

 04.06.2025 19:39 — 👍 0 🔁 0 💬 0 📌 0
04.06.2025 19:39 — 👍 0 🔁 0 💬 0 📌 0
@xc3ll.bsky.social
Just a biologist that loves to break cyber-stuff. Adepts of 0xCC founder.


 04.06.2025 19:39 — 👍 0 🔁 0 💬 0 📌 0
04.06.2025 19:39 — 👍 0 🔁 0 💬 0 📌 0
Wow, this was fast! #OffensiveCon25 videos are up!
www.youtube.com ->
Original->

New doormat
15.05.2025 09:17 — 👍 0 🔁 0 💬 0 📌 0 06.05.2025 10:01 — 👍 6 🔁 1 💬 0 📌 0
06.05.2025 10:01 — 👍 6 🔁 1 💬 0 📌 0

Our red team is growing and we have a rare open position for a Principal RT Operator - if this sounds like you, get in touch 🙏
09.04.2025 18:55 — 👍 4 🔁 3 💬 0 📌 0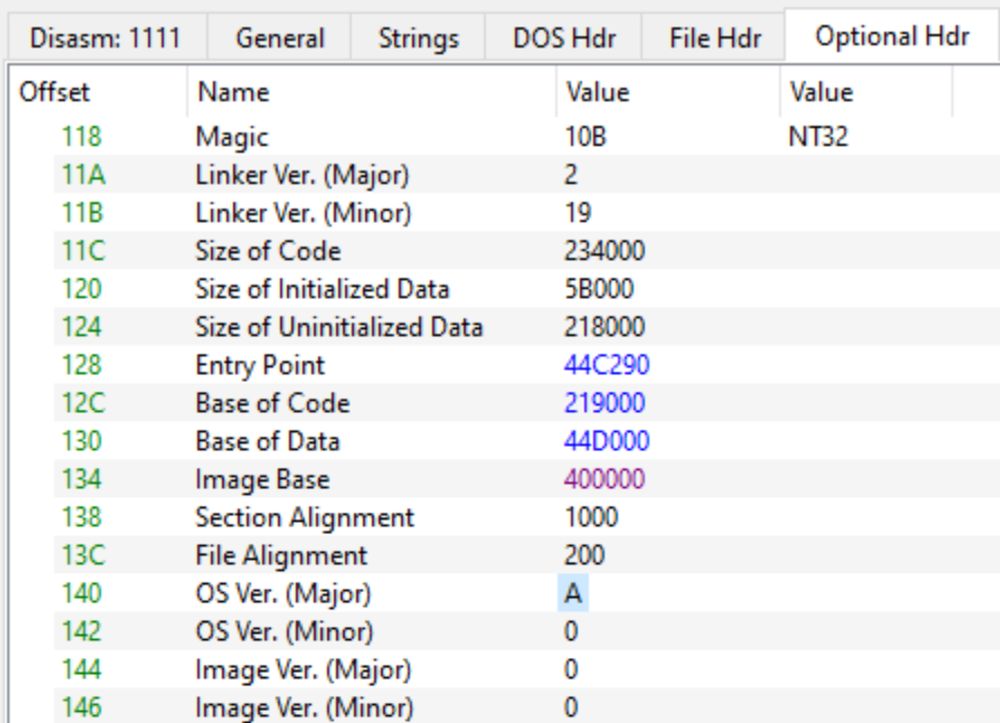
A small demo/tutorial on unpacking executables with #PEsieve and #TinyTracer: hshrzd.wordpress.com/2025/03/22/u...
- automatic OEP finding, reconstructing IAT, avoiding antidebugs and fixing imports broken by shims
I got Linux running in a PDF file using a RISC-V emulator.
PDFs support Javascript, so Emscripten is used to compile the TinyEMU emulator to asm.js, which runs in the PDF. It boots in about 30 seconds and emulates a riscv32 buildroot system.
linux.doompdf.dev/linux.pdf
github.com/ading2210/li...
New blog post on the abuse of the IDispatch COM interface to get unexpected objects loaded into a process. Demoed by using this to get arbitrary code execution in a PPL process. googleprojectzero.blogspot.com/2025/01/wind...
30.01.2025 18:37 — 👍 65 🔁 41 💬 2 📌 0 21.01.2025 08:19 — 👍 0 🔁 0 💬 0 📌 0
21.01.2025 08:19 — 👍 0 🔁 0 💬 0 📌 0
I don’t want to make a fuckin account to use my toaster. I don’t want to fuckin subscribe to software. I don’t want to create a fuckin profile to watch TV. I don’t want to fuckin register my whatever to unlock whatever. I don’t want to download a fuckin app to access anything. Death to new logins
15.01.2025 23:47 — 👍 11700 🔁 2823 💬 228 📌 194 28.12.2024 08:55 — 👍 1 🔁 0 💬 0 📌 0
28.12.2024 08:55 — 👍 1 🔁 0 💬 0 📌 0

Warming for tonight concert 🔥 www.youtube.com/watch?v=qRiA...
18.12.2024 11:07 — 👍 0 🔁 0 💬 0 📌 0Can you find an ITW 0-day from crash logs? Project Zero finds out
googleprojectzero.blogspot.com/2024/12/qual...
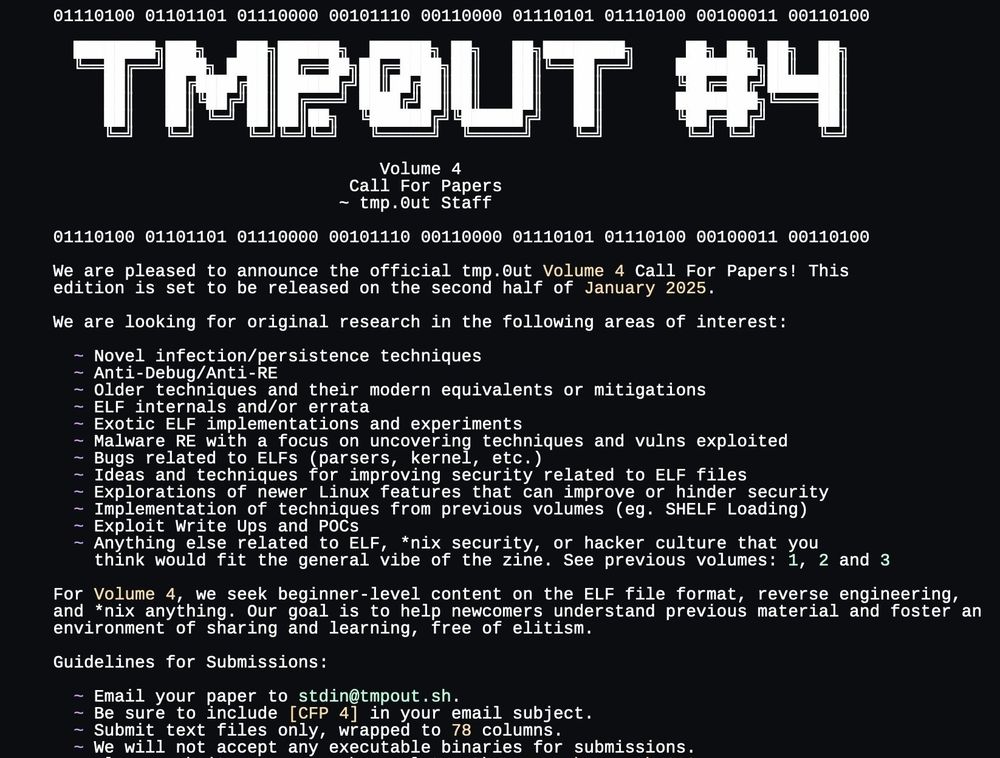
We are extending our call for papers to January 1, 2025!
We are now targeting an end of January release.
If you have any Linux/ELF related research, projects, or papers, we would love to publish them!
Huge thank you to everyone who has already submitted!
tmpout.sh/blog/vol4-cf...
@decoder-it.bsky.social and i noticed that it's no more possible to call NtLoadDriver pointing to an unprivileged regkey such as \REGISTRY\USER
Even if you have the SeLoadPrivilege you would still require the Admin group to write the required regkey.
Some more technical details below 👇
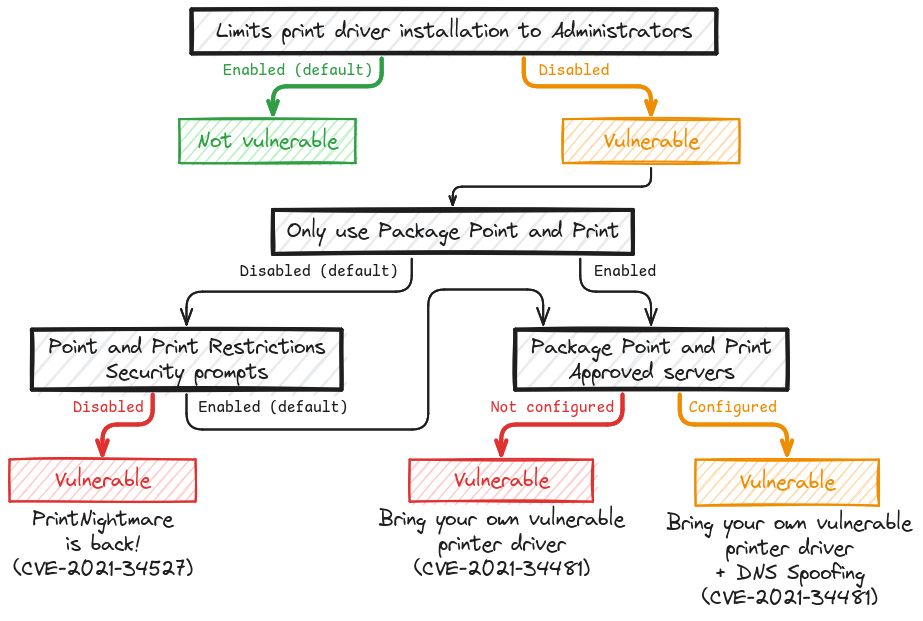
Diagram representing the various Windows Point and Print configurations that reintroduce the PrintNightmare exploit variants.
I updated the diagram representing the different Point and Print configurations and their exploitation on my blog.
Hopefully, this should provide a better understanding of the whole "PrintNightmare" situation to both defenders and red teamers. 🤞

[BLOG]
This post summarises how to tie Cobalt Strike's UDRL, SleepMask, and BeaconGate together for your syscall and call stack spoofing needs.
rastamouse.me/udrl-sleepma...

In case you missed it...the DEF CON video of my talk 'Splitting the Email Atom' is finally here! 🚀 Watch me demonstrate how to turn an email address into RCE on Joomla, bypass Zero Trust defences, and exploit parser discrepancies for misrouted emails. Don’t miss it:
youtu.be/JERBqoTllaE?...
I should start logging how many hours I'm wasting trying to to compile a static openldap lib with SASL support. I thought it would be easy but hey, second weekend trying it without luck.
10.11.2024 08:27 — 👍 0 🔁 0 💬 0 📌 0 05.11.2024 23:05 — 👍 2 🔁 0 💬 1 📌 0
05.11.2024 23:05 — 👍 2 🔁 0 💬 1 📌 0