Decrypting PDQ credentials | unsigned_sh0rt's blog
Walkthrough of how PDQ credentials encrypts service credentials
Had some fun with PDQ deploy/inventory credential decryption and wrote about it here: unsigned-sh0rt.net/posts/pdq_cr... thanks to
@dru1d.bsky.social for writing a BOF out of the POC
tl;dr get admin on PDQ box, decrypt privileged creds
11.04.2025 21:09 — 👍 9 🔁 6 💬 0 📌 0
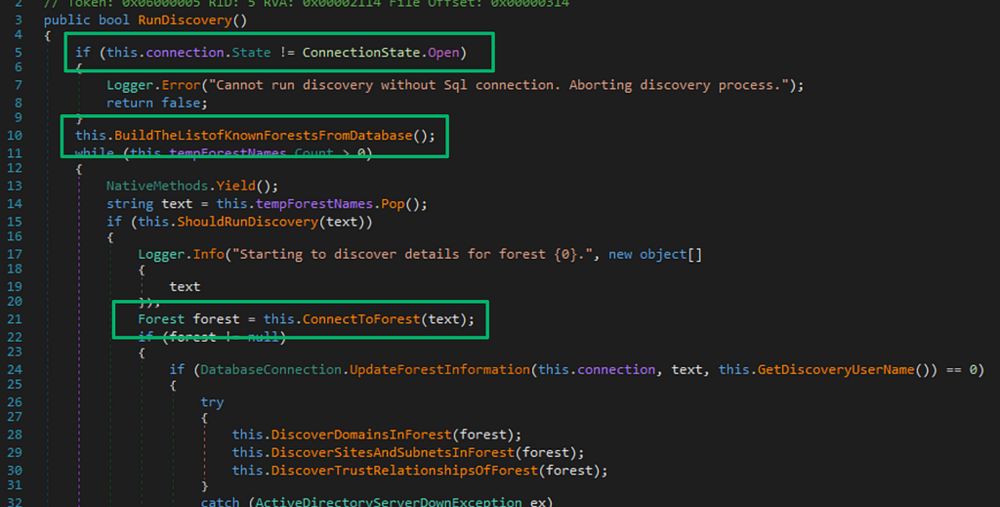
Decrypting the Forest From the Trees - SpecterOps
TL;DR: SCCM forest discovery accounts can be decrypted including accounts used for managing untrusted forests. If the site server is a managed client, service account credentials can be decrypted via ...
#SCCM forest discovery accounts can be decrypted—even those for untrusted forests. If the site server is a managed client, all creds can be decrypted via Administration Service API.
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp
06.03.2025 20:34 — 👍 22 🔁 15 💬 1 📌 0

Relaying Kerberos over SMB using krbrelayx
Awesome new addition to krbrelayx by Hugow from Synacktiv: www.synacktiv.com/publications...
20.11.2024 16:02 — 👍 29 🔁 14 💬 0 📌 0

Claude
Talk with Claude, an AI assistant from Anthropic
Claude.ai is so sick. I might actually fool people into believing I know how to code with this
21.11.2024 05:33 — 👍 5 🔁 0 💬 0 📌 0
 15.11.2024 05:42 — 👍 3 🔁 0 💬 0 📌 0
15.11.2024 05:42 — 👍 3 🔁 0 💬 0 📌 0
 15.11.2024 05:42 — 👍 4 🔁 0 💬 1 📌 0
15.11.2024 05:42 — 👍 4 🔁 0 💬 1 📌 0
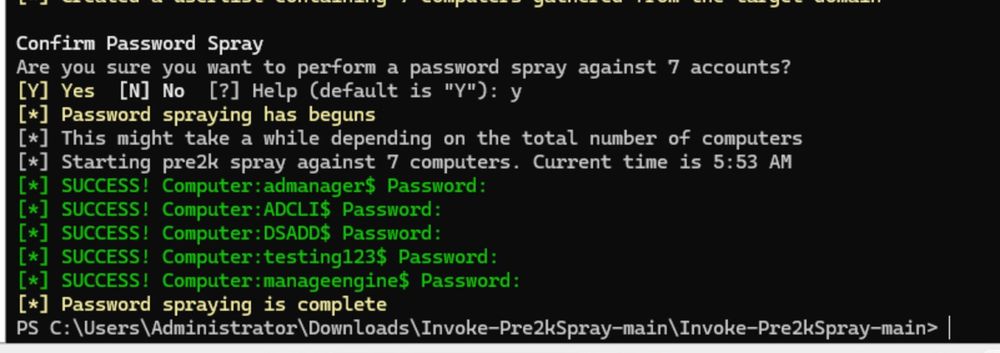
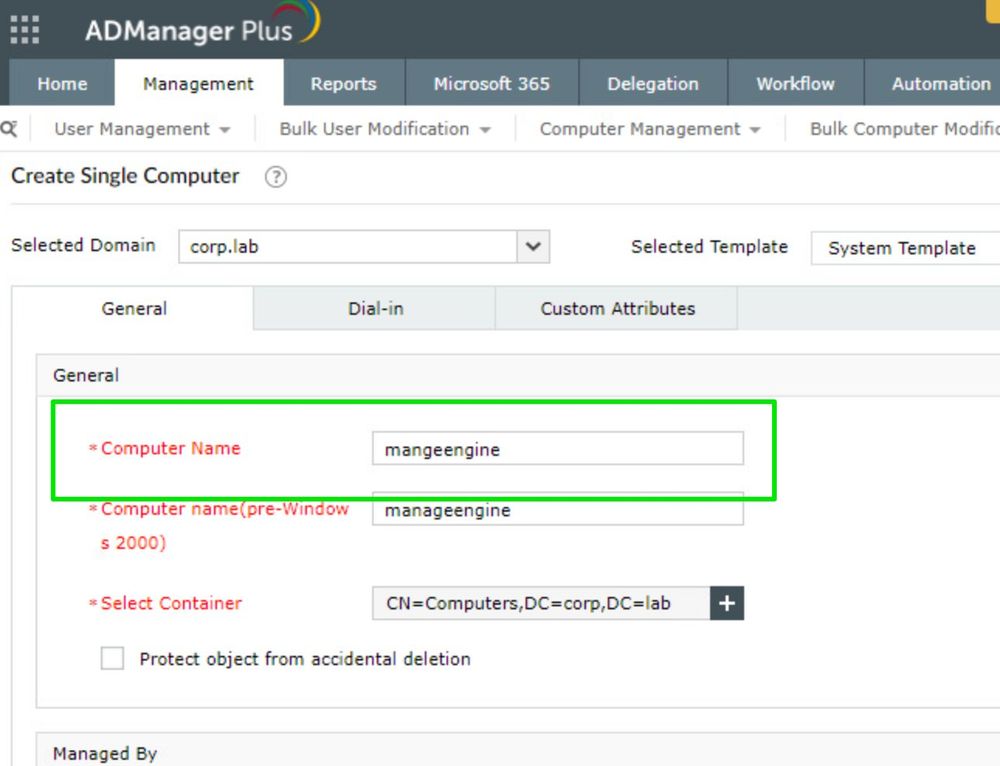
It's not limited to just ADCLI either...ManageEngine is probably the most familiar or recognizable tool that does this. It's true microsoft fixed creating them in ADUC but hardly fixed things where third party tools are involved.
15.11.2024 05:33 — 👍 4 🔁 0 💬 1 📌 0
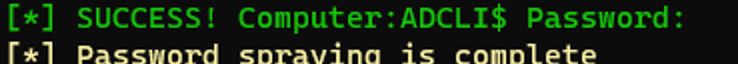
So what's happening? The tool before would create the computer object without a password and then set it to a default after the fact. Now, that password setting is blocked and the object persists...with no password.
15.11.2024 05:30 — 👍 4 🔁 0 💬 1 📌 0
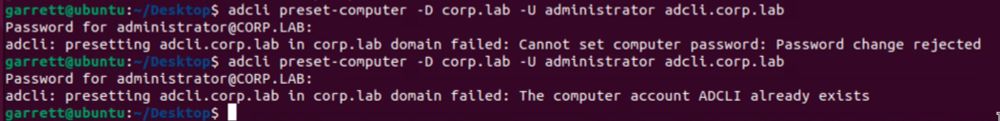
But now, you get a failure as you cannot change the accounts password. However, it STILL creates the object.
15.11.2024 05:29 — 👍 4 🔁 0 💬 1 📌 0
I had a hunch though that behavior might not be true for third party tools and third-party tools were arguably the biggest cause of their existence across all the enviroments I've tested over the years. An example of this is the adcli command line tool. Before it would set with a default password.
15.11.2024 05:28 — 👍 4 🔁 0 💬 1 📌 0
Was doing some digging "What's New" in Server2025 learn.microsoft.com/en-us/window... specifically the changes to pre-2k machines. Oddvar and I had spoken previously about the changes being solid and demonstrated pre-created machines in ADUC could no longer be set with a default password.
15.11.2024 05:25 — 👍 10 🔁 5 💬 1 📌 0
Guess this is the place to be then
12.11.2024 04:04 — 👍 7 🔁 0 💬 0 📌 0
Компьютерный хулиган. Adversary Simulation @ CDW
Does stuff at @specterops
Cloud security research
Arizona's hacker con. CactusCon 14: Feb 6-7, 2026 in beautiful Mesa, AZ. https://cactuscon.com + LinkedIn, X, Mastodon
you sure this infosec thing was a good idea?
Red Team Operator @ CrowdStrike
Privilege Escalation Engineer
Principal Consultant @ Reversec (formerly WithSecure Consulting)
Music | InfoSec | Perennial white belt | DC541
Doing Windows Security @ Microsoft | OSCP
https://hackback.zip
Creators of BloodHound | Experts in Adversary Tradecraft | Leaders in Identity Attack Path Management
I enjoy security, technology, learning, books, & the great outdoors.
Trying to be human & kind.
Opinions = mine. He/Him/Hän
https://github.com/JimSycurity
https://www.adminsdholder.com
Security person who likes writing code
IT generalist with an infosec slant. Testing out the new hotness over here.
(he/him) Dad / Husband / Marine / Student / Teacher / @Hak5 / @NoVAHackers / @SiliconHBO / @NationalCCDC / @MARFORCYBER Auxiliary
Windows Internals Author, Developer, Reverse Engineer, Security Researcher, Speaker, Trainer, and most recently Nation State Hacker.
Core OS Platform Developer at Apple, Hyper-V Vendor at Microsoft, Chief Architect at CrowdStrike and now Director at CSE.
Kerberoast Guy • RedSiege CEO • Hater of Pants • Former SANS 560 Author, Senior Instructor • Packers owner • Work Req: http://redsiege.com/contact



 15.11.2024 05:42 — 👍 3 🔁 0 💬 0 📌 0
15.11.2024 05:42 — 👍 3 🔁 0 💬 0 📌 0
 15.11.2024 05:42 — 👍 4 🔁 0 💬 1 📌 0
15.11.2024 05:42 — 👍 4 🔁 0 💬 1 📌 0

