Analysis of a Ransomware Breach
aff-wg.org/2025/09/26/a...
Breach analysis? Breach intelligence? Industry critique? Fee-only ransomware negotiator? 100% efficacy? The story of how Microsoft worked an old problem, fucked it up, we malign the guy who told us, they fixed it, and it wasn't fixed? PtH?
26.09.2025 17:12 — 👍 14 🔁 6 💬 0 📌 1

Playing with @raphaelmudge.bsky.social's latest CP update (it's very cool). I have mixed feelings about merging COFFs though. It simplifies overall development and gives the loader fewer jobs to do, but on the other hand you lose some flexibility about where each "part" goes in memory.
12.09.2025 12:48 — 👍 6 🔁 1 💬 1 📌 0

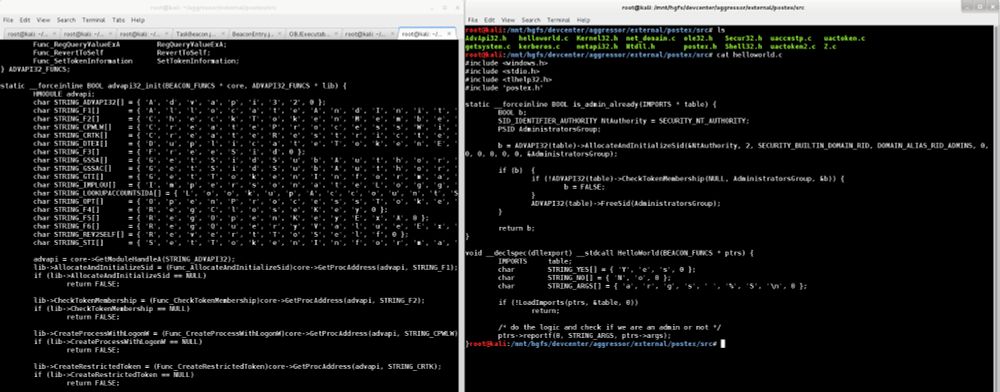
COFFing out the Night Soil
I’m back with another update to the Tradecraft Garden project. Again, this release is focused on the Crystal Palace linker. My priority in this young project is to build the foundation first, then …
COFFing out the Night Soil
aff-wg.org/2025/09/10/c...
A COFF-focused Crystal Palace update:
* internal COFF normalization & section group merging
* Crystal Palace can now export COFF
* I added COFF merging to the spec language too
Linker stuff.
10.09.2025 21:37 — 👍 11 🔁 5 💬 0 📌 1
What all do you need to know about BloodHound CE 8.0 & OpenGraph? @scoubi.bsky.social is joining @redsiege.com's Wednesday Offensive tomorrow to dive into the JSON schema for OpenGraph, how to ingest nodes & edges, best practices, & how to create custom icons.
Join 👉 ghst.ly/46MNltn
12.08.2025 16:00 — 👍 5 🔁 3 💬 0 📌 0

Certify 2.0 - SpecterOps
Certify 2.0 features a suite of new capabilities and usability enhancements. This blogpost introduces changes and features additions.
The AD CS security landscape keeps evolving, and so does our tooling. 🛠️
Valdemar Carøe drops info on Certify 2.0, including a suite of new capabilities and refined usability improvements. ghst.ly/45IrBxI
11.08.2025 20:38 — 👍 11 🔁 8 💬 0 📌 0
The ADSyncCertDump tool is now part of the adconnectdump tools and can be used to extract SP credentials from Entra ID connect hosts. I will cover that during my BH/DC talks today and Friday! Tool is heavily based on Shwmae by @ethicalchaos.bsky.social
Link: github.com/dirkjanm/adc...
06.08.2025 15:24 — 👍 5 🔁 2 💬 0 📌 0

Nemesis 2.0 - SpecterOps
Nemesis 2.0 is a complete rewrite of the Nemesis file enrichment pipeline with a simplified and extensible architecture, new interface, and a focus on file triage and operator workflows.
👋 Say hello to Nemesis 2.0, a streamlined, Docker Compose-based platform that is laser-focused on file triage. After introducing v1 two years ago, the team has reworked the platform to better serve what people need from it.
Read more from @harmj0y.bsky.social: ghst.ly/4mxQzFU
05.08.2025 16:52 — 👍 4 🔁 2 💬 1 📌 0
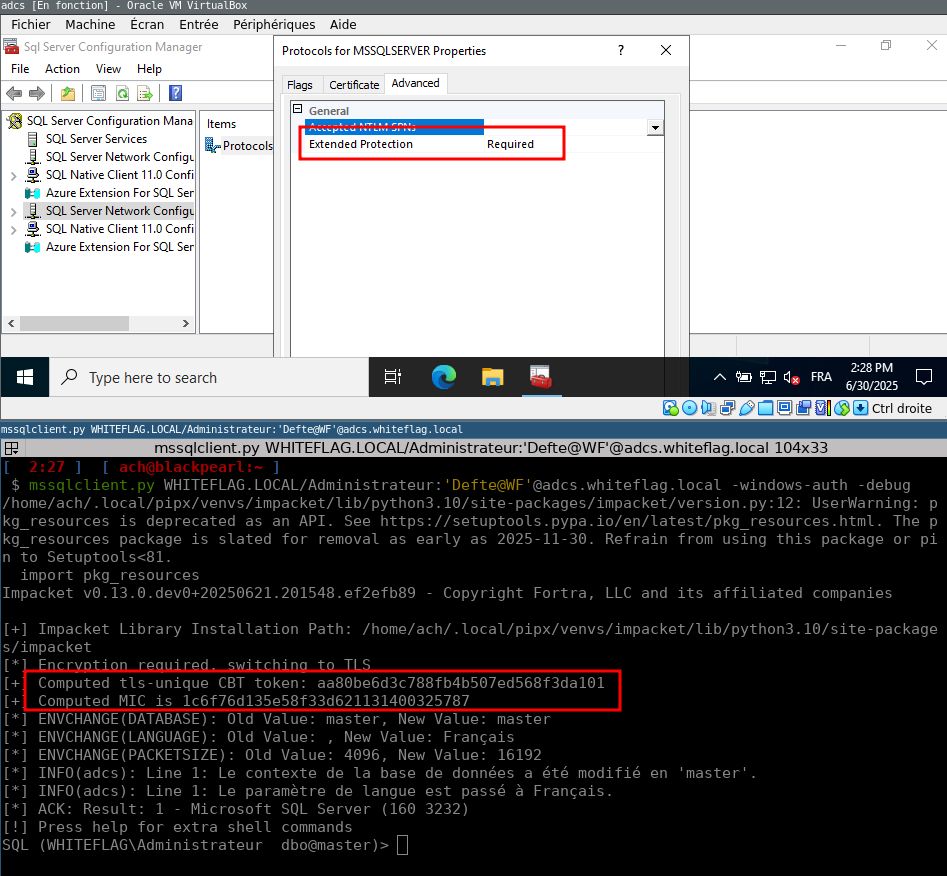
A screenshot of two windows. The top is a view of the Microsoft SQL management GUI showing that “Extended Protection” is enabled for NTLM authentication. The bottom is a terminal showing an invocation of Impacket’s mssqlclient.py successfully connecting using channel binding.
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (@Defte_ on the bird site), including instructions for reproducing the test environment yourself.
sensepost.com/blog/2025/a-...
31.07.2025 16:19 — 👍 10 🔁 6 💬 0 📌 1

Entra Connect Attacker Tradecraft: Part 3 - SpecterOps
How Entra Connect and Intune can be abused via userCertificate hijacking to bypass conditional access and compromise hybrid domains
Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and conditional access bypass.
@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9
30.07.2025 17:01 — 👍 9 🔁 6 💬 1 📌 0
BloodHound v8.0 is here! 🎉
This update introduces BloodHound OpenGraph, revolutionizing Identity Attack Path Management by exposing attack paths throughout your entire tech stack, not just AD/Entra ID.
Read more from Justin Kohler: ghst.ly/bloodhoundv8
🧵: 1/7
29.07.2025 13:13 — 👍 13 🔁 9 💬 1 📌 1

DPAPI Backup Key Compromise Pt. 1: Some Forests Must Burn - SpecterOps
Industry guidance for DPAPI backup key compromise remediation is drastic. Let's explore why.
The industry recommendation for DPAPI backup key compromise remediation is to destroy and rebuild the environment.
Alexander Sou explores why this is the current industry guidance. ghst.ly/40DTLHk
28.07.2025 18:55 — 👍 6 🔁 1 💬 0 📌 0
[BLOG]
Here's the post - I demonstrate my QoL improvements for working with the TCG codebase. This includes vscode with intellisense support, and producing debug builds for use in WinDbg.
rastamouse.me/debugging-th...
25.07.2025 11:17 — 👍 4 🔁 2 💬 1 📌 0

Escaping the Confines of Port 445 - SpecterOps
NTLM relay attacks targeting SMB restrict lateral movement options to those that solely require port 445/TCP. Learn at least one method of overcoming this restriction to enable additional lateral move...
Classic NTLM relay problem: Stuck on port 445/TCP, can't use WMI (needs 135/TCP), and dumping hashes triggers EDR alerts.
So what's a stealthy attacker to do? 🤔
Our latest blog post explores evasive alternatives beyond the old techniques. ghst.ly/3ILR1l0
25.07.2025 00:02 — 👍 8 🔁 2 💬 0 📌 0

Ghostwriter v6 is Live! - SpecterOps
TL;DR: Ghostwriter now supports real-time collaborative editing for observations, findings, and report fields using the YJS framework, Tiptap editor, and Hocuspocus server, enabling multiple users to ...
Real-time collaboration has landed in Ghostwriter v6.0! 👻
Multiple users can now edit observations, findings, & report fields simultaneously w/o the chaos of overwriting each other's work.
@printingprops.com dives into the details in his latest blog update. ghst.ly/3TTSrwc
23.07.2025 18:14 — 👍 7 🔁 1 💬 0 📌 0

Last Week in Security (LWiS) - 2025-07-21
PIC agents (@_RastaMouse), ToolShell, Async BOFs (@Cneelis), SCCM MP relays (@unsigned_sh0rt), RAITrigger (@ShitSecure), and more!
PIC agents (@_RastaMouse), ToolShell, Async BOFs (@Cneelis), SCCM MP relays (@unsigned_sh0rt), RAITrigger (@ShitSecure), and more!
blog.badsectorlabs.com/last-week-in...
22.07.2025 21:38 — 👍 2 🔁 1 💬 0 📌 0
Now live on tools.honoki.net/smuggler.html
Let me know what you think! ✨
22.07.2025 13:38 — 👍 28 🔁 11 💬 0 📌 2

Taking them to the SHITTER: an analysis of vendor abuse of security research in-the-wild
aff-wg.org/2025/07/13/t...
(There is no benefit modulating my voice for anyone's comfort. This is my fair take, but unapologetic truth. This phenomena has gone unchecked for too long)
14.07.2025 14:05 — 👍 10 🔁 7 💬 1 📌 0

LudusHound: Raising BloodHound Attack Paths to Life - SpecterOps
LudusHound is a tool for red and blue teams that transforms BloodHound data into a fully functional, Active Directory replica environment via the Ludus framework for controlled testing.
Ludushound shows the power of community driven innovation in cybersecurity. @bagelByt3s created an awesome tool to convert bloodhound data into a working lab in 🏟️ Ludus. Replicate complex live environments with automation - and get back to the fun stuff!
specterops.io/blog/2025/07...
14.07.2025 19:12 — 👍 3 🔁 1 💬 0 📌 0
DEATHcon Montreal - On Site
2 days of hands-on Detection Engineering and Threat Hunting workshops! Join us Live in Montreal.
Tickets for #DEATHcon in Montreal are on sale now!
Book now to secure your place. FYI, Virtual Tickets for round 1 are already Sold Out!
eventbrite.ca/e/deathcon-m...
Additional info (like workshops) for the con can be found here : deathcon.io
Please like & repost for reach
10.07.2025 12:59 — 👍 3 🔁 2 💬 0 📌 1
When Backups Open Backdoors: Accessing Sensitive Cloud Data via
Teammate Leonid discovered a leaked credential that allowed anyone unauthorized access to all Microsoft tenants of orgs that use Synology's "Active Backup for Microsoft 365" (ABM), including sensitive data like Teams channel messages. 🤓
#synology #disclosure #modzero
modzero.com/en/blog/when...
29.06.2025 08:01 — 👍 21 🔁 14 💬 1 📌 1

Misconfiguration Manager: Still Overlooked, Still Overprivileged - SpecterOps
It has been one year since Misconfiguration Manager's release and SCCM misconfigurations remain widespread, leading to dangerous attack paths across enterprises. Here we summarize the impact and commu...
In the year since Misconfiguration Manager's release, the security community has been actively researching new tradecraft & identifying new attack paths.
@subat0mik.bsky.social & @unsignedsh0rt.bsky.social dive into the research & its impact on the state of SCCM security. Read more: ghst.ly/460vI9d
26.06.2025 15:52 — 👍 3 🔁 3 💬 0 📌 0
Work like hell,
Share all you know,
Abide by your handshake,
Have fun. - Dan Geer
Infosec, Detection Engineering, Threat Research, Threat Hunting, OffSec, Conference Organizer.
Adversary Simulation, Red Team Lead, Security Research @ LFI
Posts are my own
He/Him
#redteam #offsec #malware #cybersecurity
https://secdsm.org
I use my real name. The trick is figuring out my handles
@natesubra@infosec.exchange
Riding around in the breeze. Security Thinker. Hacker. USAF Veteran. https://aff-wg.org
Official account for Cobalt Strike. Benchmark red teaming tool known for its flexibility and powerful user community. Follow for new releases and other updates.
BallisKit provides tooling and services to professional Pentesters & Red Teams.
We develop MacroPack Pro and ShellcodePack.
www.balliskit.com
CyberSecurity researcher and founder of BallisKit. I have a passion for all infosec subjects especially redteam and writing offensive tools!
About me?
| Website: https://mizu.re
| Tool: https://github.com/kevin-mizu/domloggerpp
| Teams: @rhackgondins, @FlatNetworkOrg, @ECSC_TeamFrance
| From: https://twitter.com/kevin_mizu
Web security research from the team at PortSwigger.
I like making computers misbehave. Does stuff at http://specterops.io.
Github: https://github.com/leechristensen
Mastodon: @tifkin_@infosec.exchange
Security researcher in Google Project Zero. Author of Attacking Network Protocols. Posts are my own etc.
Red Teamer @BHinfoSecurity. Implant Dev is my passion.
Wannabe security guy. Director @ Zero-Point Security.
Does a thing or two with red teaming @ Outflank | part time race and drift car instructor
hacker, poster, weird machine mechanic
https://chompie.rip