
If you appreciate the under-reported #InfoSec & #DataPrivacy news content I share every week, please support what I do by signing up for my newsletter. sherpaintelligence.substack.com
I'm really proud of the content I provide and subscribers make my work possible.
Repost & share with your network!
01.02.2026 22:39 — 👍 5 🔁 5 💬 0 📌 1

Screenshot of my blog post to share information on this Lumma Stealer infection with follow-up malware.
2025-12-30 (Tuesday): #LummaStealer infection with follow-up malware. A #pcap of the infection traffic, the associated #Lumma with follow-up #malware samples, and some IOCs are available at www.malware-traffic-analysis.net/2025/12/30/i...
31.12.2025 05:37 — 👍 7 🔁 3 💬 0 📌 0


Sunset over a frozen lake
30.12.2025 23:27 — 👍 1 🔁 0 💬 0 📌 0
Our Labs love the snow. They’re 11 & 12, and it makes them act like puppies.
29.11.2025 19:58 — 👍 0 🔁 0 💬 0 📌 0
 23.11.2025 02:09 — 👍 1 🔁 0 💬 0 📌 0
23.11.2025 02:09 — 👍 1 🔁 0 💬 0 📌 0
“He got you, didn’t he?”
18.11.2025 22:38 — 👍 1 🔁 0 💬 0 📌 0


If I won the lottery, I might not tell anyone, but there would be signs.
18.11.2025 01:18 — 👍 3 🔁 0 💬 0 📌 0
The back story on how that performance came together is amazing, too. And so many of the songs have cool stories behind them (or after them, like Onyx & Biohazard).
18.11.2025 01:00 — 👍 3 🔁 0 💬 0 📌 0

I mean, the movie was the excuse to make the soundtrack. But who cares? They made the soundtrack.
18.11.2025 00:57 — 👍 1 🔁 0 💬 0 📌 0
Paul Melson joined us this year as our keynote speaker to talk about the history of crimeware and its evolution through the years.
In his keynote he also gives some good advice to those who are in the field and creating their professional network. Check out what he had to say!
17.10.2025 15:11 — 👍 3 🔁 1 💬 1 📌 0
If you’re not already alerting on
CONHOST.EXE spawning CMD.EXE spawning WGET.EXE
or
CONHOST.EXE spawning CONHOST.EXE spawning CONHOST.EXE
you’re gonna want to close that gap today.
03.10.2025 16:04 — 👍 1 🔁 0 💬 0 📌 0
Are weekly dental cleanings a thing?
26.09.2025 00:14 — 👍 1 🔁 0 💬 0 📌 0
YouTube video by SLEUTHCON
Keynote | SLEUTHCON 2025
ICYMI: Paul Melson, VP of Cyber Intelligence Engineering at Capital One, delivered the SLEUTHCON 2025 keynote!
Watch here >> www.youtube.com/watch?v=9FvB...
10.09.2025 16:19 — 👍 6 🔁 2 💬 0 📌 0
That’s great
30.08.2025 19:19 — 👍 0 🔁 0 💬 0 📌 0

Happy International Dog Day, hope you spent it with your best friends
26.08.2025 23:45 — 👍 2 🔁 0 💬 0 📌 0
It’s that time again, apparently.
28.06.2025 16:52 — 👍 1 🔁 2 💬 0 📌 0

Paul Melson's Brief History of Crime[ware] was a lovely (?!) trip down memory lane. I'm old too, @pmelson.bsky.social
#SLEUTHCON #traumamemories
06.06.2025 13:37 — 👍 5 🔁 1 💬 0 📌 0
It is my position that Chatham House rules and TLP should extend to any trolling that takes place in those channels and venues.
04.05.2025 15:35 — 👍 3 🔁 1 💬 1 📌 0

New keynote drop: Paul Melson is taking the SLEUTHCON stage to dissect the rise of crime[ware]—how it started, how it scaled, and how we shut it down.
23+ yrs defending networks. ScumBots founder. Now VP @ Capital One.
🎤 June 6
📍IRL + virtual
🎟️ Tix moving fast - sleuthcon.com
🗓️ CFP closes April 18
14.04.2025 18:02 — 👍 21 🔁 8 💬 0 📌 1
So simple, but what a can of worms. It emphasizes why detection pipelines with multiple, conditional rounds are needed. Ideally you’d catch this with a simple string match for the reg key after it’s been through a generic deobfuscation round that drops non-alphanumeric characters.
08.12.2024 00:55 — 👍 2 🔁 0 💬 0 📌 0

Took this at sunset in Fall in Minnesota:
08.12.2024 00:39 — 👍 2 🔁 0 💬 0 📌 0
Today I am thankful for all of the folks working a shift and watching the wires to keep us safe. I see you and I appreciate you.
28.11.2024 14:58 — 👍 1 🔁 0 💬 0 📌 1
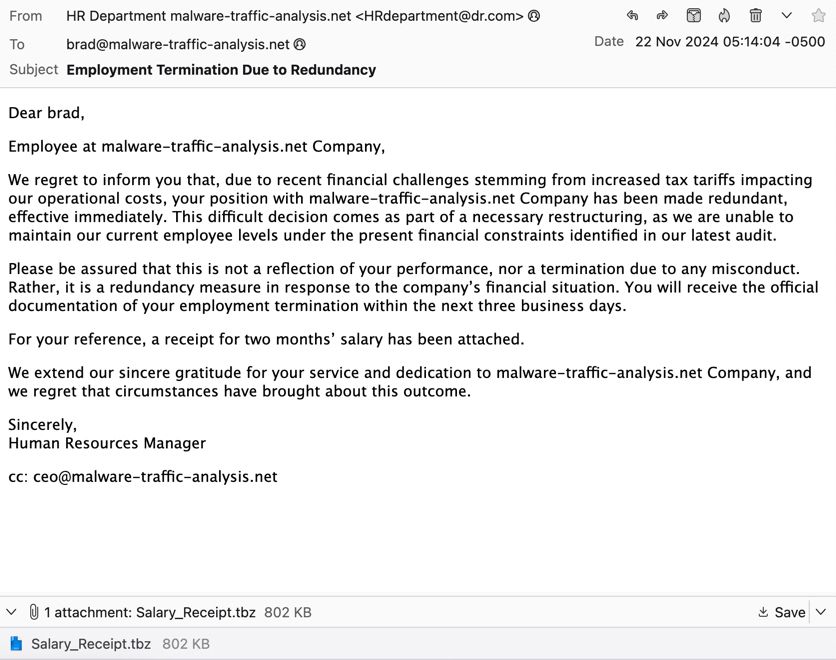
Screenshot of malicious spam (malspam) with malware file attachment.
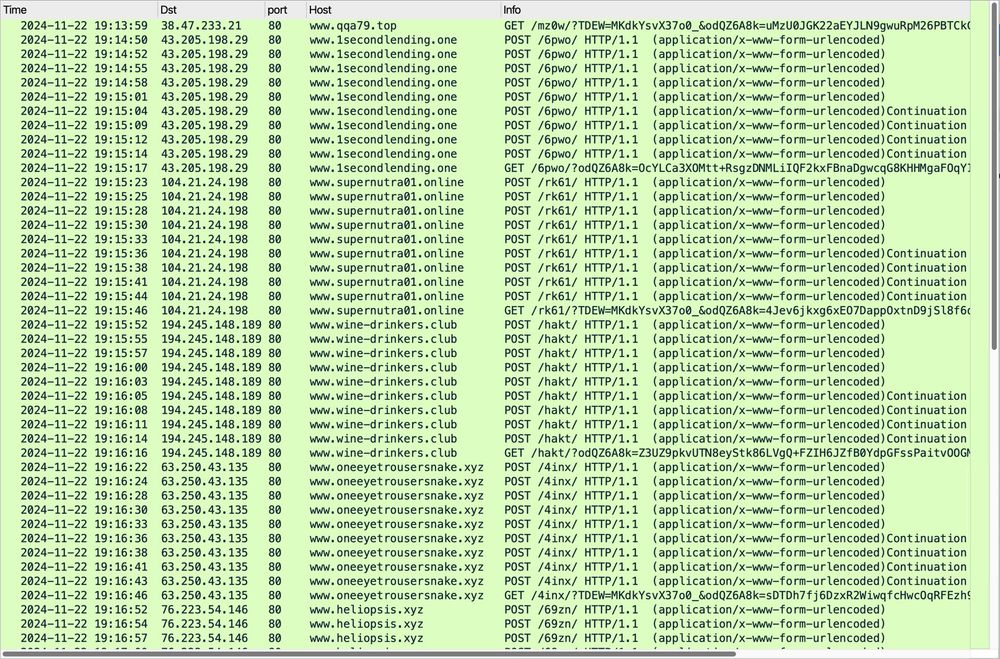
Traffic from the XLoader (Formbook) infection filtered in Wireshark.
2024-11-22 (Friday) #XLoader / #Formbook: I've been fired by my non-existent HR department. At least I got a "salary-receipt.exe" bazaar.abuse.ch/sample/003b5...
Tria.ge and Any.Run don't identify the malware, but Joe Sandbox does: www.joesandbox.com/analysis/156...
Also runs in my lab just fine
22.11.2024 19:42 — 👍 17 🔁 10 💬 2 📌 0
Security Analyst. Panther Modern.
Engineer at Security Onion Solutions.
Professor at Canisius University.
Organizer at Infosec 716 and BSides Buffalo.
DFIR, security, networking, all things tech, OneWheel, Radinn, travel, LEGO, and probably a whole lot more in small and sporadic bits. (Squirrel!)
Fierce and unapologetic ally. He/him/his.
The largest collection of malware source code, samples, and papers on the internet.
Password: infected
(unofficial, this is a bot! Maintained by @yjb.bsky.social, the bot can't handle retweets, video, and maybe a few other things)
Follow us for the latest blogs and IOCs from Team Cymru's S2 Threat Research team.
Chief Research Officer @ Unit 221B
most reliable way to reach me is my company's outreach form on the website
my other urls:
https://infosec.exchange/@nixonnixoff
https://www.linkedin.com/in/allison-nixon-81822124/
don't bother contacting me on twitter
Founder of The Vertex Project (@vtxproject)
Father of the #APT1 Report @Mandiant.
Inventor of #synapse, #vivisect, UNCs, imphash, ...
DEFCON CTF Champion, Founder of Kenshoto
Craft beer explorer 🍺 | Sharing fun reviews, brewery journeys, and must-try pours. Follow for beer pics, ratings, and bucket-list brews. Cheers! #TheBeerAdviser #CraftBeerLife
https://www.sleuthcon.com
A new DC hacker conference: Bringing together builders, breakers, and fixers to do cool shit.
Jan. 24-25, 2026
districtcon.org
@ESET Distinguished Researcher | alum of McAfee, Microsoft MVP, Tribal Voice, Zultys | Mod @Lenovo, @Neowin.Net, Scots Newsletter forums | Intel Insider Council | Repost ≠ endorse
head in the clouds. opinions are my own and not the views of my employer.
oh great, now I’m on bluesky
The only way out is through | Stringer, Central Intelligence Corporation
work time: defender
fun time: malware hoarder/puzzle solver/capacity tester
member of:
@cryptolaemus.bsky.social
fan of:
@hatching_io
@sublime_sec
/* Security & Malware Research | Developer for http://MalBeacon.com | Poking holes in everything & writing about it | Read here: http://fr3d.hk/blog */
Professional writer and talker; sports things & nerd stuff. Feature journalism, NFL analysis, books & stories, and my podcast about old video game magazines: @funfactorpod.com. Partnerships director @rankmivote.bsky.social. He/him. #ADHD
A security firm providing Incident Response, Proactive Threat Assessments, Trusted Advisory, and Threat Intelligence // volexity.com
CYBERWARCON is a one-day conference in Arlington, VA focused on the specter of destruction, disruption, and malicious influence on our society through cyber capabilities.
cyberwarcon.com





 23.11.2025 02:09 — 👍 1 🔁 0 💬 0 📌 0
23.11.2025 02:09 — 👍 1 🔁 0 💬 0 📌 0


















