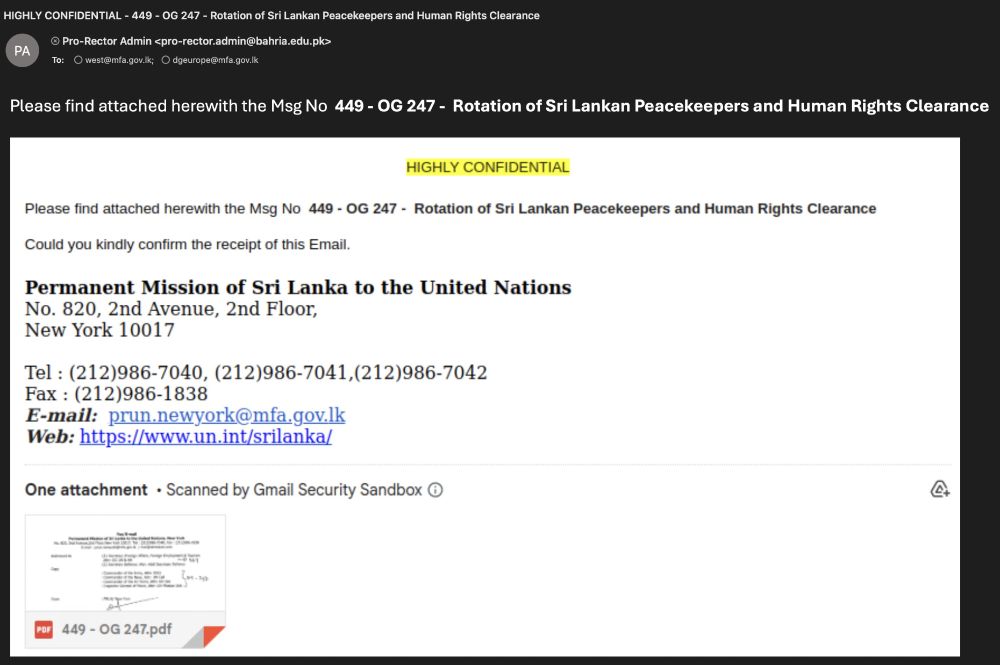
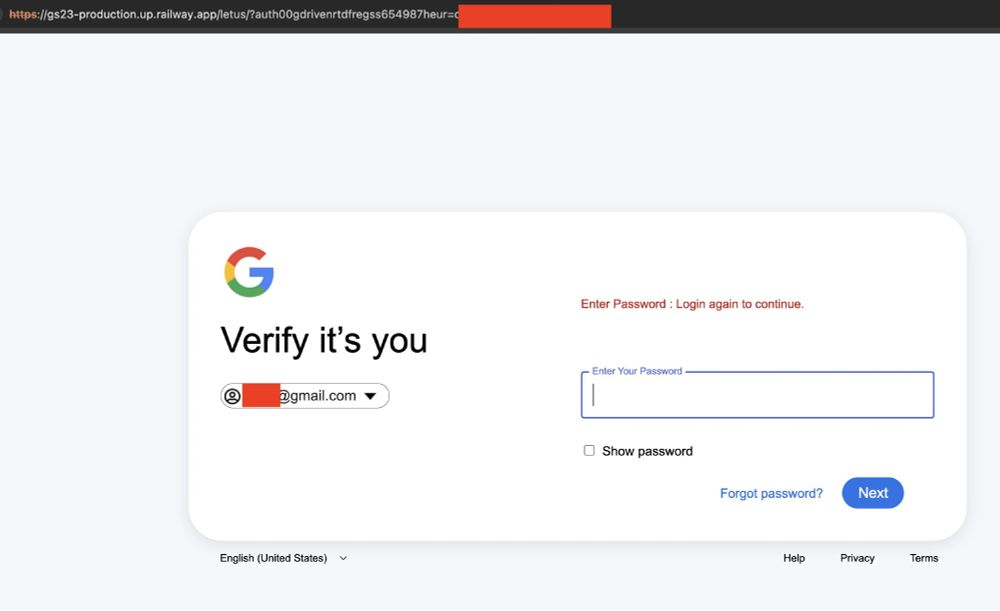
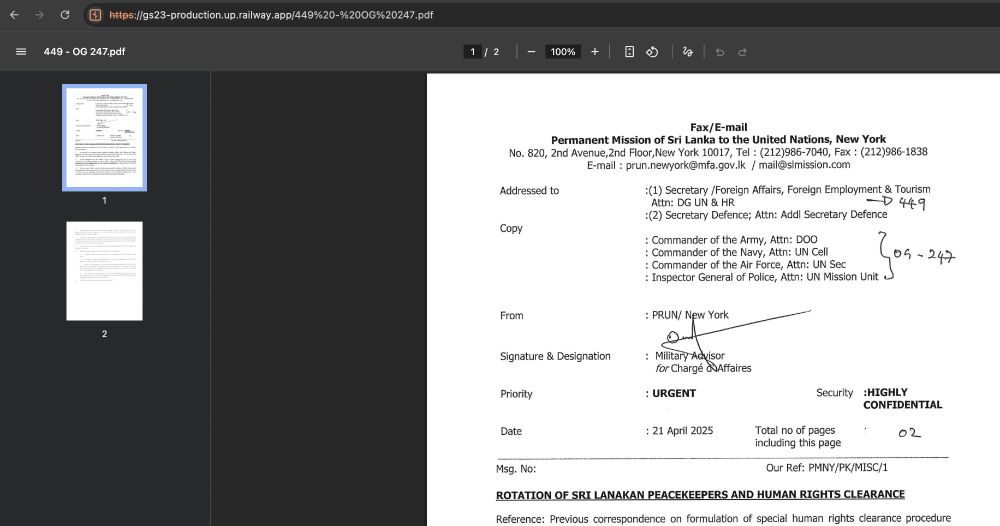
This has been confirmed today: operation-endgame.com
Europol took down servers for the Rhadamanthys infostealer, the VenomRAT, and the Elysium botnet
13.11.2025 12:23 — 👍 28 🔁 7 💬 1 📌 0

FIRST — Forum of Incident Response and Security Teams
Que "The Final Countdown" by Europe 🎶 and lock in 💻-- it's time for final submissions for #FIRSTCTI26 #lastcall #timesup 🔗 go.first.org/EHUnv
12.11.2025 18:43 — 👍 2 🔁 2 💬 0 📌 0
Yep, I've been pwned. 2FA reset email, looked very legitimate.
Only NPM affected. I've sent an email off to @npmjs.bsky.social to see if I can get access again.
Sorry everyone, I should have paid more attention. Not like me; have had a stressful week. Will work to get this cleaned up.
08.09.2025 15:15 — 👍 188 🔁 60 💬 15 📌 22

Hackers stole Social Security numbers during Allianz Life cyberattack | TechCrunch
The U.S. insurance giant tells state regulators that Social Security numbers were among the personal information stolen in its mid-July cyberattack.
New, by me: The hackers who breached Allianz Life earlier this month and stole the personal information belonging to the "majority" of its 1.4 million customers, also took Social Security numbers during the breach, per new filings with U.S. states.
30.07.2025 18:02 — 👍 16 🔁 5 💬 0 📌 0
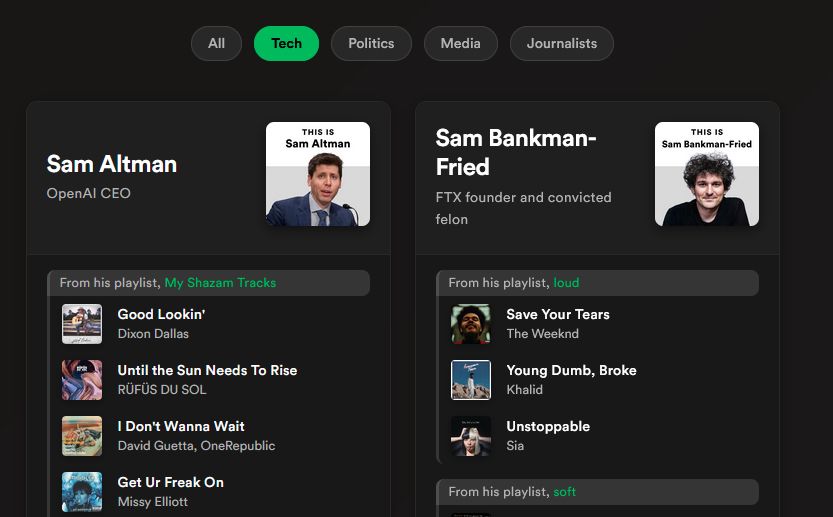
LOL... someone scrapped celebrity Spotify accounts/playlists and leaked their music preferences
The *chef's kiss* here is the name of the site: Panama Playlists 😆
panamaplaylists.com
31.07.2025 15:03 — 👍 34 🔁 12 💬 3 📌 1
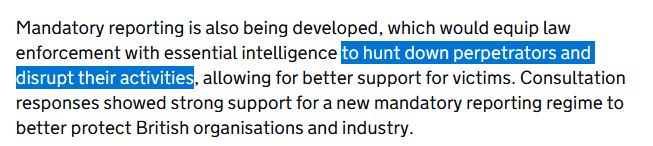
Screenshot of text that reads: "Mandatory reporting is also being developed, which would equip law enforcement with essential intelligence to hunt down perpetrators and disrupt their activities, allowing for better support for victims. Consultation responses showed strong support for a new mandatory reporting regime to better protect British organisations and industry."
This is by far the coolest part in the UK's proposed ransomware ban and mandatory reporting proposal
www.gov.uk/government/n...
22.07.2025 13:22 — 👍 10 🔁 1 💬 1 📌 1
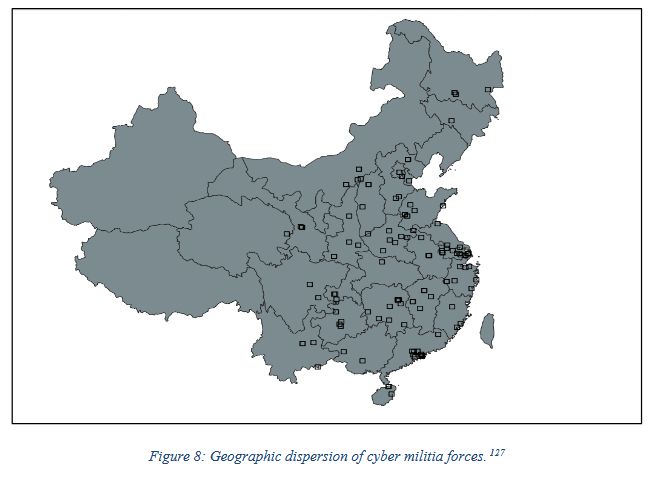
"This report presents the first detailed study of China’s cyber militia system since 2015. It draws from an analysis of 136 individual militia units, as well as authoritative Chinese-language military writings and mobilization documents."
margin.re/mobilizing-c...
09.07.2025 19:59 — 👍 18 🔁 8 💬 0 📌 0
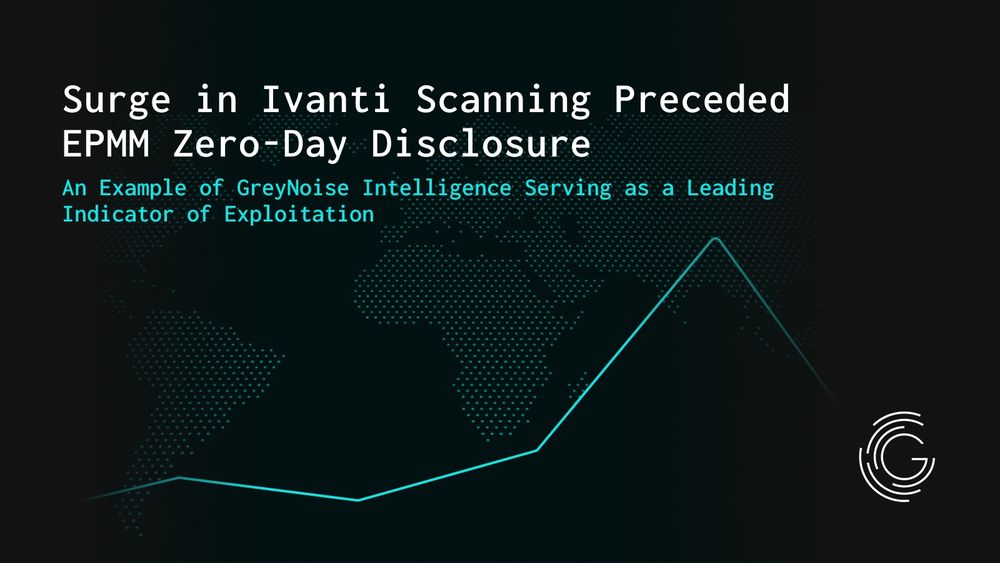
GreyNoise observed a major spike in scanning against Ivanti products weeks before two zero-days were disclosed in Ivanti EPMM. Full update: www.greynoise.io/blog/surge-i...
#Ivanti #GreyNoise #Cybersecurity #ZeroDays
20.05.2025 19:54 — 👍 8 🔁 6 💬 0 📌 0

New Russia-affiliated actor Void Blizzard targets critical sectors for espionage | Microsoft Security Blog
Microsoft Threat Intelligence has discovered a cluster of worldwide cloud abuse activity conducted by a threat actor we track as Void Blizzard, who we assess with high confidence is Russia-affiliated and has been active since at least April 2024. Void Blizzard’s cyberespionage operations tend to be highly targeted at specific organizations of interest to Russia, including in government, defense, transportation, media, non-governmental organizations (NGOs), and healthcare sectors primarily in Europe and North America.
Microsoft has discovered a cluster of worldwide cloud abuse activity by new Russia-affiliated threat actor Void Blizzard (LAUNDRY BEAR), whose cyberespionage activity targets gov't, defense, transportation, media, NGO, and healthcare in Europe and North America. https://msft.it/63324S9Jkp
27.05.2025 09:55 — 👍 32 🔁 23 💬 1 📌 5

Dutch intelligence discover a new Russian APT—LAUNDRY BEAR
www.aivd.nl/documenten/p...
Microsoft calls it Void Blizzard. Their report is here: www.microsoft.com/en-us/securi...
27.05.2025 12:11 — 👍 21 🔁 12 💬 1 📌 1
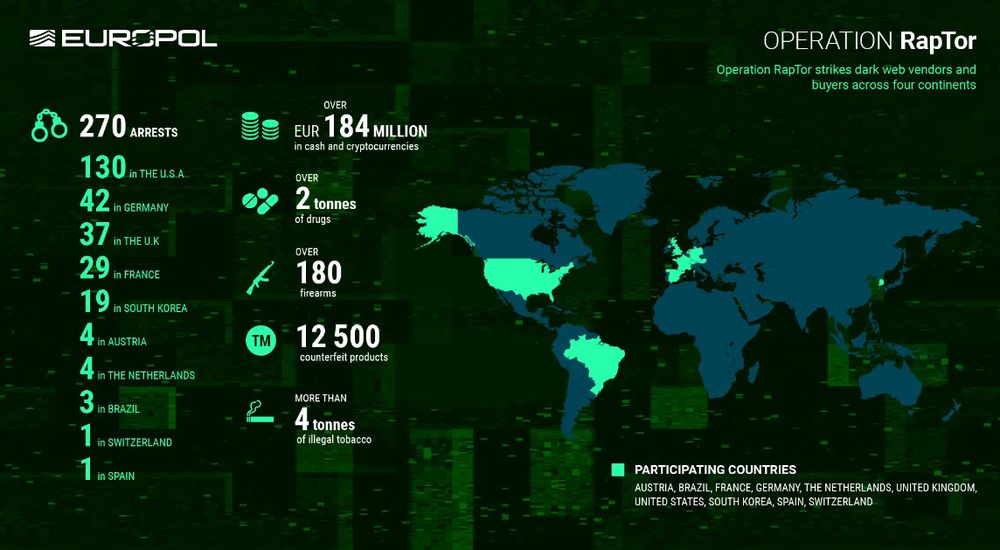
"A global law enforcement operation coordinated by Europol has struck a major blow to the criminal underground, with 270 arrests of dark web vendors and buyers across ten countries"
www.europol.europa.eu/media-press/...
22.05.2025 15:50 — 👍 12 🔁 3 💬 1 📌 0
cc @likethecoins.bsky.social
22.05.2025 11:41 — 👍 0 🔁 0 💬 0 📌 0
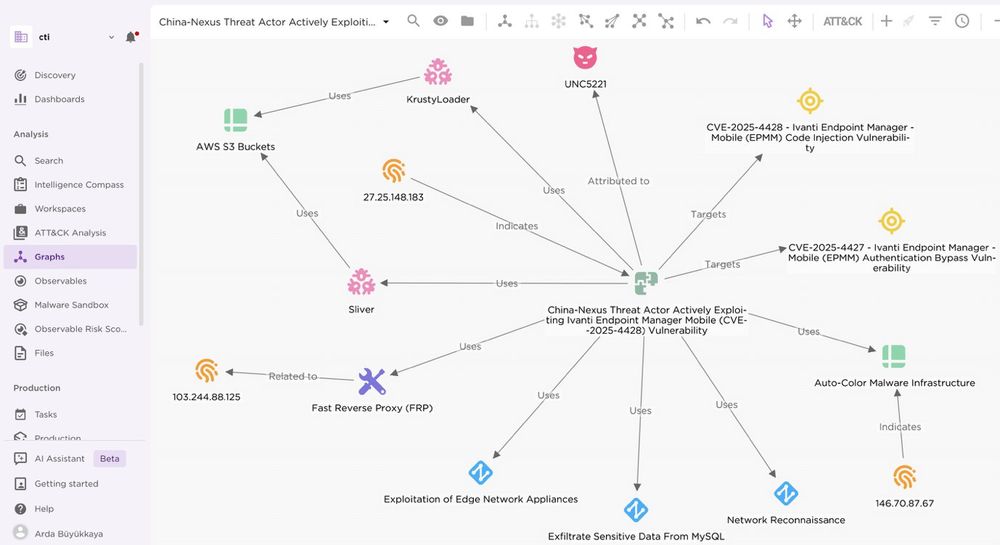
🇨🇳 UNC5221 China-Nexus Threat Actor Actively Exploiting Ivanti EPMM (CVE-2025-4428).Targets critical networks like US airports and Telecommunications companies in EU. Exfiltrating sensitive data from managed mobile devices. #cyber
Here is the full report:
blog.eclecticiq.com/china-nexus-...
22.05.2025 11:34 — 👍 4 🔁 1 💬 1 📌 0

-Ransomware IAB spreads trojanized KeePass installer
-APT28 targets email servers with XSS attacks
-Good report on DPRK cyber and IT worker schemes
-Russia uses USAID shutdown in info-op targeting Moldova
-RU disinfo group Storm-1516 is behind the Macron coke memes
16.05.2025 08:29 — 👍 6 🔁 1 💬 1 📌 0
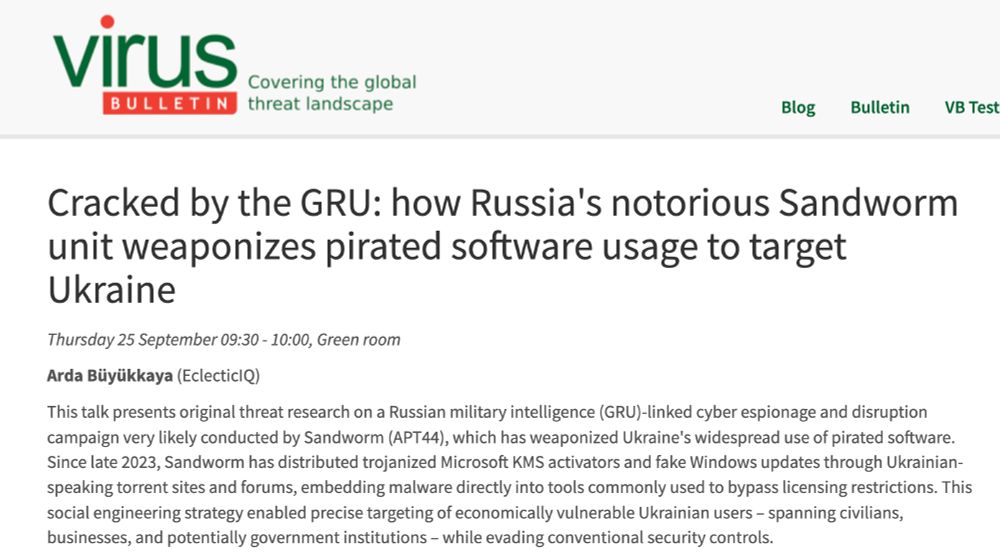
🎉 Happy to share that my talk has been accepted at Virus Bulletin! I’ll be presenting in 🇩🇪 Berlin on Friday, September 26 at VB2025:
Details: www.virusbulletin.com/conference/v...
See you there! #vbconference #VB2025
02.05.2025 14:27 — 👍 5 🔁 2 💬 0 📌 0
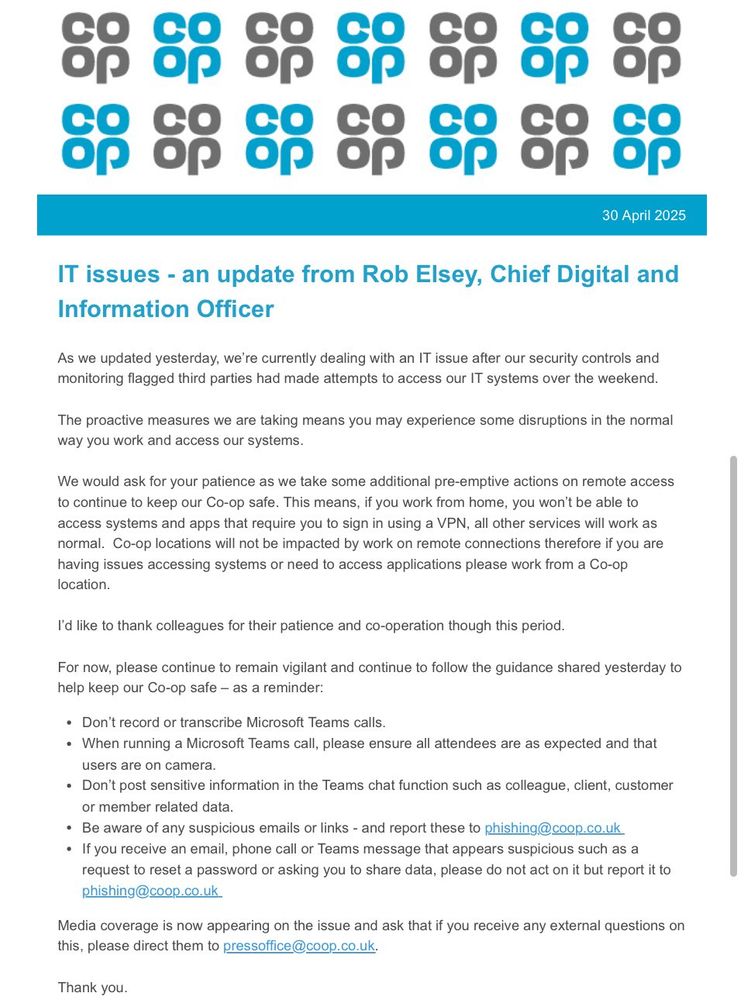
Microsoft Teams appears to have been used as part of the cyber kill chain in the Co-Op hack. I've recently seen similar tactics, where threat actors employed voice phishing via Teams calls. It’s a threat worth watching.
01.05.2025 19:43 — 👍 0 🔁 0 💬 0 📌 0
Podcast: risky.biz/RBNEWS418/
Newsletter: news.risky.biz/risky-bullet...
-French government grows a spine and calls out Russia's hacks
-Marks & Spencer sends staff home after ransomware attack
-China accuses US of hacking cryptography provider
-AirBorne vulnerabilities impact Apple's AirPlay
30.04.2025 09:30 — 👍 30 🔁 6 💬 1 📌 0
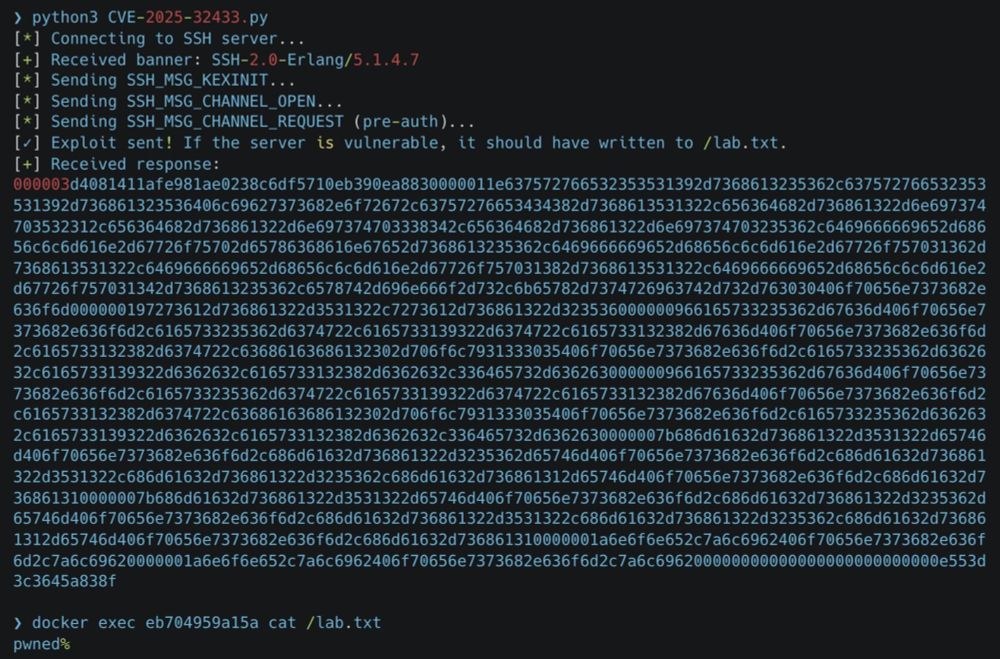
🚨 Erlang SSH RCE (CVE-2025-32433) is a significant supply chain risks to ICS and OT devices, particularly critical networking equipment like routers, switches, and smart sensors. The public availability of a POC makes this vulnerability especially concerning, as it is straightforward to exploit.
25.04.2025 20:02 — 👍 1 🔁 1 💬 0 📌 0
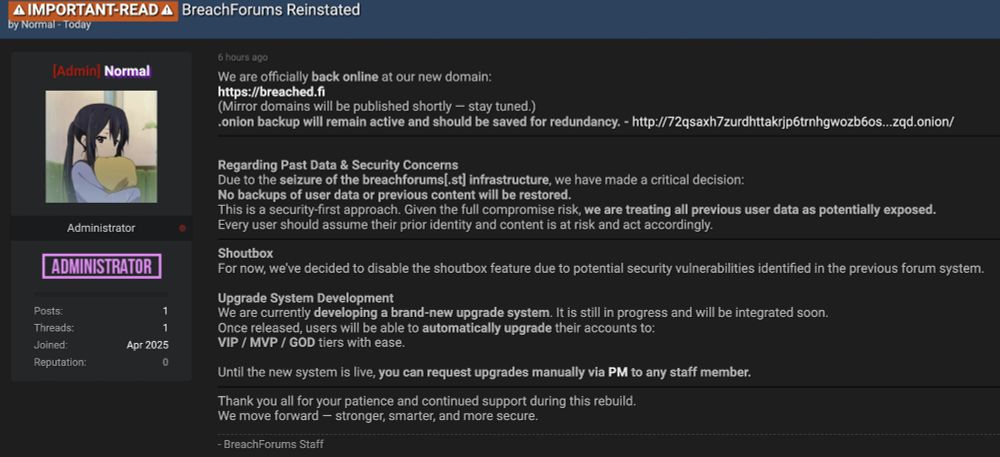
Since April 15, 2025, BreachForums 2 was offline. Admin “Normal” confirmed its return at breached[.]fi, with no prior data restored. The new site faces skepticism, with some calling it a potential honeypot, likely pushing threat actors toward other platforms.
23.04.2025 20:59 — 👍 3 🔁 3 💬 0 📌 0
BreachForums has reportedly resumed operations under a new domain, breached[.]fi
23.04.2025 20:32 — 👍 1 🔁 0 💬 0 📌 0
Cyber Intelligence Analyst at RANE
Available for media inquiries 🙂↔️🙂↕️
No bio here. Read my blog (https://rly0nheart.com) if you're bored.
Security researcher @ Cisco Talos. / Ex-Google TAG / Black Hat & HITCON review board / Organiser of Rhacklette.
⚖️ LL.M Candidate in Corporate & Commercial Law @ Maastricht University | 🎓 Public Int'l Law LL.M alumni @ University of Oslo | 💼 Privacy Lawyer | interested in tech, cybersecurity, data protection, international law & geopolitics | 📍🇪🇪 | views my own
Coding @ github.com/qix-, making an operating system @ github.com/oro-os
We are Microsoft's global network of security experts. Follow for security research and threat intelligence. https://aka.ms/threatintelblog
Security information portal, testing and certification body.
Organisers of the annual Virus Bulletin conference.
Security Test & Threat intelligence Engineer
@virusbtn.bsky.social
🇷🇴 🇪🇺
Master of (Keeping/Stealing) your Secrets | Security Advisor & Intel Analyst | Civil Servant @ BE | Klopjacht-speurder | IT Eng. + Pol. Sci. | Posts my own
@i_ball@infosec.exchange on Mastodon
But have you tried turning it off and back on again? No, I have been hacked. 👨💻 Based in Milan, Italy 🤌, my heart belongs to Dublin's chips. ☘️💚 Cyber something. 🤖
Live from lovely Saint Paul, Minnesota.
He/him
Pit bull advocate, dog rescue volunteer, dog foster.
I have no idea what to do with a new social media network.
My feed will probably be memes, dogs, and politics.
Cybersecurity dude that gets called robotic by his friends. Probably talking about sports or video games. https://linktr.ee/ben_alterman
Creator of Have I Been Pwned. Microsoft Regional Director. Pluralsight author. Online security, technology and “The Cloud”. Australian.
Principal analyst at Google's Threat Intelligence Group. Former Deputy National Intelligence Officer for East Asia and senior nonresident fellow at the Atlantic Council. Views my own.
https://markparkeryoung.net
🔳 founder of @greynoise.io. computers, networks, technology enthusiast. big goober.