Detailed write-up: jonny-johnson.medium.com/no-agent-no-...
GitHub project "JonMon-Lite": github.com/jonny-jhnson...
@jonny-johnson.bsky.social
Principal Windows Security Researcher @HuntressLabs | Windows Internals & Telemetry Research

Detailed write-up: jonny-johnson.medium.com/no-agent-no-...
GitHub project "JonMon-Lite": github.com/jonny-jhnson...

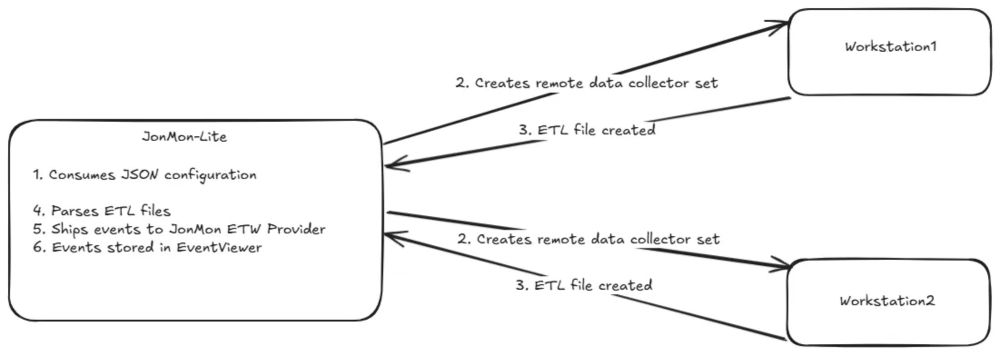
Have you ever wondered if there was a way to deploy a "Remote EDR"? Today I'm excited to share research I've been working on for the past couple months.
This dives into DCOM Interfaces that enable remote ETW trace sessions without dropping an agent to disk.
(Write-up and project link below)
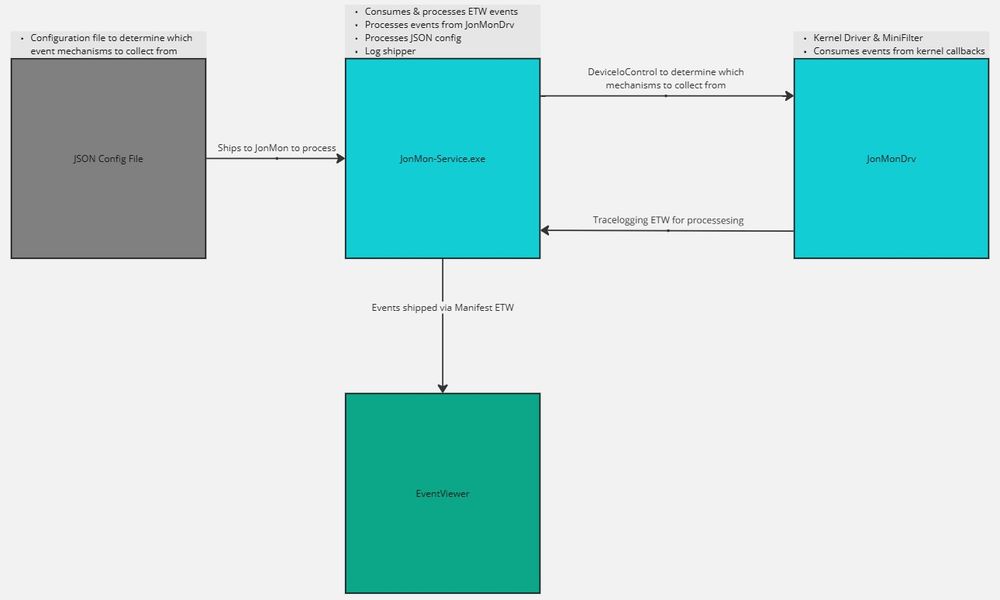
I am happy to announce JonMon2.0 has been published.
2.0 offers a lot of feature updates, as well as stability. More features still to come as time goes on. Enjoy and let me know if you have any issues or questions.
Link: github.com/jsecurity101...
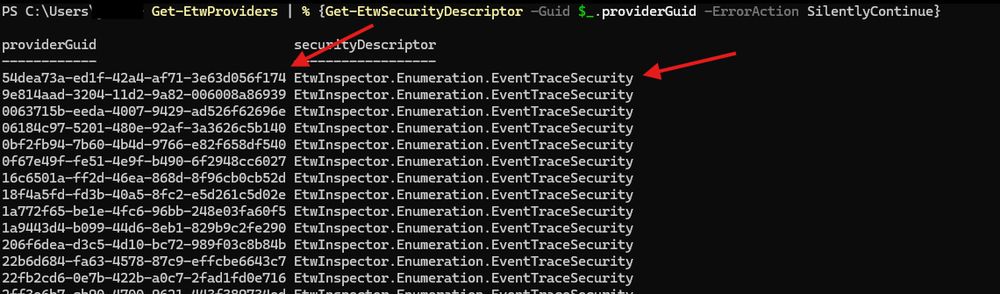
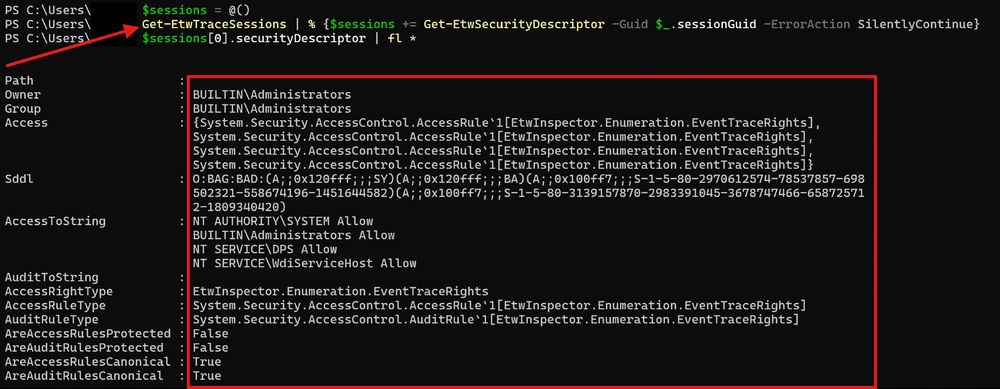
New EtwInspector kinda going hard 👀
16.01.2025 14:07 — 👍 1 🔁 0 💬 0 📌 0
The perfect loader library was updated this week to support changes made on Windows 11 24H2. A big thank you to Jarrod Davis (@tinybiggames.com) for reporting the issue and helping work on a solution!
A full writeup on the issues and fixes can be found here:
github.com/EvanMcBroom/...
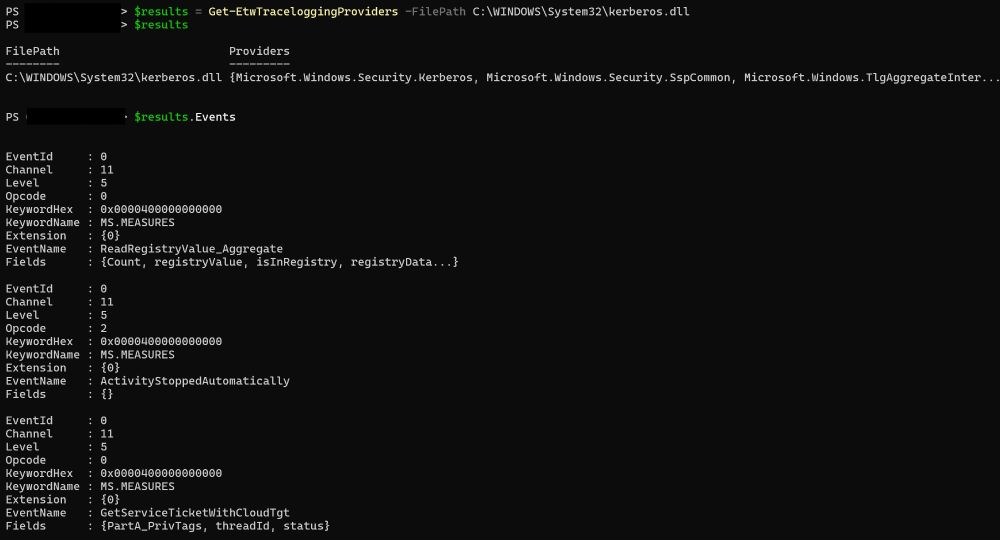
Converted Matt Graeber's TraceLogging PS script into C# into the new EtwInspector.
gist.github.com/mattifestati...
Working quite well.
New EtwInspector coming soon...
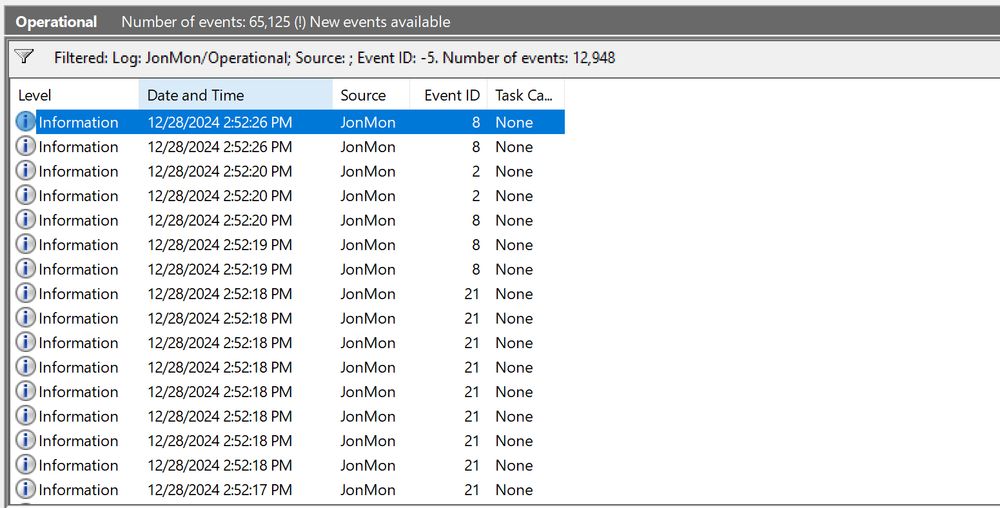
My goal by the end of the year was to finish JonMon 2.0 and I am happy to say that I have done that....Now just to clean up the code, fix the wiki, and write a blog. Stay tuned :)
28.12.2024 22:54 — 👍 2 🔁 0 💬 0 📌 0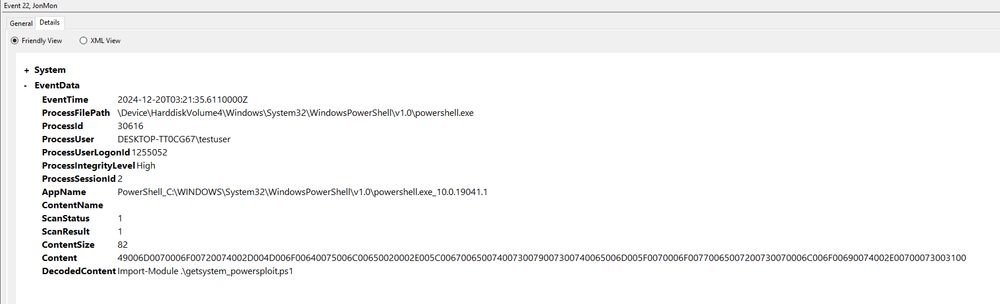
JonMon with the AMSI logs 👀
20.12.2024 03:59 — 👍 1 🔁 0 💬 0 📌 0Oh this is sick I didn’t know this. Thanks for sharing!
13.12.2024 02:47 — 👍 0 🔁 0 💬 0 📌 0Oh LETS GO
13.12.2024 02:46 — 👍 0 🔁 0 💬 0 📌 0Microsoft's Threat-Intelligence ETW provider now supports events to identify token impersonation attacks. I wrote a blog on these events and how Microsoft is surfacing them:
jsecurity101.medium.com/behind-the-m...