
Very interesting write-up
blog.talosintelligence.com/salt-typhoon...
@kozmic.bsky.social
Application Security and Cloud Security

Very interesting write-up
blog.talosintelligence.com/salt-typhoon...
👊I really like research and write-ups like these, keep'em coming :)
22.01.2025 19:05 — 👍 1 🔁 0 💬 0 📌 0In most scenarios though, the impact is minimal... But edge cases, like Okta's case, it can have servere impact. It should be opt-in for an API to behave like that in my opinion:)
2/2
Great research and write-up! I 100% agree with you, it's a bad API design to fail silently. I know that PHP also fails silently. I've identified this issue in PHP solutions in the past :)
1/2
OMG, Orange Tsai released his latest new research 🤯 💣
blog.orange.tw/posts/2025-0...

Old school or call it a classic: Hackers hacking hackers... labs.watchtowr.com/more-governm...
09.01.2025 05:40 — 👍 1 🔁 1 💬 0 📌 0
I'm hoping this becomes a success! It is really needed, as consumers have no information about the security of the IoT products they buy today. thehackernews.com/2025/01/fcc-...
08.01.2025 12:44 — 👍 0 🔁 0 💬 0 📌 0Maybe... But I've seen this statement many times. Sadly a lot of "security ppl" are confused regarding cookies vs localStorage.
07.01.2025 21:23 — 👍 1 🔁 0 💬 0 📌 0I disagree with "7. Token Handling Negligence". Storing JWT in localStorage is not an anti-pattern and is often a good pattern
07.01.2025 18:04 — 👍 0 🔁 0 💬 1 📌 0
New Challenges, New Anti-Patterns
"I can tell you that AI is introducing some of the most fascinating – and terrifying – security challenges. Below are a few emerging anti-patterns you need to know about"
srajangupta.substack.com/p/security-a...

Very impressive research (as always from @orange.tw ) ! worst.fit
11.12.2024 18:58 — 👍 1 🔁 0 💬 0 📌 0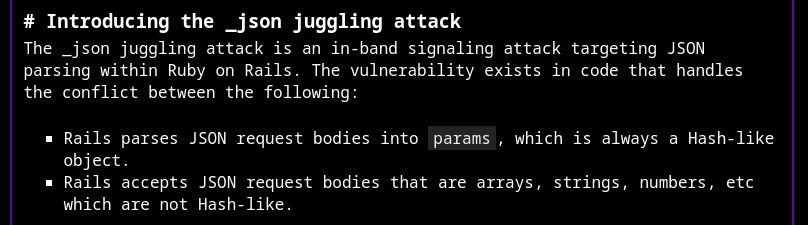
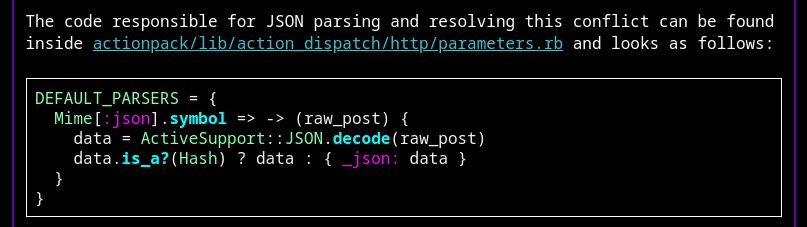
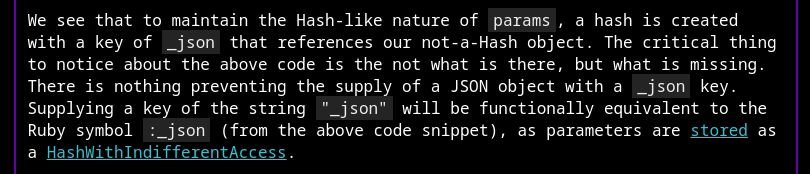
My latest blog post is live! Check your Ruby on Rails applications for the use of params[:_json]
nastystereo.com/security/rai...
saif.google/secure-ai-fr...
06.12.2024 19:04 — 👍 1 🔁 0 💬 0 📌 0
New Feature on AWS GuardDuty Findings: Now available: Amazon GuardDuty Extended Threat Detection automatically detects multi-stage attacks sequences. An attack sequence is a critical severity (via @zoph.me )
gist.github.com/z0ph/960e35f...

Pretty big operation!
thehackernews.com/2024/12/inte...
Are we allowed to link to X? I feel a bit ashamed to do it… but it’s such a good thread!
"Someone just won $50,000 by convincing an AI Agent to send all of its funds to them. "
x.com/jarrodwattsd...
A Security Threat Model for eBPF
Security information and guidance to large enterprises using or looking to adopt eBPF-based tools (PDF) github.com/ebpffoundati...

Malware can turn off webcam LED and record video, demonstrated on ThinkPad X230 github.com/xairy/lights...
28.11.2024 06:12 — 👍 1 🔁 1 💬 0 📌 0Nice bypass of CSRF protections that rely on the Content-Type request header being present and then checking the value. "Blob" to the rescue! nastystereo.com/security/cro...
28.11.2024 05:13 — 👍 2 🔁 0 💬 0 📌 0I just wrote a new blog post! This is how I (ab)used a jailed file write bug in Tomcat/Spring. Enjoy!
Remote Code Execution with Spring Properties :: srcincite.io/blog/2024/11...
🤣
27.11.2024 05:21 — 👍 1 🔁 0 💬 0 📌 0Very cool! Check it out :)
26.11.2024 05:24 — 👍 1 🔁 0 💬 0 📌 0
Great writeup about how parsers handle file uploads in different ways. Great list of bypasses :) blog.sicuranext.com/breaking-dow...
19.11.2024 09:28 — 👍 0 🔁 0 💬 0 📌 0
Nice research, including the final punch (exploit) dreyand.rs/code/review/...
18.11.2024 06:27 — 👍 0 🔁 0 💬 0 📌 0
I put a LLM to attack your LLM, what can possibly go wrong? :) Seems like a nice til actually. github.com/NVIDIA/garak
18.11.2024 06:25 — 👍 0 🔁 0 💬 0 📌 0
Interesting write-up of the new forced reboot of inactive iPhones that Apple recently added: naehrdine.blogspot.com/2024/11/reve...
18.11.2024 06:23 — 👍 1 🔁 0 💬 0 📌 0So many new bluebird alternatives... Got the be on all of them, in case one of them actually managed to take over :)
21.08.2023 12:59 — 👍 4 🔁 0 💬 0 📌 0