Hey Daniel 👋
I think the link is cut off...
Peter Stöckli
@ulldma.bsky.social
Security Researcher and Software Engineer at GitHub Security Lab
@ulldma.bsky.social
Security Researcher and Software Engineer at GitHub Security Lab
Hey Daniel 👋
I think the link is cut off...

Two tasks in sequential order displaying which notes are added to the general notes in each step. With the step trigger analysis the notes added are triggers, permissions and secrets among others. The second task “audit injection point” potentially adds notes such as sanitizers and checks to the notes.
Check out how my colleague Man Yue Mo and I used LLMs to triage CodeQL results. The GitHub Security Lab Taskflow Agent and the prompts we used are open source and ready to be used!
github.blog/security/ai-...
This is amazing. Use a SAST to detect security issues, and then triage those alerts with LLMs, to remove false positives and focus on real and exploitable issues.
And of course, the framework is open source.

Learn how we triage security alerts in GitHub Actions and JavaScript projects with the new GitHub Security Lab Taskflow Agent, and leverage LLM to focus on the exploitable vulnerabilities. github.blog/security/ai-...
20.01.2026 22:33 — 👍 1 🔁 1 💬 0 📌 1
Excited to share our open source agentic framework for security research, a collaborative framework that lets the community share AI "taskflows”! Read @kevinbackhouse.bsky.social 's blog post for details and a demo. Join us in strengthening open-source security! github.blog/security/com...
14.01.2026 23:24 — 👍 1 🔁 2 💬 0 📌 0I don't know who needs to hear this:
if you're thinking about automating a trivial task for the third time: just do it now!
It doesn't need to be something complicated, often a shell script is enough. $1 refers to the first argument passed to the shell script. (noted so I don't forget 😉)
Einstein said: “Insanity is doing the same thing over and over again and expecting different results.”
It looks like Einstein never used LLMs.
Well it's not exactly what you said, I think they "programmed" this outage themselves 😅.
There might still be a chance for such an exploitable vulnerability to be found 😉
This happened a while ago:
www.theguardian.com/technology/2...

GitHub Security Lab discovered a critical vulnerability in WooCommerce. We’d like to thank WooCommerce/Automattic for their incredibly quick response and fix of the vulnerability.
If you are using WooCommerce, please update. For more info see:
developer.woocommerce.com/2025/12/22/s...
Wohl eher ein kleiner "Teil der Wahrheit"? 😉
Auch mit grossen Sparquoten können wohl viele kaum die Tragbarkeitshürden überwinden.
FYI:
Ruby SAML 1.18.0 (released in March 2025) is not susceptible to these nice exploits. (ruby-saml got a hardened implementation with v1.18.0).
However, this hardened implementation was not backported to the 1.12.x branch of ruby-saml, that's why version 1.12.4 is susceptible.
Hack.Commit.Push Switzerland is just one week away! 🇨🇭
This is a great opportunity to get involved in Open Source projects like @assertj.github.io, with direct guidance from the maintainers!
🚀 GitHub is making Actions more secure by default
We recently announced upcoming changes to the pull_request_target event and environment protection rules to make GitHub Actions more secure by default.
We’ve opened a discussion to gather feedback 👇
🔗 github.com/orgs/communi...

🎉 It’s Friday at #EkoParty!
Join us at the GitHub booth at 15:30 for the GitHub Quiz 🧠
Test your security knowledge, win exclusive GitHub swag, grab some stickers, and chat with our experts!
👉 gh.io/eko

We're taking action to make the npm supply chain stronger and harder to attack. 🛡️
Check out our plan to create a more secure future for the JavaScript community.👇
https://github.blog/security/supply-chain-security/our-plan-for-a-more-secure-npm-supply-chain/

Recent account takeovers and attacks on package registries are a wake-up call: it's time to raise the bar on authentication and secure publishing practices. Find out what npm is doing—and what steps you can take—to help secure the open source supply chain: github.blog/security/sup...
23.09.2025 16:11 — 👍 3 🔁 3 💬 1 📌 0
I have often stated that well-implemented memory tagging will be a game changer for memory corruptions. And it seems that with the next iPhone it's finally here: security.apple.com/blog/memory-...
10.09.2025 08:06 — 👍 56 🔁 17 💬 4 📌 4
What if attackers could hijack your coding agent through a simple GitHub issue?
Prompt injections are a real and growing threat for VS Code Copilot Agent.
Learn how these attacks work and how you can defend your environment.
Read the full research: github.blog/security/vul...
Today I have a more serious topic than usual, please consider reposting for reach:
My wife and I are urgently looking for a specialist in neuropediatrics or a similar field for our autistic child with a diagnosed, but not further specified, movement disorder [1/4]

🚀 GitHub is on a mission to supercharge open-source security! We've partnered with 71 key open-source projects, giving them tools, funding, and playbooks to boost security. 🔐
Want your project to be part of this effort? Now’s the time to get involved! 💪
🔗 Find out more: github.blog/open-source/...
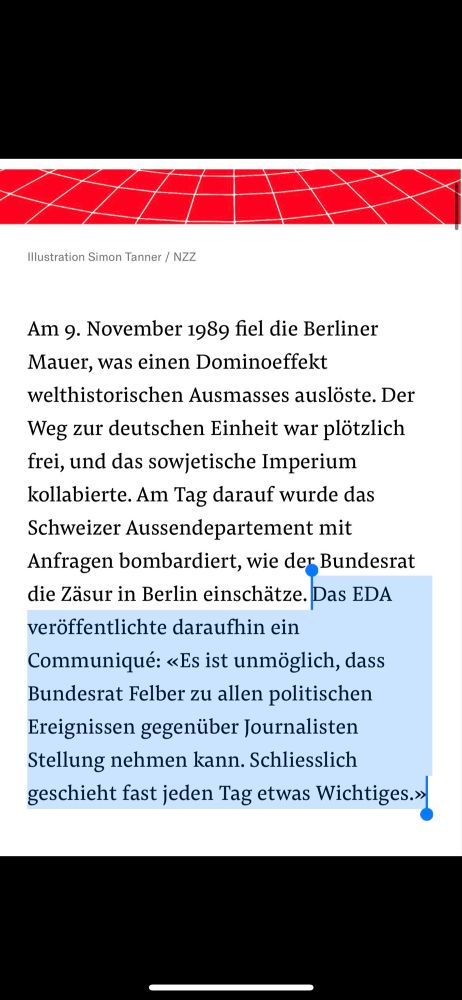
Translation: On November 9, 1989, the Berlin Wall fell, triggering a domino effect of world-historical proportions. The path to German unity was suddenly clear, and the Soviet empire collapsed. The following day, the Swiss Foreign Ministry was bombarded with inquiries as to how the Federal Council assessed the caesura in Berlin. The FDFA then issued a communiqué: "It is impossible for Federal Councillor Felber to comment on all political events to journalists. After all, something important happens almost every day."
Never change, Switzerland, never change. 😂
www.nzz.ch/meinung/schw...
"In Deutschland ist eine Mauer umgefallen."
Probleme mit der Infrastruktur kommentieren wir nicht 😉

Meinst du CryptPad? github.com/cryptpad/cry...
07.08.2025 12:49 — 👍 0 🔁 0 💬 1 📌 0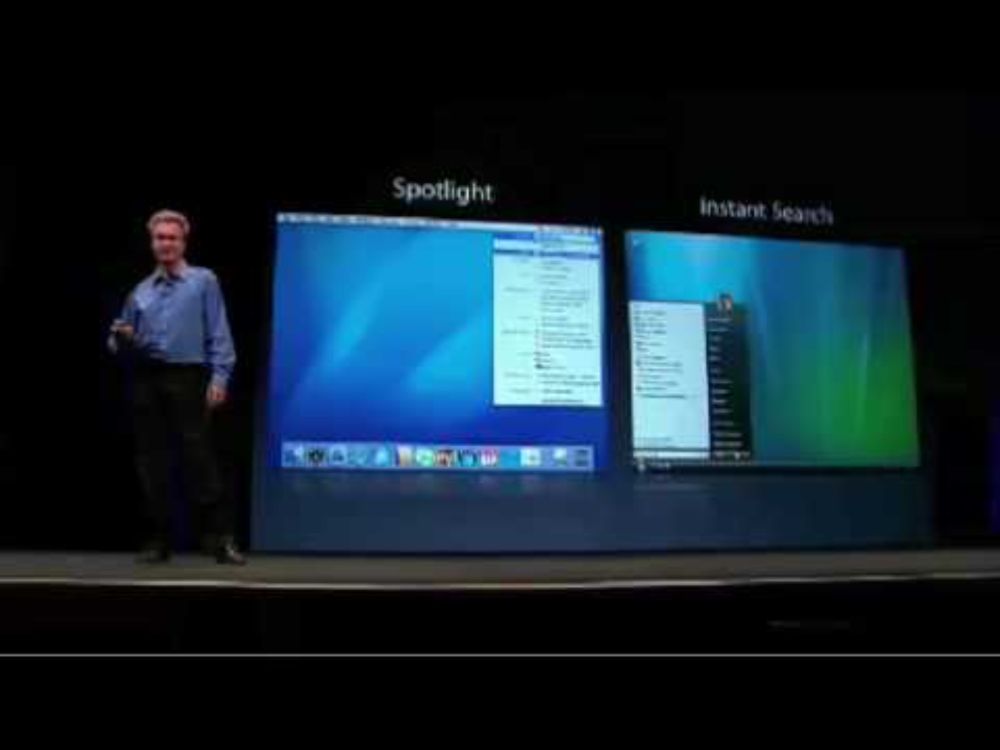
This time Cupertino started the photocopiers 😅
www.youtube.com/watch?v=N-2C...

I'm coming to Switzerland! Join me at the Microsoft Azure Zürich User Group in only a few weeks from now: www.meetup.com/de-DE/micros...
27.05.2025 00:03 — 👍 18 🔁 8 💬 1 📌 0
Our team member Man Yue Mo is back, showing a new way to bypass MTE protection on Android phones with CVE-2025-0072. github.blog/security/vul...
23.05.2025 14:52 — 👍 6 🔁 3 💬 0 📌 0 15.04.2025 15:25 — 👍 3 🔁 0 💬 1 📌 0
15.04.2025 15:25 — 👍 3 🔁 0 💬 1 📌 0

Next Monday I'm doing a 2h webinar on files as seen through the eyes of a cybersecurity researcher. This will cover useful stuff for programmers, more junior pentesters, and other tech enthusiasts who enjoy knowing how stuff works on a computer :)
hexarcana.ch/lp/files/?ut...
Note: the payloads displayed in the video have been faked to avoid disclosing details of how to implement a working exploit. The details of how to implement a working exploit have not been released yet.
More info at: github.blog/security/sig...