
And finally here's a direct link to the tool -
github.com/NetSPI/Micro...

And finally here's a direct link to the tool -
github.com/NetSPI/Micro...

Cody really did all the heavy lifting here with figuring out the decryption. I just automated that process into a tool. Make sure to read his blog on that process - dazesecurity.io/blog/abusing...
24.07.2025 15:41 — 👍 1 🔁 0 💬 1 📌 0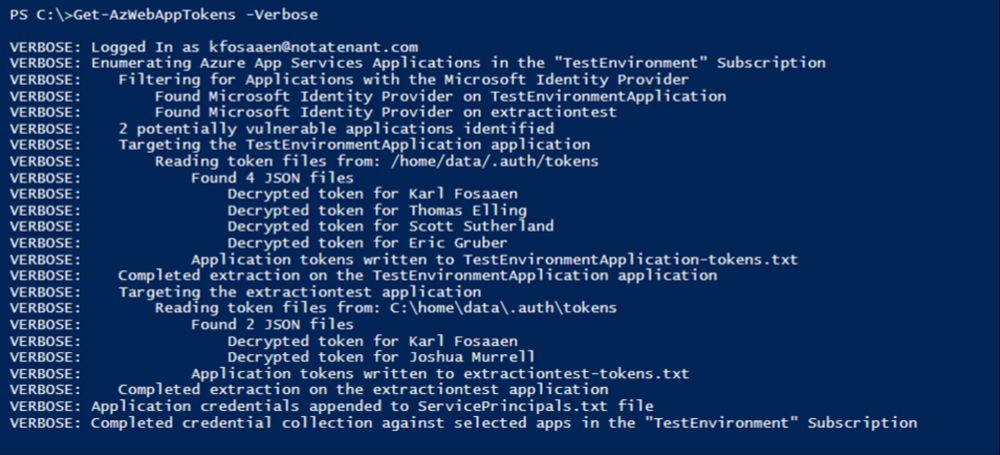
Building off of @codyburkard.com's prior work, I put together a tool for automating the decryption of Entra ID application tokens from Azure App Services resources.
Here's a blog that outlines the tooling:
www.netspi.com/blog/technic...
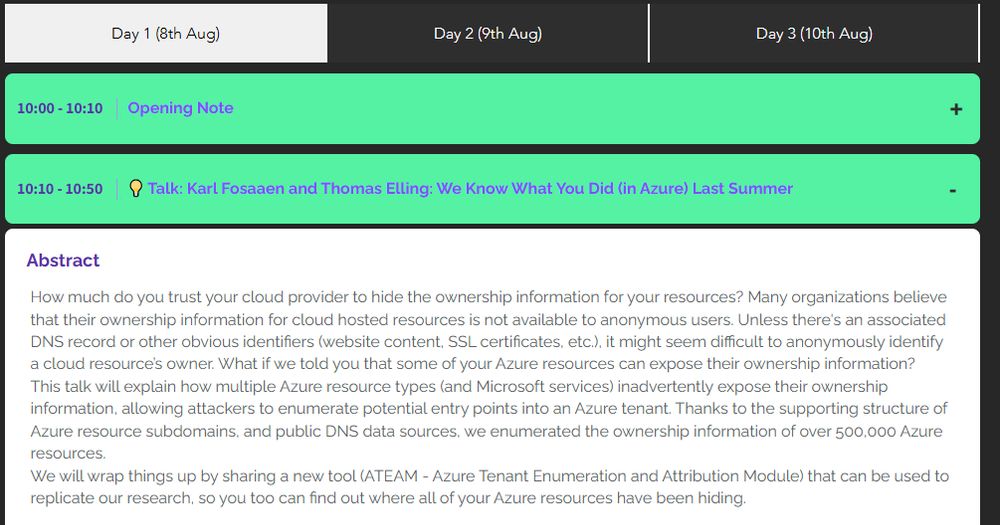
I'm very excited to share that Thomas Elling and I will be presenting "We Know What You Did (in Azure) Last Summer" at the DEF CON @cloudvillage-dc.bsky.social this year (Friday - 10 AM). We will go over some techniques that can be used to find the owners of multiple types of Azure resources.
18.07.2025 16:32 — 👍 5 🔁 2 💬 0 📌 0
NetSPI Principal Security Consultant Jason Juntunen recently published findings on a Remote Code Execution vulnerability in SailPoint's IQService component.
👉 Read the full technical breakdown: ow.ly/GbT150WmgRg
#proactivesecurity #VulnerabilityResearch

New Function (Get-AzLoadTestingData) was also added to MicroBurst to automate this attack
github.com/NetSPI/Micro...
TL;DR
The service allows you to run JMeter load tests.
It supports Managed Identities and Key Vaults.
You can get code execution on the service to extract tokens, vault secrets and certs
I have a new post out on the @netspi.bsky.social blog today. This one is on extracting sensitive information from the Azure Load Testing service. www.netspi.com/blog/technic...
01.07.2025 20:47 — 👍 3 🔁 2 💬 1 📌 1
I had a great time at #socon2025! Big thanks to the SpecterOps crew for hosting. Slides for my "Hunting SMB Shares" talk are below for those who are interested.
Slides
github.com/NetSPI/Power...
PowerHuntShares
github.com/NetSPI/Power...

If you’re on the fence about signing on to that @eff.org letter to support @thekrebscycle.bsky.social , please consider doing it sooner rather than later.
Don’t wait until there’s no one left to speak for you. #RSAC2025
www.cnn.com/2025/04/30/p...

If anyone wants to help out on a (hopefully) easy update for some functions in MicroBurst, we will need to make some adjustments for "Get-AzAccessToken" token output switching to a SecureString in Az PS 14.0.0
github.com/NetSPI/Micro...
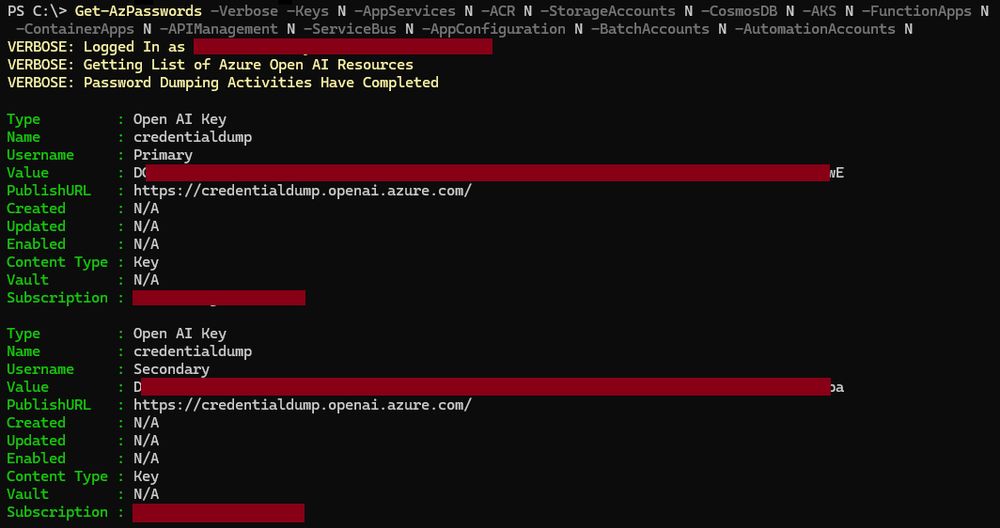
Quick addition to Get-AzPasswords in MicroBurst - Azure OpenAI keys
This new section will dump any available OpenAI keys from Cognitive Services deployments that your user has list key permissions on.
github.com/NetSPI/Micro...

And here's a link to the blog - www.netspi.com/blog/technic...
08.01.2025 16:33 — 👍 2 🔁 1 💬 0 📌 0The tooling was inspired by the research in this talk by Aled Mehta and Christian Philipov - "[D24] Smoke and Mirrors: How to hide in Microsoft Azure" - www.youtube.com/watch?v=uvoV...
08.01.2025 16:33 — 👍 2 🔁 0 💬 1 📌 0
In addition to the blog out today, there's a new tool in MicroBurst - Get-AzMachineLearningCredentials
This one has been in the works for a while, but it's a tool to dump the credentials that are stored by the Azure Machine Learning service. github.com/NetSPI/Micro...

New
@netspi.bsky.social
blog out today on "Hijacking Azure Machine Learning Notebooks (via Storage Accounts)". This is very similar to Storage Account attacks that have been done against Function/Logic Apps and Cloud Shell - www.netspi.com/blog/technic...

A big thank you to MSRC for the 2024 MVR merch! This is a nice way to wrap up the year.
30.12.2024 20:42 — 👍 2 🔁 0 💬 0 📌 0
Balancing usability and security in deployments introduce new and unfamiliar risks to organizations. NetSPI created an open Large Language Model (LLM) framework to help clarify some ambiguity around LLM security.
Read more about this framework in our most recent article: ow.ly/Nhjs50Usaio
What happens when you prioritize security over usability in AI models—or vice versa? Our Open LLM Security Benchmark dives deep into the trade-offs and implications, showcasing why this balance is critical for the future of AI. Access the paper here: ow.ly/zT2g50UsaZH
17.12.2024 14:17 — 👍 1 🔁 1 💬 0 📌 0This is some really exciting work from our team. Make sure to check out the benchmark repo on GitHub -https://github.com/NetSPI/Open-LLM-Security-Benchmark/tree/main
16.12.2024 20:50 — 👍 2 🔁 0 💬 0 📌 0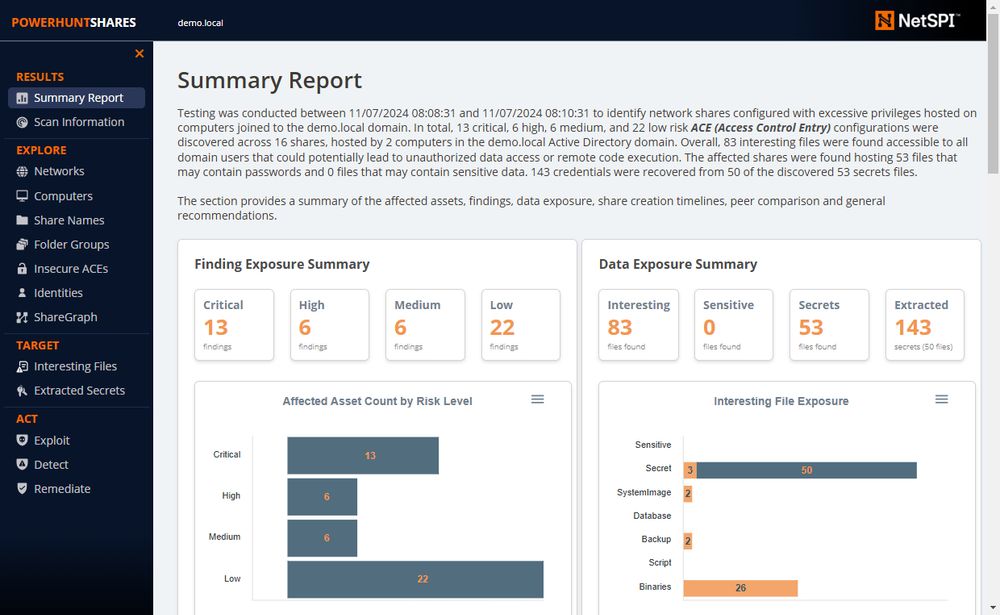
PowerHuntShares.v2: New Sample HTML Report
Here is a sample report for those who wanted it. Enjoy!
raw.githubusercontent.com/NetSPI/PowerHu…
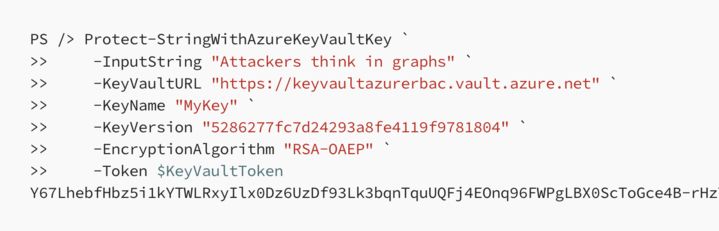
A quick tour of new functions in BARK that support Azure Key Vault tradecraft research, including a walk-through of how an adversary may chain these functions together as part of an attack path: posts.specterops.io/azure-key-va...
20.11.2024 17:44 — 👍 17 🔁 8 💬 0 📌 0

I had an amazing time last week attending and speaking at the Hybrid Identity Protection conference in New Orleans. There was a really solid line up of presentations and I was honored to be included this year.
18.11.2024 17:31 — 👍 2 🔁 0 💬 0 📌 0