
GitHub - OWASP/wrongsecrets: Vulnerable app with examples showing how to not use secrets
Vulnerable app with examples showing how to not use secrets - OWASP/wrongsecrets
We released version 1.11.2 of #OWASP #WrongSecrets: it's faster than ever, has now 55 challenges and a lot of fun! Check it out at github.com/OWASP/wrongs... or test it at www.wrongsecrets.com and don't forget to give the repo a 🌟 if you like it!
02.05.2025 10:33 — 👍 17 🔁 6 💬 1 📌 1

I just built a custom action to let you test for race conditions with a single click! No tab groups required, and it uses the cutting edge single-packet attack under the hood: gist.github.com/albinowax/10...
For more info check out portswigger.net/research/sma...
23.04.2025 14:31 — 👍 16 🔁 2 💬 0 📌 0

Ever heard of LLM poisoning? 🤔
Recently, Leif Dreizler joined Travis McPeak and William Bengtson on the @404security.bsky.social podcast to discuss how misinformation websites are intentionally spreading fake news to influence AI model responses.
🎧 Listen here: www.resourcely.io/podcast/deal...
04.04.2025 16:18 — 👍 3 🔁 1 💬 0 📌 0
I will for sure!
04.04.2025 17:11 — 👍 1 🔁 0 💬 0 📌 0
I will attend!
02.04.2025 18:18 — 👍 1 🔁 0 💬 1 📌 0

As a follow up to @maxenceschmitt.bsky.social's amazing #CSPT research, we've published a list of resources to help people interested in this class of vulnerabilities. Check it out today for video, tools, challenges and variety of publications!
blog.doyensec.com/2025/03/27/c...
#Doyensec #appsec
27.03.2025 16:46 — 👍 2 🔁 2 💬 0 📌 0

State of Threat Modeling (SOTM) 2024 Survey
Welcome to the first-ever State of Threat Modeling (SOTM) Survey!
What is the SOTM Survey?
The SOTM Survey is part of the research for the first community-driven State of Threat Modeling (SOTM) Repor...
The Threat Modeling Connect community are launching the first-ever community-driven State of Threat Modeling (SOTM) Report, led by @rewtd.bsky.social
and Dave Soldera, and we’d love your input!
docs.google.com/forms/d/e/1F...
The survey will take 15-20 minutes to complete.
#cybersec #infosec
14.03.2025 09:20 — 👍 21 🔁 15 💬 0 📌 0


OWASP Global AppSec EU 2025 Barcelona: full training schedule is out now!
Day 3 is packed with even more hands-on training sessions to enhance your AppSec expertise!
Register now:
owasp.glueup.com/eve...
#AppSecEU2025 #Cybersecurity #DevSecOps #SecureCoding #ThreatModeling #Infosec #Barcelona
24.03.2025 07:04 — 👍 3 🔁 1 💬 0 📌 0

Exciting news! The #OWASP Global #Appsec SF videos have arrived! 🎥 Get ready to boost your knowledge and skills by checking them out here: www.youtube.com/play...
21.03.2025 16:30 — 👍 3 🔁 1 💬 0 📌 0
SAML roulette: the hacker always wins
Introduction In this post, we’ll show precisely how to chain round-trip attacks and namespace confusion to achieve unauthenticated admin access on GitLab Enterprise by exploiting the ruby-saml library
You might have noticed that the recent SAML writeups omit some crucial details. In "SAML roulette: the hacker always wins", we share everything you need to know for a complete unauthenticated exploit on ruby-saml, using GitLab as a case-study.
portswigger.net/research/sam...
18.03.2025 14:57 — 👍 52 🔁 23 💬 0 📌 4
Slack Invite
There's now a ZAP Slack that's open to everyone. You can get an invite to it via zaproxy.org/slack/invite
24.02.2025 13:45 — 👍 9 🔁 6 💬 0 📌 0
AppSec Ezine
AppSec Ezine - 573rd pathonproject.com/zb/?3970e59b... #AppSec #Security 🎁
08.02.2025 11:31 — 👍 5 🔁 5 💬 0 📌 0

🤔 Based on issues that I have seen during recent assessments, I updated my code sharing project with a method related to JWT based tokens:
#appsec #appsecurity #jwt #web
🌍 URL:
github.com/righettod/co...
righettod.github.io/code-snippet...
09.02.2025 16:59 — 👍 1 🔁 1 💬 0 📌 0

Get ready for an eye-opening session with Kevin Hemmingsen, Director of Trust & Security at Bugcrowd as he explores lessons from bug bounty / offsec to help devs build more securely at the OWASP Security Summit!
OWASP Community Save 25% on tickets: http://www.eventbrit...
09.02.2025 21:40 — 👍 3 🔁 1 💬 0 📌 0
Practice on Portswigger Academy
06.02.2025 22:50 — 👍 1 🔁 0 💬 0 📌 0

GET /%0D%0ASet-Cookie: foo=bar
403 Forbidden
GET /%E4%BC%8D%E4%BC%8ASet-Cookie: foo=bar
200 OK
Set-Cookie: foo=bar
Discover blocklist bypasses via unicode overflows using the latest updates to ActiveScan++, Hackvertor & Shazzer! Thanks to Ryan Barnett and Neh Patel for sharing this technique.
portswigger.net/research/byp...
28.01.2025 14:01 — 👍 39 🔁 22 💬 0 📌 0

Sarah-Jane Madden is a keynote speaker at OWASP Global AppSec EU 2025
🎟️ Attention to those in App Sec, Cybersecurity, and Developers: take advantage of the early bird discount!
Don’t wait, register now!
owasp.glueup.com/eve...
#owaspglobalappseceu2025 #AI #threatmodeling #devsecops #infosec
29.01.2025 08:05 — 👍 5 🔁 1 💬 0 📌 0
I've just released HTTP Request Smuggler 2.17 which fixes a nasty Client-Side Desync false-negative. Big thanks to @t0xodile.com for reporting it! Hope you all find some nice CSDs in 2025 :)
07.01.2025 10:45 — 👍 34 🔁 5 💬 1 📌 1

🚨 Attention all developers and code enthusiasts! Get ready to elevate your skills with "Alice and Bob Learn Secure Coding." Secure your copy now and embark on a transformative learning experience.
shehackspurple.ca/bo...
31.12.2024 16:19 — 👍 9 🔁 3 💬 0 📌 0

Burp suite pro tips and tricks for hacking
Burp suite pro tips and tricks for hacking - Download as a PDF or view online for free
Somebody uploaded to SlideShare the slides of my talk at @northsec.bsky.social 2023 🌐
It’s the sequel of the first @burpsuite.bsky.social talk I ever gave, exactly 10 years before 🛠️
Enjoy these 50 slides of Burp tips 🎁🎅
23.12.2024 22:00 — 👍 38 🔁 18 💬 0 📌 0
Extended the starter with shy writers! 😀 If you're not on the list but write about web security, then feel free to reply with the article you're most proud of, and I will add you to the pack!
Make sure to resubscribe to not not miss on the amazing 🌐research!
go.bsky.app/9JXnB17
10.12.2024 22:29 — 👍 29 🔁 10 💬 9 📌 0

Screenshot of Burp's HTTP settings, where streaming URLs must be defined

Chunked response as seen in Repeater, with chunk metadata (their size) not stripped
Ever wondered why you NEVER see chunked responses in Burp? 🤔
The answer is simple, default settings hide them! 🫣
Go to "Settings > Network > HTTP > Streaming responses" to make them appear 🔍
20.12.2024 07:23 — 👍 20 🔁 6 💬 0 📌 2
Check out the tools I've been working on this year:
🔐 Hackvertor: Web app: hackvertor.co.uk
🔒 Hackvertor BApp: portswigger.net/bappstore/65...
⚡ Shazzer: shazzer.co.uk
🛠️ Recorder: Chrome extension: chromewebstore.google.com/detail/burp-...
🕵️ DOM Invader: portswigger.net/burp/documen...
20.12.2024 13:27 — 👍 16 🔁 4 💬 0 📌 0
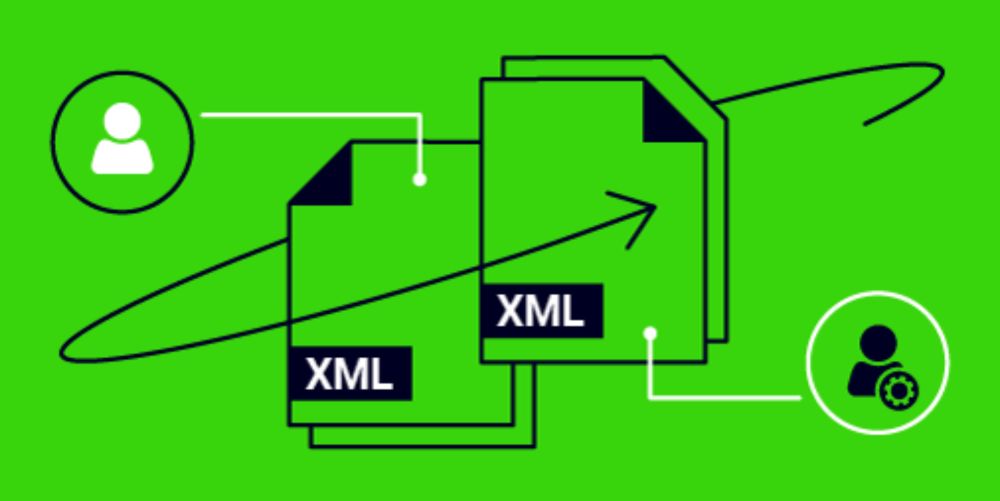
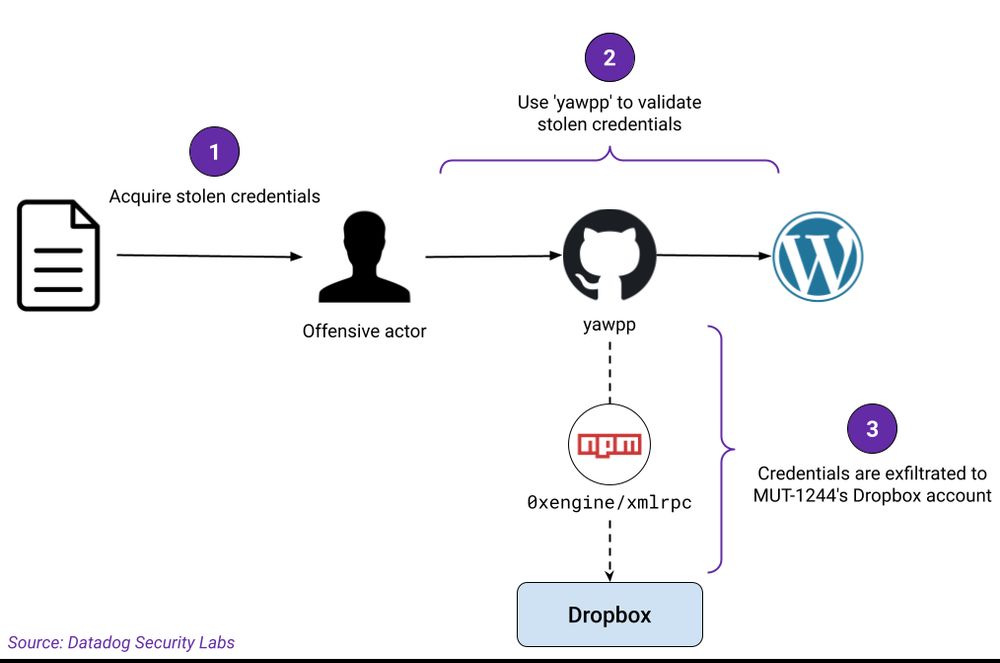
Overview of the attack flow
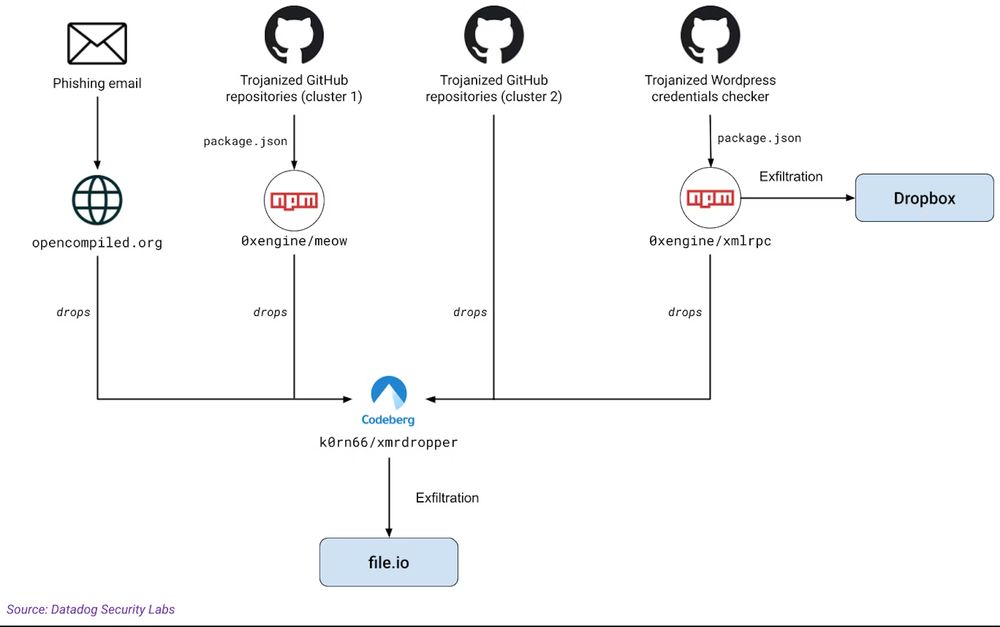
Overview of how a large number of credentials were leaked
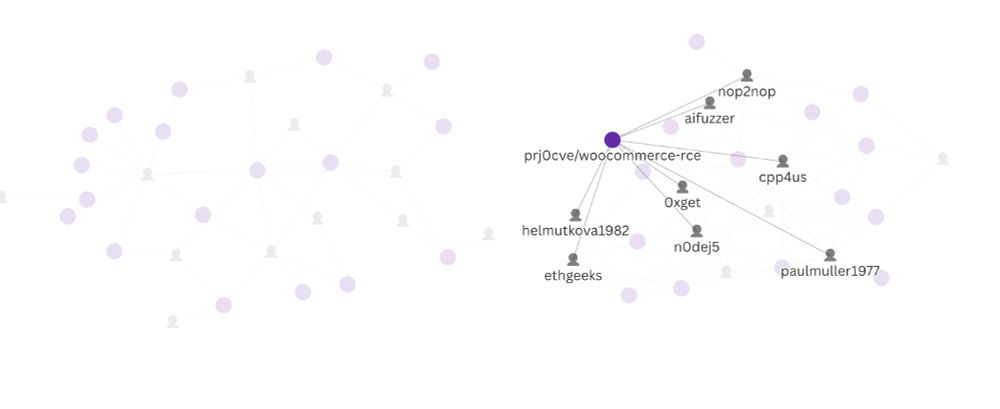
Clusters of fake GitHub profiles
Phishing e-mail
New research: We've been monitoring a threat actor publishing dozens of trojanized GitHub repositories targeting threat actors, leaking hundreds of thousands of credentials along the way
securitylabs.datadoghq.com/articles/mut...
16.12.2024 13:08 — 👍 22 🔁 13 💬 0 📌 0
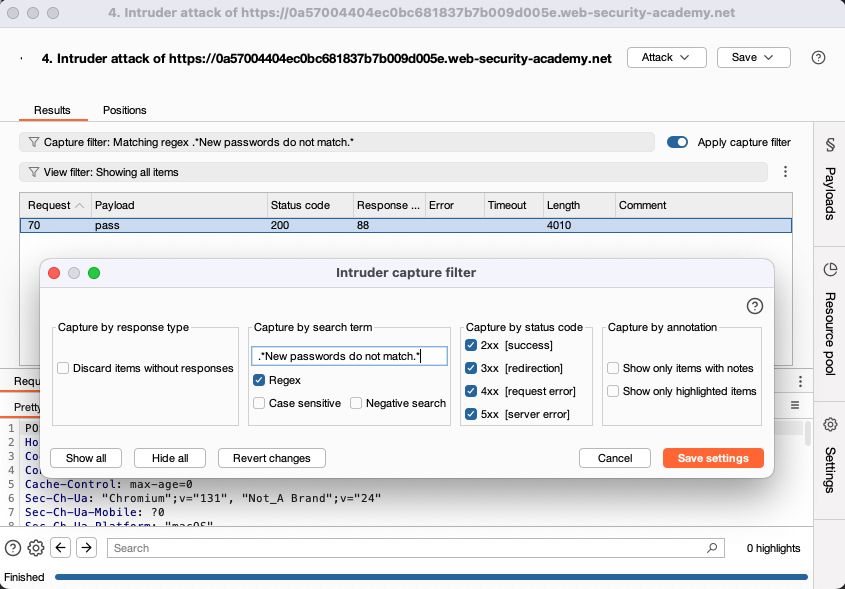
🤫 #sneakpeek #BurpSuite #Intruder
12.12.2024 13:15 — 👍 11 🔁 4 💬 2 📌 0

How does Snyk DCAIF Work under the hood? | Snyk
Read our technical deep-dive into how Snyk's DCAIF works. To start, with Snyk's Deep Code AI Fix, simply register for a Snyk account here, enable DeepCode AI Fix in your Snyk settings, and start reliably auto-fixing vulnerabilities in seconds.
Snyk SAST has a pretty clever trick to find and fix security vulnerabilities in your code
It applies a CodeReduce algorithm to "compress" your own program code before feeding it to an AI model and this results in improved by 20% success rate of security fixes:
13.12.2024 07:01 — 👍 6 🔁 1 💬 0 📌 0
Doyensec works at the intersection of software development and offensive engineering. We discover vulnerabilities others cannot, and help mitigate the risk.
Product Security @ Sage, Security Research & Speaker, OWASP Contributor, Hacker & Creator.
Personal blog: https://javan.de
I am a nerd that started a company almost 15 years ago. Secure Ideas is a security consulting firm focused on helping clients have the best penetration testing experience. I am also an IANS faculty member and currently an OWASP global board member.
open source | security | automation | founder smithy.security | maintainer opencre.org
Open Source SBOM Analysis Platform. Reduce Supply Chain Risk. #OWASP #SBOM #SaaSBOM #HBOM #VEX #SoftwareSupplyChain
https://dependencytrack.org/
Read our Security Labs blog: https://securitylabs.datadoghq.com
Subscribe to our monthly newsletter: https://securitylabs.datadoghq.com/newsletters/
Semgrep is a code scanning platform for finding first and third-party security vulnerabilities in your code base.
We are a leading provider of software and learning on web security. We make Burp Suite and the Web Security Academy.
#OpenSource Maintainer (@nodejs.org, @expressjs.bsky.social, Lodash, Yeoman...), #TC39 Delegate and #Maker | He/Him
Node.js Technical Steering Committee member
Socket is the #1 software supply chain security platform. Next-gen SCA + SBOM + 0-day prevention. LOVED BY DEVELOPERS.
https://socket.dev
I solve large software systems problems with programming language techniques.
Previously, I was the first frontend engineer on Google Calendar, and was a security engineer who worked on the industrial-strength Mad Libs undergirding Gmail.
Working on supply chain security for JS. LavaMoat and Endo contributor. meet.js Poland organizer. Node.js user since v0.8.
Addicted to teaching.
https://naugtur.pl
DivOps Engineer. OSS Maintainer: semantic-release, repository-settings, form8ion
Staff Software Engineer - Datadog APM
(he/him/his)
Dad
Royal Oak, MI
https://bryanenglish.com
Manager, security research @ Datadog | he/him | Chess lover | Blackhat speaker |
ex Sqreen.io, Shieldfy.io | my website: https://eslam.io
💻 Fullstack Developer
🏎️ @GoogleDevExpert in Web Perf
💚 @nuxt.com EcosystemTeam
👥 Ambassador @Storyblok, @algolia, @cloudinary, @supabase
Hacker / Farmer / Builder / Breaker
Prev: Code4rena, Okta, Auth0, GitHub, npm, ^lift, &yet, Symantec.
Pioneered BlindXSS & DVCS Pillaging
npm audit is my fault. More info: https://evilpacket.net
Founder of Tessl (and Snyk), reimagining software development for the AI era. Also a co-host of The AI Native Dev podcast, an angel investor, and an occasional speaker & writer.
Human who codes. Creator of @eslint.org. Author. Speaker. Advisor. Coach. GitHub Star.
Mastodon: https://fosstodon.org/@nzakas
Blog: https://humanwhocodes.com
Coaching: https://humanwhocodes.com/coaching


























