🚨 Alert on new credentials added to SPs.
🔥 Monitor changes to federated domains (federationConfiguration).
🕵🏼♂️ Hunt unusual Graph API calls to /domains, /credentials, and /federationConfiguration.
#DFIR #ThreatHunting #EntraID #CloudForensics #M365 #ThreatDetection
19.07.2025 04:18 — 👍 0 🔁 0 💬 0 📌 0
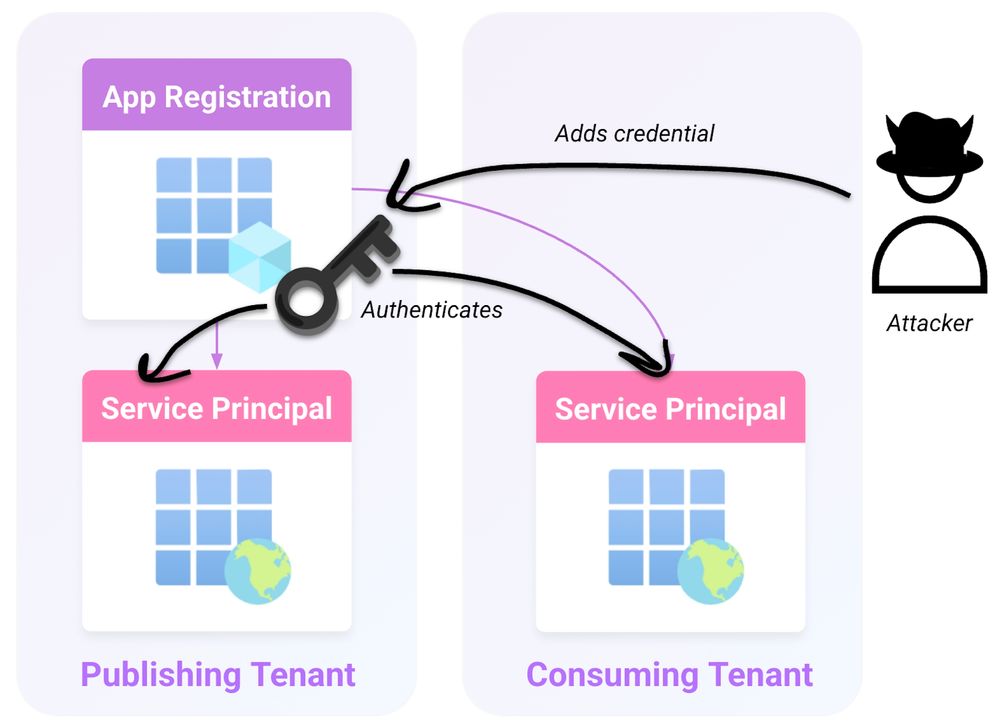
"I SPy" Entra ID Global Admin Escalation Technique
Datadog's Security Labs identified an abuse of Office 365 Exchange Online service principal (SP) allowing escalation to Global Admin. MSRC considers it "expected misconfiguration" so don't expect a fix.
🔗 securitylabs.datadoghq.com/articles/i-s...
19.07.2025 04:18 — 👍 0 🔁 0 💬 1 📌 0
Here are some recent TTPs for Scattered Spider as well.
www.crowdstrike.com/en-us/blog/c...
09.07.2025 06:14 — 👍 0 🔁 0 💬 0 📌 0
#ScatteredSpider are particularly good at #SocialEngineering their way via a third-party to other victims.
For clarity, #ScatteredSpider are considered the initial access group, #DragonForce #ransomware is the malware deployed once #ScatteredSpider are inside your network.
09.07.2025 06:07 — 👍 0 🔁 0 💬 0 📌 0
💡 On a side note, this is a great write up on #container #DFIR analysis if you're interested.
28.04.2025 10:46 — 👍 0 🔁 0 💬 0 📌 0
🕵🏼♂️ This malicious #container uses TENEO heartbeats to effectively earn credits. TENEO's ledger isn't exactly public so tracking the tokens isn't simple, there also doesn't appear to be a way to cash out...yet.
28.04.2025 10:46 — 👍 0 🔁 0 💬 1 📌 0
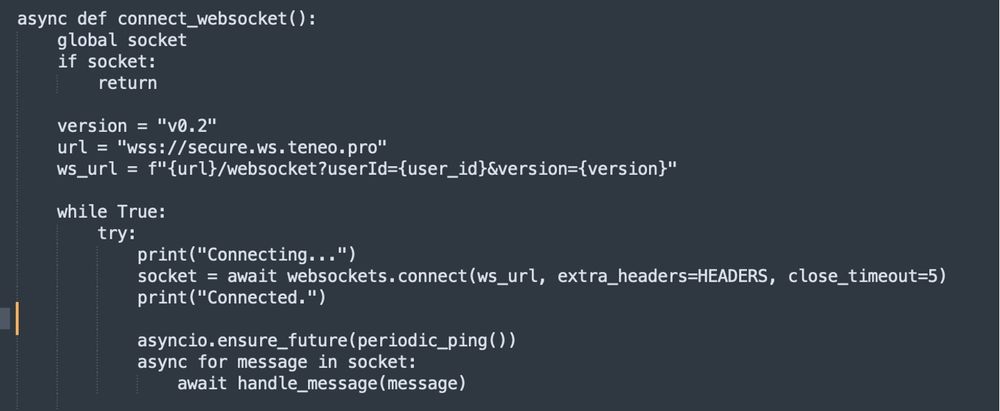
This is an interesting write up on a slightly different #Docker #container #malware attack from the Cado Security and Darktrace teams.
🔗 www.darktrace.com/blog/obfusca...
28.04.2025 10:46 — 👍 1 🔁 1 💬 1 📌 0

NSW man charged over ‘serious data breach’ that exposed thousands of sensitive court documents
More than 9,000 files downloaded from NSW JusticeLink system but authorities say no personal data compromised
Here's an update on the data breach of court documents from the NSW JusticeLink website.
tl;dr - it was an individual that was able to download +9k documents over two months, it doesn't appear they were leaked anywhere publicly.
www.theguardian.com/australia-ne...
23.04.2025 13:59 — 👍 0 🔁 0 💬 0 📌 0
🕵🏼♂️ Detect .LNK files making external connections, they are particularly easy to tune.
🕵🏼♂️ Detect mshta.exe running suspicious executables (i.e. cmd.exe).
Happy #ThreatHunting
🔗 blog.sekoia.io/detecting-mu...
23.04.2025 12:50 — 👍 0 🔁 0 💬 0 📌 0
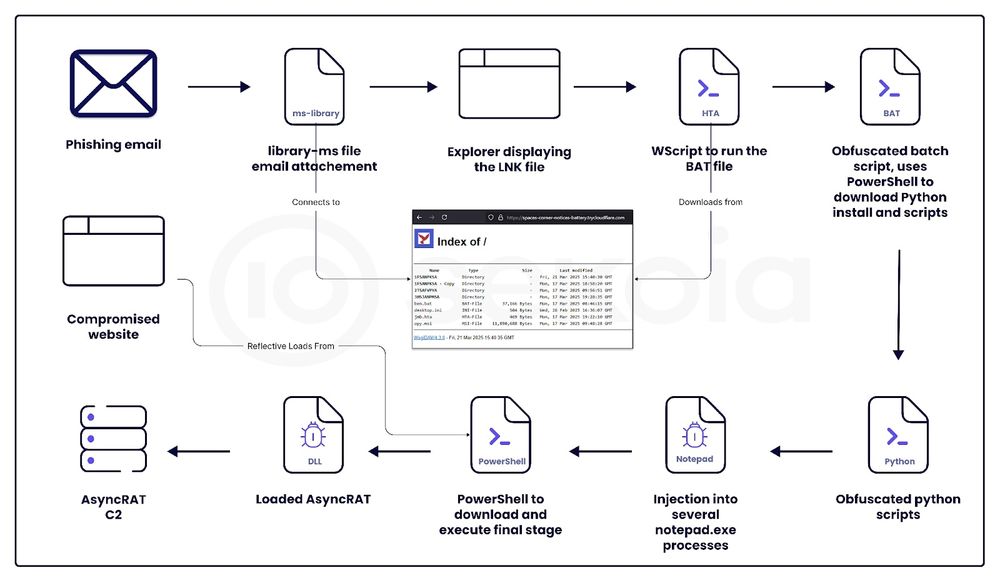
This is a really nice write up from Sekoia with lots of #ThreatDetection details, regardless of the #EDR you're using.
🔎 Of particular note, this attack is aided with a .LNK file pulling in a .HTA via a remote location.
23.04.2025 12:50 — 👍 0 🔁 0 💬 1 📌 0
signature-base/yara/vuln_erlang_otp_ssh_cve_2025_32433.yar at master · Neo23x0/signature-base
YARA signature and IOC database for my scanners and tools - Neo23x0/signature-base
- Make sure you go #ThreatHunting for compromised systems, prioritise public facing systems.
🕵🏼♂️ YARA signature: github.com/Neo23x0/sign...
ℹ️ Public disclosure: www.openwall.com/lists/oss-se...
⚙️ PoC Demo: x.com/Horizon3Atta...
19.04.2025 05:12 — 👍 0 🔁 0 💬 0 📌 0
🚨 New Critical RCE in Erlang/0TP SSH (CVSS 10)
- CVE-2025-32433
- Exploitable without authentication needed
- Exists in Erlang's built-in SSH server
- Commonly found in loT and Teleco gear
- Exploit model now in Metasploit and on GitHub
19.04.2025 05:12 — 👍 0 🔁 0 💬 1 📌 0
Google's Threat Intelligence Group published details last month of Russian #APTS targeting #Signal
➡️ Maliciously getting victims to scan QR codes
➡️ Maliciously cloning incoming messages with a Linked Device
➡️ Stealing the message database off a device
25.03.2025 23:39 — 👍 0 🔁 0 💬 0 📌 0
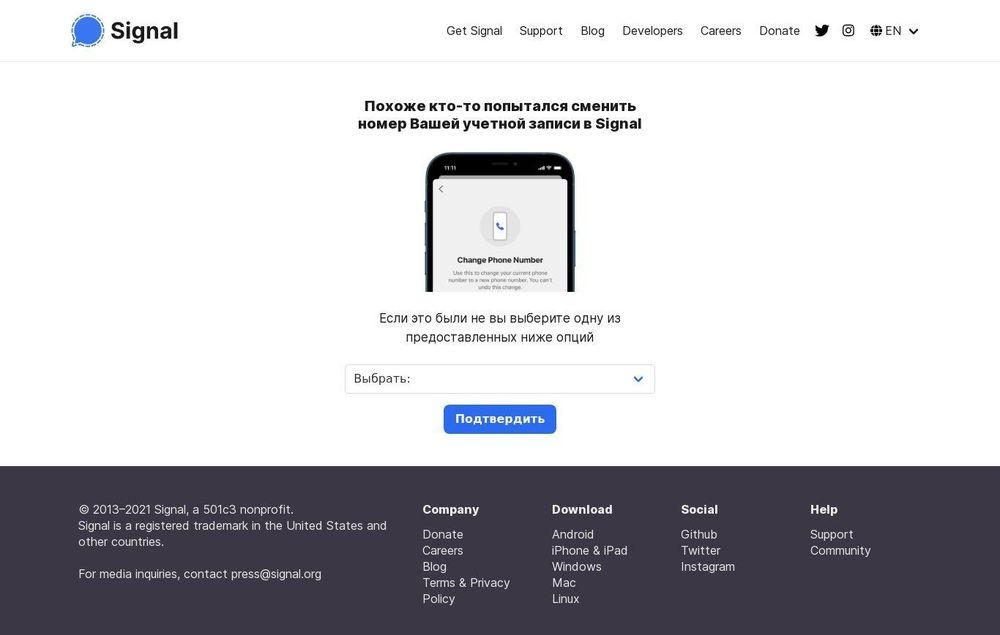
With all the talk about the use of #Signal by government officials in the US, it's worth remembering #ThreatActors will target what they need to steal the data they want.
🔗 cloud.google.com/blog/topics/...
25.03.2025 23:39 — 👍 0 🔁 0 💬 1 📌 0
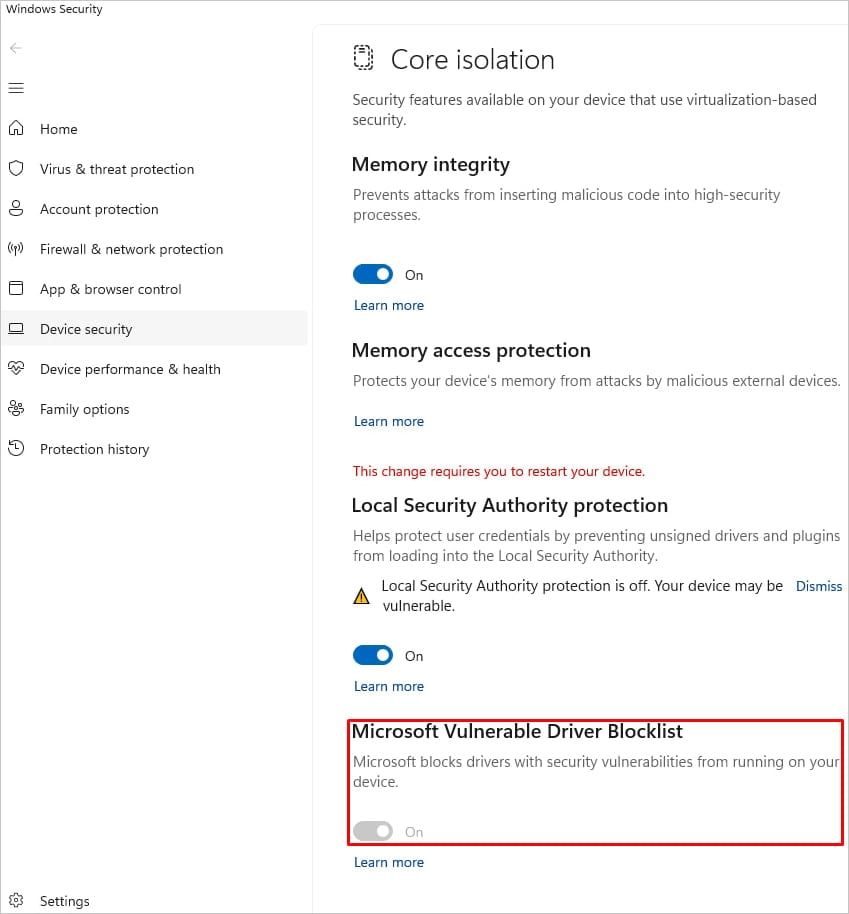
Image
#BYOVD attacks are slowly becoming more common for threat actors to escalate privilege and kill security tools.
Make sure you're #ThreatHunting for new Vulnerable Drivers!
#IncidentResponse #ransomware #ThreatDetection
02.03.2025 21:54 — 👍 0 🔁 0 💬 1 📌 0

Join me for SANS Institute #Perth Community Night today!
📋 Registration
Thurs, 13 Feb 2025
5:30pm – 6pm
🎤 Presentation
6pm – 7pm
Register Here: https://www.sans.org/mlp/community-night-perth-february-2025/
📍The Pan Pacific Perth Hotel, 207 Adelaide Terrace, Perth WA 6000
12.02.2025 23:00 — 👍 0 🔁 0 💬 0 📌 0
GitHub - MalBeacon/what-is-this-stealer: A repository of credential stealer formats
A repository of credential stealer formats . Contribute to MalBeacon/what-is-this-stealer development by creating an account on GitHub.
I just found this amazing repository of credential stealer system info files by #MalBeacon, along with #YARA sigs for them.
Useful to ID a cred stealer or going #ThreatHunting.
github.com/MalBeacon/wh... #threatintel #infosec #malware #DFIR
15.01.2025 22:42 — 👍 0 🔁 0 💬 0 📌 0
Remember this is just one botnet of #PlugX it's still used in the wild by many other threat actor groups.
For you #DFIR folks, ensure you know how to go #ThreatHunting for DLL-Side Loading to find #PlugX in your network.
15.01.2025 21:15 — 👍 0 🔁 0 💬 0 📌 0

Abusing AWS Native Services: Ransomware Encrypting S3 Buckets with SSE-C
The Halcyon RISE Team has identified a unique ransomware technique that encrypts Amazon S3 buckets with no known method to recover unless a ransom is paid...
#Ransomware threat actors are increasingly abusing #AWS Server-Side Encryption (SSE-C) to encrypt S3 buckets. Most recently a TA known as #Codefinger is using this technique.
🕵 Monitoring S3 & encryption activity via CloudTrail & GuardDuty.
www.halcyon.ai/blog/abusing...
#CloudForensics #FOR509
14.01.2025 03:46 — 👍 1 🔁 0 💬 0 📌 0
Geopolitics, Russia, China, Cyber
Chairman @silverado.org
Author of WorldOnTheBrink.com
Host GeopoliticsDecanted.com podcast
Founder Alperovitch Institute for Cybersecurity Studies at Johns Hopkins SAIS
Co-Founder CrowdStrike
@DAlperovitch elsewhere
Advances cybersecurity. Grows tech businesses. Fights malware.
CISO at Axonius. Faculty Fellow at SANS Institute. Creator of REMnux.
https://zeltser.com
The Wireshark Foundation is a non-profit organization helping as many people as possible understand their networks as much as possible.
https://wiresharkfoundation.org
DFIR | Malware Hunter | @Cryptolaemus1
Threat researcher @ Proofpoint. Formerly IBM X-Force, CMU, US Government, US Navy. Views are my own.
Hacker & CEO @SocialProofSec security awareness/social engineering training, videos, talks | 3X @DEFCON🥈 | Chair @WISPorg | @CISAgov Technical Advisory Council under Director Jen Easterly
Security editor, TechCrunch
Signal: zackwhittaker.1337
My stories: techcrunch.com/author/zack-whittaker
My weekly cyber newsletter: this.weekinsecurity.com
CTO @TrustedSec.com | Former Optiv/SecureWorks/Accuvant Labs/Redspin | Race cars
All things networking & security.
Sharer of knowledge, purveyor of puns, curator of amusement. Wielder of snark & sparkly bats.
@amyengineer@infosec.exchange
@amyengineer on the Twitters
Principal Identity Security Researcher @Microsoft. Ex-Secureworks (PhD, MSc, MEng, CITP, CCSK).
And yes, opinions are my own ;)
security engineer @OpenAI
@volatilityfoundation.org Core Dev | Art of Memory Forensics co-author | DFIR trainer and enthusiast | Director of Adversary Tactics @huntress.com
Our mission is to make the Internet more secure by bringing to light vulnerabilities, malicious activity and emerging threats. Join our Alliance!
https://shadowserver.org/partner
Frontline Intelligence with #AdvancedPractices 🦅 @Google Threat Intel | views are my own
Advanced Practices at Google Cloud’s Mandiant
Volatility Core developer, Dir. of Research Volexity, LSU Cyber
DFIR Analyst
Blog: https://dfirdiva.com/
Free & Affordable Training (DFIR, OSINT, Cybersecurity): https://training.dfirdiva.com/
Community Events: https://events.dfirdiva.com/
Curated List of Discounts: https://training.dfirdiva.com/current-discounts
DFIR and Adversary Simulation | DFIR @ ProtonMail
🤓 Digital forensics nerd.
🌹 Mobile forensics is my passion.
💡 Opinions are mine and subject to change.
🎙️ Co-host of The Digital Forensics Now Podcast
👤 He/Him
🔗 linqapp.com/abrignoni













