There's a new ClickFix variation called FileFix
This one works by tricking users into copying a file path in Windows Explorer.
Attackers modify the clipboard, so you're actually pasting and running PowerShell ahead of the file path
mrd0x.com/filefix-clic...
24.06.2025 08:28 — 👍 31 🔁 11 💬 2 📌 1
The #FBI and #DCIS disrupted #Danabot. #ESET was one of several companies that cooperated in this effort. www.welivesecurity.com/en/eset-rese... 1/6
22.05.2025 20:06 — 👍 10 🔁 8 💬 1 📌 0

First page of the paper
Wrote a paper, with Daniel Nakov, on comparing the #quality & the speed of #malware analysis assisted by #r2ai, or without.
Spoiler 1: quality is =, speed is ++.
Spoiler 2: do not expect to get good results in a single question.
arxiv.org/pdf/2504.07574
cc: @radareorg.bsky.social #arxiv #radare2
14.04.2025 06:40 — 👍 7 🔁 5 💬 1 📌 0

#ESETresearch has discovered a zero day exploit abusing #CVE-2025-24983 vulnerability in Windows Kernel to elevate privileges (#LPE). First seen in the wild in March 2023, the exploit was deployed through #PipeMagic backdoor on the compromised machines. 1/4
11.03.2025 17:15 — 👍 18 🔁 12 💬 1 📌 0

Hindsight v2025.03 Released!
Hindsight v2025.03 focuses on Extensions - parsing more activity and state records, highlighting Extension permissions, and making it easier to examine Manifests.
There's a new Hindsight release!
Hindsight v2025.03 focuses on Extensions - parsing more activity and state records, highlighting Extension permissions, and making it easier to examine Manifests.
🌐 Blog: dfir.blog/hindsight-pa...
🛠️ Tool download: hindsig.ht/release
#DFIR #Chrome #Extensions
11.03.2025 17:08 — 👍 8 🔁 4 💬 0 📌 0
Chrome 134 is out and there's a new system that automatically blocks unpacked Chrome extensions from running if Developer Mode is not enabled first.
05.03.2025 19:59 — 👍 12 🔁 5 💬 1 📌 0
No more platform-hopping! 🕵️♂️ Hunt across all abuse.ch platforms with just 1️⃣ simple query. 🔎 Search for any IPv4, domain, URL, or file hash, and instantly see if it’s been identified on any abuse.ch platform!
Start your hunt now 👉 hunting.abuse.ch
26.02.2025 13:01 — 👍 21 🔁 12 💬 0 📌 0
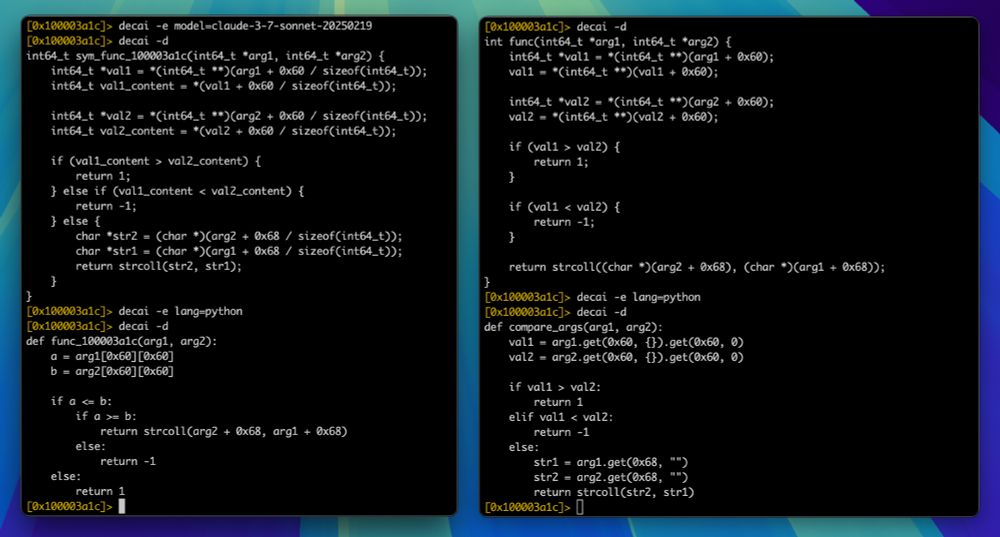
Comparing Decai decompilation using @anthropic.com 's Claude 3.5 vs 3.7 with a simple strcoll wrapper function #r2ai #radare2
25.02.2025 12:35 — 👍 6 🔁 5 💬 1 📌 0

You receive a laptop (powered off) in a high-stakes case. You are told the owner is extremely technical but given no useful technical details. The laptop is modern, with chassis intrusion features, and you must assume Secure Boot & BitLocker are in use. How do you proceed? #DFIR
18.02.2025 19:17 — 👍 2 🔁 1 💬 1 📌 1

An inside look at NSA (Equation Group) TTPs from China’s lense
If you live in the West, it's not often you read about CIA/NSA cyber operations against China. But here's one: "How the NSA Allegedly Hacked China’s Northwestern Polytechnical," a leading Chinese university specializing in aerospace & defence. www.inversecos.com/2025/02/an-i...
19.02.2025 22:51 — 👍 22 🔁 14 💬 2 📌 5
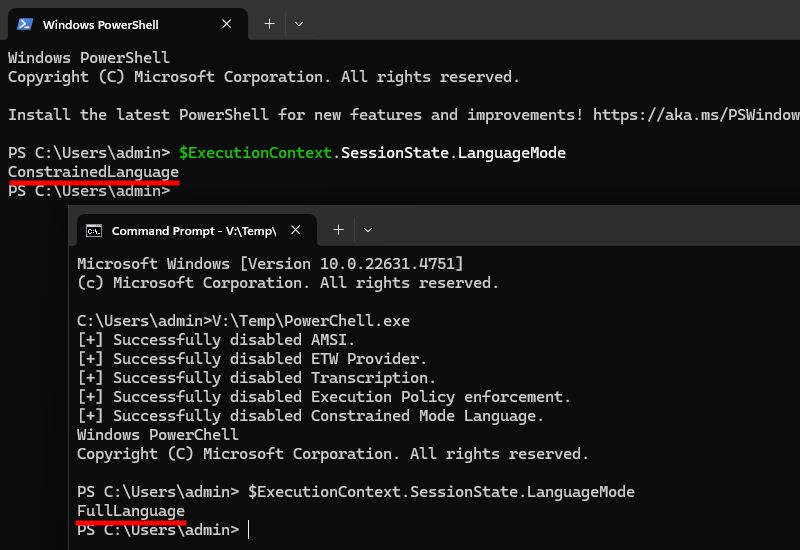
Screenshot showing the execution of the proof-of-concept named PowerChell in comparison to a typical PowerShell prompt. In particular, it shows that PowerChell is able to bypass the Constrained Language Mode (CLM).
In this blog post, I explain how I was able to create a PowerShell console in C/C++, and disable all its security features (AMSI, logging, transcription, execution policy, CLM) in doing so. 💪
👉 blog.scrt.ch/2025/02/18/r...
19.02.2025 09:13 — 👍 43 🔁 19 💬 2 📌 2
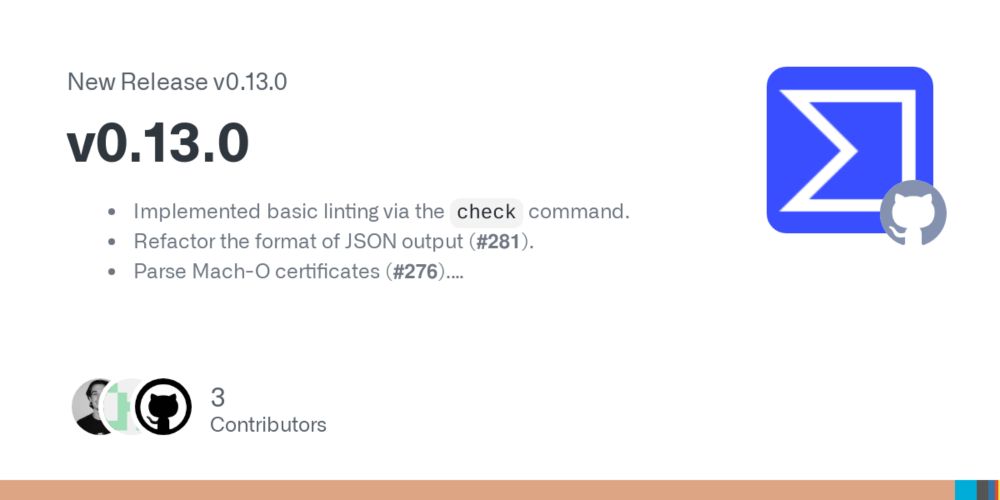
Release v0.13.0 · VirusTotal/yara-x
Implemented basic linting via the check command.
Refactor the format of JSON output (#281).
Parse Mach-O certificates (#276).
Allow using previously defined variables in with statements (#287).
BUG...
YARA-X 0.13.0 is out: github.com/VirusTotal/y...
As always, Victor and the contributors are cranking out quality improvements!
In particular, check out the docs on how to use the formatter and linter and open issues (or tell me somehow) if you hit bugs or have things you want to see.
03.02.2025 18:04 — 👍 8 🔁 4 💬 1 📌 0
The threat landscape in H2 2024 was quite tumultuous when it comes to some of the most prominent infostealer threats. One of them, the notorious #RedLine Stealer, finally met its demise after being taken down by law enforcement in #OperationMagnus. #ESETresearch 🧵 1/5
01.02.2025 04:36 — 👍 7 🔁 5 💬 1 📌 1

by savage | 2025-01-22
A "code family" is a basic concept in @vertexproject.bsky.social's approach to tool analysis. Check out the next installment in Mary Beth Lee's malware manifesto as she defines "code family", how it differs from "malware family", and how this aids your #CTI analysis!
vertex.link/blogs/catego...
27.01.2025 16:58 — 👍 11 🔁 5 💬 0 📌 0
Introducing Venture, a cross-platform viewer for Windows Event Logs! This is an overview of the early alpha at v0.2.0. Grab Venture at https://github.com/mttaggart/venture/releases/latest!
Venture Windows Log Viewer: Early Alpha Overview
Here's a video overview of Venture, the cross-platform Windows Event Viewer. Version 0.2.0 now has the ability to join multiple .evtx files into a single view!
www.youtube.com/watc...
Grab Venture here: github.com/mttaggart...
22.01.2025 21:02 — 👍 32 🔁 13 💬 1 📌 3

Intune Attack Paths — Part 1
Intune is an attractive system for adversaries to target…
Check out this new blog post from @andyrobbins.bsky.social discussing the fundamental components & mechanics that enable the emergence of critical Attack Paths in Microsoft's increasingly popular Intune product. ghst.ly/3Cd5cwH
15.01.2025 17:48 — 👍 6 🔁 4 💬 0 📌 0


live #dprk fake interview site up and running if you're looking to experiment ... digitptalent[.]com ... both windows and mac malware
13.01.2025 15:22 — 👍 2 🔁 1 💬 0 📌 0
Even on Friday evenings? 😈
08.01.2025 19:54 — 👍 0 🔁 0 💬 0 📌 0
I know the feeling! 🤣
08.01.2025 17:16 — 👍 1 🔁 0 💬 0 📌 0
*non-cyber people 😄
19.12.2024 17:54 — 👍 0 🔁 0 💬 0 📌 0

Phishing platform Rockstar 2FA trips, and “FlowerStorm” picks up the pieces
A sudden disruption of a major phishing-as-a-service provider leads to the rise of another…that looks very familiar
Just put out this research on MiTM PaaS kits labeled Rockstar and Flowerstorm over the past few months. While my name is on this I partnered with two researchers, Josh Rawles and Jordon Olness who did a bulk of the work alongside @thepacketrat.net, and Colin Cowie who are all individually brilliant!
19.12.2024 16:17 — 👍 4 🔁 3 💬 1 📌 0

🐧 It’s finally here! 🔍
The Linux EDR Telemetry Project results are live! After months of testing and collaboration, we’re excited to share how well EDR solutions handle Linux visibility.
Read the full blog here: 📝👇
kostas-ts.medium.com...
1/2
17.12.2024 15:30 — 👍 12 🔁 10 💬 1 📌 0
NorthSec — A community-run cybersecurity event offering world-class talks, trainings & a 48-hour, on-site capture-the-flag competition. Every May in Montréal since 2013 🇨🇦 Publications en français et en anglais.
https://nsec.io/
Master of (Keeping/Stealing) your Secrets | Security Advisor & Intel Analyst | Civil Servant @ BE | Klopjacht-speurder | IT Eng. + Pol. Sci. | Posts my own
Native Hawaiian Hacker | Prev Co-captain of @Shellphish | PhD Student in Comp Sci @ASU l Decompiler Research | https://mahaloz.re
Malware analysis can be hard, but learning it shouldn’t be.
https://training.invokere.com
professional strings(1) operator
rust reverse engineering training -> @decoderloop.com
she/her or they/them
🏳️🌈😎
personal account! views are mine.
https://cxiao.net
https://infosec.exchange/@cxiao
Android malware analysis. Ph0wn CTF founder. IoT hacking. Frequent speaker at Virus Bulletin, Insomnihack etc. Based in France.
Currently testing Bluesky. Otherwise on Mastodon.social.
Ninja Owl specialises in Proactive Cyber & Privacy Security.
📰: This is our auto news feed to keep you up-to-date and aware.
🕸️: https://ninjaowl.ai
#cybersecurity #hacking #news #security #technology #infosec #osint
🔳 founder of @greynoise.io. computers, networks, technology enthusiast. big goober.
Just someone that dabbles in threat research, malware analysis, RE, incident response, CTFs, and old school forensics.
Apologetic ginger.
#OSINT enthusiast, started OSINTing when Usenet was still big, اوسینت
Woman. Hacker. Artist. Researcher at CTU in Prague. BlackHat Trainer. BlackHat Review Board. Making good things happen. Intelligence and Security Studies Master student at LJMU. Argentinean in Czechia.
A fork of https://twitter.com/xme
http://isc.sans.edu - Global Network Security Information Sharing Community - Daily blogs and cyber security news podcast.
Notre métier ? Protéger le vôtre !
Management des risques, Évaluation, Cyber Threat Intelligence, Détection, Réponse (CERT), Innovation.
Pour en savoir plus, visitez intrinsec.com
DFIR. Ex-Lead intelligence. Ex @ANSSI_FR. PhD in intl law. Mostly working on Chinese #APT but also on russian and cybercrime actors #ThreatIntel #Malware #DFIR https://linktr.ee/l_lgde
China-Focused Consultant @SentinelOne | Nonresident Fellow @ACGlobalChina | Adjunct @Georgetown | Unprofessional Cook | ❤️💜💙
https://linktr.ee/dakotaindc
Securing every bit of your data
https://quarkslab.com
Immigrant. VP Security Intelligence @Forescout, Co-founder @RespectInSec. Board @vaultree, Cybersecurity Futurist, Researcher, Award-winning writer/producer. He/Him. Pussy in bio.
Substack - Ferguson.ink
Slava Ukraini 🇺🇦
software engineer. 💖✨
(go/aws/infra/platform) ✨
ex twilio. ex sendgrid. ✨
just a little cat girl in a big dog world. 🐱
denver, co ✨
my opinions are my own.
https://hannahapuan.github.io/
add me on WoW: Elestara-Turalyon (❄️ DK)