
Team picture
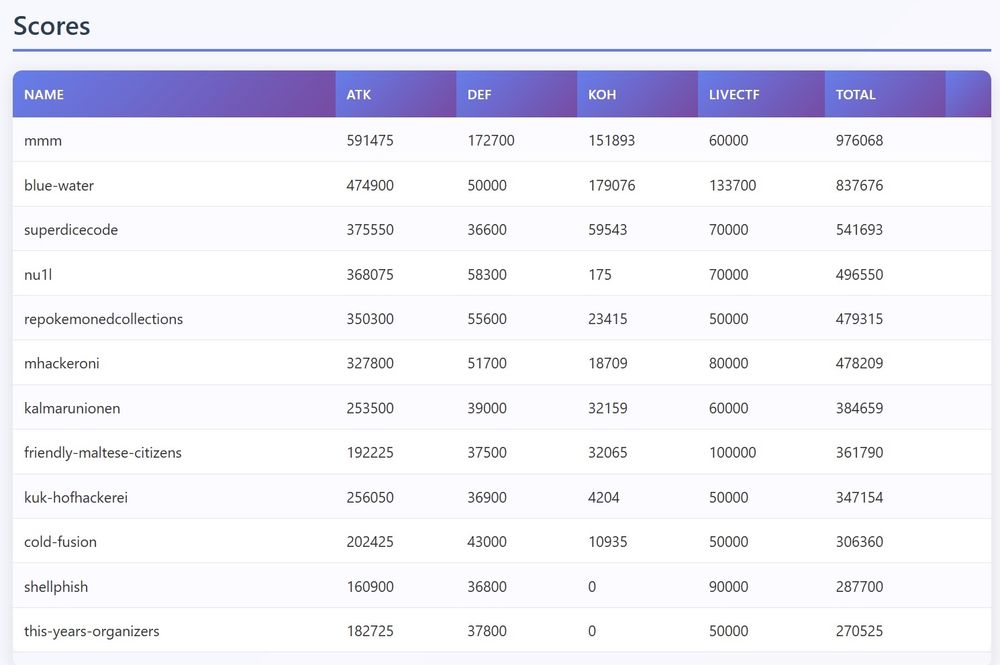
Final scoreboard
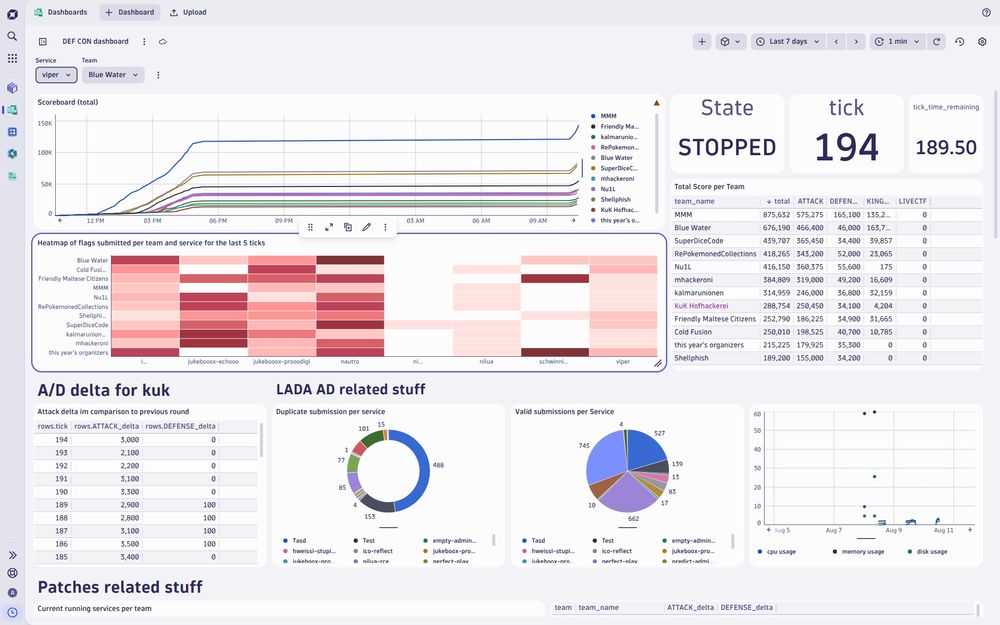
Team dashboard
We got 9th place at @defcon.bsky.social #CTF! Props to all finalists for an intense fight over the past three days and congrats to MMM for taking the win.
Thanks to Nautilus Institute for the neat setup this year, we had a blast.
Until next time, Vegas!
#DEFCON #DEFCON33
12.08.2025 02:04 — 👍 18 🔁 2 💬 2 📌 4
Thanks to @v4m1n.bsky.social , @supersingular.bsky.social, @notimaginary.bsky.social, Stefan Gast, @j4nw.bsky.social, @tom-crypt.bsky.social and @gruss.cc for the great collaboration!
13.06.2025 13:47 — 👍 6 🔁 0 💬 0 📌 0
It protects against fine-grained performance-counter attacks on TEE's, while keeping coarse-grained trends intact for legitimate use cases.
hannesweissteiner.xyz/pdfs/teecorr...
13.06.2025 13:47 — 👍 5 🔁 0 💬 1 📌 0
I am happy to announce that my first paper has been accepted at USENIX Security!
We propose TEEcorrelate, a mitigation that statistically decorrelates reported performance counters from real ones during TEE execution.
13.06.2025 13:47 — 👍 22 🔁 8 💬 2 📌 0
I'm very happy to announce our new Cohere+Reload: Re-enabling High-Resolution Cache Attacks on AMD SEV-SNP was accepted at DIMVA 2025!
In it @snee.la, @gruss.cc and I investigate AMD's ciphertext coherence mechanism and show even low resolution leakage can go a long way.
Paper preview: cr.giner.cc
03.04.2025 15:40 — 👍 16 🔁 5 💬 2 📌 1
Researcher at Microsoft Azure
boriskoepf.de
postdoc in (mostly) microarchitectural security @ distrinet, ku leuven
https://mici.hu
Austrian CTF team merger 🇦🇹
https://hofhackerei.at
Official account of the Microarchitecture Security Conference (µASC).
Cutting-edge research on #security in #microarchitecture contexts.
Next Conference: February 3, 2026, in Leuven, Belgium. https://uasc.cc
Apple Security Researcher | Informatics PhD | TUGraz Alumni | Pwnie Award 2022 | BlackHat Speaker | Power Analysis | Fault Attacks | μ-Architectural Attacks | https://andreaskogler.com/
Security Researcher | PhD Candidate with CoreSec at @tugraz.bsky.social | Microarchitectural Attacks | OS/HV Development | https://responsible.fyi
PhD student working on system, side-channel, and CPU security at @isec-tugraz.bsky.social TU Graz, Austria.
He/Him
┌ Website: https://snee.la
└ Mastodon: https://infosec.exchange/@vmcall
PhD student 📍 University of Luebeck, Institute for IT Security
wannabe hacker... he/him
🌱 grow your hacking skills https://hextree.io
Senior Scientist @TU Wien / Web & Mobile Security / #drumandbass DJ
🚩 with @mhackeroni.bsky.social We_0wn_Y0u kukhofhackerei Team Austria
🔗 https://minimalblue.com/
Research Scientist at Intel Labs. Working on (post-quantum) cryptography, hardware design, and side-channel analysis.
Professor of Computer Science | Director GameLabGraz GameDevDays | #GameDev Research Science Tech VR AI | @TUGraz | past LMU ETH MIT EA | Forbes 30u30 Science | mountains ⛰️
twitch.tv/JoeyPrink
youtube.com/@JoeyPrink
jpirker.com
PhD Student TU Graz trying to improve computer security.
Follow me on instagram for photos and videos: @jonas.juffinger
he/him
https://www.jonasjuffinger.com
(he/him) Security Engineer/Researcher, PhD. AppSec, Fuzzing, Binary Analysis, Rust. Also 🤘🚴🥋👶
The 22nd Conference on Detection of Intrusions and Malware & Vulnerability Assessment (DIMVA '25)
✨July 9 to 11, 2025 ✨in Graz, AUSTRIA 🇦🇹
🔒 Professor of IT Security @ University of Luebeck
💡 Research in systems security, applied cryptography, and side channels
🌐 More info: its.uni-luebeck.de
Research assistant and PostDoc for system security @ University of Lübeck
InfoSec Faculty @ #CISPA. Side-channel attacks. Exploiting microarchitectures. Discovering CPU vulnerabilities.



