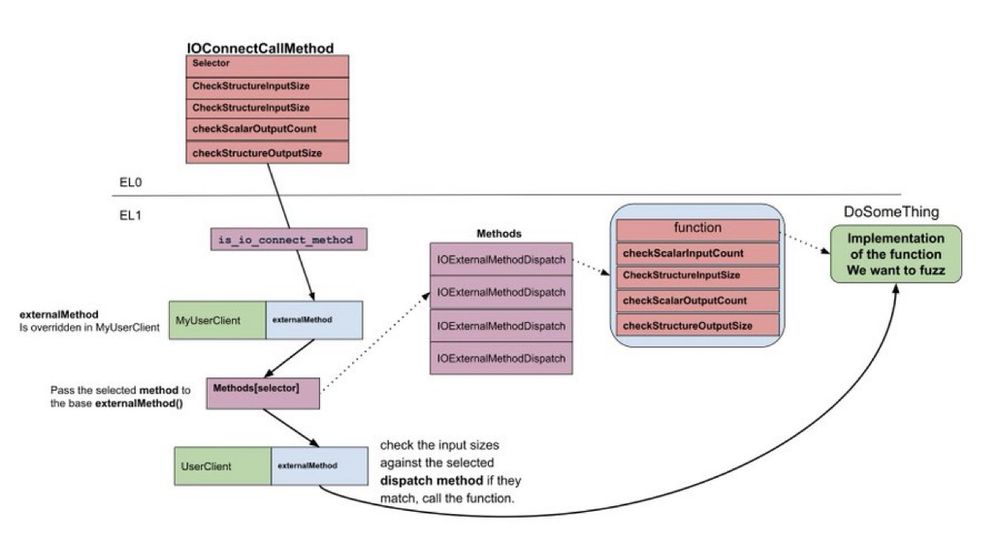
Come learn how to hack the XNU kernel, like a pro 🍎
with beautiful diagrams to guide every step. :)
📅 Nov 10-12 (3 days)
📍 Four Seasons Hotel Seoul, South Korea
🔗 More info powerofcommunity.net/#training
@r00tkitsmm.bsky.social
Security Researcher.

Come learn how to hack the XNU kernel, like a pro 🍎
with beautiful diagrams to guide every step. :)
📅 Nov 10-12 (3 days)
📍 Four Seasons Hotel Seoul, South Korea
🔗 More info powerofcommunity.net/#training
Here is the source code of my fuzzer ai development for macOS.
github.com/R00tkitSMM/P...
Oh, We have a long weekend ahead in Germany/Berlin.
Maybe I can finish my unpublished blog posts.
Share blogs or papers that I can read and enjoy.
My new blog post, which I presented at #Zer0Con2025
A binary level macOS KEXT kernel address sanitizer
r00tkitsmm.github.io/fuzzing/2025...
Will be in Korea next week for Zer0Con. Ping me and let’s chat about software security.
03.04.2025 17:42 — 👍 2 🔁 0 💬 1 📌 0Paged Out! #6 has arrived! And it's jam-packed with content!
You can download it here:
pagedout.institute?page=issues....
Happy to share my slides from BOOTSTRAP25. Unfortunately the bug discussed is still not patched in Linux 6.14.0 despite it being reported explicitly. Slides are in markdown but there's a PDF in "releases" too github.com/jduck/bs25-s...
25.03.2025 19:26 — 👍 14 🔁 7 💬 1 📌 0[RSS] The Evolution of Dirty COW (1)
u1f383.github.io ->
Original->

Neat, #riscv emu with #LibAFL support
github.com/fkie-cad/squid
Did you know that pressing CTRL+D in linux terminal is like pressing ENTER? (to some extent, of course)
Well, I didn't, so after randomly investigating what CTRL+D actually does, I've decided it's a fun topic to write about:
hackarcana.com/article/ctrl...
This is so cool: The LibAFL_QEMU ASan implementation was ported to rust
github.com/AFLplusplus/...
#LibAFL #QEMU #ASan #Rust
I will talk about macOS Kernel fuzzing at the zer0con.org#schedule-sec... conference.
10.03.2025 18:27 — 👍 4 🔁 0 💬 0 📌 0Very interesting thank you
22.01.2025 16:45 — 👍 0 🔁 0 💬 0 📌 0I usually dig into a topic I research by googling and reading blogs, manuals, sources,… and have not read a technical book for a year.
What would you recommend for low level software/CPU/OS security/exploit topics?
All videos from The 38th Chaos Communication Congress (38C3) 2024:
media.ccc.de/b/congress/2...
#cybersecurity #informationsecurity #hacking #exploitation #iOS #android #apple #exploitation #reverseengineering #vulnerability
Doing Apple Silicon’s security research for days non stop. Hope it becomes a blogpost at some point.
29.12.2024 20:15 — 👍 2 🔁 0 💬 0 📌 0I sometimes print them. But I think iPad is the only option to deal with PDFs.
28.12.2024 21:21 — 👍 1 🔁 0 💬 0 📌 0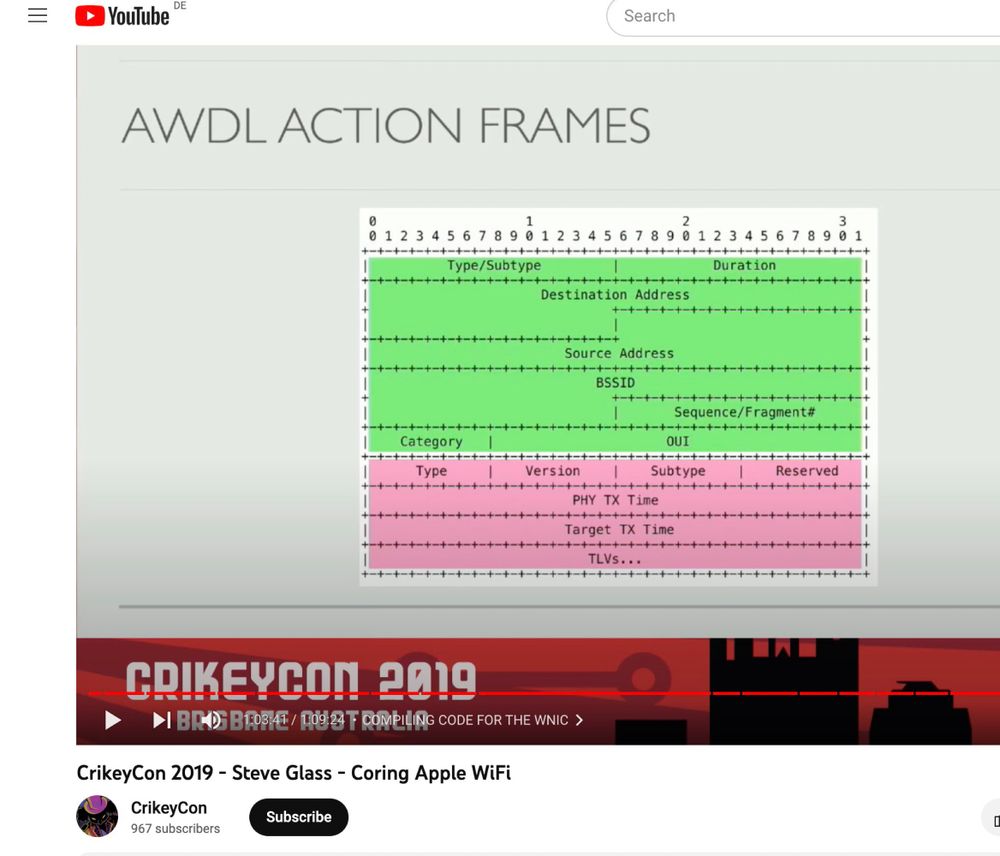
Steve Glass, talks about potential vulnerabilities in TLV parser of AWDL in jun 2019,
And some months later ian beer reported that famous vulnerability in exactly TLV parser of AWDL.
Conferences are sources of ideas.
It’s not* the best option. :)
28.12.2024 13:34 — 👍 1 🔁 0 💬 1 📌 0Where do you read papers? I have kindle and it’s the best option.
28.12.2024 09:47 — 👍 0 🔁 0 💬 3 📌 0Thank you it’s too late for me now.
27.12.2024 11:50 — 👍 0 🔁 0 💬 0 📌 0I’m in Hamburg, but wouldn’t attend #38c3 due to ticket issue :)
27.12.2024 10:21 — 👍 2 🔁 0 💬 1 📌 0Re-sharing to keep bluesky rolling
go.bsky.app/EhGFSVj

I have read and watched a lot of papers and presentations this week about
Compiler 🤝 OS 🤝SoC
security.
www.youtube.com/watch?v=bytW...
www.youtube.com/watch?v=C1nZ...
These two are about PAC
Pishi2 needed more compiler/LLVM
Knowledge.
This is very good reference.
llsoftsec.github.io/llsoftsecbook/
Have written new macOS binary level fuzzing blog post.
Second part of
r00tkitsmm.github.io/fuzzing/2024...
Don’t know when to publish it
Took 3 weeks off, bought a new MacBook. It’s to to fuzz the kernel.
29.11.2024 21:33 — 👍 7 🔁 0 💬 0 📌 0