
Here's my bsidessf talk on using LLM's to self replicate and ransome the planet:
youtu.be/s4RKXTC8iuM
@insecurenature.bsky.social
Appsec and security hot takes.

Here's my bsidessf talk on using LLM's to self replicate and ransome the planet:
youtu.be/s4RKXTC8iuM
Bsides works really hard, and they're all volunteers, I didn't mean to tease them too hard here
27.04.2025 16:24 — 👍 2 🔁 0 💬 0 📌 0
🔥 You can now add TruffleHog to Burp Suite!
🌐 Install it directly from the BApp Store
🔍Scan web traffic for live, verified credentials—active & exploitable
Because secrets don’t just leak in code… 😬
🔗 trufflesecurity.com/blog/introdu...

The privacy concerns I have around the Eightsleep have kept me from buying one, the security concerns make me want to warn people about buying one:
trufflesecurity.com/blog/removin...

NEW: security researchers found what they say appears to be a backdoor into Eight Sleep beds, which could allow company engineers to SSH into any bed
in theory, they could see if you're home or not, if you're sleeping alone or with someone
in today's newsletter for @bloomberg.com

Agent Zuck takes you out to a stake dinner and offers to plug you into the oculus, which perfectly simulates the year 1999.
All you have to do is hand over the codes to Zion.

🐷 Under the Hood of TruffleHog!
⚡ Part 1 of 2: How Aho-Corasick + CPU optimizations deliver 11-17% faster scans with precomputed keyword matching. 🚀
👉 trufflesecurity.com/blog/under-t...

Forbes and Arstechnica ran a story on my research, neat! www.forbes.com/sites/daveyw...
16.01.2025 02:16 — 👍 4 🔁 0 💬 0 📌 0I wrote a blog about my shmoocon talk, check it out 👇
14.01.2025 04:35 — 👍 4 🔁 2 💬 0 📌 0I spoke at Shmoocon today and linked my Twitter and Blue Sky.
It led to:
+ 5 Twitter follows
+ 19 Blue Sky follows

Vigilante Justice on GitHub. 🦇🦸
Here's how to spray painting on other fraudster's GitHub Activity Graph.
trufflesecurity.com/blog/vigilan...

🚨 10% of SaaS platforms mishandle GitHub OAuth tokens, opening potential backdoors into corporate accounts. 😱
⚠️ Extends to Azure, Slack & more—increasing risk with poor token handling.
🛑 The issue isn’t OAuth; it’s how platforms secure tokens.
👉 trufflesecurity.com/blog/mishand...
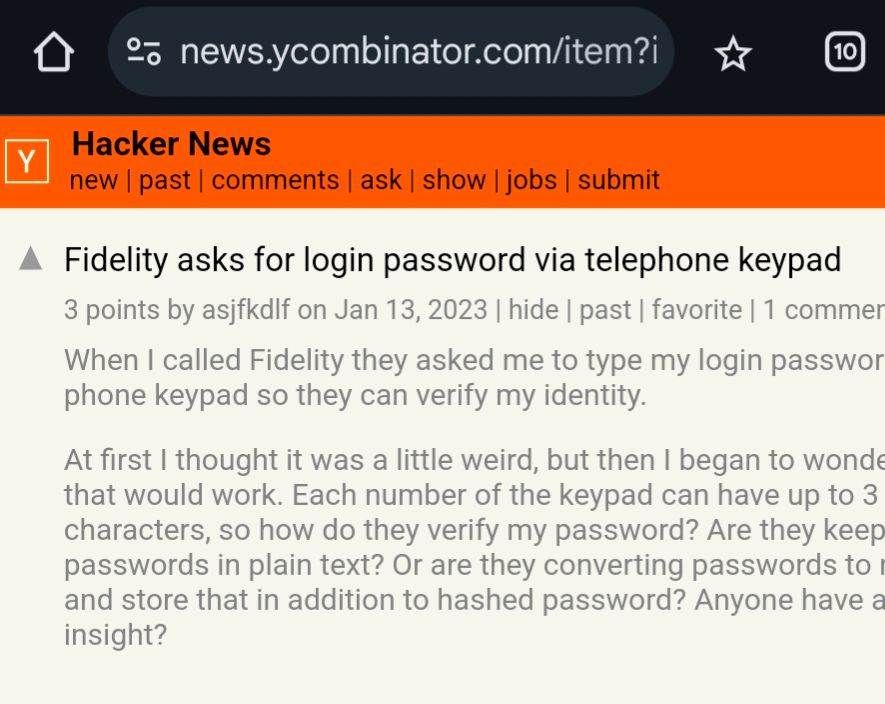
Hey Fidelity,
Now that CCP is literally in our phone networks-
Can you please stop making your customers rawdog their passwords over touch tone?
Thanks.
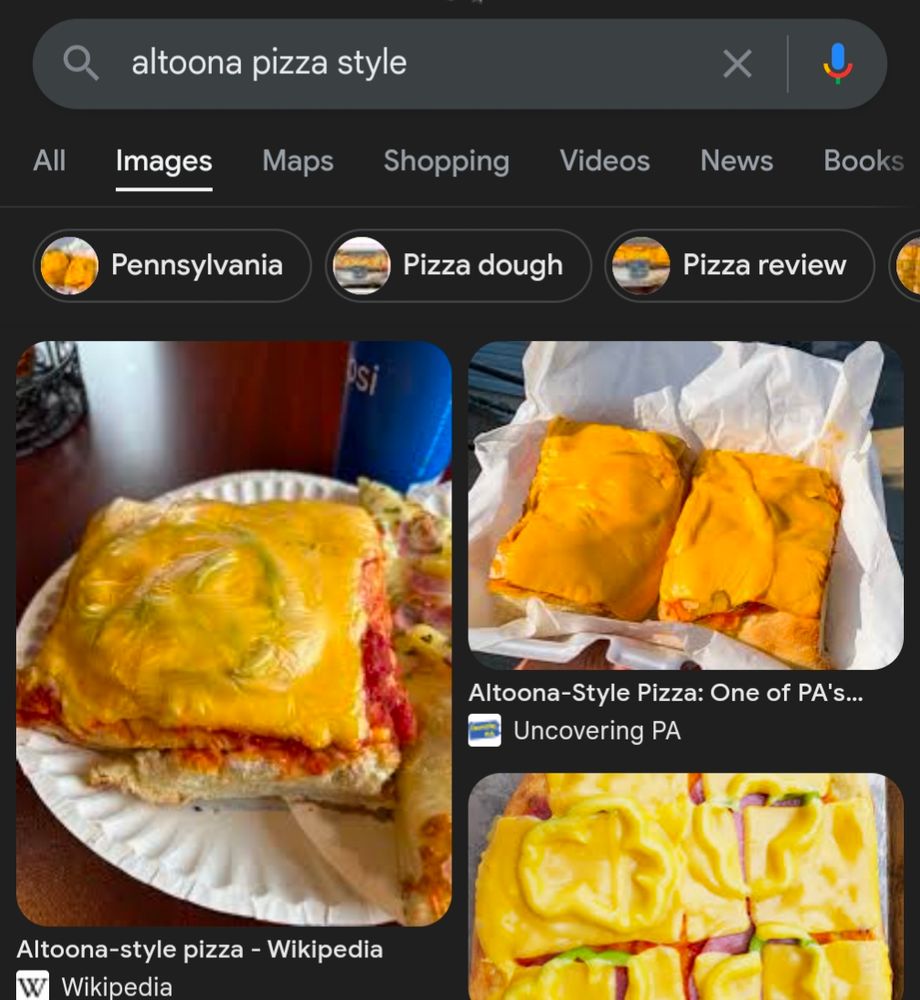
Look up "Altoona Pizza", I can't even
12.12.2024 02:56 — 👍 1 🔁 0 💬 0 📌 0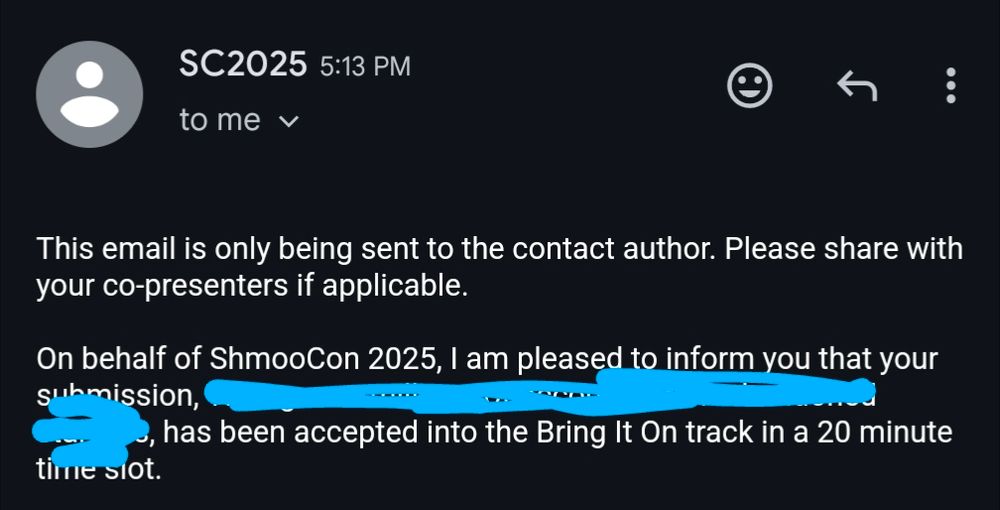
My Shmoocon talk got accepted!
I've never spoken at Shmoocon before, but I have been submitting every year for a while.
If you're wondering what it takes to get accepted at a conference the answer is a lot of rejection first.
Truffle Security is posting on Blue Sky now??
09.12.2024 17:40 — 👍 1 🔁 0 💬 0 📌 0I found an AWS key inside one of my household devices, does anyone want to guess which one?
07.12.2024 07:51 — 👍 1 🔁 0 💬 1 📌 0
It's no secret Android apps have a lot of passwords and API keys in them.
TruffleHog can now find them, fast: trufflesecurity.com/blog/crackin...
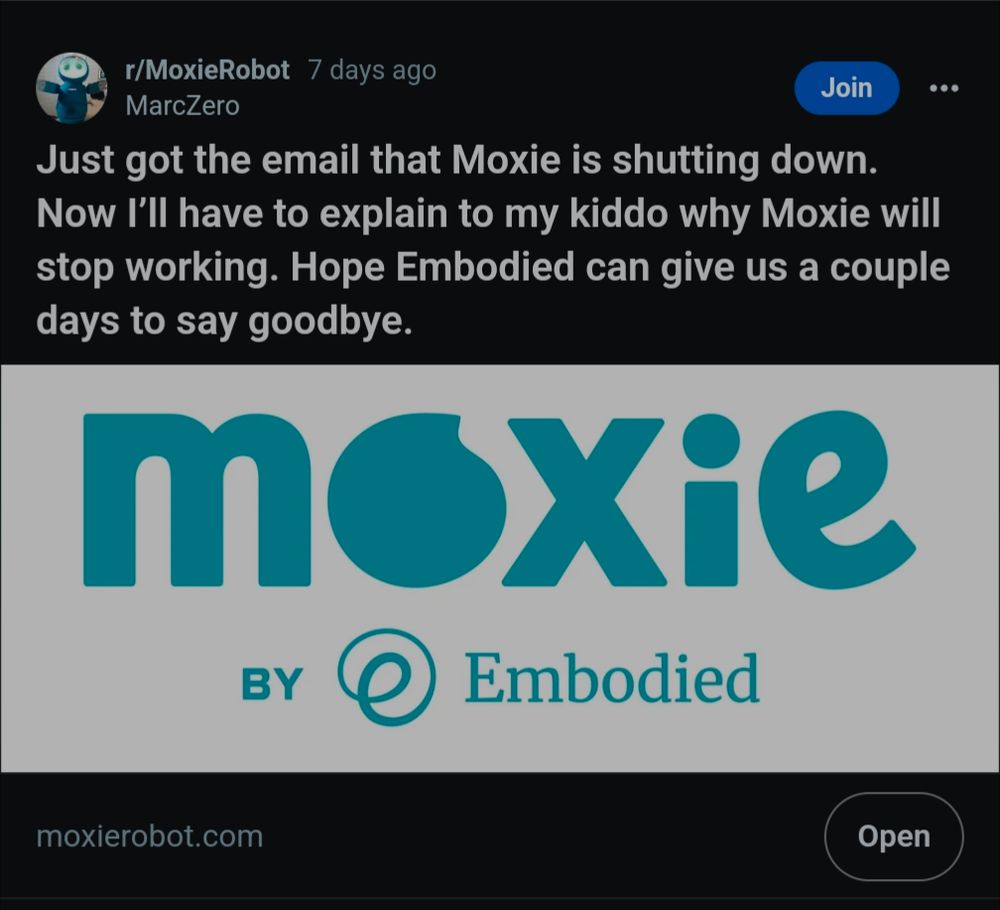
I'll pay $200 bucks for a moxie robot. Seriously.
03.12.2024 02:07 — 👍 0 🔁 0 💬 0 📌 0
Truffle Security sponsors security research, in case anyone is tired of the conference loop: trufflesecurity.com/blog/announc...
02.12.2024 21:29 — 👍 0 🔁 0 💬 0 📌 0
Technically you can satisfy data breach notification requirements by sending snail mail to those impacted, and never announcing publicly.
02.12.2024 20:25 — 👍 0 🔁 0 💬 0 📌 0
How will code gen will change the security landscape?
AI will write code containing vulnerabilities, and humans won't know the first thing about it.
Then they will actively push to not be held accountable to review and fix it.
So do people use this app?
19.11.2024 03:13 — 👍 5 🔁 0 💬 3 📌 0
Sometimes you find the shell, sometimes the shell finds you
05.07.2023 10:27 — 👍 0 🔁 0 💬 0 📌 0
Hacking on coffee
@twitchyliquid64.bsky.social is enjoying a coffee
14.05.2023 19:22 — 👍 1 🔁 0 💬 0 📌 0
A few years ago reports came out suggesting the NSA had hardware signing keys and used them to embed hardware level backdoors. Now, with MSI keys leaking, you can make your own https://nakedsecurity.sophos.com/2023/05/09/low-level-motherboard-security-keys-leaked-in-msi-breach-claim-researchers/
12.05.2023 20:12 — 👍 0 🔁 0 💬 0 📌 0Okay I'm posting my first.... What is this action? Sky? Am I skying?
08.05.2023 19:23 — 👍 1 🔁 0 💬 0 📌 0Omg is that why I got followers minutes after joining? I was wondering what the deal was...
05.05.2023 23:53 — 👍 5 🔁 0 💬 1 📌 0