I believe likes are a lot more general than “train the algorithm to show me this”
Likes can show support, be used to save posts, and even generate vitality of other user content
But it would be nice to toggle th capability to map them to the same I think
05.08.2025 01:00 — 👍 0 🔁 0 💬 0 📌 0
A screenshot highlighting the “show more like this” button
all in an honest day’s work 🥶
04.08.2025 18:54 — 👍 3 🔁 0 💬 1 📌 0
The candidate rightly pushed back on the request, and rather than my organization view it as extortion its seen as an unwilling candidate.
I am not sure I’m ready to be in the meat shield of management. That's wild 😭😵💫
04.08.2025 18:38 — 👍 0 🔁 0 💬 0 📌 0
The geniuses at my organization decided a candidate’s willingness to share slides after a discussion is an indicator of their teamwork aptitude.
For this candidate, the slides included IP from their personal business, for which we are a (bigger competitor).
04.08.2025 18:38 — 👍 0 🔁 0 💬 1 📌 0
No praying mantis were harmed in the making of this video
Poor lady probably has PTSD now watching a plant destroyed with a column of fire sounding like a jet engine
04.08.2025 04:08 — 👍 0 🔁 0 💬 0 📌 0
It is once again time for hacker summer camp. Headed to #BlackhatUSA tomorrow 😎
03.08.2025 03:28 — 👍 0 🔁 0 💬 0 📌 0
Above average concert recording quality 🤣
02.08.2025 16:06 — 👍 1 🔁 0 💬 0 📌 0
mamdanitimes.com
30.07.2025 15:31 — 👍 0 🔁 0 💬 0 📌 0
Really interesting, poked around a bit. Redacted registrations in Iceland, hosting across US AWS and Cloudflare… some strange AI scraping related domains all registered in the last week.
Hmm. Can't make sense of some of the related file IOCs but uh yeah safe to say, user beware… up to no good!
29.07.2025 02:46 — 👍 0 🔁 0 💬 0 📌 0
This is such a good reply 😤✊
25.07.2025 06:21 — 👍 1 🔁 0 💬 0 📌 0
that perversion isn't welcome here 🇬🇧🇳🇿🇦🇺
jk 🤣
24.07.2025 17:26 — 👍 1 🔁 0 💬 0 📌 0
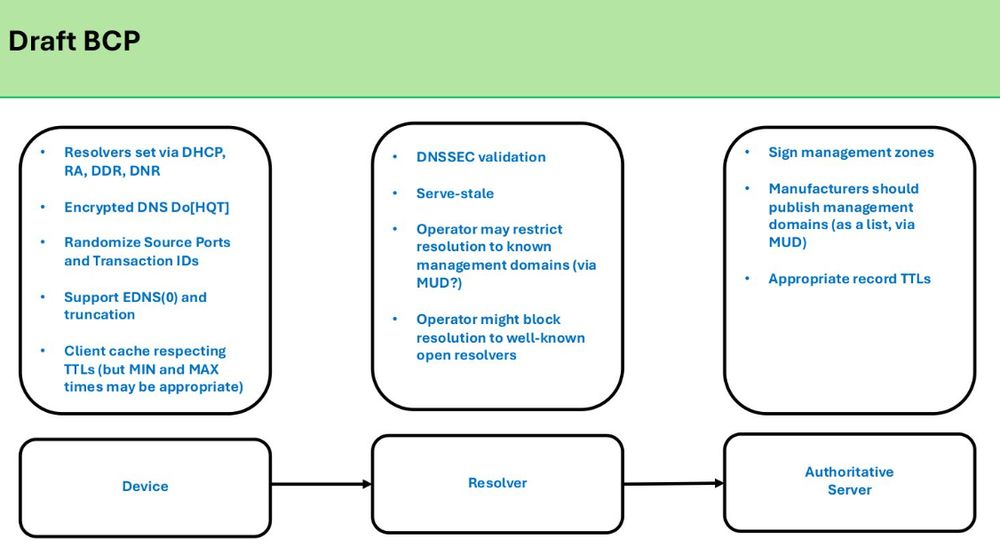
best current practice slide citing main pillars of device, resolver, auth server
There's a draft best current practice to provide more comprehensive controls to protect IOT devices.
24.07.2025 11:05 — 👍 0 🔁 0 💬 0 📌 0
The question asker cites DOT/H lack of support as a privacy problem may actually be a feature. The device makers likely don't believe these devices have a right to privacy in the same way user data does
Even forcing these devices to use DOT, the device class can be inferred by packet size
24.07.2025 11:05 — 👍 0 🔁 0 💬 1 📌 0
First question: what type of devices were being looked at in experiments? From smart plugs to smart TVs (low to high cost)
Some run an off the shelf embedded linux, so the guidance for a laptop would likely follow
For a really small and specific device there's a restricted DNS implementation
24.07.2025 11:05 — 👍 0 🔁 0 💬 1 📌 0
Lacking EDNS0 capabilities, limited IPv6 DNS64 capabilities etc
These are significant findings but were unable to find specific governing bodies in relation to IOT and protecting them based on DNS capabilities
24.07.2025 11:05 — 👍 0 🔁 0 💬 1 📌 0
The researchers changed the response sizes, expected query responses, set abnormally large TTLs, and fingerprint devices to 98% accuracy just based off startup behavior of what domains they query
The devices don't honor any caching, despite giving a #DNS server in DHCP not honoring them
24.07.2025 11:05 — 👍 0 🔁 0 💬 1 📌 0
If an attacker has access to a resolver where replies can be crafted, and what vulnerabilities can be identified via DNS queries it is seen that there aren't many supports for security considerations: ID randomization, source port randomization, support for DOT/Q
24.07.2025 11:05 — 👍 0 🔁 0 💬 1 📌 0
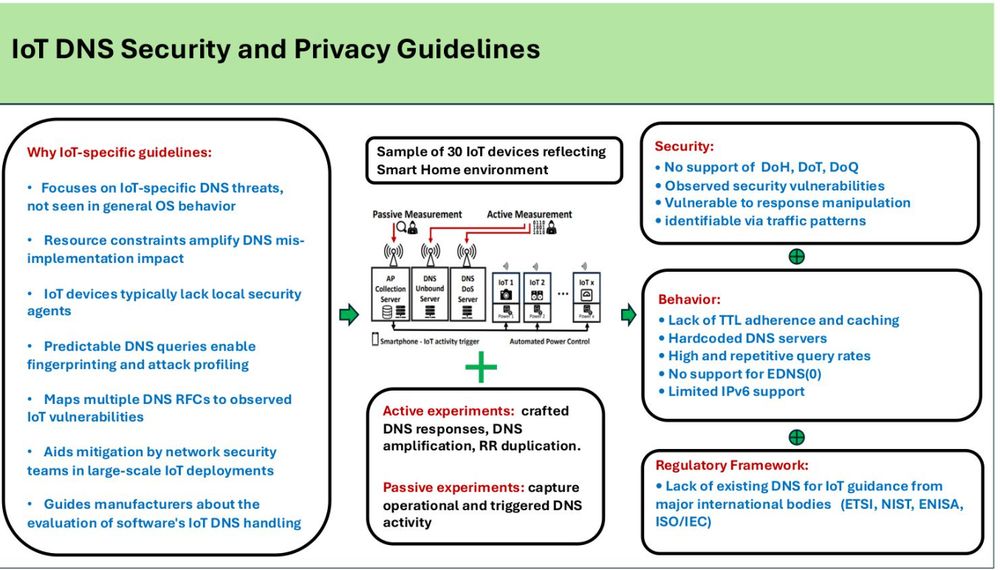
a slide showing the guidelines in the realms of behavior, regulatory framework, security, and why they are needed
IOT devices have quite predictable DNS queries which leads them to be prone to targeted attacks. Guides to manufacturers that are looking for implementation assistance this may reduce nation state ORB-like capabilities as well as removing amplification and redirection attacks
24.07.2025 11:05 — 👍 0 🔁 0 💬 1 📌 0

slide title: iot DNS security and privacy guidelines
Does #IOT need #DNS guidelines for #cybersecurity and #privacy?
24.07.2025 11:05 — 👍 1 🔁 0 💬 1 📌 0
vocal chip erasure
24.07.2025 09:53 — 👍 1 🔁 0 💬 1 📌 0
Getting to the end of my #IETF123 Madrid experience, second to last day. These early afternoon WG discussions revolve around #IOT. One of my friends is presenting today, which I'm looking forward to today!
#technology #DNS #standards #cybersecurity #ProtectiveDNS so let's see what it's all about...
24.07.2025 09:48 — 👍 0 🔁 0 💬 1 📌 0
I ended up speaking up regarding my organization and my customers. If you listen to the recording you may find me near the end 😎
24.07.2025 09:28 — 👍 0 🔁 0 💬 0 📌 0
There are a lot of downstream benefits of using TCP instead of UDP in not participating in amplification attacks etc and others if UDP
24.07.2025 09:26 — 👍 0 🔁 0 💬 1 📌 0
If the providers did some work on shared credential discovery with one another perhaps this a way to enforce group adoption
Flashback: DNSSEC adoption is so low because the business case is hard to make (higher costs lower benefit) which ADOT/ADOQ may fall into the same pitfall
24.07.2025 09:26 — 👍 0 🔁 0 💬 1 📌 0
Let's Encrypt mention that an outsized impact of the top 10 authoritative resolvers (Cloudflare and others) about getting it supported as LE will be able to enforce encrypted transport if the domain is know to be hosted on a nameserver provider that supports DOT
Discoverability mechanism... hmm
24.07.2025 09:26 — 👍 0 🔁 0 💬 1 📌 0
PCH are actively looking at this, and are offering and authoritative DOT service. Clients are requesting a timeline for it, they are currently evaluating measurements on capabilities from a performance perspective. Tips between implementers to mitigate as much as possible need to be prioritized
24.07.2025 09:10 — 👍 0 🔁 0 💬 1 📌 0
There is more appetite for collaboration with trusted partners for experiments which may lead to public service deployment over time
Prior to enabling, many groups experimenting need to deploy their numbers
24.07.2025 09:10 — 👍 0 🔁 0 💬 1 📌 0
Chicken and egg problem: businesses won't prioritize developing capabilities of DOT as adoption is low, and as a result the adoption is low as most commercial organizations don't support it
24.07.2025 09:10 — 👍 0 🔁 0 💬 1 📌 0
Quad9's experiments over the last year were in a small group of POPs but as of today rolled out to more places. The problem is while rolling out to more POPs, very few adopted the capabilities. Facebook and a CDN are the top consumers of DOT, B root of course allow for it
24.07.2025 09:10 — 👍 0 🔁 0 💬 1 📌 0
Google, Quad9, IBM, and others are enabling probing. Google's most recent publications on this were nearly 6% of egress traffic utilizing opportunistic signal to upgrade to encrypted. If the stars align groups may try and co-op launch a public trial end of this year
24.07.2025 09:01 — 👍 0 🔁 0 💬 1 📌 0
Working on finding bad browser extensions. More at: https://secureannex.com
Labor economist, personal account, all opinions my own
IT Security | InfoSec | Cybersecurity | Cloud | DevOps | Automation | Infrastructure
https://hollandj.uk
Innovating at Palo Alto Networks. Views are my own
Old Skool Internet geek, particularly DNS. Pronouns: us/y’all.
[bridged from https://infosec.exchange/@paulehoffman on the fediverse by https://fed.brid.gy/ ]
senior politics editor @wired.com -- signal leahfeiger.86 with tips
Open Source Strategist at Samsung and general Open Web Curmudgeon.
Co-chair of the W3C @ab and ex-chair of W3C @tag; @openwebdocs co-founder; @openssf […]
🌉 bridged from https://mastodon.social/@torgo on the fediverse by https://fed.brid.gy/
I'm getting older but unlike whisky I'm not getting any better. Author of the Janus WebRTC Server, the imquic QUIC library and the KIAVC adventure engine, and a VERY amateur musician (and an even more amateur game developer).
Mastodon: @lminiero@fosstodon
Interested in the old and boring side of tech.
Internet standards, infrastructure security and privacy are my work-life. Also devoted to inclusive tech teams. Fan of OFMD and many SFF authors, fan of walking everywhere. She/they
Internet R&D, Open Standards and Open Source Sofware at NLnet Labs
🎓Music Fandom & Internet Cultures Postdoctoral Researcher (Stanford University)
✍🏽Music Journalist (DIY, FortyFive, Guardian, NME etc.)
📌 https://jenessawilliams.substack.com
UK Educator-Mathematics-primary/early years.
“Playful mathematics” award winning book: https://uk.sagepub.com/en-gb/eur/playful-mathematics/book276080
Early Childhood Mathematics Group https://earlymaths.org/
Blogs:
https://info125328.wixsite.com/website
DNS Operations Working Group of the Internet Engineering Task Force (IETF)
The Internet Architecture Board provides long-range technical direction for Internet development, ensuring the Internet continues to grow and evolve as a platform for global communication and innovation.
The Internet Research Task Force (IRTF) supports research of importance to the evolution of the Internet protocols, applications, architecture, and technology.
https://www.irtf.org/
The overall goal of the IETF is to make the Internet work better by producing open technical standards.
A legacy of discovery. A future of innovation.
Football. Basketball. Cream cheese.
Editor. Writer.
Social that puts the user in control, with AT Protocol at its core.
Coming soon. Join the waitlist at sprk.so
Questions? Thoughts? Cupcake recipes? hello@sprk.so




