
Lateral movement getting blocked by traditional methods?
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
@werdhaihai.bsky.social
Adversary Simulation Consultant @SpecterOps https://github.com/werdhaihai

Lateral movement getting blocked by traditional methods?
@werdhaihai.bsky.social just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG

Finally putting out my research from this spring. "Imitune" coming in soon to support the POC
specterops.io/blog/2025/07...

Entra Connect sync accounts can be exploited to hijack device userCertificate properties, enabling device impersonation and conditional access bypass.
@hotnops.bsky.social explores cross-domain compromise tradecraft within the same tenant.
Read more: ghst.ly/3ISMGN9
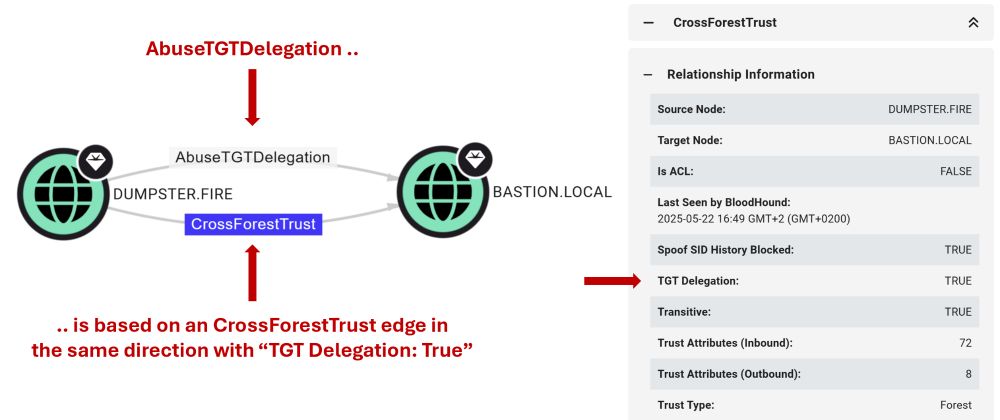
I publish two blog posts today! 📝🐫
First dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06...
Second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06...
Hope you enjoy the read 🥳

Think NTLM relay is a solved problem? Think again.
Relay attacks are more complicated than many people realize. Check out this deep dive from Elad Shamir on NTLM relay attacks & the new edges we recently added to BloodHound. ghst.ly/4lv3E31

Nothing new, but formalized some operator notes on Entra ID/Azure tradecraft I've found to be exceptionally useful on ops. Overlooked this myself for quite some time and thought others in the same boat might find it worth a read! 📖
medium.com/specter-ops-...

Super excited to be speaking at SO‑CON 2025 on March 31st with my coworker Lance Cain. We’re diving into an example attack path from real-life red team assessments by Lance Cain, Dan Mayer, myself, and the entire @specterops.bsky.social crew. specterops.io/so-con/ #SOCON2025 #redteam
22.03.2025 17:38 — 👍 4 🔁 1 💬 0 📌 0
The Mythic family continues to grow! Another cool Windows agent written in C that already has COFF execution! Be sure to check it out and their blog series on it c0rnbread.com/creating-myt...
x.com/0xC0rnbread/...
#SCCM forest discovery accounts can be decrypted—even those for untrusted forests. If the site server is a managed client, all creds can be decrypted via Administration Service API.
Check out our latest blog post from @unsignedsh0rt.bsky.social to learn more. ghst.ly/4buoISp

BIG NEWS: SpecterOps raises $75M Series B to strengthen identity security! Led by Insight Partners with Ansa Capital, M12, Ballistic Ventures, Decibel, and Cisco Investments. ghst.ly/seriesb
#IdentitySecurity #CyberSecurity
(1/6)

Many in the Mythic Community have asked for a way to standardize BOF/.NET execution within Mythic Agents. Today I'm releasing Forge, a new Mythic container to do just that: posts.specterops.io/forging-a-be...
We're starting off with default support for Apollo and Athena. Check it out! :)
I have done this 🤦
31.01.2025 02:11 — 👍 0 🔁 0 💬 0 📌 0
This post goes more into Entra Connect tradecraft and how partially synced objects can be hijacked for cross domain attacks.
posts.specterops.io/entra-connec...

What does the road to becoming a Specter look like? In his latest blog post, @subat0mik.bsky.social provides a high level overview of how we approach recruiting consultants, demystifying the process along the way from application review through interviews. ghst.ly/3PQeuSh
21.01.2025 17:47 — 👍 4 🔁 1 💬 1 📌 0Aight, who dcsyn'd today?
23.11.2024 05:42 — 👍 2 🔁 0 💬 1 📌 0
Following my prev tweet, my Kerberos MITM relay/forwarder is almost finished! It targets for example insecure DNS updates in AD, allowing DNS name forgery. It intercepts, relays, and forwards traffic, with the client unaware. Currently supporting smb->smb and smb->http (adcs)
20.11.2024 11:21 — 👍 36 🔁 14 💬 1 📌 0 16.11.2024 03:18 — 👍 4 🔁 0 💬 0 📌 0
16.11.2024 03:18 — 👍 4 🔁 0 💬 0 📌 0
Was doing some digging "What's New" in Server2025 learn.microsoft.com/en-us/window... specifically the changes to pre-2k machines. Oddvar and I had spoken previously about the changes being solid and demonstrated pre-created machines in ADUC could no longer be set with a default password.
15.11.2024 05:25 — 👍 10 🔁 5 💬 1 📌 0
SO-CON 2025 Call for Presenters Closes November 15
The CFP for #SOCON2025 closes TOMORROW!
We are accepting talks focused on identity-based security and Attack Paths. Submit yours today!
➡️ ghst.ly/cfp-socon25
top notch engineering
13.11.2024 20:23 — 👍 1 🔁 0 💬 0 📌 0
Python implementation of some remote modules from Seatbelt by @0xthirteen
github.com/0xthirteen/C...

README for this is great
github.com/0xHossam/Ker...
Anyone read Cory Doctorow's Red Team Blues yet? Curious to hear thoughts and opinions on it.
07.11.2024 16:05 — 👍 2 🔁 0 💬 0 📌 0