
Remote access, real cargo: cybercriminals targeting trucking and logistics | Proofpoint US
Key findings Cybercriminals are compromising trucking and freight companies in elaborate attack chains to steal cargo freight. Cargo theft is a multi-million-dollar criminal
Threat actors are teaming up with organized crime to target truckers — stealing identities, placing fraudulent bids on freight, and making off with the cargo. Their entry point? Emails with links delivering Remote Monitoring and Management (RMM) tools. Together with @selenalarson.bsky.social :
03.11.2025 10:40 — 👍 29 🔁 20 💬 1 📌 3
🚨 Job seekers, watch out! 🚨
Proofpoint found threat actors targeting job seekers to distribute remote management tools that can lead to data or financial theft, or potentially to install follow-on malware like ransomware.
24.07.2025 15:41 — 👍 3 🔁 2 💬 1 📌 1
I just call it "first lunch" or "second breakfast"
28.05.2025 22:04 — 👍 1 🔁 0 💬 1 📌 0

Remote Monitoring and Management (RMM) Tooling Increasingly an Attacker’s First Choice | Proofpoint US
Key findings More threat actors are using legitimate remote monitoring and management (RMM) tools as a first-stage payload in email campaigns. RMMs can be used for
New cyber threat research from Proofpoint highlights how attackers are adapting to law enforcement disruptions, leveraging trusted software to evade detection and compromise systems.
This blog details our team's findings: www.proofpoint.com/us/blog/thre....
#malware #ransomware #dataloss
11.03.2025 16:14 — 👍 5 🔁 1 💬 0 📌 0
In December 11 and 12, 2024, a spearphishing campaign targeted at least 20 Autonomous System (AS) owners, predominantly Internet Service Providers (ISPs), and purported to come from the Network Operations Center (NOC) of a prominent European ISP.
🧵⤵️
12.12.2024 21:18 — 👍 17 🔁 11 💬 1 📌 5

Screenshot of the email showing a TAR archive as an email attachment.

The TAR archive and its content, a Windows EXE file for AgentTesla

An update to the Windows registry showing the malware persistent on an infected Windows host.

Traffic from an infection filtered in Wireshark to show the FTP data exfiltration traffic.
2024-12-04 (Wednesday): #AgentTesla variant using #FTP for data exfiltration. A sanitized copy of the email distributing the malware, a #pcap from an infection run, the associated malware samples, and a list of indicators are available at www.malware-traffic-analysis.net/2024/12/04/i...
05.12.2024 01:14 — 👍 6 🔁 4 💬 1 📌 0

Malicious BumbleBee PDF using Cisco AnyConnect as a lure
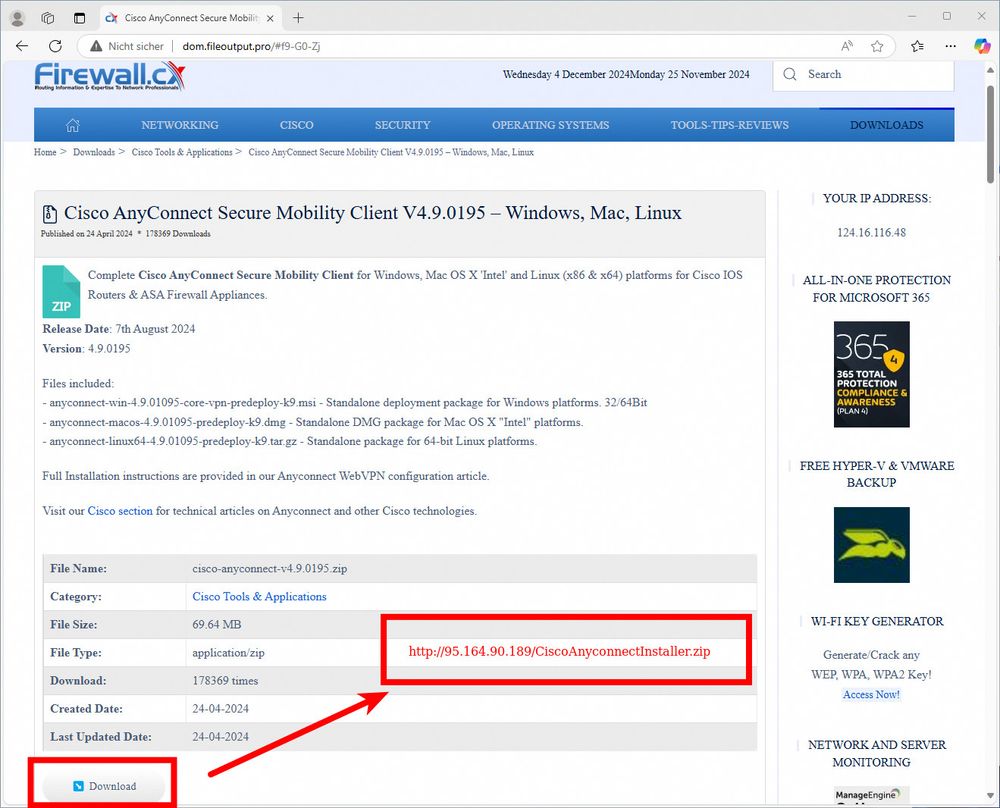
Malicious download page using Cisco AnyConnect as a lure to infect users with BumbleBee malware
#BumbleBee malspam using Cisco AnyConnect as a lure. It contains a PDF with a link to a fake AnyConnect installer that opens AnyConnect on the Microsoft App Store to mask the BumbleBee infection 🔥
Payload delivery URLs:
🌐 urlhaus.abuse.ch/host/95.164....
Payload:
📄 bazaar.abuse.ch/sample/b8794...
04.12.2024 10:06 — 👍 5 🔁 2 💬 0 📌 0

#BruteRatel - #Latrodectus - url > .js > .msi > .dll
wscript.exe Document-v15-51-07.js
msiexec.exe /I C:\Users\Admin\AppData\Local\Temp\fes.msi
rundll32.exe C:\Users\Admin\AppData\Roaming\avutil.dll, DLLMain
(1/3)👇
IOC's
github.com/pr0xylife/La...
03.12.2024 21:22 — 👍 20 🔁 8 💬 1 📌 0
I really like the freedom of BlueSky's API and hope it can be maintained. I will use the API to push more IOCs.
27.11.2024 08:05 — 👍 1 🔁 1 💬 0 📌 0
T-Minus 37 days til the next season of #100DaysofYARA kicks off!!
Who’s excited and what will you be working on?
I can’t believe it but I’m excited to write rules for JavaScript 😬😵💫
But also get to show off the new macho module from the one and only
@jacoblatonis.me
25.11.2024 21:57 — 👍 6 🔁 3 💬 0 📌 0
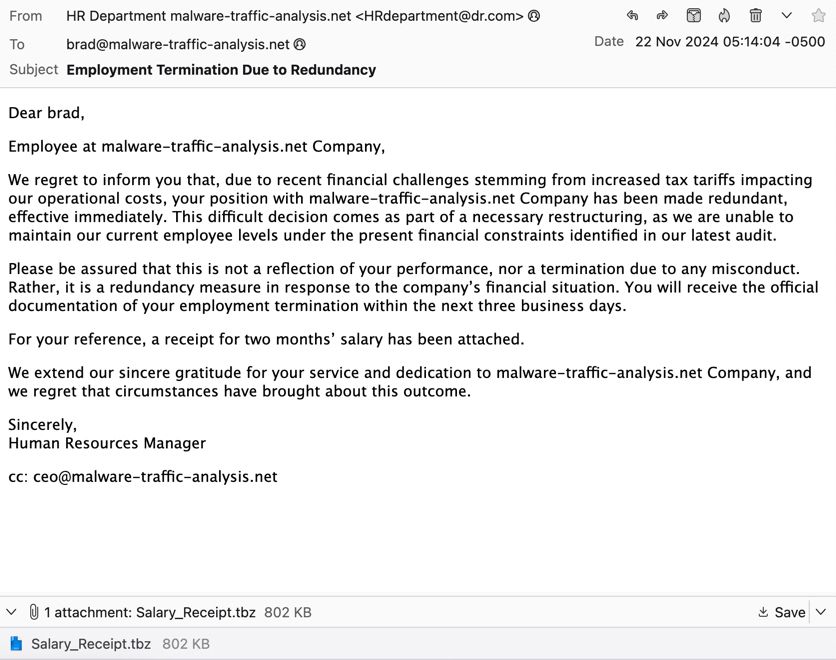
Screenshot of malicious spam (malspam) with malware file attachment.
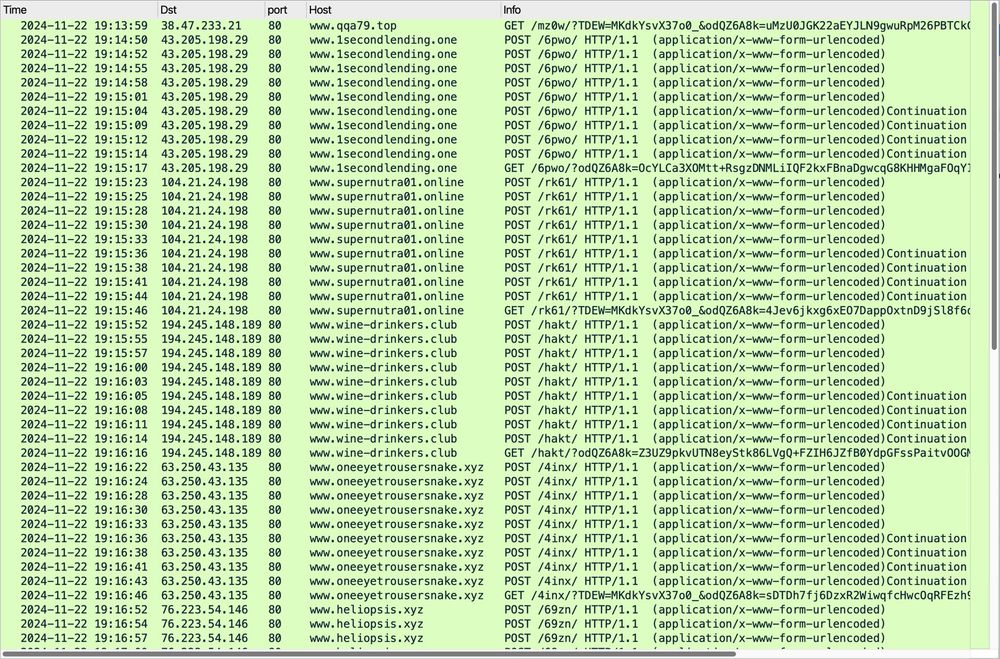
Traffic from the XLoader (Formbook) infection filtered in Wireshark.
2024-11-22 (Friday) #XLoader / #Formbook: I've been fired by my non-existent HR department. At least I got a "salary-receipt.exe" bazaar.abuse.ch/sample/003b5...
Tria.ge and Any.Run don't identify the malware, but Joe Sandbox does: www.joesandbox.com/analysis/156...
Also runs in my lab just fine
22.11.2024 19:42 — 👍 17 🔁 10 💬 2 📌 0
Welcome Brad! @malware-traffic.bsky.social
22.11.2024 19:01 — 👍 2 🔁 0 💬 1 📌 0

China’s Surveillance State Is Selling Citizen Data as a Side Hustle
Chinese black market operators are openly recruiting government agency insiders, paying them for access to surveillance data and then reselling it online—no questions asked.
Very interesting story which in my opinion that shows how the Chinese surveillance state is even "knocking off" on itself when it comes to IP/Data. This is some great research from SpyCloud Labs! Very proud of the Labs Research Team! www.wired.com/story/chines...
21.11.2024 16:26 — 👍 8 🔁 2 💬 0 📌 0
For visibility - x0rz now on Blue Sky, so happy :)
18.11.2024 14:29 — 👍 0 🔁 0 💬 1 📌 0
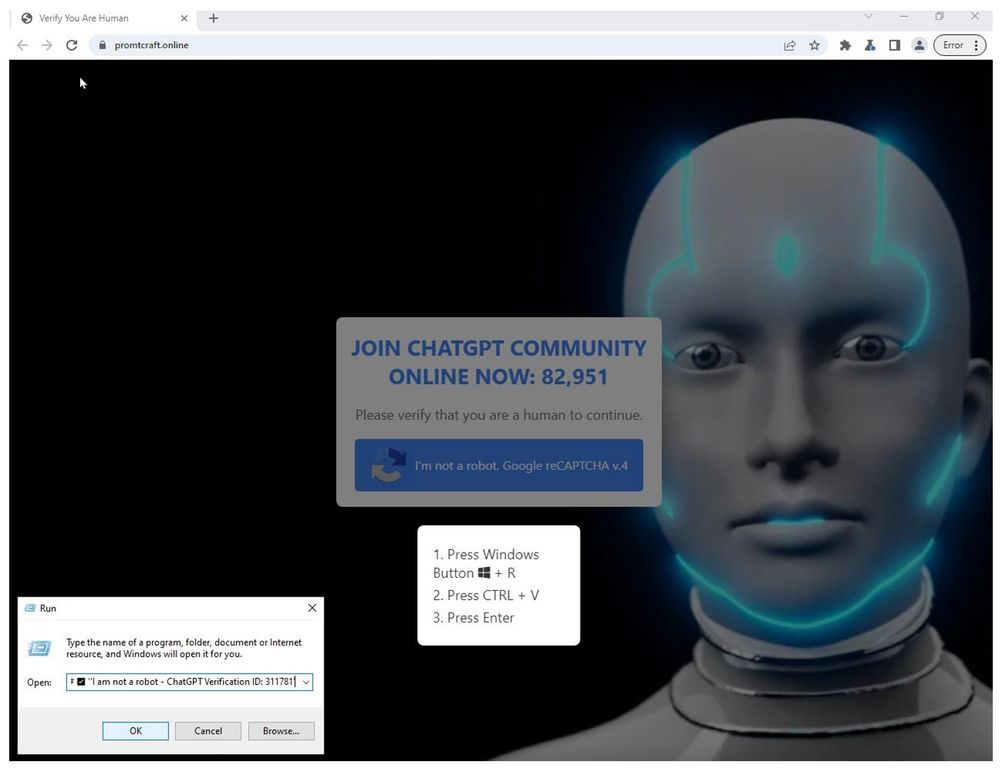
New blog drop with @selenalarson.bsky.social and the rest of the team. This one covers a lot of threats using the #ClickFix technique to lure targets to infect themselves by pasting malicious CMD/PS code. My "fave" is the chumbox #malvertising on major tech sites.
www.proofpoint.com/us/blog/thre...
18.11.2024 12:44 — 👍 11 🔁 5 💬 0 📌 1

Reuters also confirms the story about Biden allowing Ukraine to use US arms to strike inside Russia, citing three sources familiar with the matter. Ukraine plans to conduct its first long-range attacks in the coming days.
www.reuters.com/world/biden-...
17.11.2024 18:53 — 👍 809 🔁 95 💬 29 📌 14
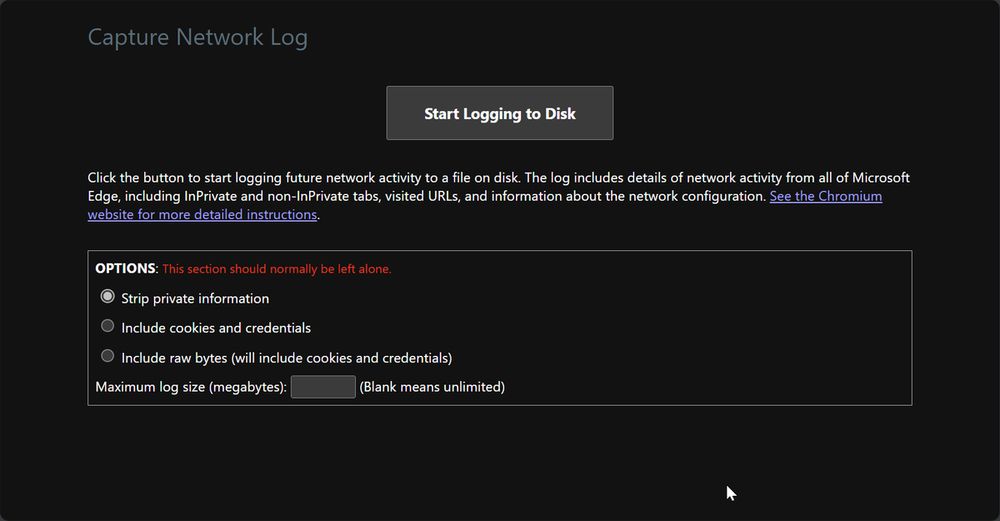
Almost embarrassed to post this, but I've always used Fiddler or Burp for capturing things like this...
I didn't have admin rights and was trying to capture network traffic from a pop-up, so Dev Tools wasn't working
Apparently this is built into Chrome/Edge! So cool :)
edge://net-export/
17.11.2024 06:49 — 👍 187 🔁 45 💬 15 📌 3
Two great easy-to-use tools to find new follows - both worked great.
17.11.2024 01:02 — 👍 2 🔁 0 💬 0 📌 0
YouTube video by BSides Portland
Smokeloader: The Pandora’s box of tricks, payloads and anti-analysis - BSides Portland 2022
Smokeloader keeps crawling its way back into the limelight. If you want a primer on it, I gave a public talk on it 2 years ago
www.youtube.com/watch?v=O69e...
16.11.2024 03:41 — 👍 24 🔁 9 💬 1 📌 0
I see at least AlphV/BlackCat
06.07.2023 21:00 — 👍 2 🔁 0 💬 1 📌 0

IMO: Storm-0875 (overlaps UNC3944/Scattered Spider) is the most dangerous financial threat actor right now
Some recent developments:
1. Now deploying ransomware (had been extorting orgs before)
2. In last few months targeting large/well known enterprises (not just telcos/help desk/crypto orgs)
06.07.2023 12:45 — 👍 8 🔁 5 💬 1 📌 2
Thank you - are there particular ransomware families they are deploying that you can share?
06.07.2023 17:30 — 👍 0 🔁 0 💬 1 📌 0
Security without fear since 2018.
https://decipher.sc
https://www.youtube.com/@DecipherSec
https://www.buzzsprout.com/228511/supporters/new
WithSecure™ is Europe's cybersecurity partner of choice. Built in Europe and designed for mid-market MSPs.
Malware Stuff @ Proofpoint
Threat research at HarfangLab. Opinions are my own.
Journalist at Bloomberg News in DC. Signal: @howelloneill.01, email: patoneill1@bloomberg.net https://www.bloomberg.com/authors/AXb8dLPHBFc/patrick-howell-oneill
We are Microsoft's global network of security experts. Follow for security research and threat intelligence. https://aka.ms/threatintelblog
Chief of DIFR at SoteriaSec | SANS Institute Principal Instructor | SANS FOR509 co-author | Director MDR Uptycs | Digital Forensics & Incident Response geek.
Threat Research @ Proofpoint. Former @virtualroutes.bsky.social fellow. @warstudieskcl.bsky.social alum. She/her
Cyber Threat Intelligence Analyst
@EclecticIQ | Threat Hunter | Malware Analyst |. (All opinions expressed here are mine only). 🇹🇷🇳🇱
#cybersecurity
http://isc.sans.edu - Global Network Security Information Sharing Community - Daily blogs and cyber security news podcast.
I break into banks, spy on threats, drive a golf cart and play Lorcana
VGhlIEFuYWx5c3QgZm9ybWVybHkga25vd24gYXMgWW9zaGk=
#Cyber Intelligence and Risk Services
Free ransomware & cybers news RSS feed: https://ecrime.ch/app/intel-news.php?rss
#ransomware #monitoring #threat
COO at CheckFirst @checkfirst.network
Signal:hlx75_CF.96
#fimi #disinfo #osint #CTI #music #art #photography
Ex #VIGINUM, ex #ANSSI
Paris, France
Cybercrime & Hacktivism @ Recorded Future | Insikt Group | Curated Intelligence | @aejleslie everywhere else.
Pattern recognizer *Author: China’s Digital Colonialism, Diamond Model for Influence Operations * Public Speaker
VP at NRF for cybersecurity, AI and other tech issues. Adjunct senior fellow at CNAS, former Senate HSGAC staffer.
An Aussie who does cyber things | Manager @Huntress.com | Former Principal @CrowdStrike.com and HuntressLabs | https://jaiminton.com | https://www.youtube.com/@cyberraiju/featured
data scientist, independent variable
https://linkedin.com/in/doyle/



















