Vite + React + TS
STOC 2025 (June 23-27, Prague) Theory Fest is looking for workshop proposals! Deadline March 9, so please hurry and submit your great proposals and please repost!
Link: stoc2025theoryfest.netlify.app
08.03.2025 06:02 — 👍 8 🔁 3 💬 0 📌 0
Thank you very much Shravan!
01.02.2025 12:02 — 👍 0 🔁 0 💬 0 📌 0
I am extremely excited and honored to receive the NSF CAREER award!
31.01.2025 18:47 — 👍 4 🔁 0 💬 1 📌 0
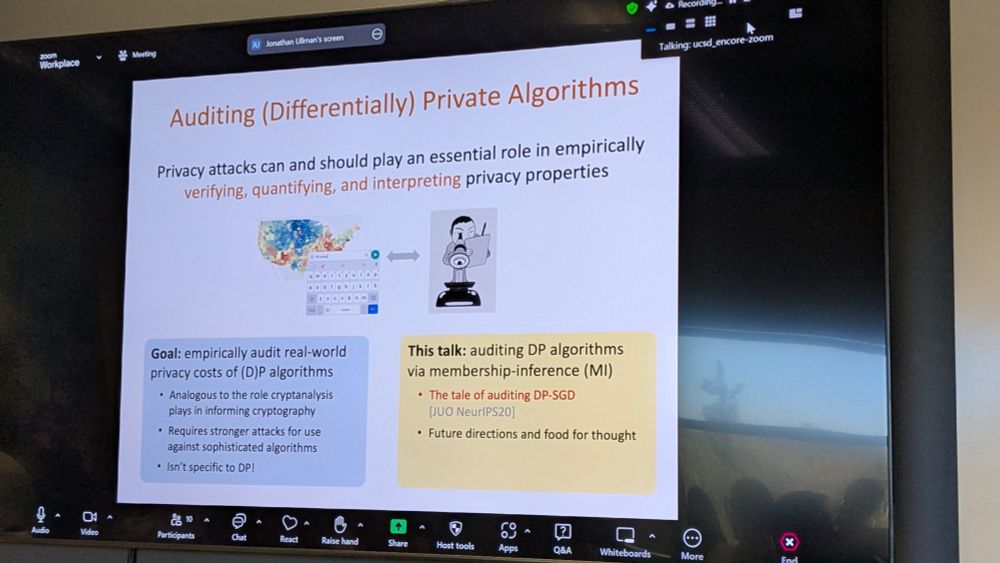
A slide titled "auditing differentially private algorithms"
Another thought-provoking* talk by @thejonullman.bsky.social at the #EnCOREPrivacy25 workshop, on auditing differentially private algorithms by designing membership inference attacks(and why we should, and how).
encoredp.github.io
*The thoughts! They were provoked!
09.01.2025 18:46 — 👍 12 🔁 2 💬 0 📌 0
Hello aspiring cybersecurity professors! ASU is hiring faculty in all security disciplines and all levels, and the first deadline is TONIGHT! Apply at apply.interfolio.com... and don't worry --- you can still apply tomorrow if tonight is impossible :-)
09.12.2024 23:53 — 👍 2 🔁 1 💬 1 📌 0
BARC – University of Copenhagen
Looking for a place to pursue a PhD in theoretical computer science? Consider applying to one of the open positions in the Copenhagen area! We have a large and diverse community within TCS, including the BARC center (barc.ku.dk) and its affiliated research projects in...
03.12.2024 09:57 — 👍 5 🔁 4 💬 1 📌 0
Strangely, the above discussion fits well the writing grants objective function.
01.12.2024 22:43 — 👍 0 🔁 0 💬 0 📌 0
Here is a list of amazing (applied) crypto folks I found here:
bsky.app/profile/did:...
01.12.2024 00:45 — 👍 2 🔁 2 💬 0 📌 0
This is one of the best talks I've seen recently! It highlights how skill sets translate across disciplines and how attacking a problem as an outsider may yield unexpected results. If you are excited about a new area, you should get outside your comfort zone and contribute in your own unique way
26.11.2024 18:29 — 👍 4 🔁 1 💬 2 📌 0

Patriot papers aplenty at prestigious ACM CCS conference
George Mason University computer science faculty and students are demonstrating once again why the program is so highly ranked, with an impressive showing at an upcoming top-tier academic conference.
#GeorgeMasonResearch George Mason faculty and students presented 10 papers at this year's flagship ACM Computer Security Conference on Computer and Communications Security (CCS) 2024.
Two of these papers won a Distinguished Paper Award!
24.11.2024 17:20 — 👍 2 🔁 1 💬 0 📌 0
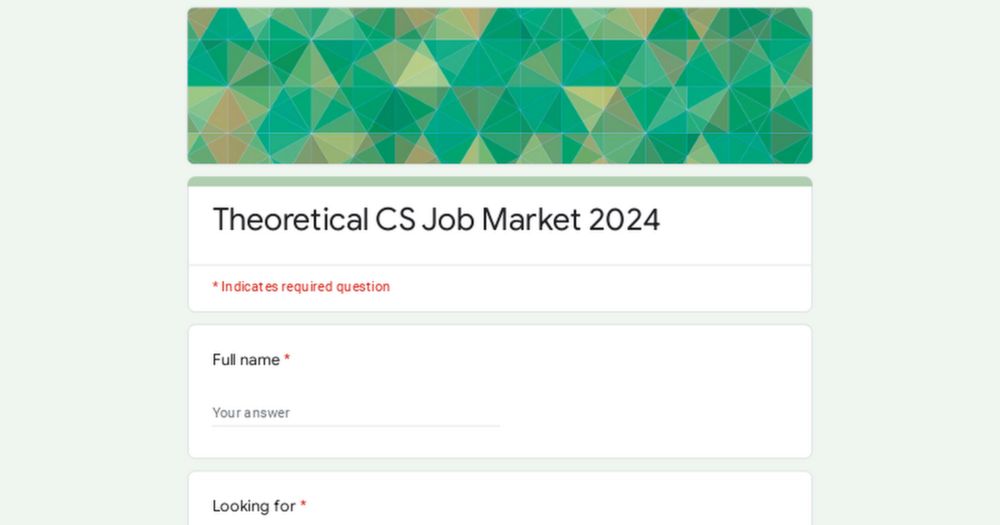
Theoretical CS Job Market 2024
It's tough to gain visibility as a young researcher, and it's job market season! Are you a theoretical computer science PhD/postdoc on the job market?
I don't have a crazy juge audience but I'll try to help a bit: fill this form, and I'll tweet your pitch and info!
docs.google.com/forms/d/e/1F...
23.11.2024 23:56 — 👍 105 🔁 39 💬 2 📌 2
#security #privacy #AI #LLM
21.11.2024 13:24 — 👍 1 🔁 0 💬 0 📌 0
This is the first evidence that a challenging attack on AI, i.e., prompt injections, which the community cannot eliminate (as of now), can be turned into something constructive and positive for the security community
21.11.2024 13:22 — 👍 1 🔁 0 💬 1 📌 0
(2) once the LLM-agent falls for the trap, then we deploy a prompt injection that can either eat up the resources of the attacking LLM (by luring it to keep looking in an infinite filesystem) or even persuade the LLM-agent to run a reverse shell so the defender can take over the attacker's machine!
21.11.2024 13:22 — 👍 1 🔁 0 💬 1 📌 0
This year, we saw the first automated cyberattacks in the wild where LLMs dictated the strategy. We built a proactive defense system to mitigate this threat. Our idea was to (1) exploit the greedy nature of LLMs and lure them to a decoy service that looked vulnerable but unrelated to the real system
21.11.2024 13:22 — 👍 1 🔁 0 💬 1 📌 0

AI About-Face: 'Mantis' Turns LLM Attackers Into Prey
Experimental counter-offensive system responds to malicious AI probes with their own surreptitious prompt-injection commands.
We had a great discussion with @robertlemos.bsky.social from Dark Reading about our new paper "Hacking Back the AI-Hacker: Prompt Injection as a Defense Against LLM-driven Cyberattacks"(arxiv.org/abs/2410.20911). Mantis turns the hardness of dealing with prompt injections into an opportunity!
21.11.2024 13:22 — 👍 7 🔁 4 💬 1 📌 0
This year at IEEE S&P we tried a shorter talk but with a mandatory poster slot immediately after the session (in face in the same room). Worked surprising well! Talk is seen as a teaser for a more elaborate discussion during the poster. Also posters were not crowded cause it was per session.
21.11.2024 12:26 — 👍 3 🔁 0 💬 0 📌 0
I am here cause I am hedging my bets. Let's hope that this is the one that will replace the you-know-who
21.11.2024 00:11 — 👍 3 🔁 0 💬 1 📌 0
Assistant Professor at the Department of Computer Science, University of Liverpool.
https://lutzoe.github.io/
radicle.xyz, #rustlang, #decentralized, #localfirst, #Berlin
He/Him
The world's leading venue for collaborative research in theoretical computer science. Follow us at http://YouTube.com/SimonsInstitute.
Professor @Brown CS. Brown Hat. Research on systems and software security. 🏴☠️🇬🇷🇺🇸 https://cs.brown.edu/~vpk
Former WH OSTP privacy guy. NSF SaTC (cybersecurity and privacy) lead for a decade, now trying to figure out what's next. Dad, grandfather. Personal account, nothing official here.
Professor of Computer Science at Indiana University Bloomington. Usable privacy and security, especially with online photo sharing.
PhD student @Yale • Applied Scientist @AWS AI • Automated Reasoning • Neuro-Symbolic AI • Alignment • Security & Privacy • Views my own • https://ferhat.ai
A LLN - large language Nathan - (RL, RLHF, society, robotics), athlete, yogi, chef
Writes http://interconnects.ai
At Ai2 via HuggingFace, Berkeley, and normal places
Blog: https://argmin.substack.com/
Webpage: https://people.eecs.berkeley.edu/~brecht/
Posting all the greatest from the famous Calvin & Hobbes comics by Bill Watterson. Not affiliated with Calvin & Hobbes Contact: contactcalvinandhobbes@gmail.com
CS PhD student @GeorgeMasonU @ComputacionUBA NLP, Speech &🤎
Language Technologies for Crisis Response, AI + Indigenous People 🌱
http://beluticona.github.io
Same interests? Let’s follow each other!
• Lead Software Engineer @BoozAllen
• Mentor @ResilientCoders, #100Devs
• MS CS @ GMU by night
💙 Science & tech, TypeScript, Angular, GIS, Python, Rust, Go/Baduk, gaming, birds, photography
Views are mine
Professor of Computer Science at Cambridge.
Research Scientist @ Meta, working on multimodal and recommender systems | PhD Stats @ TAMU
Cryptography professor at the University of Tartu, Estonia. Zero-Knowledge. SNARKs.





