V8 now has a JS bytecode verifier!
IMO a good example for the benefits of the V8 Sandbox architecture:
- Hard: verify that bytecode is correct (no memory corruption)
- Easier: verify that it is secure (no out-of-sandbox memory corruption)
The sandbox basically separates correctness from security.
09.12.2025 10:00 — 👍 20 🔁 4 💬 1 📌 0
Google Issue Tracker
We derestricted a number of vulnerabilities found by Big Sleep in JavaScriptCore today: issuetracker.google.com/issues?q=com...
All of them were fixed in the iOS 26.1 (and equivalent) update last month. Definitely some cool bugs in there!
03.12.2025 17:28 — 👍 6 🔁 4 💬 0 📌 0
I've uploaded the slides of my recent talk "JS Engine Security in 2025": saelo.github.io/presentation.... I think there'll also be a recording available at some point (otherwise I can make one as not everything's in the slides).
Fantastic conference as usual, big thanks to the PoC Crew!
24.11.2025 09:58 — 👍 22 🔁 11 💬 0 📌 0
About the security content of iOS 26.1 and iPadOS 26.1 - Apple Support
This document describes the security content of iOS 26.1 and iPadOS 26.1.
Some more cool JS Engine bugs found by Big Sleep were fixed in yesterday's Apple security updates: support.apple.com/en-us/125632
Technical details will be available soon at issuetracker.google.com/issues?q=com...
04.11.2025 17:10 — 👍 8 🔁 4 💬 1 📌 0
We derestricted crbug.com/382005099 today which might just be my favorite bug of the last few years: bad interaction between WebAudio changing the CPU's handling of floats and V8 not expecting that. See crbug.com/382005099#co... for a PoC exploit. Also affected other browsers
29.10.2025 14:27 — 👍 18 🔁 7 💬 0 📌 0
It's been a great pleasure being part of the core V8 team and I'll still be active in the V8 Security space in a (mostly) consulting role to help ensure the V8 Sandbox keeps progressing and becomes a strong security boundary! :)
12.08.2025 11:37 — 👍 5 🔁 0 💬 0 📌 0
Google Issue Tracker
Some personal news: I'm thrilled to be moving back to Project Zero! Specifically I'll be joining the Big Sleep project to find vulnerabilities in JavaScript engines. We've already found and reported our first vulnerability in V8 last week: issuetracker.google.com/issues/43621...
12.08.2025 11:37 — 👍 24 🔁 2 💬 1 📌 0
Chromium
It's not (yet) meant for production use, but should offer a preliminary look at where things might be heading. See crbug.com/350324877 for more details.
Feedback welcome! :)
09.07.2025 09:04 — 👍 7 🔁 0 💬 0 📌 0
If you have a machine with PKEY support and somewhat recent Linux kernel you can now play around with hardware support for the V8 sandbox. When active, JS + Wasm code has no write permissions outside the sandbox address space. To enable, simply set `v8_enable_sandbox_hardware_support = true`.
09.07.2025 09:04 — 👍 18 🔁 4 💬 1 📌 2
Software Engineer III, V8 Security — Google Careers
V8 Security is hiring in Munich, Germany: www.google.com/about/career...
Great opportunity to work on some really hard and interesting problems in the security space!
02.07.2025 16:34 — 👍 12 🔁 5 💬 0 📌 0

Stable Channel Update for Desktop
The Stable channel has been updated to 137.0.7151.68/.69 for Windows, Mac and 137.0.7151.68 for Linux which will roll out over the coming...
chromereleases.googleblog.com/2025/06/stable-channel-update-for-desktop.html
Some cool things to note though:
- the bug was mitigated via finch kill switch a day after the report from TAG
- we also fixed the V8 Sandbox bypass within 7 days even though it's not yet considered a security boundary
03.06.2025 07:42 — 👍 8 🔁 0 💬 1 📌 0
I’m very excited to announce that we at V8 Security have finally published our first version of Fuzzilli that understands Wasm!
Go check it out at https://github.com/googleprojectzero/fuzzilli.
While we still have a way to go in improving it, we think it shows a promising approach!
04.02.2025 19:34 — 👍 31 🔁 16 💬 1 📌 1
This for example shows that the V8 Sandbox is pretty promising in terms of "bug coverage". Of course that also assumes that it'll become a strong security boundary (it's still pretty soft at the moment), see bsky.app/profile/sael...
07.06.2024 16:01 — 👍 3 🔁 0 💬 0 📌 0
And the recording is now also public: youtu.be/5otAw81AHQ0?... thanks @offensivecon.bsky.social!
05.06.2024 08:38 — 👍 0 🔁 0 💬 0 📌 1
Finally got around to publishing the slides of my talk @offensivecon.bsky.social from ~two weeks ago. Sorry for the delay!
The V8 Heap Sandbox: saelo.github.io/presentation...
Fantastic conference, as usual! :)
22.05.2024 19:01 — 👍 4 🔁 5 💬 0 📌 1
Thanks Justin!
04.04.2024 17:46 — 👍 1 🔁 0 💬 0 📌 0
Big day for the V8 Sandbox:
* Now included in the Chrome VRP: g.co/chrome/vrp/#...
* Motivation & goals discussed in a new technical blog post: v8.dev/blog/sandbox
If there is ever a Sandbox "beta" release, this is it!
04.04.2024 13:07 — 👍 6 🔁 3 💬 0 📌 0
New V8 Sandbox design document is out: docs.google.com/document/d/1...
This discusses how a hardware-based sandbox instead of the currently purely software-based one might look like in a somewhat distant future (if at all)
15.02.2024 10:00 — 👍 0 🔁 0 💬 0 📌 0
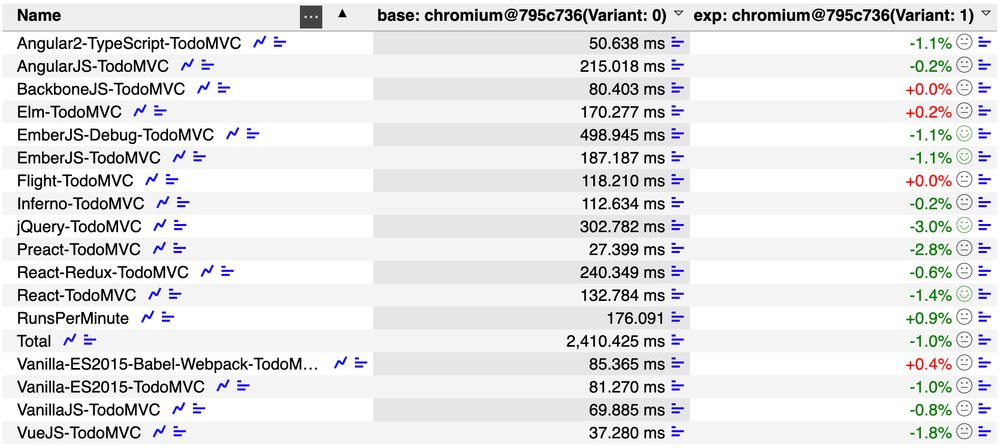
Benchmark results on Speedometer2 showing that the overall performance impact of the V8 sandbox is only around 1% total
Some early performance numbers for the V8 Sandbox: looks like with most of the performance critical parts in place now, the overall performance cost of this future security boundary is only around 1% on popular benchmarks \o/
More results linked from chromium-review.googlesource.com/c/v8/v8/+/52...
19.01.2024 10:21 — 👍 2 🔁 1 💬 0 📌 0

V8 Sandbox - Glossary
I've been meaning to write this for some time now and finally got around to it: a "V8 Sandbox Glossary" document that briefly explains the most important terms/concepts used for the sandbox and links to the respective design documents: docs.google.com/document/d/1...
08.12.2023 12:35 — 👍 0 🔁 0 💬 0 📌 0
Gerrit Code Review
Another exciting step for the V8 sandbox: with crrev.com/c/5007733 BytecodeArrays are now the first objects to move into the new trusted heap space! Still a number of remaining issues around bytecode execution, but this fixes the long-standing issue that an attacker could directly corrupt bytecode
30.11.2023 17:13 — 👍 3 🔁 2 💬 1 📌 0
senior researcher at @citizenlab.ca
Assistant Professor @ Eurecom. I'm interested in formal methods for low-level security. https://leslyann-daniel.fr
Die einzige nur von Björn Höcke anerkannte Terrororganisation. Werde jetzt Kompliz:in! Wir machen für Dich Stress und radikalen Humanismus: https://werde-komplizin.de
METR is a research nonprofit that builds evaluations to empirically test AI systems for capabilities that could threaten catastrophic harm to society.
Working on WebAssembly / wasm in V8 | Opinions are my own
Defence Editor at The Economist.
Visiting Fellow at Department of War Studies, KCL. For speaking engagements: https://chartwellspeakers.com/speaker/shashank-joshi
Software Security @ MPI for Security and Privacy
Spokesperson for Max Planck Research Group Leads at CPTS
PhD @NUS, Dipl.-Inf. @TUDresden
Research Group: http://mpi-softsec.github.io
Sometime verb, real person, lover of 8-bit computers, husband & father, trying to be a kind person. #blacklivesmatter; trans rights are human rights.
he/him
A website for exploring the output of compilers. aka godbolt.org
Supports C, C++, Rust, Fortran, COBOL and many many more.
Support us at https://patreon.com/mattgodbolt
Writer. Contact me here: https://raphae.li
News and information from the European Commission. Social media and data protection policy: http://europa.eu/!MnfFmT
Wir bieten der Finanzlobby die Stirn. Mach Dich mit uns für eine faire Finanzwelt stark! http://finanzwende.de/mitmachen/
manager/security things for Firefox. love my family, my bike and reading books.
You can also find me on Mastodon as @freddy@security.plumbing, which I consider my primary account.
Homepage: https://frederikbraun.de/
since 1985
https://phrack.org
Windows Internals Author, Developer, Reverse Engineer, Security Researcher, Speaker, Trainer, and most recently Nation State Hacker.
Core OS Platform Developer at Apple, Hyper-V Vendor at Microsoft, Chief Architect at CrowdStrike and now Director at CSE.
reverse-engineering / low-level security
Dragon Sector CTF vice-captain, Invisible Things Lab
Mastodon: @redford@infosec.exchange
Also known as Redford
Aussie security / tech guy.
Google Threat Intelligence. Co-founder Threat Analysis Group (TAG). Tweets are my own not my employers.
VXRL/VXCON/Blackhat Asia & USA review board/Browser vulnerability & exploitation