
We are going to hold VXCON
www.vxcon.hk
@darkfloyd1216.bsky.social
VXRL/VXCON/Blackhat Asia & USA review board/Browser vulnerability & exploitation

We are going to hold VXCON
www.vxcon.hk

This time is a real thrilling announcement as our paper about template-based fuzzing for JavaScript engine is accepted in OOPSLA24-25.
Thank you so much to every co-authors including Ken Wong, Dongwei Xiao, Dr. Daoyuan Wu Dr. Shuai Wang and Yiteng Peng.
What a good evening!

Congratulations to Carl Smith from v8 Security team and join Blackhat USA review board as guest reviewer. He is willing to share, open-minded, and a hardcore researcher and developer.
@rwx.page
… Threat actors will expose more about their plans when they get in only, and let them get into our matrix. This is more interactive with threat actor, and it is the art.
29.01.2025 15:13 — 👍 0 🔁 0 💬 0 📌 0… the back-end system is all fabricated, when particular threat actor is detected. We can differentiate who is the threat actor or not with provision of different security level of backend systems.
29.01.2025 15:12 — 👍 0 🔁 0 💬 0 📌 0
The countries always attempt to hack into vendor platforms or apps, my idea is making a “Realistic Honeypot Platform” and let them in, capture as much as information about them and …
cloud.google.com/blog/topics/...

An inspiration of beginning of new year. It is our first Chrome VRP bounty.
Our first Chrome VRP bounty, it is an inspiration and keep going.
11.01.2025 03:57 — 👍 0 🔁 0 💬 0 📌 0
We got our first Google Chrome bounty for minimum wage or McDonalds before Christmas 🎄.
Getting money from Google is mission impossible.
Minimum wage 🤣
19.12.2024 01:51 — 👍 1 🔁 0 💬 0 📌 0



We are glad to complete VXCON. Thank you so much to every speakers, guest, and crew member to make it happen.
#vxcon #vxrl
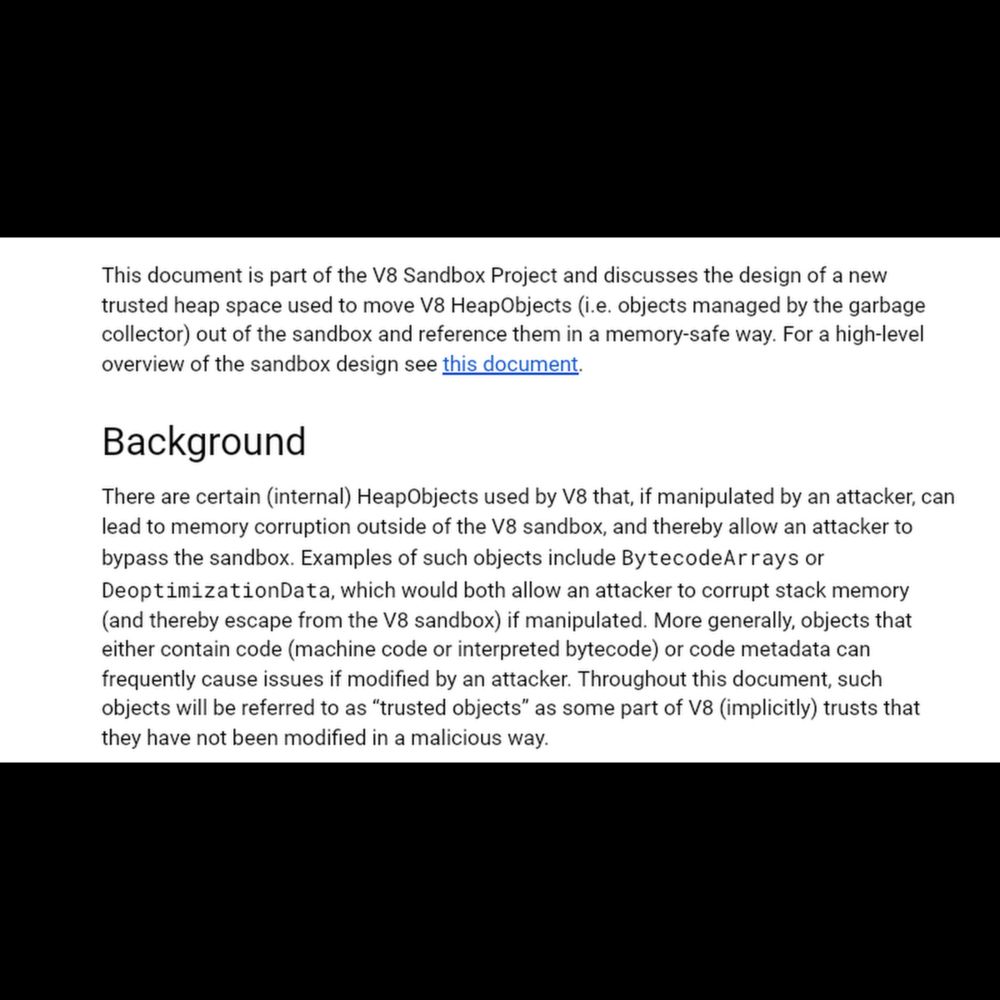
Here's another V8 sandbox design document, this time discussing how sensitive ("trusted") V8-internal objects (such as BytecodeArrays) can be protected: docs.google.com/document/d/1...
This should be one of the last pieces of infrastructure required for the sandbox.
Finally got around to publishing the slides of my talk @offensivecon.bsky.social from ~two weeks ago. Sorry for the delay!
The V8 Heap Sandbox: saelo.github.io/presentation...
Fantastic conference, as usual! :)

Another big step towards becoming a security boundary: today we’re expanding the VRP for the V8 Sandbox
* No longer limited to d8
* Rewards for controlled writes increased to $20k
* Any memory corruption outside the sandbox is now in scope
bughunters.google.com/about/rules/...
Happy hacking!



VXCON finished and thank you so much to everyone.
19.11.2024 11:56 — 👍 0 🔁 0 💬 0 📌 0