


On stage at #x33fcon for the lightning talks! Web payloads management, EDR bypasses and insights into CVE-2025-33073🔥
12.06.2025 11:02 — 👍 4 🔁 2 💬 0 📌 0@b-paul.bsky.social
Pentest / redteam @synacktiv.com



On stage at #x33fcon for the lightning talks! Web payloads management, EDR bypasses and insights into CVE-2025-33073🔥
12.06.2025 11:02 — 👍 4 🔁 2 💬 0 📌 0
It's now time for @matthieub.bsky.social and @b-paul.bsky.social to present Azure conditional access policies ☁️ #SSTIC2025
05.06.2025 12:35 — 👍 7 🔁 4 💬 0 📌 0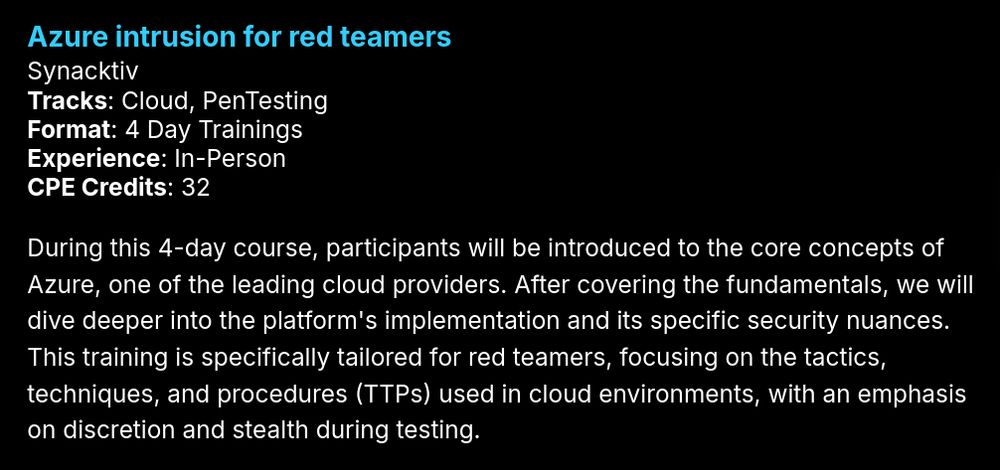
Last chance to grab early bird tickets for our Azure Intrusion training at #BHUSA 2025! Join us in Las Vegas for 100% offensive, hands-on content showcasing real-world attack techniques against modern Azure environments! @blackhatevents.bsky.social outline at www.blackhat.com/us-25/traini...
19.05.2025 13:03 — 👍 2 🔁 3 💬 0 📌 0
Azure intrusion for red teamers
by Paul Barbé & Matthieu Barjole
www.hexacon.fr/trainer/barb...

From firmware dumps to wireless exploration — check out our latest dive into DVB receiver analysis and the hidden attack surface it exposes!
www.synacktiv.com/en/publicati...
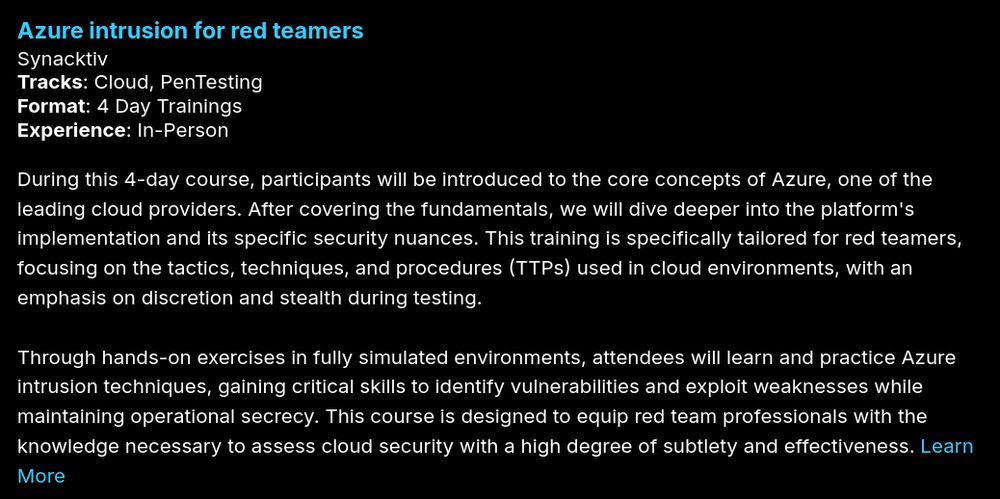
Want to master cutting-edge techniques for attacking Azure?
Join us this summer at @blackhatevents.bsky.social in Vegas for a deep dive into red teaming on Azure, M365, Azure DevOps, and hybrid infrastructures.
Early bird tickets available until May 23rd!
www.blackhat.com/us-25/traini...

In our latest article, @croco-byte.bsky.social and @scaum.bsky.social demonstrate a trick allowing to make Windows SMB clients fall back to WebDav HTTP authentication, enhancing the NTLM and Kerberos relaying capabilities of multicast poisoning attacks!
www.synacktiv.com/publications...
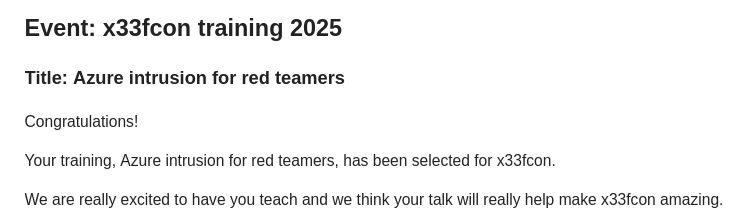
Exciting news, our Offensive Azure training has been accepted at #x33fcon! 🥳 Can’t wait to see you there and dive into the latest techniques for attacking Azure environments!
19.02.2025 11:00 — 👍 5 🔁 2 💬 0 📌 0In 2024, Fortinet deployed several patches for CVE-2023-42791 and CVE-2024-23666, discovered by @aeinot.bsky.social, @b-paul.bsky.social and load. These vulnerabilities allow, from read-only access to a FortiManager, to execute code as root and thus take control of all managed FortiGates.
18.02.2025 12:25 — 👍 8 🔁 3 💬 0 📌 1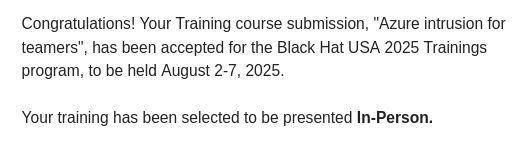
Yay! Our offensive Azure training was accepted at BlackHat USA 2025 🥳 Can't wait to see you there and share cutting-edge techniques for attacking Azure environments!
20.01.2025 09:24 — 👍 9 🔁 7 💬 0 📌 0A few weeks ago, Rapid7 released a new version of #Velociraptor to patch CVE-2024-10526, a local privilege escalation discovered by jbms. You can read the advisory here:
www.synacktiv.com/advisories/l...