
Injected KongTuke script in page from compromised website.
![Fake CAPTCHA page from KongTuke domain, scrroeder[.]com.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:v3kgm6hujff4gbxies5vwbnb/bafkreielwil5fxjm3tv2gkrdwcv4airp2xlmojctkj7wjgyzh7ogo7bfzu@jpeg)
Fake CAPTCHA page from KongTuke domain, scrroeder[.]com.

KongTuke's "ClickFix" command injected into the viewer's clipboard.

Traffic from the activity filtered in Wireshark. I did not get the malware from this.
2026-01-05 (Monday): #KongTuke domain scrroeder[.]com generated #ClickFix script for 144.31.221[.]71, but I didn't get a malware infection when I tried it today.
05.01.2026 16:50 — 👍 7 🔁 1 💬 0 📌 0
God I hate the fact that Threat + Hunting is being called "Thrunting." And we now have Threat + Hunters who are "Thrunters." This is all I can see when I see these terms...
21.10.2025 17:40 — 👍 10 🔁 1 💬 1 📌 0

Page to download the initial file.

HTTPS URLs seen from the infection.

Traffic from the infection filtered in Wireshark.

Example of post-infection data exfiltration traffic.
2025-10-16 (Thursday): Unidentified #stealer/#Loader found when searching for URLs that follow patterns previously seen for Koi Loader/Koi Stealer.
Details at github.com/malware-traf...
16.10.2025 17:18 — 👍 1 🔁 1 💬 0 📌 0

Screenshot of the email.

Screenshot of webpage for the malware download.

Downloaded malware EXE showing digital signature and metadata.

Scheduled task to keep the infection persistent.
2025-09-25 (Thursday): Received an email distributing a malicious installer for an #RMM tool. Details at github.com/malware-traf...
28.09.2025 17:19 — 👍 7 🔁 2 💬 0 📌 0

Screenshot of the email.

Screenshot of webpage for the malware download.

Downloaded installer EXE showing digital signature and metadata.

Scheduled task to keep the infection persistent.
2025-09-29 (Monday): Follow-up to my post last week. I've been seeing one or two of these emails almost every day. Details on the latest example at github.com/malware-traf...
30.09.2025 17:04 — 👍 5 🔁 3 💬 0 📌 0

Screenshot of icon for the malicious app on a cell phone.

Screenshot of the login screen for the malicious app on a cell phone.

It's asking me to place a credit card on the phone.

Traffic from an infection filtered in Wireshark.
2025-10-02 (Thursday): #pcap and some images from an Android malware infection at www.malware-traffic-analysis.net/2025/10/02/i...
07.10.2025 02:59 — 👍 2 🔁 2 💬 0 📌 0

Screen shot of the blog post.
2025-10-06 (Monday): A collection of 200+ phishing emails in Japanese that were sent to my blog email addresses. Available at www.malware-traffic-analysis.net/2025/10/06/i...
07.10.2025 03:41 — 👍 3 🔁 1 💬 0 📌 0
Thank you!
06.10.2025 19:36 — 👍 1 🔁 0 💬 0 📌 0

Screenshot of the page from my website with the post for this information.

Example of path to download the initial 7-zip archive for the malware.

Page with the download for the initial 7-zip archive.

Traffic from the possible Rhadamanthys malware, filtered in Wireshark.
2025-10-01 (Wed) I've posted #malware samples and a #pcap of the post-infection traffic from an infection by possible #Rhadamanthys malware at www.malware-traffic-analysis.net/2025/10/01/i...
This is from a file disguised as a cracked version of software, and I usually see #LummaStealer from this.
06.10.2025 18:52 — 👍 2 🔁 3 💬 1 📌 0
Looking forward to the exercise file. 🙂
22.09.2025 20:31 — 👍 0 🔁 0 💬 0 📌 0
Dr. Brian Fehrman give us his reason why we want to defeat AI-Based Malware Detection.
Join us for a free one-hour session with AI-security researcher & BHIS pentester Dr. Brian Fehrman on defeating AI malware detection with AI.
Thu, Sep 11 1:00 PM ET
Register: events.zoom.us/ev/AuO1quTvv...
09.09.2025 17:43 — 👍 2 🔁 2 💬 0 📌 0

THURSDAY - BHIS Webcast
What if you could use AI to defeat AI-based malware detection?
Join us for a free one-hour session with AI-security researcher and BHIS pentester Brian Fehrman on defeating AI malware detection with AI.
Thu, Sep 11 1:00 PM EDT
Register: events.zoom.us/ev/AuO1quTvv...
09.09.2025 18:52 — 👍 2 🔁 1 💬 0 📌 0

Hey folks!
WEDS- Antisyphon Training Anticast
Join Nick Ascoli & Eric Clay from Flare for a free one-hour training session, "Unraveling Infostealer Threat Networks,".
Wed, Sep 10 12:00 PM EDT
Register: events.zoom.us/ev/AtRoO7tR8...
09.09.2025 18:52 — 👍 4 🔁 2 💬 1 📌 0

Kongtuke style injected script in page from compromised website

Fake CAPTCHA page that performs clipboard hijacking (pastejacking) showing the ClickFix style instructions and malicious script a victim would paste into a Run window or command line terminal.

Location of the downloaded zip archive for Lumma Stealer, and the content of that zip archive in the user's AppData\Roaming directory.

Traffic from an infection filtered in Wireshark.
2025-09-03 (Wednesday): #Kongtuke fake CAPTCHA page leads to #ClickFix style script for #LummaStealer
A #pcap of the infection traffic, the associated malware, and IOCs are at www.malware-traffic-analysis.net/2025/09/03/i...
03.09.2025 18:13 — 👍 6 🔁 4 💬 0 📌 0

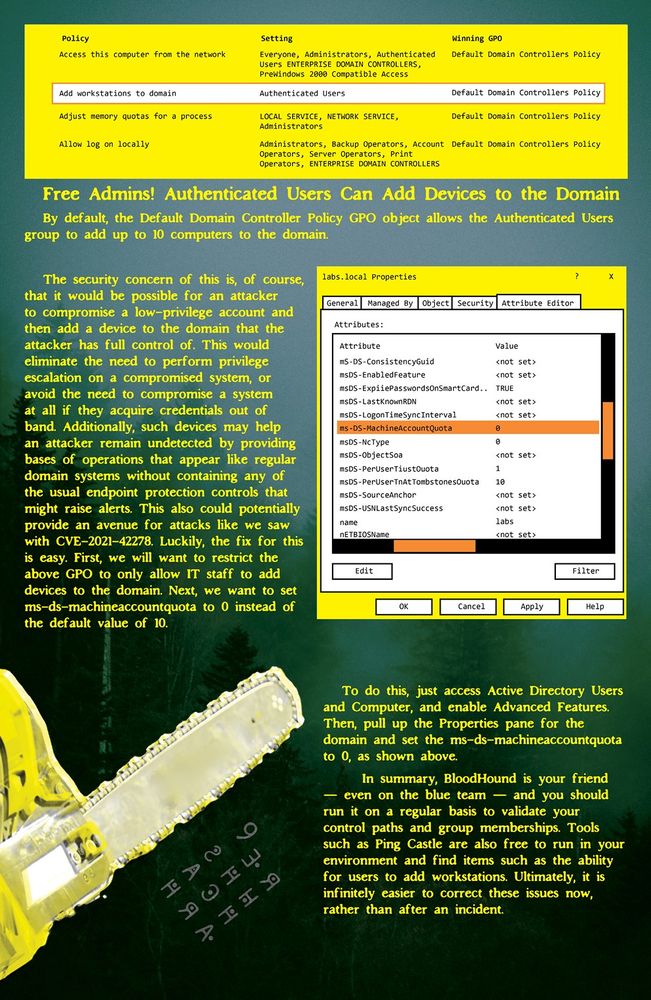
Blue teamers — sometimes we can lose sight of Active Directory. I mean, it just works in the background, right? Active Directory is crucial to Windows networks & a perfect target for bad actors. Dive into this article to learn common active directory pitfalls 7 how to avoid getting your day ruined.
17.12.2024 21:50 — 👍 12 🔁 2 💬 1 📌 0

Anti-Cast: Finding and Fixing AD CS Issues with Locksmith with Jake Hildreth - Antisyphon Training
Join us for a free one-hour infosec training session from Trimarc’s Jake Hildreth on Finding and Fixing AD CS Issues with Locksmith.
Howdy folks. I'm sending this skeet to let you know about the free @antisyphontraining.bsky.social Anti-cast tomorrow on Finding and Fixing AD CS Issues with Locksmith w/ Jake Hildreth (@dotdot.horse).
Jake's my coworker & friend. Sign up!
www.antisyphontraining.com/event/anti-c...
10.12.2024 16:58 — 👍 6 🔁 2 💬 0 📌 0

Do you want to level up your cloud penetration testing skills? Then be sure to register for "Breaching the Cloud" with Beau Bullock for pre-con training at Wild West Hackin' Fest @ Mile High 2025! Check out details and register here: wildwesthackinfest.com/wild-west-ha...
03.12.2024 17:13 — 👍 2 🔁 1 💬 0 📌 0
Threat Hunting Zine — PROMPT#
You can read the entire Threat Hunting issue of PROMPT# for FREE:
www.promptzine.com/threat-hunti...
26.11.2024 17:58 — 👍 1 🔁 1 💬 0 📌 0

Do you want AI to take your job? NO! Give yourself a holiday present and attend the "AI for Cyber Security Professionals" two day course at the @antisyphontraining.bsky.social Secure Code Summit on Dec5th and 6th 2024. www.antisyphontraining.com/course/ai-fo...
I promise this will change your life!
25.11.2024 14:22 — 👍 3 🔁 3 💬 0 📌 0
Builder of security products and programs. Teacher of those who run them.
https://zeltser.com
Mike is a digital paleontologist working on velociraptor
Fighting malware and botnets
Sometimes, I build stuff. Sometimes, I break stuff.
Blue Team Con is an annual cybersecurity conference built for defenders, inclusive of anyone interested in safeguarding organizations.
https://blueteamcon.com
Next Conference:
Training: 10-11 September 2026
General Conference: 12-13 September 2026
Infosec, Detection Engineering, Threat Research, Threat Hunting, OffSec, Conference Organizer.
Since 1984, 2600 Magazine has published the hacker perspective and documented the development of the hacking community. In addition to the magazine, we have a weekly radio show ("Off The Hook") and a biennial conference (Hackers On Planet Earth - HOPE).
The open source AI code editor
SpyCloud - Director of Security Research, Cryptolaemus Coordinator, Emotet(Ivan)/QBot(Boris) Destroyer, gold prospector & former sysadmin.
Threat Researcher @ Proofpoint. Opinions are my own etc
Senior Security Researcher, Proofpoint Emerging Threats. I stare at pcaps all day, and use my pattern-seeking scattered hunter-gatherer brain, to write IDS signatures. I'm also a huge fuckin nerd. Obligatory My words are not fit for consumption warning.
Threat researcher @ Proofpoint. Formerly IBM X-Force, CMU, US Government, US Navy. Views are my own.
🏴☠️ OFFENSIVE-INTEL 🏴☠️ Cyber Threat Intelligence by Hackers | Security Researcher en CronUp.com | CuratedIntel Member | 🥷🧠🇨🇱
By defenders. For defenders.
Peel back the layers of your network and make your adversaries cry.
https://www.securityonion.com
Detection Engineer @ Red Canary
https://github.com/killamjr
Cybercrime Fighter 🛡Threat Intelligence 🕵🏻♂️ & Malware Analysis 🦠 Fortunate to work @ Trend Micro. Happy to help whenever possible.
🔮 Senior Threat Researcher at @proofpoint 🔮 | Kindness and Compassion | Not a reflection of the opinions or policies of my employer | Andrew Northern
Recovering sysadmin that now chases adversaries instead of uptime. Sr Malware Analyst @redcanary

![Fake CAPTCHA page from KongTuke domain, scrroeder[.]com.](https://cdn.bsky.app/img/feed_thumbnail/plain/did:plc:v3kgm6hujff4gbxies5vwbnb/bafkreielwil5fxjm3tv2gkrdwcv4airp2xlmojctkj7wjgyzh7ogo7bfzu@jpeg)













































