
#flareon12 🥲
06.10.2025 22:25 — 👍 2 🔁 0 💬 0 📌 0@ege.sh.bsky.social
Malware enthusiast. Security Researcher. Reverse Engineer. Exploit developper. Threat Intel @PRODAFT FPV drone pilot 🚁 https://twitter.com/egeblc https://ege.sh @ege@infosec.exchange

#flareon12 🥲
06.10.2025 22:25 — 👍 2 🔁 0 💬 0 📌 0
As a fun little weekend project, I have weaponized OpenReplay for exploiting XSS on "HttpOnly" websites. It allows you to remotely control a victim's browser without the need for stealing any cookies.
github.com/EgeBalci/evi...
Heading to London next week for Infosecurity Europe (3-5 June). If you're around and fancy grabbing a coffee or a beer after the exhibit, hit me up.
26.05.2025 12:04 — 👍 0 🔁 0 💬 0 📌 0
Wrote a linker patch for mangling pclntab and removing build info from Golang binaries 🙃
github.com/EgeBalci/go/...

An unidentified individual has leaked the internal chats of the BlackBasta ransomware group
x.com/PRODAFT/stat...

Finally finished #flareon11 🥲 Lost a lot of time AND SANITY on question 9. Learned a lot and had fun as always.
15.10.2024 16:23 — 👍 2 🔁 0 💬 1 📌 0Phrack #71 is ONLINE! 🔥🔥
This is literally a dream come true. My article “Evasion by De-Optimization” got accepted into PHRACK 71! It is such an honor to be considered. I still can’t wrap my head around the fact that my work has been published among the legends.
phrack.org/issues/71/1....
The new version is out 🎉 Version v0.1.2 is capable of simple control flow tracing. Now, it can find possible code paths and automatically skip dead offsets.
github.com/EgeBalci/deo...


I built myself a couple of #Meshtastic nodes 😊 I got up to 22km of range with a 443 MHz Heltec V3. Hit me up if you're near. Node names: FAP1, FAP2 (MQTT enabled).
06.07.2024 14:58 — 👍 1 🔁 0 💬 0 📌 0
Added to the collection 🥰 #flareon10
03.07.2024 10:30 — 👍 0 🔁 0 💬 0 📌 0
New tool drop! 🔥🔥 de-optimizer uses several mathematical approaches for mutating machine code instructions to their functional equivalents. Very good for bypassing rule-based detection without using any RWE memory. github.com/EgeBalci/deo...
01.07.2024 08:51 — 👍 0 🔁 0 💬 0 📌 0Attention to all AV evasion enthusiasts! 🚨🚨 I'll be talking about how to bypass security products by de-optimizing x86 binaries at Insomni'hack. See you all at Lausanne 👋 #INSO24 www.insomnihack.ch/talks-2024/?...
21.03.2024 12:35 — 👍 0 🔁 0 💬 0 📌 0
Oops 😆 #Lockbit
20.02.2024 13:21 — 👍 0 🔁 0 💬 0 📌 0
SGN v2.0.1 is out! 🔥🎊🎉 Here are the changelogs:
- Register value preserving (-safe option) related bug fixes
- Random register selection bug fixed
- Better argument parsing
- Major code refactoring
github.com/EgeBalci/sgn...

Some TAs are using Github issues to target repo owners with crypto scams. Github notification mails are guaranteed to reach your inbox, bypassing any spam filters and security products. The content of the scam is very basic, but I can give points for creativity for sure :)
16.11.2023 12:02 — 👍 0 🔁 0 💬 0 📌 0
QSocket v0.0.6-beta released 🔥🎊🎉
- New websocket based knock protocol
- QSRN moved behind Cloudflare CDN
- Multi session support
- Better traffic forwarding capabilities
- Terminal QR code generation on deploy
github.com/qsocket/qs-n...
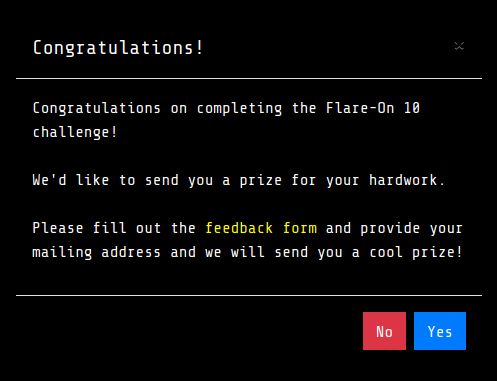
Finished #flareon10 in 69th place this year. 🎉🎉 It was definitely the hardest year. I had so much fun and agony at the same time. Next year's goal is to top 30.
20.10.2023 10:00 — 👍 1 🔁 0 💬 0 📌 0
Dibs on CVE-2023-32560 🔥 I have added the Ivanti Avalanche MDM buffer overflow (DEP bypass) exploit this week. 🎉🎉 I'll take a break from writing N-days until the end of Flareon. www.rapid7.com/blog/post/20...
22.09.2023 18:29 — 👍 0 🔁 0 💬 0 📌 0
Added two more ZDI exploits this week 🎉🎉 VMware vRealize Log Insight RCE module was very interesting, it chains together tree vulnerabilities for code execution.
www.rapid7.com/blog/post/20...

I was reading the PoC for the CVE-2023-37903 NodeJS sandbox escape, and I remembered that box-js was also using vm2 for emulation. Escape is looking very easy; I suggest you don't use emulation on analysis until the update. ¯\_(ツ)_/¯ gist.github.com/leesh3288/e4...
10.09.2023 11:25 — 👍 0 🔁 0 💬 0 📌 0
I was able to write 10+ RCE exploits last month just by following ZDI and CVE feeds. Ended up at No. 1 on the Metasploit contributions last month 😁
08.09.2023 20:17 — 👍 0 🔁 0 💬 0 📌 0If you can’t reproduce the bug, you simply need to do more reversing. At the end, the prize is guaranteed; you're not wasting your time. This could be a very good starting point for beginners. There are a lot of critical vulnerabilities being disclosed without a proper exploit.
08.09.2023 20:17 — 👍 0 🔁 0 💬 1 📌 0I’ve realized that I’m having much more fun writing N-day exploits than doing vuln research. It takes MUCH LESS time and equally sharpens your skills, maybe even more. Writing N-days with just a brief CVE description is very much like solving a CTF challenge.
08.09.2023 20:16 — 👍 1 🔁 0 💬 1 📌 1
Added another ZDI exploit this week, more on the way 🎉 www.rapid7.com/blog/post/20...
01.09.2023 16:38 — 👍 1 🔁 0 💬 0 📌 0Ivanti Avalance making a lot of hackers happy nowadays 😁
26.08.2023 16:24 — 👍 0 🔁 0 💬 0 📌 0
+2 this week. Lets goo! 🔥🔥🔥
https://www.rapid7.com/blog/post/2023/08/18/metasploit-weekly-wrap-up-23/

It's that time of the year again :(
12.08.2023 22:24 — 👍 0 🔁 0 💬 0 📌 0
use exploits/multi/http/rudder_server_sqli_rce 🎉🎉
https://www.rapid7.com/blog/post/2023/08/04/metasploit-weekly-wrap-up-22/