepPass2 - SpecterOps
Discover DeepPass2 - a secret scanning tool combining BERT-based model and LLMs to detect free-form passwords, and other structured tokens and secrets with high accuracy.
Red teamers know the drill: endless file churning, hunting for passwords & tokens. 🔍
Meet DeepPass2, our new secret scanning tool that goes beyond structured tokens to catch those tricky free-form passwords too. Read Neeraj Gupta's blog post for more. ghst.ly/40HLNNA
31.07.2025 17:36 — 👍 12 🔁 4 💬 0 📌 1
BloodHound 8.0 is here.
A big leap forward in identity security prevention.
Now we’re able to model attack paths across the entire modern enterprise stack.
Our folks will be at #BlackHat next week to show off a few examples. Check it out:
29.07.2025 17:23 — 👍 8 🔁 1 💬 0 📌 0

Introducing the BloodHound Query Library - SpecterOps
The BloodHound Query Library is a community-driven collection of BloodHound Cypher available at https://queries.specterops.io
Introducing the BloodHound Query Library! 📚
@martinsohn.dk & @joeydreijer.bsky.social explore the new collection of Cypher queries designed to help BloodHound users to unlock the full potential of the BloodHound platform by creating an open query ecosystem. ghst.ly/4jTgRQQ
17.06.2025 19:14 — 👍 14 🔁 10 💬 0 📌 1

Andy Robbins: The Evolution of Bloodhound by Phillip Wylie Show
About The Guest:Andy Robbins is the Principal Product Architect at SpecterOps and one of the original 13 founding members of the company. He has a background in pen testing and red teaming and is the co-creator of Bloodhound, a popular open-source tool for attack path mapping in Active Directory environments.
Summary:Andy Robbins, the Principal Product Architect at SpecterOps, joins host Phillip Wylie to discuss the evolution of Bloodhound, a tool for attack path mapping in Active Directory environments. Andy shares the origin story of Bloodhound and how it was developed to solve the problem of finding attack paths in complex environments. He explains the graph theory behind Bloodhound and how it visualizes data to help practitioners and defenders understand and mitigate security risks. Andy also discusses the recent release of Bloodhound Community Edition (CE) and the improvements it brings, including faster data ingest, query times, and a friendlier user experience. He highlights the focus on practical attack primitives and abuse primitives in Bloodhound and the goal of making attack paths a non-issue for organizations. Andy concludes by sharing valuable advice for those looking to advance in the industry, emphasizing the importance of understanding and solving real problems and being loyal to people rather than companies.
Key Takeaways:
Bloodhound is a tool for attack path mapping in Active Directory environments, using graph theory to visualize data and identify security risks.
Bloodhound Community Edition (CE) brings improvements such as faster data ingest, query times, and a friendlier user experience.
Bloodhound focuses on practical attack primitives and abuse primitives to solve real security problems and make attack paths a non-issue for organizations.
Quotes:
"If we give people an excellent experience for free, then enough of those people will choose to become paying customers that we have a viable business." - Andy Robbins
"The industry as a whole is very young, but the capability of visualizing data problems and data security problems in this way is also relatively brand new." - Andy Robbins
"We focus on attack paths or risk that emerges out of a combination of the mechanics of a system, the configurations of that system, and the behaviors of users or identities in that system." - Andy Robbins
Socials and Resources:
https://twitter.com/_wald0
https://twitter.com/SpecterOps
https://specterops.io/
https://bloodhoundenterprise.io/
https://github.com/SpecterOps/BloodHound
Andy Robbins: The Evolution of Bloodhound podcasters.spotify.c...
27.05.2025 23:48 — 👍 7 🔁 3 💬 0 📌 0
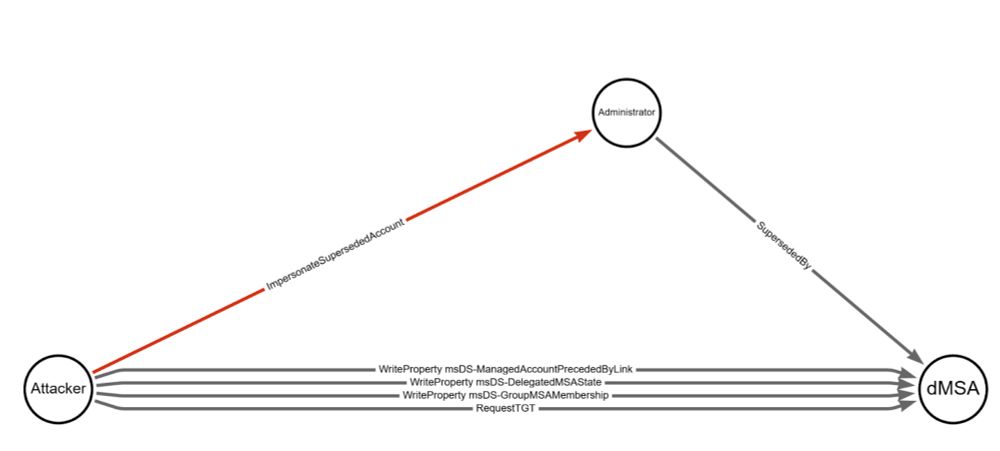
Understanding & Mitigating BadSuccessor - SpecterOps
Understanding the impact of the BadSuccessor AD attack primitive and mitigating the abuse via targeted Deny ACEs on Organizational Units.
BadSuccessor is a new AD attack primitive that abuses dMSAs, allowing an attacker who can modify or create a dMSA to escalate privileges and take over the forest.
Check out @jimsycurity.adminsdholder.com's latest blog post to understand how you can mitigate risk. ghst.ly/4kXTLd9
27.05.2025 21:11 — 👍 16 🔁 9 💬 0 📌 1
Did you miss #SOCON2025? Did you have a favorite talk you'd like to rewatch?
🎥 All presentations from SO-CON 2025 are now live at ghst.ly/socon25-talks.
💻 Slides for each talk are available at ghst.ly/socon25-slides.
19.05.2025 16:34 — 👍 5 🔁 5 💬 0 📌 0
Getting started w/ Mythic? We've got you covered.
@its-a-feature.bsky.social walks through the web UI basics, login process, & how to configure your default username/password. Check it out! ▶️ ghst.ly/user-interface
Watch the full series: ghst.ly/mythic-op
17.04.2025 20:12 — 👍 7 🔁 3 💬 0 📌 0
Thrilled to be speaking at @wearetroopers.bsky.social again this year - can’t wait to be back! 🥳
17.04.2025 16:00 — 👍 5 🔁 1 💬 0 📌 0
This has been a LONG time coming! This is just the beginning though :) I'll be recording more videos for updates, new features, workflow enhancements, and yes - a developer series too! Be sure to let me know what you do/don't like about this format and what kinds of things you'd like to see!
15.04.2025 20:14 — 👍 12 🔁 4 💬 1 📌 0
I had a great time at #socon2025! Big thanks to the SpecterOps crew for hosting. Slides for my "Hunting SMB Shares" talk are below for those who are interested.
Slides
github.com/NetSPI/Power...
PowerHuntShares
github.com/NetSPI/Power...
02.04.2025 12:48 — 👍 3 🔁 2 💬 0 📌 0

SOCON swag
Last week I had a fantastic experience at @specterops.bsky.social's #SOCON2025 and subsequent IDOT training. It was a great opportunity to get in touch with leading experts. Apparently I also bugged them enough to merge my small BloodHound contribution. github.com/SpecterOps/B...
11.04.2025 18:12 — 👍 8 🔁 1 💬 0 📌 0

Think NTLM relay is a solved problem? Think again.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31
08.04.2025 23:00 — 👍 27 🔁 20 💬 1 📌 2

Excited to be at @specterops.bsky.social SO-CON this week!! If you're around, I'll be presenting "Abusing AUs, Confusing the SOC" tomorrow bright & early:
31.03.2025 14:39 — 👍 15 🔁 7 💬 1 📌 0

Smile and say cheese! 😁
As you go between sessions at #SOCON2025 make sure to snap a photo with our display on Floor 29.
31.03.2025 17:11 — 👍 7 🔁 1 💬 0 📌 0

We are excited to see everyone at #SOCON2025 tomorrow! 🙌
Get the details on everything you need to know before arriving at the conference: specterops.io/so-con
30.03.2025 19:04 — 👍 16 🔁 4 💬 0 📌 0
Hey you know, just a gentle reminder. These are tough times. They’re tough for everyone in different ways, in different spectrums, because SO many important things are under attack.
Let’s try to be kind to one another, ok? It doesn’t cost much.
We’re stronger when we show each other grace.
23.03.2025 18:41 — 👍 274 🔁 31 💬 5 📌 4
The world has plenty of jerks, the Devil has too many advocates.
Choose kindness with intentionality.
It's life-changing.
Keep at it for long enough and it begins to feel selfish to be honest; I get so much back from it.
#MakeKindnessNormal
22.03.2025 17:54 — 👍 24 🔁 3 💬 1 📌 0

Attackers see what you don't: paths between your cloud & on-prem systems.
Our Chief Product Officer Justin Kohler will be at #GartnerIAM demonstrating how attackers exploit these connections & how Attack Path Management can help close these gaps. ghst.ly/4kzkFbB
20.03.2025 13:26 — 👍 4 🔁 3 💬 0 📌 0
I feel sorry for young people who will never experience the intense satisfaction of pressing a CRT monitor degauss button
17.03.2025 17:28 — 👍 496 🔁 90 💬 20 📌 7
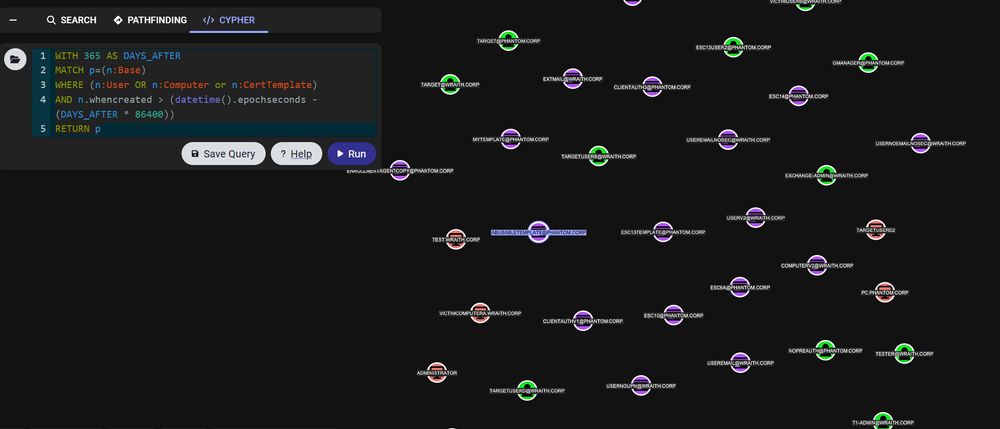
Happy #BloodHoundBasics day to all who celebrate!
Easily RETURN computers, users, and certificate templates created in the last X days where X can match anything you want. In this case we are looking for objects created in the last 365 days.
🧵: 1/3
07.03.2025 19:26 — 👍 6 🔁 3 💬 1 📌 0
We’re excited to keep pushing forward in eliminating Identity Attack Paths! As orgs grow more complex, Identity Risk is a top concern for security leaders. Proactively shutting down attack paths is the most direct way to reduce the risk of a major breach.
05.03.2025 19:29 — 👍 7 🔁 1 💬 0 📌 0

Andy Robbins: The Evolution of Bloodhound by Phillip Wylie Show
About The Guest:Andy Robbins is the Principal Product Architect at SpecterOps and one of the original 13 founding members of the company. He has a background in pen testing and red teaming and is the co-creator of Bloodhound, a popular open-source tool for attack path mapping in Active Directory environments.
Summary:Andy Robbins, the Principal Product Architect at SpecterOps, joins host Phillip Wylie to discuss the evolution of Bloodhound, a tool for attack path mapping in Active Directory environments. Andy shares the origin story of Bloodhound and how it was developed to solve the problem of finding attack paths in complex environments. He explains the graph theory behind Bloodhound and how it visualizes data to help practitioners and defenders understand and mitigate security risks. Andy also discusses the recent release of Bloodhound Community Edition (CE) and the improvements it brings, including faster data ingest, query times, and a friendlier user experience. He highlights the focus on practical attack primitives and abuse primitives in Bloodhound and the goal of making attack paths a non-issue for organizations. Andy concludes by sharing valuable advice for those looking to advance in the industry, emphasizing the importance of understanding and solving real problems and being loyal to people rather than companies.
Key Takeaways:
Bloodhound is a tool for attack path mapping in Active Directory environments, using graph theory to visualize data and identify security risks.
Bloodhound Community Edition (CE) brings improvements such as faster data ingest, query times, and a friendlier user experience.
Bloodhound focuses on practical attack primitives and abuse primitives to solve real security problems and make attack paths a non-issue for organizations.
Quotes:
"If we give people an excellent experience for free, then enough of those people will choose to become paying customers that we have a viable business." - Andy Robbins
"The industry as a whole is very young, but the capability of visualizing data problems and data security problems in this way is also relatively brand new." - Andy Robbins
"We focus on attack paths or risk that emerges out of a combination of the mechanics of a system, the configurations of that system, and the behaviors of users or identities in that system." - Andy Robbins
Socials and Resources:
https://twitter.com/_wald0
https://twitter.com/SpecterOps
https://specterops.io/
https://bloodhoundenterprise.io/
https://github.com/SpecterOps/BloodHound
Andy Robbins: The Evolution of Bloodhound podcasters.spotify.c...
03.03.2025 23:32 — 👍 10 🔁 3 💬 0 📌 0
The Cyber Security Recruiters talks to Jason Frank, Chief Operations Officer, SpecterOps
Enjoy the videos and music you love, upload original content, and share it all with friends, family, and the world on YouTube.
Our COO @jasonjfrank.bsky.social recently joined The Cyber Security Recruiter Podcast to chat about SpecterOps and how we approach recruiting. He also his perspective on leadership and guiding a growing team.
Listen to the full conversation: ghst.ly/41bR9B7
14.02.2025 21:49 — 👍 3 🔁 1 💬 0 📌 0

Happy #BloodHoundBasics Day!
Did you know BloodHound started with just 3 node types and a few edges? Today, it supports 36 node types and 113 edge types, uncovering a vast array of attack paths.
Explore more in our docs ➡️ ghst.ly/3WSKoS7
s/o @jonas-bk.bsky.social
07.02.2025 20:02 — 👍 4 🔁 2 💬 0 📌 0
Hello world.
25.01.2025 16:10 — 👍 8 🔁 0 💬 1 📌 0
Logging into things I shouldn't.
Red Team Lead @ NVIDIA
Security person who likes writing code
CISO, Thinkerer, Advisor, Mentor
I like to make stuff and do hacks. Consultant penetration tester for 9 years. #cybersecurity #infosec #hacking Denver CO. https://github.com/ninjastyle82
Adversary Simulation @ SpecterOps
Her Majesty the King
She/They
Lurker
Medievalist
Painfully awkward
I do the security stuff.
I'd rather be on stage in a unicorn suit because I'm shy.
Blog @ www.InnoVirtuoso.com | InfoSec, Cyber, AI Enthusiast | I write about Tech and News, AI, BCI, and other IT stuff.
Contact me at 📧 info@innovirtuoso.com
Assemblymember. Democratic Nominee for Mayor of NYC. Running to freeze the rent, make buses fast + free, and deliver universal childcare. Democratic Socialist. zohranfornyc.com
We are Microsoft's global network of security experts. Follow for security research and threat intelligence. https://aka.ms/threatintelblog
Director of Cybersecurity @eff.org
Co-founder of @stopstalkerware.bsky.social
These opinions are my own, not my employers’
I did a TED talk once
Specializing in pen testing, red teaming, and Active SOC. We share our knowledge through blogs, webcasts, open-source tools, and Backdoors & Breaches game.
blackhillsinfosec.com & poweredbybhis.com
- [REDACTED]’s husband
- Bear's dad
- Recovering sysadmin
- Microsoft MVP (PowerShell/Identity)
- Forever student
- Open-Source Toolmaker
- Whisk(e)y fan
- College football fan (Go Blue!)
- Stuff: https://dotdot.horse
responsible tech, science nerd, comics spouse. He/Him
Posts are short form opinions and should be post scripted with "in some relevant situations"
freelance tech journalist, copywriter & editor ✨available for commissions✨
☎️ Signal: carly.44
✉️ carlypagewrites@gmail.com
✍️ carlypagewrites.co.uk
Past: Host of "Tribe of Hackers"; Assoc. Producer "Darknet Diaries."
Current: Cybersecurity researcher and executive. Also, father of the fastest climber who has ever lived. Seriously.
Warning: I talk about my son ALOT
“Ut scandis, alios subleva.”
Sen. Sanders of Vermont, Ranking Member of the U.S. Senate Committee on Health, Education, Labor & Pensions, is the longest-serving independent in congressional history.
PowerShell inventor, Reader, Science & Geopolitics geek, Google Distinguished Engineer

















